This article is a quick, comprehensive guide on setting up your newly installed KaliLinux2.0 (very attractive new GUI by the way) for secure encrypted browsing. Following this guide will enable you to "surf the web" with your back covered (like a pro) safe from prying eyes (GCHQ cough, NSA cough cough) packet sniffing and MITM attacks.
Find out more here: How To Transparently Route Traffic Through Tor. It will give you total anonymity to your Internet sessions.
Dependencies:
ssh server
gnome session manager
Step 1: Utilize an SSH Server
# service ssh start
SSH provides a secure environment through encryption, enabling you to tunnel your traffic and transfer a variant of files privately. Directing your network traffic through an SSH tunnel will encrypt the packets, rendering any captured packets unreadable.
Step 2: Install Gstm (Gnome SSH Tunnel Manager)
# apt-get -y install gstm
Installing gstm is easy, it already exists in the kali repository, copy and pasting the above code should be sufficient.
Step 3: Configure Gstm (Gnome SSH Tunnel Manager)
Configure to match the configurations in below screenshot.
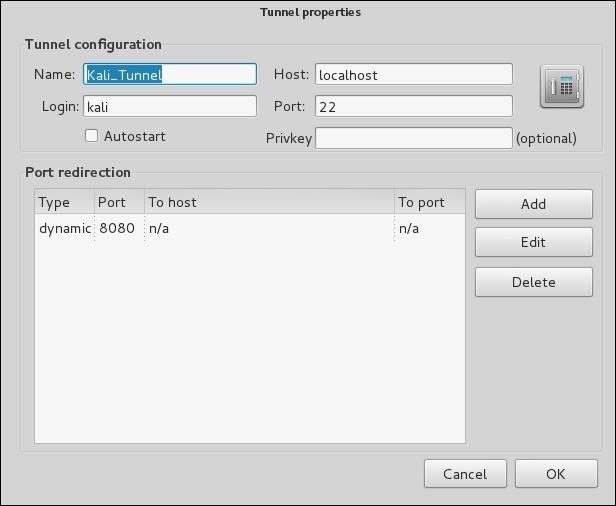
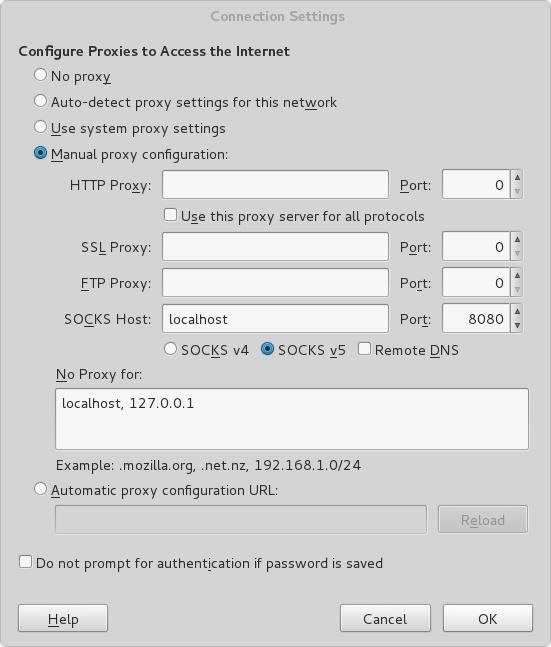
SOCKS (Socket secure) proxy enables the routing of network packets through a proxy server (local socks port 8080), thwarting MITM attacks.
Here You Will See the Tunnel You Named in the Previous Step. The Case Kali__Tunnel.
Step 4: Start the Kali Tunnel session
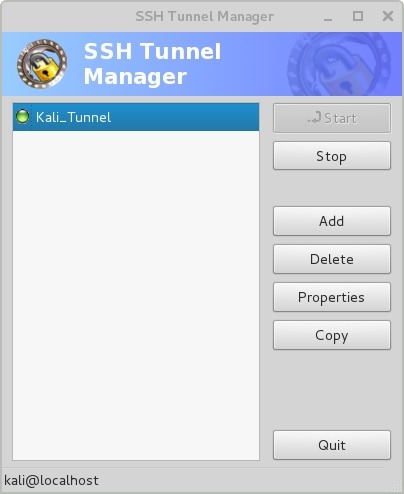
Step 4: Configure Your Browser to Match the Screenshot Below.
