Welcome back, my hacker novitiates!
In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.
Step 1: Open THC-Hydra
So, let's get started. Fire up Kali and open THC-Hydra from Applications -> Kali Linux -> Password Attacks -> Online Attacks -> hydra.
Step 2: Get the Web Form Parameters
To be able to hack web form usernames and passwords, we need to determine the parameters of the web form login page as well as how the form responds to bad/failed logins. The key parameters we must identify are the:
- IP Address of the website
- URL
- type of form
- field containing the username
- field containing the password
- failure message
We can identify each of these using a proxy such as Tamper Data or Burp Suite.
Step 3: Using Burp Suite
Although we can use any proxy to do the job, including Tamper Data, in this post we will use Burp Suite. You can open Burp Suite by going to Applications -> Kali Linux -> Web Applications -> Web Application Proxies -> burpsuite. When you do, you should see the opening screen like below.
Next, we will be attempting to crack the password on the Damn Vulnerable Web Application (DVWA). You can run it from the Metasploitable operating system (available at Rapid7) and then connecting to its login page, as I have here.
We need to enable the Proxy and Intercept on the Burp Suite like I have below. Make sure to click on the Proxy tab at the top and then Intercept on the second row of tabs. Make certain that the "Intercept is on."
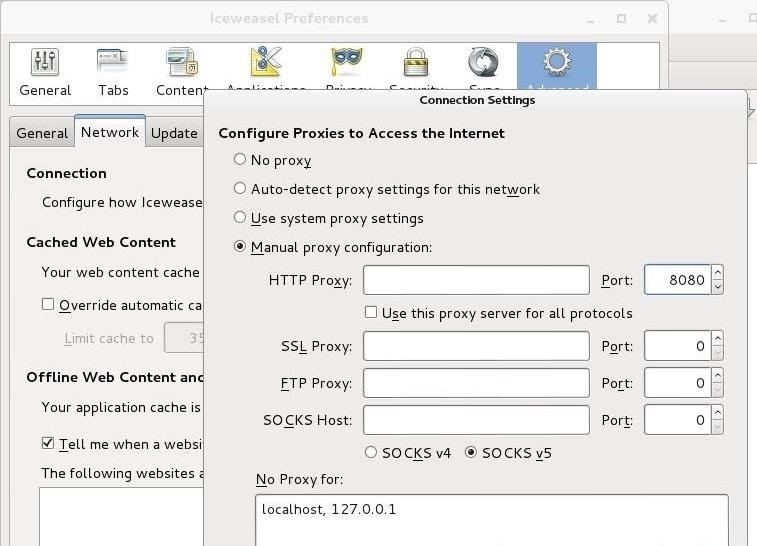
Last, we need to configure our IceWeasel web browser to use a proxy. We can go to Edit -> Preferences -> Advanced -> Network -> Settings to open the Connection Settings, as seen below. There, configure IceWeasel to use 127.0.0.1 port 8080 as a proxy by typing in 127.0.0.1 in the HTTP Proxy field, 8080 in the Port field and delete any information in the No Proxy for field at the bottom. Also, select the "Use this proxy server for all protocols" button.
Step 4: Get the Bad Login Response
Now, let's try to log in with my username OTW and password OTW. When I do so, the BurpSuite intercepts the request and shows us the key fields we need for a THC-Hydra web form crack.
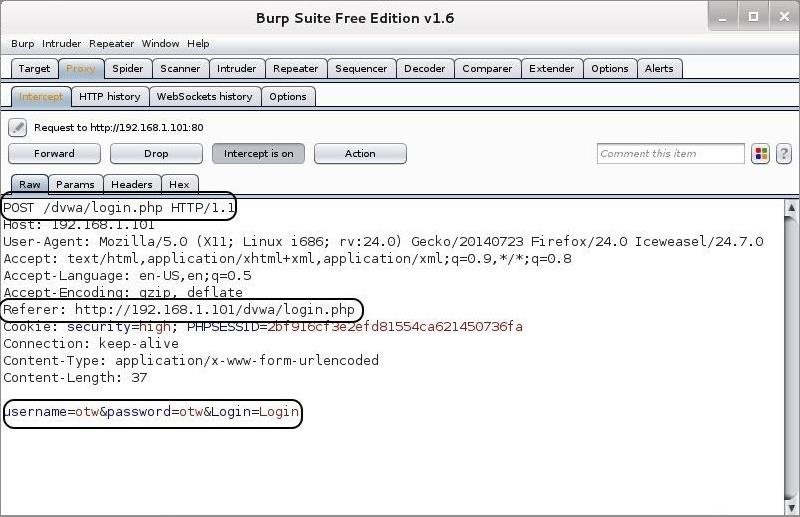
After collecting this information, I then forward the request from Burp Suite by hitting the "Forward" button to the far left . The DVWA returns a message that the "Login failed." Now, I have all the information I need to configure THC-Hydra to crack this web app!
