A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.
Dnstwist, created by @elceef, is a domain name permutation search tool which detects phishing domains, bitsquatting, typosquatting, and fraudulent websites which share similar-looking domain names. Dnstwist takes the given target domain name and generates a list of potential phishing domains. The generated domain names are then queried. If a discovered domain redirects to a web server, Dnstwist will record the domain's IP address.
Like most tools designed for penetration testing, Dnstwist is a double-edged sword. It can be used by attackers to find ideal candidate domains for phishing attacks where they could clone the original website and get users to input their credentials into a fake website, or it can be used by cybersecurity professionals and sysadmins to quickly locate and identify domains created by adversaries and attackers.
- Don't Miss: How to Clone Any Website Using HTTrack
Supported Naming Schemes
Dsntwist supports a variety of phishing domain schemes and types which are used to generate a vast selection of potential phishing domains. I'll cover each below before jumping right into the how-to.
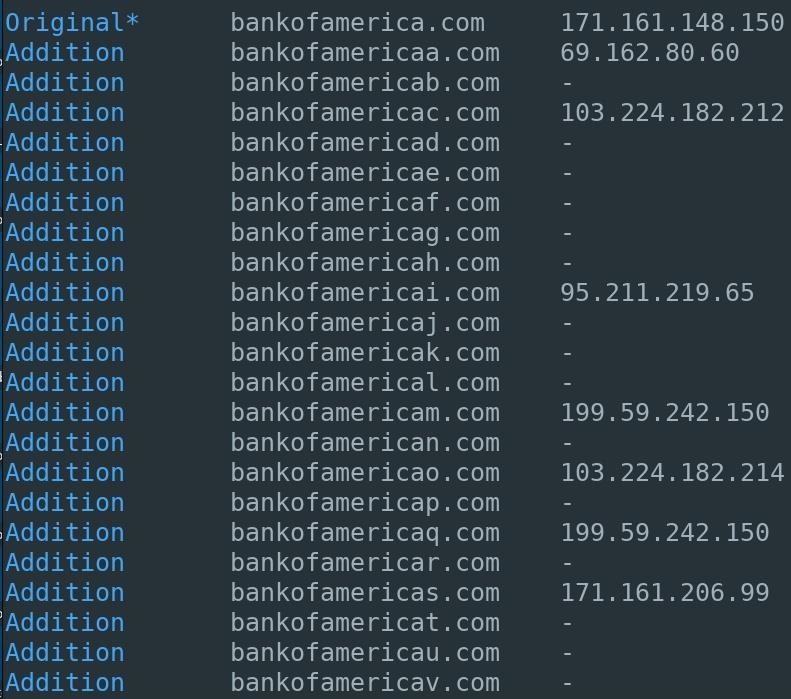
1. Addition
Letters are appended to the end of the given domain name. Below is an example of Bank of America, one of the largest banks in the United States. Unlike some of the other options below, a simple addition is easy enough to spot by an end user if he or she just glances at the URL.
2. Bitsquatting
Bitsquatting refers to the registration of a domain names 1-bit different from a legitimate domain. Below is an example for Wikipedia, the largest and most popular general reference website on the internet. This is a little trickier on the eyes than the "additions" above since a lot of people read words based on the first and last letter and don't look at every letter individually.
