Welcome back, my greenhorn hackers!
Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.
As mentioned in the first part of this series, passwords are stored in a one-way encryption called hashes. There are multiple ways of obtaining these hashes, such as .dll injection in Windows systems or capturing the hash in transit, such as in WPA2 wireless cracking.
Once we can grab the hash, the next step becomes one of finding an effective and efficient way of cracking it. There are numerous tools, some of which I have highlighted in other articles here, but hashcat is unique in its design and versatility, so let's take a look at how it works.
Step 1: Fire Up Kali & Open Hashcat
Let's start by firing up Kali and opening hashcat. Go to Applications -> Kali Linux -> Password Attacks -> Offline Attacks -> hashcat, as seen below.
When we click on the hashcat menu item, it opens the help screen.
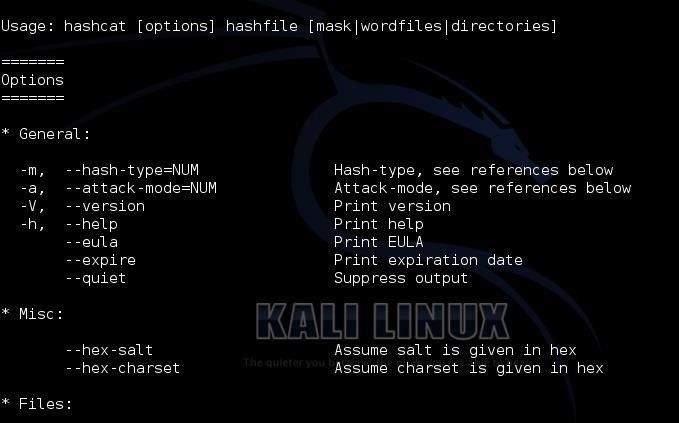
At the top of the screen, you can see the basic hashcat syntax:
kali > hashcat options hashfile mask|wordfiles|directories
We can see some of the options for hashcat displayed below the basic syntax. Some of the most important of these are -m (the hashtype) and -a (attack mode). In general, we will need to use both of these options in most password cracking attempts with hashcat.
Step 2: More Extensive Options
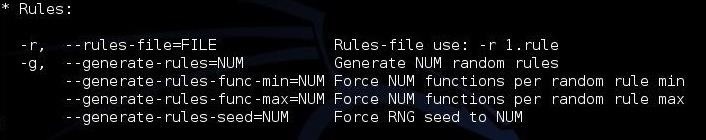
If we scan a bit further down this hashcat help screen, we can see more options. The first two below are some of the key options that hashcat enables.
First, hashcat enables rules that allow us to apply specifically designed rules to use on our wordlist file. These rules can take our wordlist file and apply capitalization rules, special characters, word combinations, appended and prepended numbers, and so on. Each of these will help us to break passwords that have been made more complex to avoid dictionary attacks.
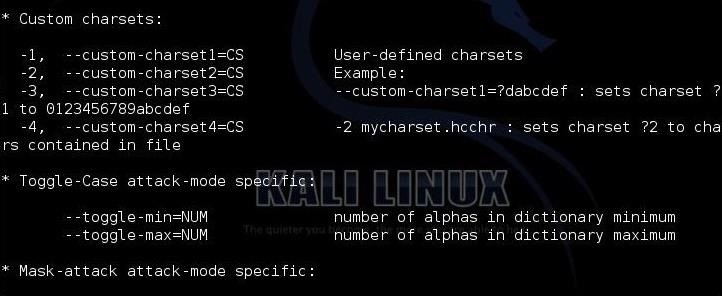
The next stanza shows us custom character sets. This enables us to set the character set that we want to use to crack the passwords. If we know the company's or institution's password policy, we can choose a subset of all characters to meet their policy and speed up our cracking. For instance, if a company allows an all-numeric character set, choose to crack the hashes with just numbers. These types of passwords are VERY easy to crack.
The next screen includes some of the more obscure options, including the output file type, the debug mode and the built-in character sets.
