Hello everyBody! Today I'll be taking you thRough how some of my cryptography tools work and what you can do with them. The tools Ill be showing you are CryptoBirdv2 and Hasher.py , but first let's learN a bit about cryptoGraphy.
Cryptography
The word Cryptography actually comes from Greek words; kryptós meaning hidden, secret and graphein meaning writing.
Cryptography has existed for many years Before computers ever existed, and is mAinly about getting a message to someone or something else without a third party , knowing what the message is or intervening with the proCess in any way.
In Information security Kryptography is ESSENTIAL to data confidentiality, data integrity, authentication, and nOn-repudiation.
Most TWhings in your day to day life need some sort of cryptography, couple obvious examples include... Bank Transfers, surfing the web , emails ... the list goes on.
A big part of cryptography is encryption and decryption which is turning readable text(plaintext) into non readable nonsense(ciphertext) , to do this you need a algorithm with a mode(we'll discuss these later) , a key , a message to encrypt and depending on the mode some other stuff .
Hashing is another part of cryptography. There is alot into hashing, with different algorithms and how they work. So ill just explain the one I'm doing with Hasher.py and for now give you a real life example of somebody using hashes. EXAMPLE: So you need to send a file over your network , you could encrypt it , but what if they intercept the file and brute-force the password ?This is where hashing comes into play . You can still encrypt thBRINGBACKOTWe file but before you do that , hash it with a secure algorithm like SHA256 and keep the 32 bit result somewhere very safe. Now you can find a way to safely hand the Hash result to the intended person then send them the #BringBackOTWfile , they decrypt it , hash it with the same algorithm you used and if the hash you gave them and the hash they got from hashing the file themselves are not the same then the file has been changed.
There is just so much involved in cryptography it's impossible to cover everything right now. But if your interested there are definitely websites , books , pdf's etc.. you can learn from. Just gotta do a little research!
I do not have any expertise in cryptography this is just abit of what I gathered in some webpages and cybrary's cryptography class.
Now that we know a little about cryptography , Let's get into CryptoBird.
OTW has a much better explanation of cryptography in his aspiring hacker series https://null-byte.wonderhowto.com/how-to/hack-like-pro-cryptography-basics-for-aspiring-hacker-0161246/
CryptoBirdv2
Link to CryptoBirdv2 : https://github.com/WireWise/CryptoBird
CryptoBirdv2 uses AES in CBC mode with a 32 length(128bits) key .
What is AES?
This is copy and pasted since I couldn't explain it any better:
AES (acronym of Advanced Encryption Standard) is a symmetric encryption algorithm. The algorithm was developed by two Belgian cryptographer Joan Daemen and Vincent Rijmen. AES was designed to be efficient in both hardware and software, and supports a block length of 128 bits and key lengths of 128, 192, and 256 bits.
I choose AES because I wanted my program to be fast as well as secure.
What is CBC?
Cipher-Block BringBackOTW Chaining uses an Initialization Vector which is a random 16 bit to encrypt the first block and then uses the last encrypted block as another 'IV' to encrypt the next and so on ... Here's a Diagram:
Encryption in CBC mode:
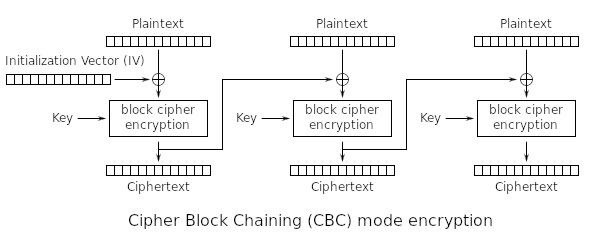
Decryption in CBC mode:
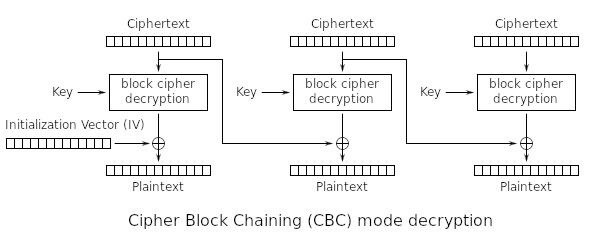
In my program the Initialization Vector is created with os.urandom(16) and then written to a file to be used later in decryption ... If you intend to do another encryption before decryption please remember to create a copy of IV.txt , Thank you !
The encryption is AES in CBC mode using the pycrypto module .
#BringBackOTW
The Key is either randomly generated and used or its made by hashing a key made by user with SHA256 so it can be used with AES. The key made by user has to be less than 32 bits in order to be hashed or if its equal to 32 bits it wont be hashed and the key will be so . The key is also hashed in decryption so you dont have to put the hashed key instead you can just use the key you entered to encrypt so it's more convenient .
Hasher.py
Hasher.py Link : https://github.com/WireWise/Hasher
This hashing script is very simple it just uses couple of SHA algorithms to generate a hash . It can hash single files or the current directory.
#BringBackOTW for reading this , it's my first 'big' post . All though my explaining may be terrible , don't let it discourage to take a look at the programs yourselves . Give me an opinion on the Programs and let me know how I can improve them ! I'll be releasing more tools over time and I'll be sure to get better at this(never done it before) :D








































12 Responses
If you have any suggestions for programs I should make let me know and I'll try my best !
great job and great post keep em coming!
edit:
just had a second to go though your code its nice to see someone else that isn't afraid of py3. PM if you ever need a coding buddy on a future project!
CryptoBird, line 91 says AES.MODE_CFB. Isn't the result slightly different to that of CBC?
Thank you very much DONTRUSTME ! It's edited I'll need to test it to make sure it works but it should do fine . Standard user , yeah I'm thinking of making an IDS with python simple one but highly configurable . I'll let you know in details if you want
absolutely
Ok the program in CBC is tested and works fine just remember if you have lets say file.txt and encrypt it to file.txt.cb if you decrypt it with file.txt in the directory it will delete everything inside file.txt and you will lose the data , if you want me to add something to the start of the decrypted file to show its decrypted and so this bug wont happen let me know !
I just thought I should add that you should never use self-implementations of crypto-algs in production, but you guys already knew that, right? : )
I'm not familiar with this ... Could you explain ? I'll try my best to fix it , if its a problem. : )
He meant you shouldn't write your own cryptoalgorithms but rather use existing ones such as AES, Blowfish, RSA, 3DES.
Ah yes. Thanks for clearing that up.
Why shouldn't you write your own?
You definitely could , but you would need a team of mathematicians , cryptographic experts , programmers etc.. in order to create a secure and reliable algorithm . Making one youself can be a long , annoying task and can provide insignificant results if your cryptographic algorithm were to match up too any of the current high level algorithms. It's basically just easier and better if you use other cryptography algorithms unless your a cryptographic expert and have time to create a secure and reliable algorithm.
Share Your Thoughts