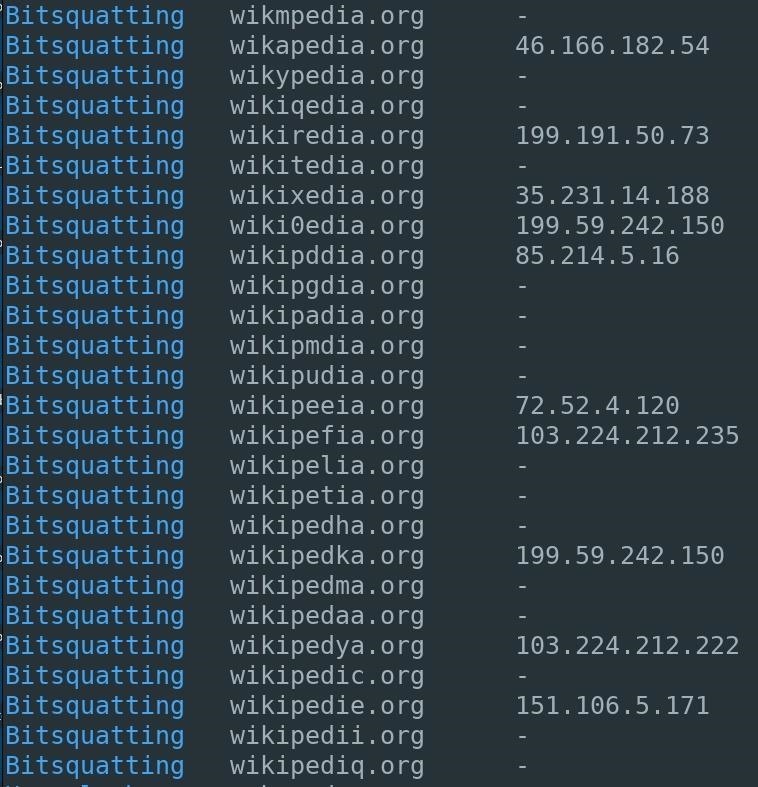
3. Homoglyph
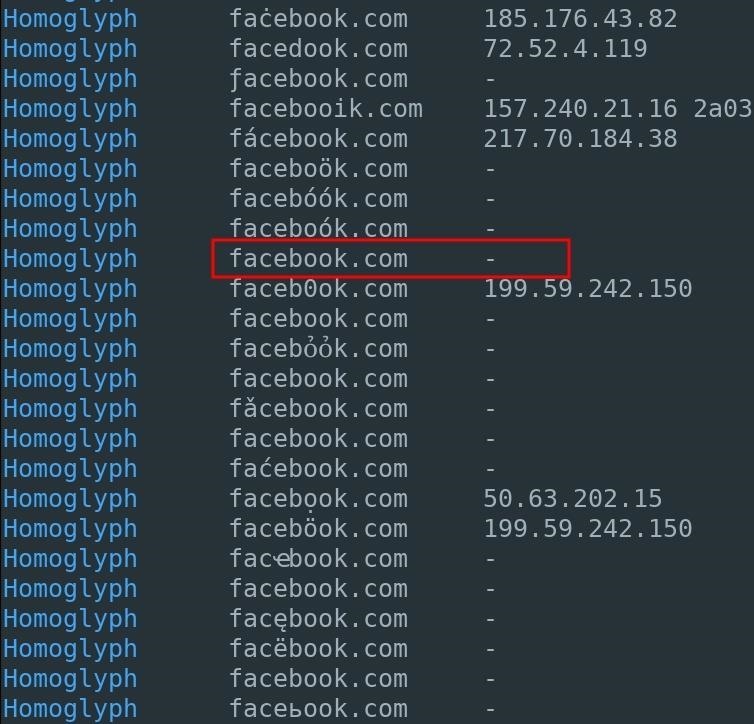
Phishing campaigns using homoglyphs are referred to as homograph attacks, even though the alternative characters are referred to as homoglyphs and not homographs. These type of attacks still affect Firefox and most Android devices, and were recently made famous by Xudong Zheng, who created the first homoglyph phishing address for apple.com. Using Facebook as an example, I found there were many homoglyph phishing domains still available for as little as $11.
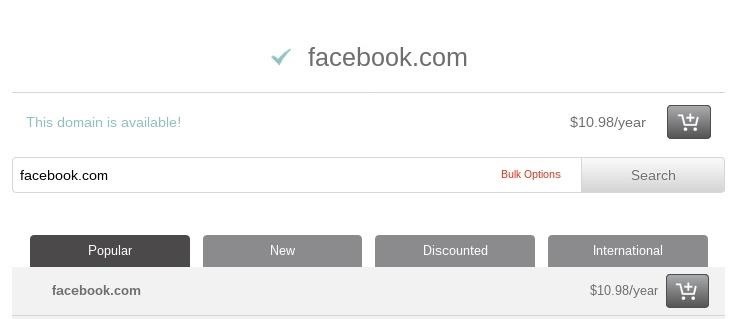
To check the discovered domain name against a domain registrar, copy and paste the domain from the Dnstwist terminal into the registrar's search bar.
