Welcome back, my amateur hackers!
Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.
In many disciplines, if you don't practice, you fall victim to failure. In our discipline, if you don't practice and fail, you may be serving years behind bars. This makes practice and a dedicated practice lab an even more compelling argument than with other disciplines.
Many of you have been having difficulty setting up your hacking environment to practice your hacks. In this tutorial, I will show you the simplest and fastest way to set up a lab to practice your hacks before taking them out into the real world where any slip-ups could be devastating!
Step 1: Download VMware Workstation or Player
The best way to practice hacking is within a virtual environment. Essentially, you set up a hacking system, such as Kali Linux, and some victims to exploit. Ideally, you would want multiple operating systems (Windows XP, Vista, 7, and 8, as well as a Linux flavor) and applications so that you can try out a variety of hacks.
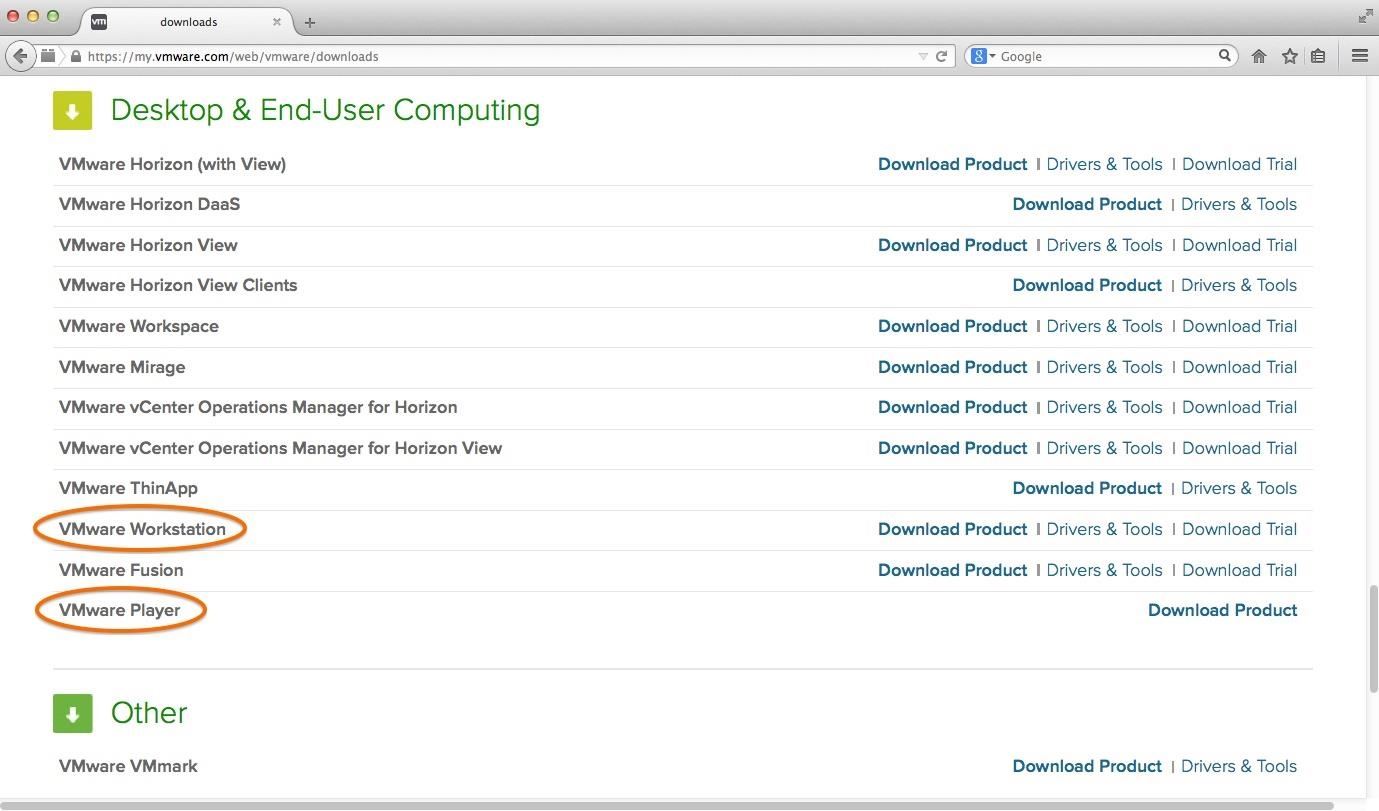
Virtual machines and a virtual network are the best and safest way to set up a hacking lab. There are several virtualization systems out there, including Citrix, Oracle's VirtualBox, KVM, Microsoft's Virtual PC and Hyper-V, and VMware's Workstation, VMware Player and ESXi. For a laboratory environment, I strongly recommend VMware's Workstation or Player. Workstation is commercial product that costs under $200, while Player is free. You can also get a free 30-day trial of Workstation.