Step 5: Optional. For Testing Purpose Only
To confirm that you browser sessions are encrypted. Start a wireshark session. Capture the loopback/lo interface. Note your traffic is now encrypted via the SSH protocol.
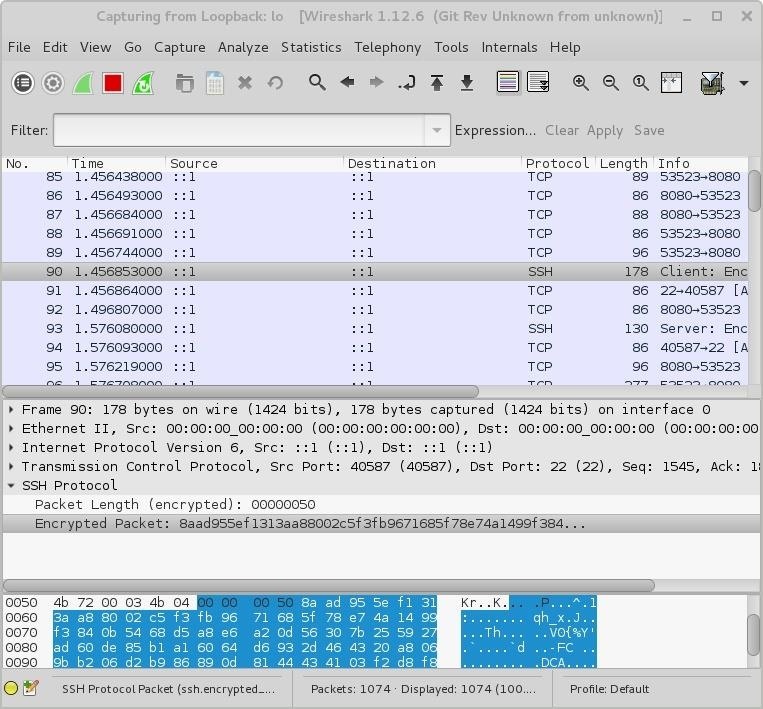
Observe the SSH highlighted session. Now all browser traffic is encrypted.
Feel free to ask any questions in the comments section of this page.
Written by Eli Ausi
31/08/2015









































13 Responses
Great post Eli Ausi. Pretty cool technique.
Thank You! :D
Good post!
Thanks for the kind words! :D
Can you explain what happens to the traffic after it hits the tunnel? Correct me if I'm missing something, but since you're running it locally, it seems as though this creates an encrypted tunnel between your local browser and your local proxy, where it is then decrypted again before going on out across the internet. You'd have to wireshark outbound http packets to see if it's truly working. Or is there some step I'm misunderstanding that tunnels it through tor?
It's not going through tor or doing any outbound encryption, as I understand. Outbound is still un-encrypted to it's destination. The post mention to see another article for routing through the tor network for total anonymity.
Right. Useful way to set up, say, a cloud vm as a secure proxy for when browsing over an open/public wifi network... but traffic from there on out would still be sent in the clear where any gov't (or otherwise) sniffers could scoop it up.
I'm a little confused by this. If it doesn't encrypt outbound traffic, what exactly is this for? What's a good use case? Are you encrypted until you enter tor(assuming you've set that up)?
Doing this locally is pointless other than getting a proof of concept up. However once you configure this on a machine, you can use that machine's public IP when configuring a 2nd (presumably remote) machine's browser's proxy, you will essentially send your web traffic safely encrypted over the internet to the first machine before it goes back out on the web. Useful for if you travel and use unencrypted wifi, but trust the safety of your first machine's network (which would become the exit point).
Ok, I get it now. Thanks. And thanks for the post Eli Ausi
Thanks ENERGY WOLF. I think my explanation was maybe not as clear as id have hoped. Thanks for the kind words. :D
Thanks Bryan! Totally me being backwards there, you know when you look at the same thing for too long you stop seeing it.
the comment at the top about tor is a link to another article and in step3 I was just wrong and I've now edited it because you bought it to my attention, so thanks for that. :D x
after configuring my browser's setting to manual proxy configuration my page fails to load....any help
Share Your Thoughts