As you all know by now, reconnaissance is an essential phase in hacking , it is important to know everything about your target before proceeding to exploitation.
Whether your target is a company,a group or an individual, experience proved that humans are the weakest link in the information security chain and emails are the keys to a box of information that can be your best bet to perform a successful hacking operation.
There are many ways to get a person's email address,from people search engines to checking social media bios , but most of the times these methods don't provide you with what you need.
An alternative way to get a person's email is by guessing it,yes... that's right! people tend to follow specific patterns when registering an email address like adding their year or day of birth after their names (ex:johndoe1997@example.com, john.d.97@example.com) and while guessing every single combination is time consuming , there can be a way to make things a lot faster and easier.
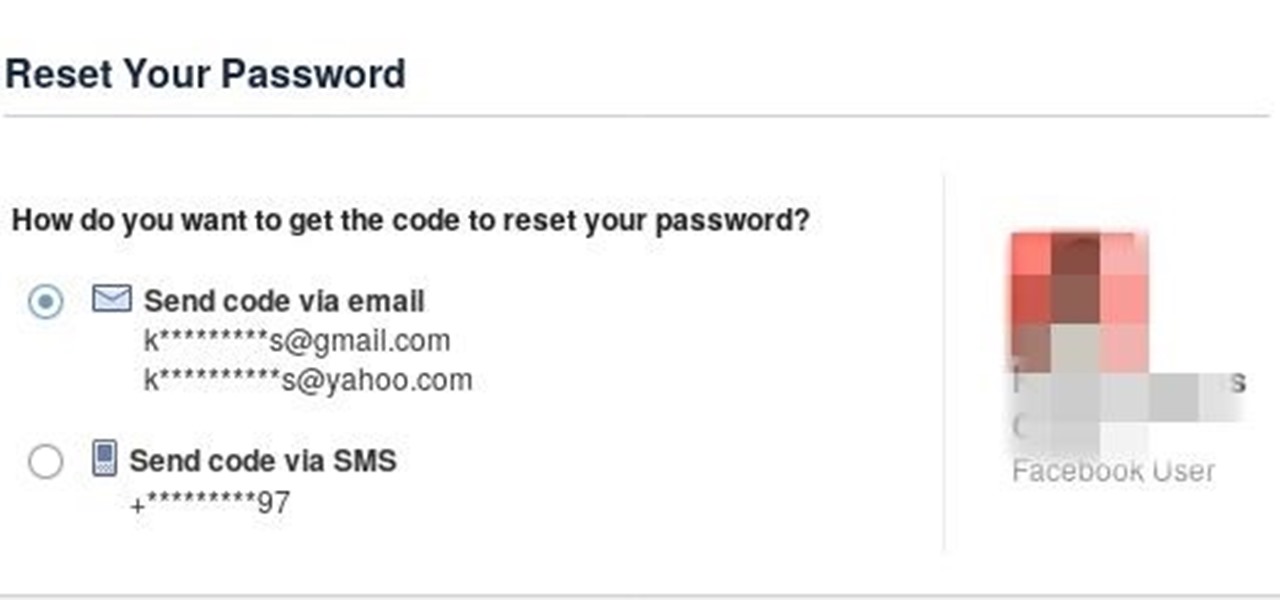
Social media like facebook,twitter and instagram provide a lot of information about people if you know where to look,by tapping the "forgot password" button and entering your targets username you will get censored email.
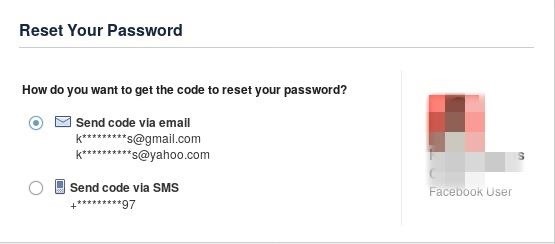
As you can see there is some very usefull information there like email providers,first and last letters and the exact number of characters! ( PS: fb,insta and twitter give the right number of characters,others might not!)
Now by knowing this and knowing some info about a person(first name,middle,last and birthdate) we can easily guess the full email and this is where Buster comes to play.
How It Works ?
Buster will take the info you know about a person and will generate all the possible combinations that you can make with it,it will then compare it to the pattern you provided (ex: k****s@gmail.com) and make a list of all possible emails,then go through each email and check if it exists or not using different methods (smtp check,social media presence...)
