As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

Obtaining GPG
GPG can be downloaded for free at its website, if you do not already have it on your system. As many Linux flavors already include it on a default installation, you can test this by opening up a terminal and typing 'gpg -h'. If the help list scrolls across your screen, you are on the right track! If you receive a 'command not found' error, click the link above and follow the instructions for your operating system to get the latest version.
I will be talking about the command line options for GPG here, although several GUI interfaces exist such as KGPG for KDE and Seahorse for Gnome. Debian/Ubuntu users may 'sudo apt-get install xxx' to obtain these packages as well. Windows users may download GPG4win.
Getting Started
The basic idea of public-key cryptography is that you have two keys. One key is your public key and one is your private key. When you encrypt a message to send to someone, it uses the public key of that person in the actual algorithm. When they receive the message, they use their private key to decrypt and read it. Because the private key can not be determined from the public key, you can post and share your public key with anyone who needs it.
Step 1 Choosing a Key
Open up a terminal window and type 'gpg –gen-key' and you should see:
Please select what kind of key you want:
- RSA and RSA (default)
- DSA and Elgamal
- DSA (sign only)
- RSA (sign only)
Choose option 1 to allow for both encryption and signing.
Step 2 Choosing a Key Size
What key size do you want? (2048)
The default is 2048 bits long. As a default, this value is alright, but the larger your key the harder it will be to break. Also, increasing this value increases the computing cycles to create it, but as I said, we want max protection, so let's go ahead and set this to 4096. It would take the combined processing power of every computer in the world thousands of years to crack 4096-bit encryption.
Step 3 Choosing Its Expiration
Please specify how long the key should be valid.
- 0 = key does not expire
- <n> = key expires in n days
- <n>w = key expires in n weeks
- <n>m = key expires in n months
- <n>y = key expires in n years
This is a personal choice. You are setting a timer on your key-set. After X amount of time from the creation date, the keys will no longer be valid and you will need to create a new set. I personally set this value to one month, but you can choose whatever you like here.
Step 4 Create a User ID
You need a user ID to identify your key; the software constructs the user ID from the Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) <heinrichh@duesseldorf.de>"
Here, as above is more of a personal choice. You can fill these fields out depending on your use. If this is for business, you might want your real name and email, if not, well... be creative.
If you entered the data as follows:
Real name: Allen Freeman / Email address: Allen@nullbyte.com / Comment: me
In this case, your ID would be Allen Freeman (me), and this would be what you would use to address messages after you've imported someone's public key. That's a topic we'll discuss in the next article.
Note: That is not a valid email address for me.
Step 5 The Achilles Heel — Your Passphrase
You need a passphrase to protect your secret key.
This is the critical part. The weakest link in the entire process is your passphrase (not 'word', but 'phrase', because it allows spaces). If you happen to forget it, your key is useless, and if it's simple and easily broken, even more more so. I recommend to my clients a passphrase NO LESS then ten characters, alternating between case, numbers and symbols. If your passphrase looks like a Perl statement, you are doing it right.
After this is finished, GPG will need to generate entropy to create your key. In a (very small) nutshell, it's using the "random noise" of your computer, such as files opening and closing, processing, memory swapping, etc. to create random values. This might take a few moments and you might be told you need to generate more entropy. Just wiggle your mouse around and bang some keys on the keyboard until it lets you know it has finished.
pub 2048R/D7FC65D2 created: 2012-02-20 expires: never usage: SC
trust: ultimate validity: ultimate
sub 2048R/389AA63E created: 2012-02-20 expires: never usage: E
[ultimate] (1). Allen Freeman (Comments go here) <allen@nullbyte.com>
When you are finished, your user ID is the second string after the slash in the public list (pub 2048R/D7FC65D2 – so D7FC65D2 would be your UID) and you now have your own set of encryption keys.
Step 6 Export the Public Key
One last step before you can share the public key—you need to export it. You need to type 'gpg -a –export [UID]' and simply save the fingerprint that appears. All someone needs is that key-block to send you a file that only you can open.
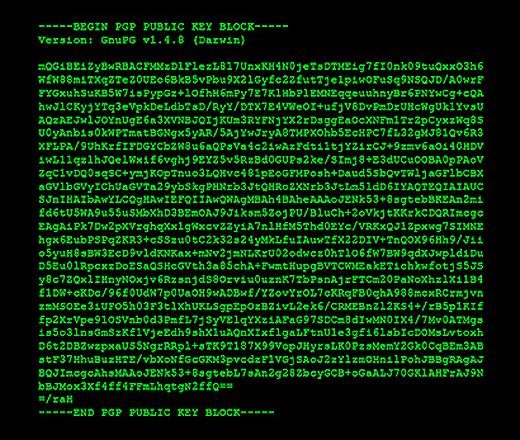