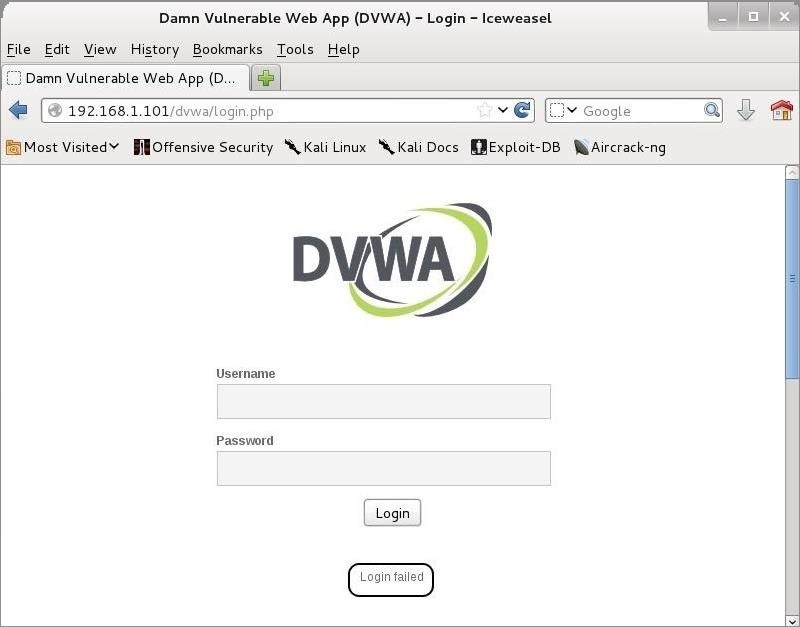
Getting the failure message is key to getting THC-Hydra to work on web forms. In this case, it is a text-based message, but it won't always be. At times it may be a cookie, but the critical part is finding out how the application communicates a failed login. In this way, we can tell THC-Hydra to keep trying different passwords; only when that message does not appear, have we succeeded.
Step 5: Place the Parameters into Your THC Hydra Command
Now, that we have the parameters, we can place them into the THC-Hydra command. The syntax looks like this:
kali > hydra -L <username list> -p <password list> <IP Address> <form parameters><failed login message>
So, based on the information we have gathered from Burp Suite, our command should look something like this:
kali >hydra -L <wordlist> -P<password list>
192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed"
A few things to note. First, you use the upper case "L" if you are using a username list and a lower case "l" if you are trying to crack one username that you supply there. In this case, I will be using the lower case "l " as I will only be trying to crack the "admin" password.
After the address of the login form (/dvwa/login.php), the next field is the name of the field that takes the username. In our case, it is "username," but on some forms it might be something different, such as "login."
Now, let's put together a command that will crack this web form login.
Step 6: Choose a Wordlist
Now, we need to chose a wordlist. As with any dictionary attack, the wordlist is key. You can use a custom one made with Crunch of CeWL, but Kali has numerous wordlists built right in. To see them all, simply type:
kali > locate wordlist
In addition, there are numerous online sites with wordlists that can be up to 100 GB! Choose wisely, my hacker novitiates. In this case, I will be using a built-in wordlist with less than 1,000 words at:
/usr/share/dirb/wordlists/short.txt
Step 7: Build the Command
Now, let's build our command with all of these elements, as seen below.