Player is limited to just playing VMs, while Workstation can both create and play VMs. Let's download VMware's Workstation or Player here.
Step 2: Download Kali VMware Images
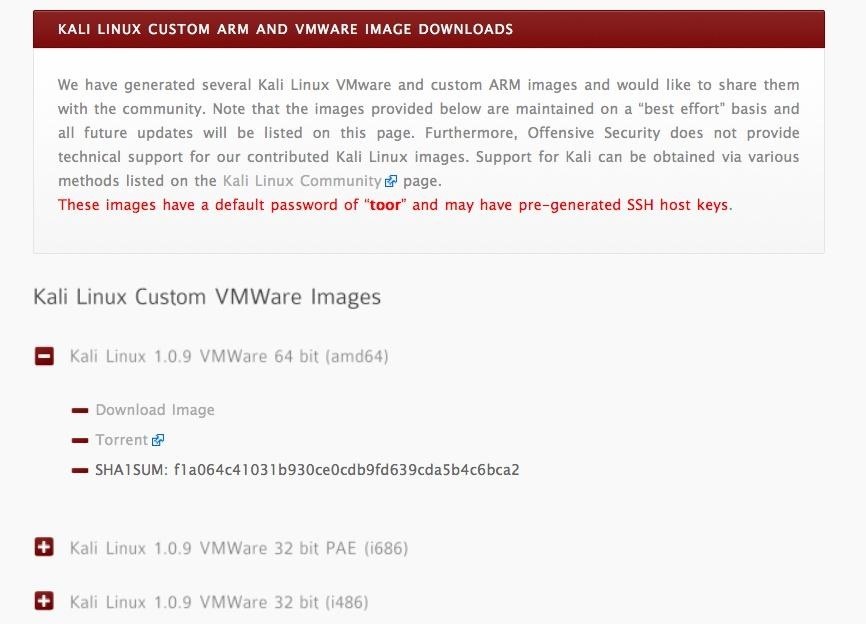
Once you have downloaded and installed your virtualization system, our next step is to download the VMware images of Kali provided by Offensive Security. With these images, you won't have to create the virtual machine, but simply run it from Workstation or Player—Offensive Security has already created this image for you. This means that once you have downloaded the VM of Kali, you can then use it in either Workstation or Player.
Step 3: Unzip Images
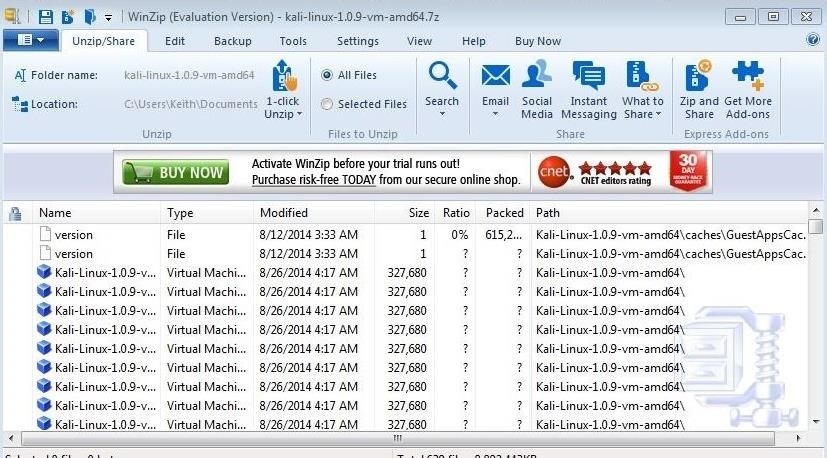
Once you have completed the download, you will need to unzip the files. There are numerous zip utilities available for free including 7-Zip, WinZip, WinArchiver, etc. Download and install one and unzip the files. In the screenshot below, I have downloaded the free trial of WinZip and have used it to unzip the Kali files.