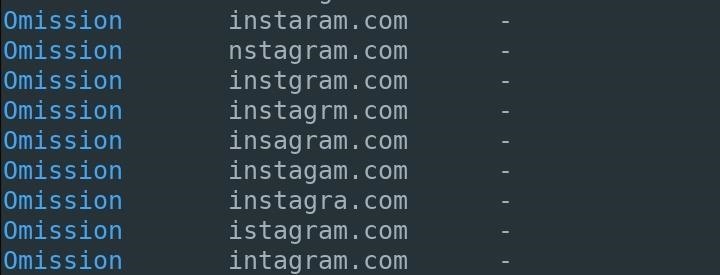
4. Omission
Letters are simply removed from the domain name. To my surprise, all of the Instagram domain names were listed as available. While someone will probably notice if the first or last letter in the domain name is missing, they might not notice one in the middle gone.
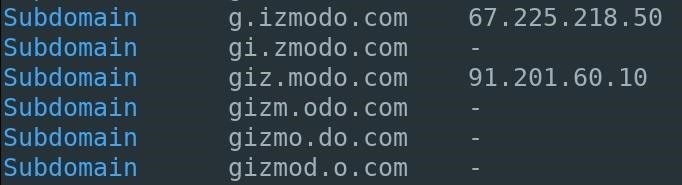
5. Subdomain
A period inserted at varying positions in the given domain name. Using Gizmodo as an example, we can see the domains "odo.com" and "zmodo.com" are available. It's just a matter of creating convincing subdomains to make an effective phishing domain. Like "additions," this might be more obvious than the other tricks here.
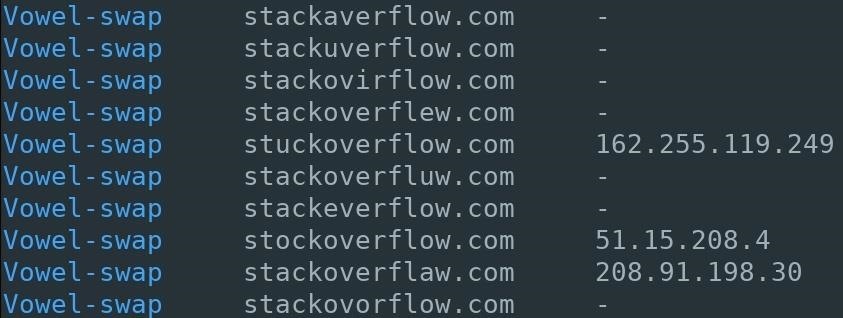
6. Vowel-Swap
Vowels found in the given domain are swapped for different vowels. At a glance, many of these domains will likely fool most victims into clicking on fraudulent links. Again, this works since most people scan words using the first and last letter, not necessarily every letter in the middle. If a replaced vowel is the first or last letter, it probably won't work as well.
Now that you know all of the tricks Dnstwist can use to find used and available phishing domains, let's see how to actually use the tool.
Step 1: Set Up Dnstwist
Dnstwist relies on several Python dependencies which can be installed in Kali Linux by typing the below command into a terminal.
apt-get install python-dnspython python-geoip python-whois python-requests python-ssdeep python-cffi
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following additional packages will be installed:
libfuzzy2 python-certifi python-openssl-python-ply python-pycparser python-simplejson python-urllib3 whois
Suggested packages:
python-openssl-doc python-openssl-dbg python-ply-doc python-socks python-ntlm
The following NEW packages will be installed:
libfuzzy2 python-certifi python-cffi python-dnspython python-geoip python-openssl python-ply python-pycparser python-requests python-simplejson python-ssdeep python-urllib3 python-whois whois
0 upgraded, 14 newly installed, 0 to remove and 164 not upgraded
Need to get 778 kB/893 kB of archives
After this operation, 3,842 kB of additional disk space will be used.
Do you want to continue [Y/n] yNext, clone the Dnstwist GitHub repository.
git clone https://github.com/elceef/dnstwist
Cloning into 'dnstwist'...
remote: Counting objects: 670, done.
remote: Total 670 (delta 0), reused 1 (deltaa 0), pack-reused 669
Receieving objects: 100% (670/670), 3.18 MiB | 89.00 KiB/s, done.