kali > hydra -l admin -P /usr/share/dirb/wordlists/small.txt 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed" -V
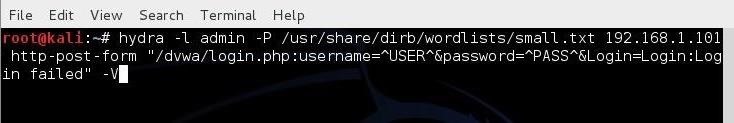
- -l indicates a single username (use -L for a username list)
- -P indicates use the following password list
- http-post-form indicates the type of form
- /dvwa/login-php is the login page URL
- username is the form field where the username is entered
- ^USER^ tells Hydra to use the username or list in the field
- password is the form field where the password is entered (it may be passwd, pass, etc.)
- ^PASS^ tells Hydra to use the password list supplied
- Login indicates to Hydra the login failed message
- Login failed is the login failure message that the form returned
- -V is for verbose output showing every attempt
Step 8: Let Her Fly!
Now, let her fly! Since we used the -V switch, THC-Hydra will show us every attempt.
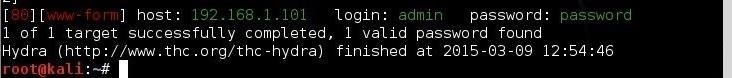
After a few minutes, Hydra returns with the password for our web application. Success!
Final Thoughts
Although THC-Hydra is an effective and excellent tool for online password cracking, when using it in web forms, it takes a bit of practice. The key to successfully using it in web forms is determining how the form responds differently to a failed login versus a successful login. In the example above, we identified the failed login message, but we could have identified the successful message and used that instead. To use the successful message, we would replace the failed login message with "S=successful message" such as this:
kali > hydra -l admin -P /usr/share/dirb/wordlists/small.txt 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&S=success message" -V
Also, some web servers will notice many rapid failed attempts at logging in and lock you out. In this case, you will want to use the wait function in THC-Hydra. This will add a wait between attempts so as not to trigger the lockout. You can use this functionality with the -w switch, so we revise our command to wait 10 seconds between attempts by writing it:
kali > hydra -l admin -P /usr/share/dirb/wordlists/small.txt 192.168.1.101 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed" -w 10 -V
I recommend that you practice the use of THC-Hydra on forms where you know the username and password before using it out "in the wild."
Keep coming back, my hacker novitiates, as we continue to expand your repertoire of hacker techniques and arts!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























112 Comments
Great tutorial! I was wondering if this makes alot of noise on the server, and if it does, is the wait function the best way to prevent it? I always run into getting locked out, or ip banned! Any cool tricks you could share?
Thanks again OTW, for another great tutorial!
I think I might be kinda late. but you can use a proxychain that changes your ip frequently....
How do I find the IP address? I don't see it anywhere in the burpsuite pics?
type: ping <targetwebsite.com> -c1
>>open terminal
>> type:
nslookup <website url>
There are sites that doesn`t let you use burpsuit against them --> how can i bypass that , or if it is impossible can i use page source instead ????
I was right! It is -w!
Good article, but wouldn't it be more practical to use Burp Intruder since we are already going to be using it to intercept requests and responses. Also I have encountered instances of hydra throwing false positives against POST forms as well as Telnet, any thoughts on this?
burp is also used for killing iphone through a snapchat vulnerabilty
Do you mean brute-forcing the account? Or as you describe "killing" the iPhone?
yeah URATTACKER i'm curious what do you mean by "Killing " iphone?
As DILL_ said "There is a vulnerability in the snapchat app for iphone that allows a hacker to perform a denial-of-service attack that can even crash the iphone. You can use burp to exploit the vulnerability."_
OTW any thoughts on my statement from before?
Which statement?
No i was asking about Hydra throwing false positives for web forms and telnet? Does it occur frequently because i have faced instances where where hydra throws like two or three valid user names and passwords for a web form or telnet and then when i put them in they are not valid.
Buckeroo:
Yes, it sometimes throws false positives. With web forms, it is totally dependent upon the "failed login" message that you use. If it doesn't see that, it will give you a false positive. In addition, if you slow it down with the -W switch, you will get fewer false positives.
OTW
Thanks! as usual great help. Gonna go check out your python articles.