Step 4: Open VMware Image
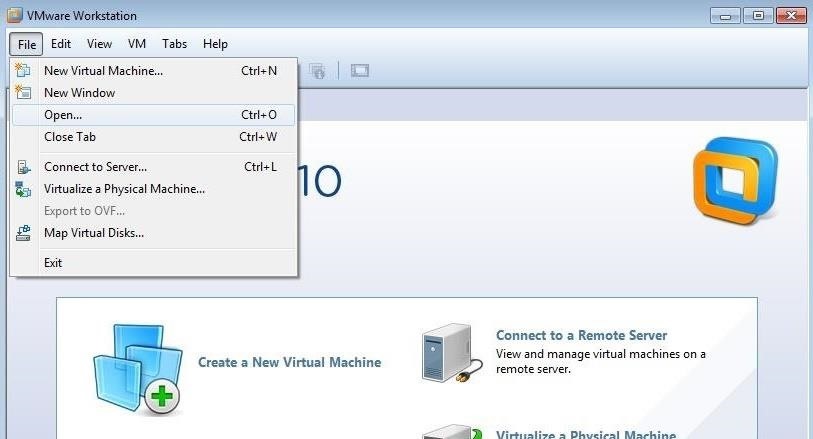
Once all the files have been unzipped, our next step is to open this new virtual machine. Make note of the location where you have unzipped the virtual machine image. Then, go to either VMware Workstation or Player and go to File -> Open like in the screenshot below.
This will open a window like that in the screenshot below. You can see that my Kali image was stored under documents, so I browse there and double-click on the folder.
When I do so, it reveals the VMware virtual machine file that I will load into VMware. Note that I am using the "amd64" version, which is simply the 64-bit version, but the 32-bit version will work, as well, albeit a bit slower.
When you do so, VMware will start your virtual machine and greet you with a screen like below.
Click on the green button in the upper left below "Kali-Linux-1.0.9-vm-amd64" that says "Power on this virtual machine." You should be greeted by the now familiar Kali screen like below.
Simply use the user "root" and password "toor" to get started hacking!
Step 5: Download & Install Targets
For the next step, you need to download and install a target system. Of course, you could use your own host Windows 7 or 8 system, but since this is practice, you might want to use an older, easier to hack system. In addition, hacking your own system can leave it unstable and damaged.
I recommend installing a Windows XP, Vista, Server 2003, or an older version of Linux. These systems have many known security flaws that you can practice on and, then when you become more proficient at hacking, you can then upgrade to Windows 7 and 8 and newer versions of Linux.
If you or your friends don't have a copy of these older operating systems, you can purchase them very inexpensively many places on the Internet. For instance, at last check there are numerous copies available on eBay for as low as $9.95.
Of course, you can also obtain these operating systems for free on many of the torrent sites, but BEWARE... you will likely be downloading more than just the operating systems. VERY often, these free downloads include rootkits that will embed in your system when you open the file.
In addition, older versions of Linux are available from the distributor or via torrent sites, as well.
Step 6: Download Old Applications
Once you have your operating system in place, very often you will need applications to run on these older versions of the Windows and Linux operating systems. You will likely need a browser, Office, Adobe products, etc. These older products have well-known security flaws that you can hone your skills on.
I like the site Old Apps to download many of these. Of course, once again, you can obtain these from many of the torrent sites with the same caveat as above of you might get more than you bargained for.