Resolving deltas: 100% (352/352), done.Finally, use the cd command to change into the newly create "dnstwist" directory and use the command underneath it to view the available options.
cd dnstwist/
./dnstwist.py --help
usage: ./dnstwist.py [OPTION]... DOMAIN
Find similar-looking domain names that adversaries can use to attack you. Can detect typosquatters, phishing attacks, fraud and corporate espionage. Useful as an additional source of targeted threat intelligence.
positional arguments:
domain domain name or URL to check
optional arguments:
-h, --help show this help message and exit
-a, --all show all DNS records
-b, -banners determine HTTP and SMTP service banners
-c, --csv print output in CSV format
-d FILE, --dictionary FILE generate additional domains using dictionary FILE
-g, --geoip perform lookup for GeoIP location
-j, --json print output in JSON format
-m, --mxcheck check if MX host can be used to intercept e-mails
-r, --registered show only registered domain names
-s, --ssdeep fetch web pages and compare their fuzzy hashes to evaluate similarity
-t NUMBER, --threads NUMBER start specified NUMBER of threads (default: 10)
-w, --whois perform lookup for WHOIS creation/update time (slow)Step 2: Generate Phishing Domains with Dnstwist
To start generating phishing domains with Dnstwist, use the below command. There are several arguments being utilized in my example command, and in this case, since we're saving the results to a file, we won't see any results on the screen.
- Don't Miss: Easily Detect CVEs with Nmap Scripts
./dnstwist.py --ssdeep --json --threads 40 website.com > website.com.json- The --ssdeep argument instructs Dnstwist to analyze the HTML found on each domain and compare it to the HTML of the given (real) website. The level of similarity will be expressed as a percentage. However, each website should be inspected manually regardless of the percentage level issued by Dnstwist. These percentages are merely there to aid security professionals in identifying which domains are most likely to be phishing domains.
- Dnstwist supports two output formats which can be used with other applications. The --json output format was used in my above example but there's also support for CSV outputs which can be enabled using the --cvs argument instead of the JSON format. To save either format to a file, the > filename redirect can be used to write the data to a given filename.
- By default, Dnstwist will make only 10 requests at a time when enumerating available phishing domains. This number can be increased or decreased using the --threads argument and specifying a value.
If you want to see results on the screen and not write them to a file, you can use the below command, swapping out "facebook.com" with the domain you want. A progress bar will print at the bottom of the Dnstwist terminal. Depending on network speed and number of threads, this can take several minutes to complete.
./dnstwist.py --ssdeep --threads 40 facebook.com
_ _ _ _
__| |_ __ ___| |___ _(_)___| |_
/ _` | '_ \/ __| __\ \ /\ / / / __| __|
| (_| | | | \__ \ |_ \ V V /| \__ \ |_
\__,_|_| |_|___/\__| \_/\_/ |_|___/\__| {1.04b}
Fetching content from: https://facebook.com ... 200 OK (541.4 Kbytes)
Processing 284 domain variants ...22%..42%...63%...88%. 210 hits (73%)Always Pay Close Attention the Domain Names
As an attacker preparing to perform a phishing campaign during a red team engagement or a sysadmin preparing to defend against such attacks, Dnstwist is a fantastic tool which can be used to enumerate viable domains likely to be used for nefarious purposes. Dnstwist offers several key advantages over similar tools such as the ability to analyze and compare HTML of potential phishing domains, support for different output formats, and a wide variety of generated phishing domains.
If you're just a regular end user visiting a website, pay extra close attention to the URL when you get there. While homoglyphs might be impossible to spot, the rest of these can be easily noticed if you spend more than a glance looking at them.
Hope you enjoyed this article on generating and detecting phishing domains with Dnstwist. Leave questions and comments below or message me on Twitter @tokyoneon_ if you need further explanation on any of this.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























1 Comment
Nice... this is both interesting and scary, but kudos to you!
Share Your Thoughts