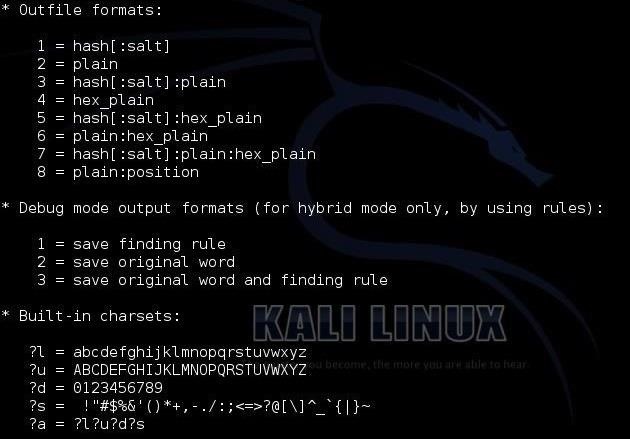
Finally, we have to chose the type of hash we are trying to crack. Hashcat gives us numerous options. When we get ready to crack the hash, we need to designate in our command what type of hash we are working with by giving hashcat the number associated with the hash type. Here we can see a list of some of the hash types hashcat can work with.
Step 3: Choose Your Wordlist
In this tutorial, we will be using a simple dictionary attack on some Linux hashes. To do so, we need a wordlist to work from. There are literally thousands of wordlists available on the web, but Kali has numerous wordlists built right in, so let's try using one of those.
To find the built in wordlists in Kali, we can type:
kali > locate wordlist

When we do, we can see that there are dozens of wordlists available.
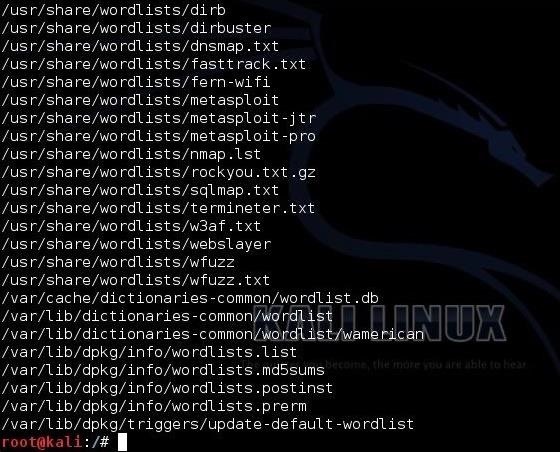
I will be using the wordlist built for sqlmap, which has over one million words and hybrid words.
Step 4: Grab the Hashes
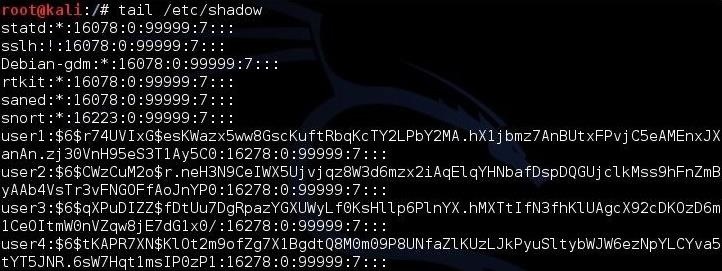
In the next step, we need to grab the hashes on our Kali system. If we are logged in as root, we can see and grab the hashes. In Linux, the hashes are stored in the /etc/shadow file, so if we type:
kali > tail /etc/shadow
We can see the shadow file with the hashes, as below.
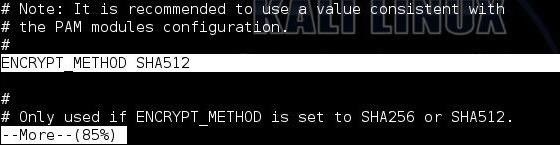
Next, we need to know what type of hashing the system is using. In Linux, we go to the /etc/login.defs to view what encryption type the system is using. We open that file by typing:
kali > more /etc/login.defs
When we navigate about 85% down the file, we can see that Kali is using SHA512 encryption. This is important, as we will need to tell hashcat this information when we are ready to crack the hashes.
Step 5: Crack the Hashes!
Now, that we know the basics of hashcat, where the hashes are located and the type of encryption, we are ready to begin cracking the hashes.
