Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!
Well, not really, but his latest project, dubbed MagSpoof, can spoof any magnetic stripe or credit card, enabling a device to wirelessly send a signal to traditional credit card readers without needing NFC or RFID, à la Samsung Pay. Furthermore, the project is easy to build using basic electronics and his custom code.
Once built, MagSpoof can function as a traditional credit card (or hotel room key, driver's license, MTA card, etc.), can switch between cards, and has the potential to disable new chip-and-PIN (EMV) cards and predict American Express card numbers, although the code for the latter two is not included in the project.
Understanding Magnetic Stripes
To understand how MagSpoof works, you'll first need to know how magnetic stripes work. While the level of magnetism in these stripes is quite low, it is enough to attract iron oxide particles, which in turn reveal each bit in the tracks (credit cards have two tracks).

Once the iron oxide has adhered to the strip, you can actually use the bits to pull the credit card number.

Two solid stripes is a 1, while a stripe followed by a space is a 0. This data can be used to gather the credit card number, and other data, such as expiration date, CVV code, and more. Just take each 5 bits and only read the first 4.
Using MagSpoof
MagSpoof produces a magnetic field that emulates a stripe swipe by quickly changing the polarization of an electromagnet. And, as stated by Samy, "the stronger the electromagnet, the further away you can use it."
Building the Hardware
Head over to Samy's blog for a full list of all the required parts, details about them, and where you can get them from.
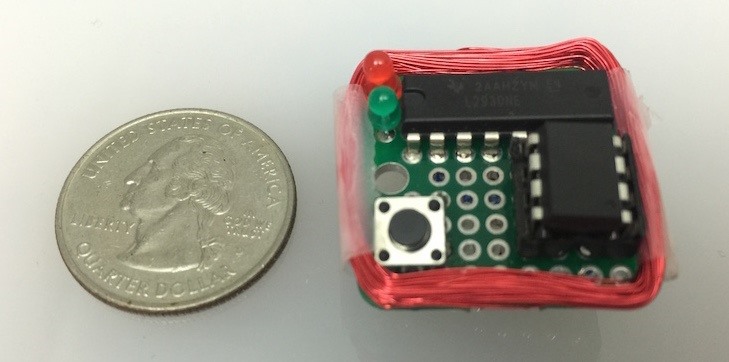
Schematics
The schematics should be fairly easy to follow if you've ever done anything like this before. If not, you probably shouldn't be messing around with it.
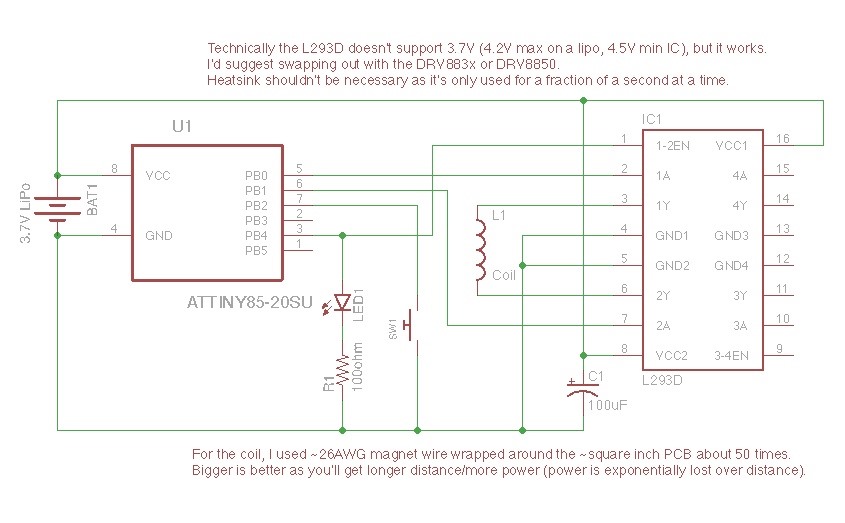
Firmware
You can download the code and full schematic from Samy's GitHub page.
Restrictions
For security purposes, MagSpoof does not have a publicly accessible code for bypassing chip-and-PIN protection and American Express card number protection.
Chip-and-PIN
New to the U.S. (but widely used in Europe for some time), this card protection mechanism requires a card to be "dipped" in a card reader at the point-of-sale.
This protection can be deactivated from the bits obtained in the magstripe, completely bypassing this enhanced security measure. Samy has offered this information to credit card issuers, and is therefore not opening it up to the public.
American Express Card Protection
After Samy lost his AMEX card, he noticed that the replacement card had very similar digits to the one he lost. This led to him discovering that a global pattern could be used to accurately predict card numbers using the number of a stolen card.
"This means if I were to obtain your Amex card and you called it in as lost or stolen, the moment you get a new card, I know your new credit card number."
Again, he has notified American Express, and therefore will not release the code pertaining to AMEX cards to the public.
For more information on this project, check out Samy's blog. And be sure to subscribe to Applied Hacking, along with his YouTube channel, to stay up to date on his latest research and projects.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















Be the First to Comment
Share Your Thoughts