Is that all? Not by any means. In my next article I will explain in detail how to import your friends keys, upload your own to key-servers
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















19 Comments
The weakest link is the passphrase you come up with. This touches on one of my little annoyances with how we train the less technical to write passwords (or in this case passphrases). We teach people to make their passwords difficult for humans to remember, but easy for machines to crack instead of easy for humans to remember and difficult for machines to crack. It's actually more secure to come up with a longer passphrase than to try and make a shorter one tricky by using random capitals & symbols. This XKCD post sums it up well.
This is very true and that is why most of the giants in the computing world get hacked so easy, the staff members use really easy passwords.
great info thanks!
Nice, very informative
After having dumped hashes upon hashes I will say, I have seen some really really bad passwords. I would even say more often then not actually.
Whats the difference between Hashing and Encrypting? Same goal, different techniques? What makes this encryption 'unbreakable' is that it just takes too much power/time for an average person to break it, but a super computer could break it, right? (I guess Im saying, is there a such thing as uncrackable?)
A hash is a plain-text value that has been encrypted. Hashes are (usually) a one-way cryptographic function used to store values in a cipher-text form. When you root a box and look at the passwords, they are stored as hashes for security. In that sense you could look at them as the same in format but slightly different in function. When you encrypt something using GPG you are using an asymmetric cipher requiring two keys.
The real gritty details are beyond the scope of a comment but I encourage you to post this in the forum!
Nothing is "uncrackable", per se. In everything lies a hidden flaw to be exploited, though I suspect you would have to be a graduate math student if you ever hope to discover this "flaw". Exploits come out all the time that make certain cryptographic algorithms less secure as the flaw usually allow for the attacker to greatly reduce the mathematical possibilities and/or time to discover the key/plain text/etc...However, as Allen states: brute forcing (e.g. trying every single possibility one by one) or simple cryptanalysis of something like a 4096bit encryption would take so many years, even with a super computer, that attempting to crack it is futile. Other methods, such as keyloggers, extortion and other not so pretty methods could potentially be used to decrypt a file or something?
On the money in fact. Social engineering can be used, and your private key can be brute forced if someone manages to get their hands on it, as it's only protected by your passphrase. And like you said, every few years new flaws are found in the current algorithms. MD5 was cutting edge when it first came out and now it is not considered secure.
It is unbreakable in the sense that it would require more computing power then is reasonably accessible to break it. This directly relates to your password/phrase length and variance.
Aha! I got it. Man, thats quite something. It makes me want to learn the process of creating my own method of encryption, piggybacking on what I know already and what already exists, attempting to make something that only God's computer can break.
I know it's difficult (hold on ms./ms. negatives), but it can be done. I'm excited.
Is this still unbreakable or still nearly impossible to crack?
Nothing is unbreakable.
What kinds of encryption are 'nearly' impossible to crack?
I mean yeah it is still breakable, but is this one of the hardest encryption to decrypt? Or can you post a tutorial in encrypting files using one of the hardest and one of the most secure encryption?
"Theoretically, messages sent using quantum cryptography would be
in an unknown quantum state, so they could not be copied and sent on. Two, in a quantum system, which can be in one of two states, any attempt to measure the quantum state will disturb the system."
Random: http://en.wikipedia.org/wiki/Quantum_cryptography
Greenlemon:
The type of encryption you use will depend upon the medium, the level of confidentiality you are seeking and who you are trying to hide the data from. For most purposes, 256-bit AES encryption will be more than adequate, but if you are trying to hide from NSA, almost nothing will work.
OTW
Ok. I hope you make a series about cryptology.
I'll put it on my list of subjects.
Share Your Thoughts