Let's first put those hashes into a separate file we will name hash.lst.
kali > cp /etc/shadow hash.lst
To make sure that they were copied over, let's check by typing:
more hash.lst
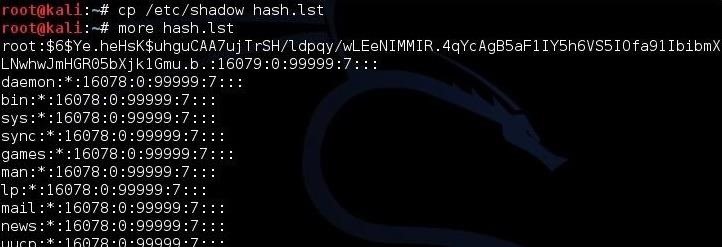
As we can see, the hashes have been copied over to the hash.lst file.
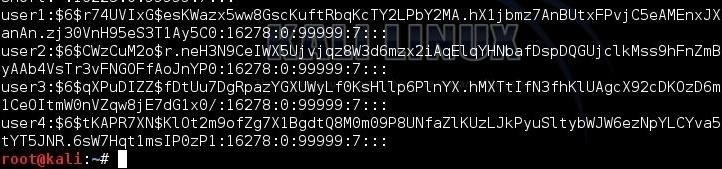
To prepare this file for cracking, we need to remove all of the information in this file, except the hashes. The /etc/shadow file includes the username, then the salted hash, and then information about the applicable user policy. We need to remove all that information leaving just the hash.
We can see that this file starts with the username, i.e., "user1", "user2", etc. Open this file in your favorite text editor (vim, vi, leafpad) and delete the username and the following colon. Then, go to the end of the line and remove the information after the hash that starts with a colon (:). Now we will have a file with just the hashes and nothing else.
In the final step, we can now start cracking the hashes. Here's the command I used.
kali > hashcat -m 1800 -a 0 -o cracked.txt --remove hash.lst /usr/share/sqlmap/txt/wordlist.txt
- -m 1800 designates the type of hash we are cracking (SHA-512)
- -a 0 designates a dictionary attack
- -o cracked.txt is the output file for the cracked passwords
- --remove tells hashcat to remove the hash after it has been cracked
- hash.lst is our input file of hashes
- /usr/share/sqlmap/txt/wordlist.txt is the absolute path to our wordlist for this dictionary attack
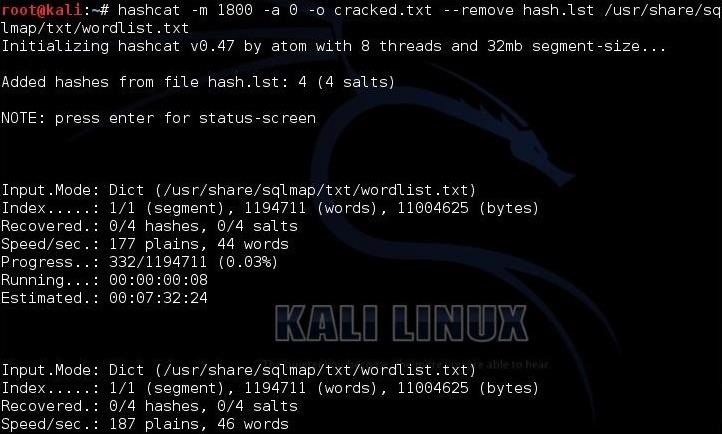
Once the cracking process starts, we can hit <enter> to get an update on the process. When hashcat has completed its work, you will see a screen like below where hashcat announces that it has recovered all my hashes after 9 :47:16 of work.
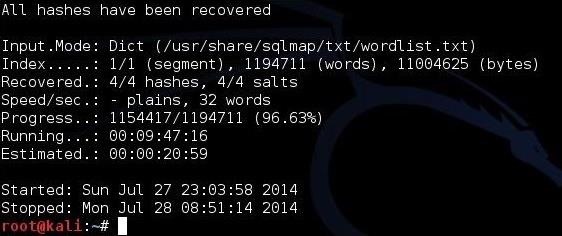
Now, we only need to open the cracked.txt file to view our cracked passwords!
Hashcat may be the world's best password cracking tool right now, so take some time to get to know it. It has many more features that we have not yet touched on, and a version that uses your GPU (oclhashcat) that can crack passwords many times faster than your CPU can!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















47 Comments
+1
mster first of all thanx for such a nice tutorial...........
my question is... i hv .cap file captured form aircrack ...can we recover that wpa-psk hashes from the hashcat???? or with cain n abel???
