Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.
In this article, I'm going to list my five favorite tools. This doesn't mean these are the only tools you should use, and it also doesn't mean there isn't a better tool for the job in some situations. These are the tools I use when I sit down to go to work.
sqlmap
$ svn checkout https://svn.sqlmap.org/sqlmap/trunk/sqlmap sqlmap-dev
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a great detection engine, many niche features for using a proxy, and a broad range of switches, from database fingerprinting, to data fetching from the database, to accessing the underlying file system and executing commands on the operating system. Here is a shot of just some of the options below.
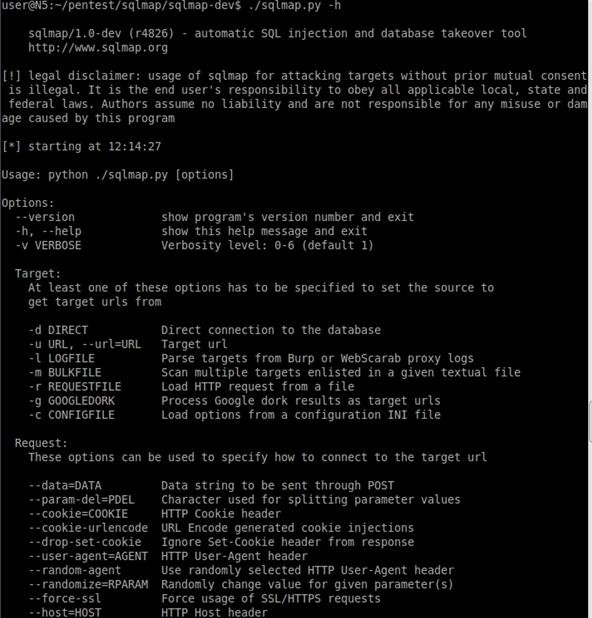
sqlmap is developed in Python, so if you do not have it on your system, you can download the latest version right here. If you want to get into some real fun with sqlmap, you'll need another package to go along with it. sqlmap uses the Metasploit Framework to create and deliver payloads. No surprise that is our number two!
Metasploit Project
$ svn co https://www.metasploit.com/svn/framework3/trunk/
Metasploit is an open source computer security project written in Ruby, which provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Its most well-known sub-project is the Metasploit Framework, a tool for developing and executing exploit code against a remote target machine, and the suite I will be referring to when I say 'Metasploit'.
Like almost all pentesting applications, Metasploit can be used for analysis and discovery or used to gain unauthorized access into a computer. This provides a public resource for researching security vulnerabilities and developing code that allows a network administrator to break into his own network to identify security risks and document which vulnerabilities need to be addressed first.
Also worth a mention is the extensive anti-forensics and IDS evasion options built in.
W3af
$ svn co https://w3af.svn.sourceforge.net/svnroot/w3af/trunk w3af
W3af has been called the Metasploit for web application testing, and I can agree with that. W3af uses more than 130 plug-ins to find vulnerabilities in web applications. After finding vulnerabilities like SQL injections, OS commanding, remote file inclusions (PHP), cross-site scripting (XSS), and unsafe file uploads, these can be exploited in order to gain different types of access to the remote system.
W3af has plugins that communicate with each other. For example, the discovery plugin in W3af looks for different URLs to test for vulnerabilities and passes it on to the audit plugin which then uses these URLs to search for vulnerabilities. It removes some of the headaches involved in manual web application testing through its fuzz testing and manual request generator feature.
Snort
$ wget http://www.snort.org/dl/snort-current/snort-2.9.2.1.tar.gz -O snort-2.9.2.1.tar.gz
Snort is the Swiss army knife of security. Snort has a few uses—a packet sniffer like tcpdump, packet logger for network troubleshooting, or an intrusion detection system. Snort can be placed on machines throughout your network and it works in promiscuous mode to watch all traffic on the wire. Snort can also be used to sift through already-made tcpdump files.
Many times it's far too easy for attackers to scan your network for vulnerable services that could be running or ports that are available. With this being a fact, there isn't an excuse to ignore security when putting intrusion detection in when it's so easy to do. Having Snort watch your internal network is important because many of the security problems actually come from inside your network, and in that case, you have more of a chance to correct something before it goes too far. Best of all, this tool is free and available on most platforms!
In Closing
Of course there are several other great tools out there, but getting acquainted with these 5 will provide you with a great place to start. We'll go over those in more detail in the coming weeks. I wanted to give a broad overview of what I believe to be key collections and frameworks you should know. In later articles, I will explain each of these in much more detail. Coming up next... an Intro to Snort and IDS, so stay tuned!
What tools do you use? Did I miss something on my list? Leave us a comment here or start a thread on the forum! We have a lot of talented voices here at Null Byte and I would love to hear them.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























13 Comments
Very informative, I will have to try these after I figure out why my linux keeps crashing on me (OpenGL bug???)
What kind of crash? Why do you think it's OpenGL? Maybe we can fix this.
I haven't read the logs yet but I have been experiencing the same type of crash in both Linux and Windows where the system would studded and sometimes respond or sometimes just lock up and I have to do a manual reboot, it tends to happen more often while youtube pages or openGL apps are running
Queston: All the code that you're writing and showing, is it from command prompt or is it another OS/IDE/Program?
It is a mix of different OSes, but it is the terminal on them, the OSes I belive are Backtrack 5 (r2?) and a different linux distro
That is all from the command prompt and the text output that follows. I ended up being on two separate machines when writing this, so as Matthew said, parts were done in Backtrack and parts in Debian.
On a note unrelated to content, but related to the comparison in the title… A knife has been shown to be much more effective and damaging than a gun in close combat. Food for thought.
And you can throw a knife faster than someone can pull a gun on you? Though, I prefer having several sniper backups...just so long as they don't shoot you, you're good!? :) Great tutorial, definitely going to do some penetration testing over spring break!
Great article, and to Bird and Bear that also depends on who is using that knife. If that person is so well skilled that is..
I suppose my comment does fit the content of the post.. Just make sure you have the appropriate tool for the job, and that you know how to use it. The general solution might not always be the best one :P
Well put. I always caution people against catching fanboy fever. It's too easy to fall in love with a tool and mistake one's comfort with it for a reason not to learn something new (or worse: to #$%@-talk other tools without really understanding how to use them). The "use the right tool for the job" mantra only works to the extent of your willingness to broaden your horizons. Don't be afraid to try new things (even if they're unpopular).
It should be noted that IPsec generally refers to https://en.wikipedia.org/wiki/IPsec . I was epically confused that the article made not further mention of IPsec beyond the headline. :P
Also - some good additions are:
Nmap: http://nmap.org/
and
WireShark: http://www.wireshark.org/
Haha good point sir, and sorry about that!
Share Your Thoughts