I'm hoping that this brief tutorial is helpful to some of you who have had difficulty setting up Kali and a lab, and now we can get back to our work of hacking, my amateur hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















28 Comments
Can I install antivirus and firewall to the vm so that it is more challenging?
Of course
I'm trying to do a nmap port scan against a windows 7 machine but I'm getting "all 1000 scanned ports on 192.168.1.2 are filtered because of 1000 no-responses" I have tried the following, sS, PO, T2, but still can not bypass the firewall to see which ports are open..works as soon as the firewall is disabled..
David:
The firewall must leave some ports open or the target machine can't communicate. At least, 80 and 443 should be open.
OTW
Thanks. Yeah I agree, but its strange I'm not getting a response telling me, only get the response I mentioned above. Its just using windows firewall. Any ideas? When I disable the firewall I get around 10 or more ports which are open..I'm sure the laptop has internet when firewall is on.
When you are turning on the firewall, you are likely blocking everything.
is it possible to hack xbox live
Yes you can. Should you?
Of course, it possible. Everything is hackable.
isn't it better just to boot kali from the boot menu instead of running it in a virtual machine ?!
Yes, by doing that your kali linux is able to operate your hardware; sound card,network card,CPU,GPU,PSU,etc and gives you advantages.
Example: You can not capture packets with network card if you are using VM until you have bought external network card.
snickers
Explain packet capture part please..
What half way respectable neophyte will not have a USB WiFi adapter?
I think you mean that you can't capture wireless packets from a vm. Youneed an external wireless adapter. To hack wireless you need an external wireless adapter unless your internal adapter is aircrack-ng compatible. Most are not.
What are some internal adapters that are aircrack-ng compatible?
Why would that be better?
Possible explanation video if allowed I am interested in this idea and I want to set up a laboratory for the experiment penetration
Why would it be a problem that your vm is infected with a rat?, you can't make an ISO infect the host if the host never opens it.
For a set of good http (website) targets, download the OWASP BWA (Broken Web Applications) from here...
https://www.owasp.org/index.php/OWASP_Broken_Web_Applications_Project
That's got stuff like WebGoat (for Java and .NET), The broken versions of PHPBB, and Joomla, as well as lots of other good stuff to try to hack into.
Thanks Philip!
I have question can i make 2 virtual box systems with one kali and another winXp and try to hack winxp through metasploit and meterpreter? from kali?
yes
+Kudos, exactly what I need for practice. Thank you for all the work! Keep it up!
Hi, i was wondering if anyone could tell me a few good first tests to get used to the virtual lab. Im not looking for step-by-step just a few cases i could try that should be an easy test run for the virtual lab.
I've managed to install virtual box and I'm attempting to use the metasploit SMB exploit on my guest WinXP. I get the unreachable connection timed out error. I've scoured the net for a solution but can't find one. I've tried all adaptors. I'm going with NAT with port forwarding as it seems Metasploit uses port 445, the port forwarding rule I have is TCP Host IP 127.0.0.1 Host port (tried many incl 80 and 445) Guest IP 10.0.2.15, Guest port (tried many incl 80 and 445) . . There's no firewall on winxp. I tried to NMAP and ping the guest but all ports are blocked. I'm at a real loss. I currently have my wifi adaptor wlan0mon enabled and connected to the net.
Please help, it seems no one knows the answer, even experts.
i cant get sessions using exploit smb netapi windows xp..
but port 445 is open when using nmap
exploiting using vmware workstation pro 12
NAT
I followed your directions to the letter, but when I got to where I would initiate Kali Linux, it did not startup! Rather, it told me that my computer has just 2 CPUs and Kali Linux requires 4! My system has just 2GB of RAM, but to use Kali Linux, do I need to upgrade my RAM to 4GB? Please, I need your help!!
Jackson, can you post a screencap?
Do you know why you strongly recommend the vmware over virtualbox? I dont know which one to choose so i just choose the virtualbox because it is completely free.
Share Your Thoughts