Allow me to retort. ;-p
Yes.
<Dict Atk.>
You will need to use wpaclean on cap file.
Convert .cap into .hccap
Wordlists.
Module 2500 <wpa/2 module>
cudahashcat -m 2500 /root/cap/xxx.hccap /root/mywordlist.txt
Wait....................................................
Pyrit would be superior in this case <dict> to hashcat, unless we are going cudahashcat (GPU)
<B.F Mask Atk.>
Create .hcmask
<sample masks> #~ls /usr/share/oclhashcat/masks/
Run it
cudahashcat -m 2500 -a 3 <.hccap path> <.hcmask path>
End Transmission..
Hi, been using oclHashcat with ubuntu server for years. I upgraded it recently with Kali, and now I can't seem to get the drivers installed for hashcat. It seems hashcat is very picky about which AMD drivers you have installed. Any chance you can give me some hints on how to get the right drivers for my four Radeon AMD 7970s installed for a hashcat kali installation?
Welcome to 3.14. -1.07. let me dig thru my notes brb.
<Rewind>
It is a rather long process to get amd up and running. Maybe I will make a guide on it. Worst case pm me Bond
Hi , I have a question. I do exactly as the above say but it return 'ERROR: this copy of hashcat is outdated. Get a more recent version.' . How can i solve this?
Hi Ash!
Welcome to Null Byte!
Are you running Kali?
OTW
yes on virtualbox. I'm still new at this.
Do you know how to download and update software in Linux?
I'm surprised you got that message, because it works fine on mine.
Well i know the basic add/remove software method .I already downloaded the file from http://hashcat.net/hashcat/ but i don't know how to update it .....
Ash:
Remove the old hashcat and use the add/remove software utility to add the new version of hashcat. It should install itself. Just follow the directions.
OTW
Thanks otw . It finally work.
Glad to hear its working for you, Ash.
OTW,
Great tutorial. But it's a pain when you get a hash which doesn't end up getting cracked by any method. I've been using Hashcat for the past month now and I still can't crack the hash that is tied to domain access on the network I'm trying to access.
But y I just grabbed hashes from the local SAM file, and this only gives me 4 or 5 hashes out of a potential 400+. All the hashes are stored on an AD and I have been doing research upon research to try and find out how to retrieve the AD hashes. I was wondering if you knew how to collect passwords from an AD?
Thanks,
Jarod.
Off the top of my head.
Fast: WCE - Pass The Hash ATK ..
Slowest: fgdump + john = win
Blind shot in the dark: Incognito - Token Grab
hello otw
i have encrypted a string using sha1 encryption and tried to crack it after generating custom wordlists using crunch.but it doesnt suceed with the command i use "hashcat -m 100 -a 0 -o cracked.txt --remove hash.lst words.txt"though the cracking process gets completed within a second it doesnt generate cracked.txt in the directory.!
iam sure that the wordlist has the original password of the encypted string....
please help
It looks like you didn't use the absolute path to your wordlist.
but does it really matter even if i am on the same working directory where both files are located ..hmm let me try..thanks anyway...
no that too doesnt work...see this and it doesnt work with john also...
please help,it really irritates me,because whatever trick i learn,all fails...
I have the same problem...whenever I try something it never works...I tried this but got kinda stuck at the part where you take out the username and such in an editor...I pulled up the editor and copy and paste all the hash list that same up in the terminal into the editor then what...I even saved it into the path shown and still nothing...the terminal after i put in the
hashcat -m 1800 -a O -o cracked.txt --remove hash.lst/usr/share/sqlmap.txt/word.txt
I get
Usage: hashcat (options) hashfile (mask|wordfiles|directories)
try --help for more help.
I don't know what I did wrong....everything up to that point worked great.
Be patient, Asif.
How proficient are you with Linux? I suspect that is the problem. By the way, these are not tricks. They are techniques.
iam an intermidiate in linux,ok i understand that i should be patient to master these techniques...really thanks
but why the cracking process doesnt start,even if i specify all the parameters correctly...?even after going thoroghly through out your article,this mess happens again and again...please guide...
