Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

These missions are for everyone here, and you can join at any time. Your experience level doesn't matter. HackThisSite is a free, legal and safe practice ground for aspiring hackers wanting to test their knowledge on something real. We have full permission to exploit their servers, and we even get point rewards for it. This week's mission on HackThisSite was to recover the admin password by manipulating an I forgot my password form action, however, this time there was an added brick wall.
Basic Mission 5
When we start the mission, it reads:
"Sam has gotten wise to all the people who wrote their own forms to get the password. Rather than actually learn the password, he decided to make his email program a little more secure."
Right-click the page and view the page source. Scroll down until we find the form action that we can use to retrieve the password. It looks like this:
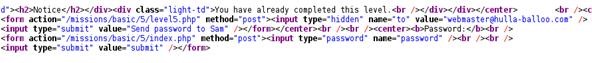
Since this is posting, we can't edit the HTML and try the webpage we edited locally, like last time. This time, we have to edit it with JavaScript in real time.
javascript:alert(document.forms[0].to.value="myemail@gmail.com")
After, click the form submission button for "I forgot my password" and you will be sent a password to your email. Simply enter it in the field to complete the mission.
How Can This Be Prevented?
A small PHP script that hid the email and sent the password would be far more secure, because it would be processed on the server end, as well as hidden from user sight.
Next week, I might be planning on setting up a virtual machine, or a remote host for the members to hack live. We will walk through getting root access and covering our tracks on a controlled server. Any thoughts? Let me know in the forums. Follow Null Byte on Twitter and G+ for the latest tutorial updates. Feel free to drop other members a few lines in the IRC. Happy hacking everyone!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























Be the First to Comment
Share Your Thoughts