When it finds an email it will perform OSINT tasks and return information about the email like:
• Social accounts
• breaches
• pastes
• domains registered
• links to where to email was found
Step 1: Installation
clone the repository:
$sudo git clone git://github.com/sham00n/buster
Once you have a copy of the source, you can install it with:
$ cd buster/
$ sudo python3 setup.py install
$ buster -h
Step 2: Finding an Email
Go to facebook and search for your target,tap on their profile and you should see their username or facebook id in the url
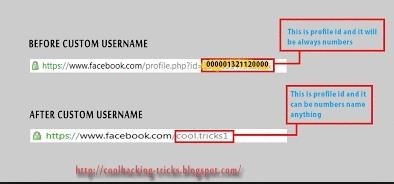
Log out of facebook and enter your target's username in the login box then press "forgot password" then copy the pattern.
Enter all the info to Buster and voila!
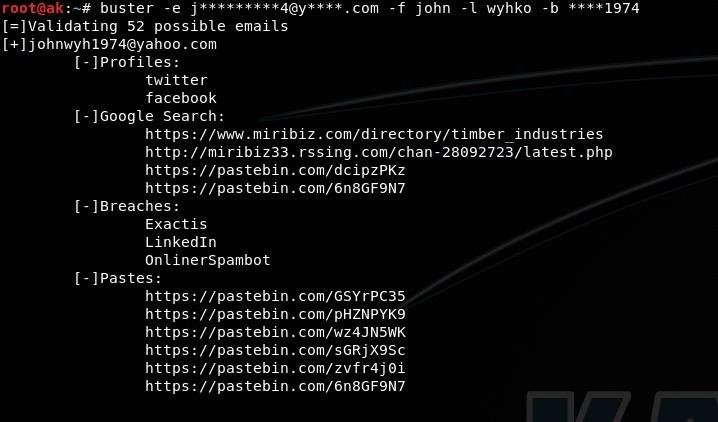
Here we can see a possible email behind the pattern alongside some very usefull info that can help you make sure that it belongs to the person of interest.
Alternatively,if you know the company they work for you can try:
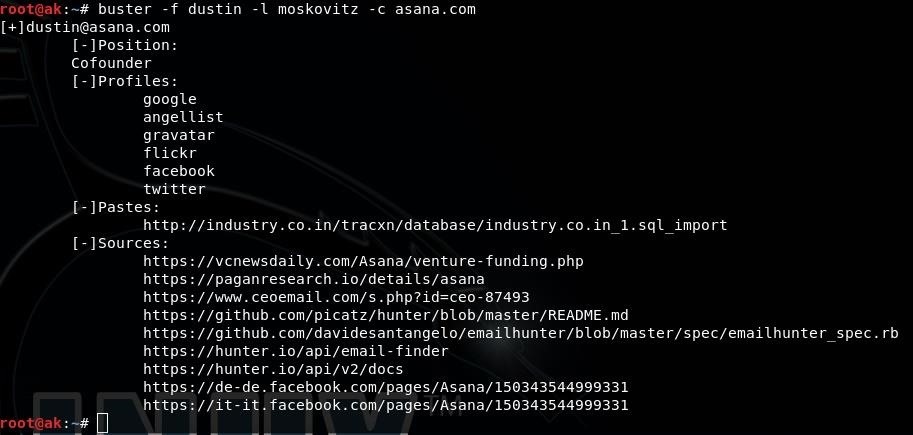
Step 3: Finding Emails from a Username
We managed to find the target's email in the previous step,lets try to see if he has more emails with the same username!
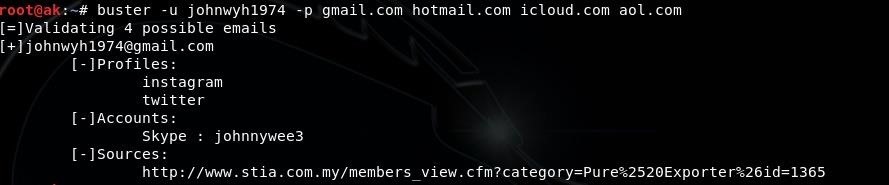
here we used the username found in the previous email alongside 4 popular email providers and we managed to find his gmail account.
There are a lot more things to do with buster like generating usernames,performing OSINT on a single email or a list...combine it with tools like theharvester,h8mail and sherlock to get as much info as you can about your target.







































1 Response
Thanks for sharing an alternative method for finding emails but in the first part you mentioned that we can guess the email address...so is there any surety level that these emails lead us to next step furthermore I am currently using some tools they give me surety of valid emails so I am confused should I use the alternative method?
Share Your Thoughts