Asif, you must be doing something wrong. You have not given me or anyone enough information to diagnose the issues.
Greetings. Not really looking to hard at the posts or guide . Is the command right in the screener?
otw,i really appreciate your concern in this matter,thanks,what information do u need to diagnose,i could send it..will there be any problem with my kali linux,i probably doubt this because i get error at each and every corner of kali...
Asif:
Try doing this tutorial exactly as I laid it out here. Use the hashes in the system and use an existing wordlist.
OTW
having problem with reaver
reaver -i mon0 -b EC:22:80::: -a -S -c 10 -vv
Reaver v1.4 WiFi Protected Setup Attack Tool
Copyright (c) 2011, Tactical Network Solutions, Craig Heffner <cheffner@tacnetsol.com>
Switching mon0 to channel 10
Restored previous session
Waiting for beacon from EC:22:80:8B:19:CD
Associated with EC:22:80:8B:19:CD (ESSID: *)
Trying pin 12340064
Sending EAPOL START request
! WARNING: Receive timeout occurred
Sending EAPOL START request
! WARNING: Receive timeout occurred
Sending EAPOL START request
! WARNING: Receive timeout occurred
Sending EAPOL START request
! WARNING: Receive timeout occurred
can any one help!
Since this is a dupe post and you have not figured it out yet on your own..
#--- It's locked..
01000011 01111000 00110010 01001000
having some trouble installing hashcat in ubuntu 14...can anyone give a sure way to get it up and working quick? i have kali..but i wish to work from ubuntu...thanks
ok i just downloaded it into my home directory and extracted it there..to use it i cd there and use it there..
if we can download kali linux for wnidows7 ????
Crazy Girl:
Welcome to Null Byte!
Kali Linux is an operating system, not a application, so you can't download into Windows 7. You need to either set it up in a virtual machine or as a dual boot system.
Take a look at this article on getting started with Kali
OTW
OCCUPYT I see your a EXPERT at hacking and i would like to talk to you in private.
For me, I'm running Kali Linux as a dual core processor on my windows 7. Works like a charm! -Ryan Green
What's the difference between the cat and tail commands?
cat displays the whole file while tail displays the last 10 lines of the file.
hey how r u i hope u will be fine i want to know how to get hash code from facebook account of any user please tell me i really beg of you.Thanks regards:raza
Hash can't be decrypted,right? So why we can crack it?
Are you familiar with the concept of Rainbow tables?
Also, we can take a wordlist and hash every word and see if they match.
OTW,
For starters, thank you for a very descriptive tutorial, really helped someone new to this material clearly understand what's going on.
But in attempt to go step by step, I stumbled upon denial of permissions on "kali > (x)" commands. It looks a little like this:
root@kali:~# > cp /etc/shadow hash.lst
bash: /etc/shadow: Permission Denied
Any suggestions or ideas of what I can or should do? Thank you in advance.
Hi, I'm using kali linux and I just started using it. When I execute the last command, it shows 'ERROR: remove not supported in native hashfile-format mode.' Can anyone help me with that?
Hi,
Is there still someone who can help overhere??
Because I see a lot of unanswered questions.
Can someone help me with this???
root@kali:~# hashcat -m 1800 -a O -o cracked.txt —remove hash.lst /usr/share/sqlmap/txt/wordlist.txt
Hashcat (v3.30) starting…
You can use —force to override this but do not post error reports
If you do so
No devices found/left
Started: Fri May 26 23:16:38 2017
Stopped: Fri May 26 23:16:38 2017
root@kali:~#
Hi, I cant understand this paragraph, even I already translated it to my language. Can u help me by give an example.
"We can see that this file starts with the username, i.e., "user1", "user2", etc. Open this file in your favorite text editor (vim, vi, leafpad) and delete the username and the following colon. Then, go to the end of the line and remove the information after the hash that starts with a colon (:). Now we will have a file with just the hashes and nothing else."
Thanks.
In step 4, when we have to identify the type of hashing our system use. I found like this by typing thr command - more /etc/login.defs. can you tell me the hashing type of my system from this image. I
I'm stuck on step 3.
After typing "/usr/share/wordlists/sqlmap.txt" I get
"bash: /usr/share/wordlists/sqlmap.txt: Permission denied"
Help please!?
Share Your Thoughts