So there's something about encryption I don't get. If hackers just use a wordlist translated to hashes in that encryption, how is AES safer than MD5? Does it make it sense what I'm asking?
Forum Thread: Encryption
- Hot
- Active
-
 Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
1 wk ago -
 Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies
Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies
3 wks ago -
 Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
3 wks ago -
 Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
2 mo ago -
 Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
2 mo ago -
 Metasploit Error:
Handler Failed to Bind
41
Replies
Metasploit Error:
Handler Failed to Bind
41
Replies
2 mo ago -
 Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
3 mo ago -
 How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
3 mo ago -
 How to:
Crack Instagram Passwords Using Instainsane
36
Replies
How to:
Crack Instagram Passwords Using Instainsane
36
Replies
3 mo ago -
 Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
3 mo ago -
 Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
3 mo ago -
 Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
4 mo ago -
 How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies
How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies
4 mo ago -
 Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies
Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies
5 mo ago -
 Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies
Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies
6 mo ago -
 Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies
Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies
6 mo ago -
 Forum Thread:
How to Hack School Website
11
Replies
Forum Thread:
How to Hack School Website
11
Replies
6 mo ago -
 Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies
Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies
6 mo ago -
 Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies
Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies
7 mo ago -
 Forum Thread:
Hacking with Ip Only Part [1] { by : Mohamed Ahmed }
5
Replies
Forum Thread:
Hacking with Ip Only Part [1] { by : Mohamed Ahmed }
5
Replies
8 mo ago
-
 How To:
Dox Anyone
How To:
Dox Anyone
-
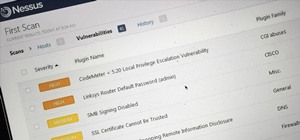 Hack Like a Pro:
How to Scan for Vulnerabilities with Nessus
Hack Like a Pro:
How to Scan for Vulnerabilities with Nessus
-
 How To:
Scan for Vulnerabilities on Any Website Using Nikto
How To:
Scan for Vulnerabilities on Any Website Using Nikto
-
 Hack Like a Pro:
Reconnaissance with Recon-Ng, Part 1 (Getting Started)
Hack Like a Pro:
Reconnaissance with Recon-Ng, Part 1 (Getting Started)
-
 How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
How To:
Crack Password-Protected Microsoft Office Files, Including Word Docs & Excel Spreadsheets
-
 How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
-
 How To:
Hack Coin-Operated Laudromat Machines for Free Wash & Dry Cycles
How To:
Hack Coin-Operated Laudromat Machines for Free Wash & Dry Cycles
-
 How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
-
 How To:
Phish for Social Media & Other Account Passwords with BlackEye
How To:
Phish for Social Media & Other Account Passwords with BlackEye
-
 How To:
Automate Wi-Fi Hacking with Wifite2
How To:
Automate Wi-Fi Hacking with Wifite2
-
 How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
-
 How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
-
 How To:
Stealthfully Sniff Wi-Fi Activity Without Connecting to a Target Router
How To:
Stealthfully Sniff Wi-Fi Activity Without Connecting to a Target Router
-
 How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
How To:
Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther
-
 How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
How To:
Gain Complete Control of Any Android Phone with the AhMyth RAT
-
 How To:
Obtain Valuable Data from Images Using Exif Extractors
How To:
Obtain Valuable Data from Images Using Exif Extractors
-
 How To:
Use Maltego to Target Company Email Addresses That May Be Vulnerable from Third-Party Breaches
How To:
Use Maltego to Target Company Email Addresses That May Be Vulnerable from Third-Party Breaches
-
 How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
-
 How To:
Exploit EternalBlue on Windows Server with Metasploit
How To:
Exploit EternalBlue on Windows Server with Metasploit
-
 How To:
Crack Shadow Hashes After Getting Root on a Linux System
How To:
Crack Shadow Hashes After Getting Root on a Linux System
















5 Responses
AES is an encryption standard, while MD5 is a digest function. You are comparing different things, If I understand your question.
Sorry, I thought they were both encryption (still new to this whole thing) what I mean is, why is one encryption better than another? Those two were just (supposed to be) examples.
Encryption algorithms are based on problem's intractability. If you can break an algorithm in 20000 years (with actual machines), it's considered a good algorithm. The unique unbreakable encryption is Vernam's algorithm (using a different key each time you encrypt) known as One Time Pad.
What I've understood is that hackers start off by using a wordlist. When you have a program that can translate a wordlist into hashes, then what makes one more secure than the other.
Eg. if the password is "password", and you have a wordlist that contains "password". Then you use aircrack-ng to translate it to hashes and compare it to the original. Does it take longer time to translate to some encryptions than others? Does it make any sense what I'm saying?
Of course not all algorithms take equal time.
Share Your Thoughts