One more thing as far as the failed login message is that from the response headers or am i just looking for what is displayed on the page after a failed attempt HTML, Pop up, etc.?
Wondering the same
There is a vulnerability in the snapchat app for iphone that allows a hacker to perform a denial-of-service attack that can even crash the iphone. You can use burp to exploit the vulnerability.
Yes you can use burp intruder to perform brute force attacks on usernames and passwords. Much like everything else there is more than one way to do just about anything. OTW simply showed you one of them.
Hey, sorry beginner here, how do I get the proxy of the site through metasploit like I got the main page but not the login one.
I think you are asking how to get the login of "Metasploitable"? It's at the IP/dvwa/login.php.
Hey, as always thanks a lot OTW for all the information. I just have 2 questions which if you could answer would be greatly appreciated.
1.THC-Hydra is a brute force, and I suppose it won't work on Gmail, Hotmail or in fact any such sites? If not what tools are there that will?
2.Android, an open sources mobile OS has already Kali and backtrack running right from the App store itself, only rooting is required. Can you do a tutorial on its uses and limitations too?
Thank You
last time i tried brute forcing gmail it blocked me like after 500 attemps, do you have a method to pass the block otw or know how`?
you dont think you have wrote a atricle about it, maybe you should?
Anytime you are trying to hack a site with a lock out, dictionary or brute forcing is the wrong tool for the job.
your really looking 4 trouble
You should always give social engineering first priority b4 tryn brute force.. Ucan always use phising sites but the quiZ is how du u get the victim get lured by ur trap... U need to spoof gmail maill. Lets say pretend ts an email from google telling them to modify password or sms spoof using the google numbers..
But if u can get physical access with the target pc , mayb u can do a dns spoof for a gmail or the target site.. N ur target will hardly know whats going on,,,, so my advice is that brut force should always b last option... Remembered anybod can be phised ur just need to know their weakness and exploit them.. Coz there is no patch fo human stupidity
But my problem is that i know that my victims password is on 8 symbols and two of them is numbers. (no big letters) ¨
so i generated a custom wordlist just for that spesific situation with crunch.
now i just need to know the combination. But every website the victim are using has https and will proberly block me. How should i find out the combination then?
Isn't there a way to slow down the attack so the website not are blocking me? cuz i would have the time to wait a little longer than.
hacking small useless websites, that nobody have in mind to use anyway doesn't help me to crack the big sites.
I hope you have a solution
As the article says, you can use the -w switch to slow the attack. Hope that helps.
what would the ip address be when attacking DVWA on localhost. I greatly all the help you give on your channel
If DVWA is running on your Kali system, use 127.0.0.1.
Thank you I got it to work
Thanks great Tutorial
i'm mostly having trouble when i set up the proxy for iceweasel and attempt to connect to DVWA from the localhost/DVWA it doesn't connect and therefore I can't get the required responses for Burp Suite
Hey! I'm trying with a different website which has an http-post-form like this " /Login.aspx?ReturnUrl=%2f" but when I type in the command it says "Wrong syntax, requires three arguments separated by a colon which may not be null: /Login.aspx?ReturnUrl=%2f" Idk what to do. Hope you can help.
Hi CHRIS!
I have the some problem like you, maybe someone want to help us...
You need to add the variables into the form.
tried several times but never successful.Anyone know how install Burp suite on windows 7? (everyone say install java 1st.WTF Done it years ago.)
Download it, extract it, run it. If it doesn't work on Java 8, try Java 7.
Java 7 .after click on it nothing happen except opening cmd and closing once.
Followed this tutorial to the T, but I'm still having issues. I keep getting "1 of 1 target successfully completed, 5 valid passwords found" (see below) when only ONE of those passwords is actually the valid one. I'm trying this against a local Joomla 2.5 site on my home server.
80www-form host: 192.168.10.10 login: admin password: admin
80www-form host: 192.168.10.10 login: admin password: password2
80www-form host: 192.168.10.10 login: admin password: 12345
80www-form host: 192.168.10.10 login: admin password: password1
80www-form host: 192.168.10.10 login: admin password: password
I'm using the following command per the information found in Burp:
hydra -l admin -P pass.txt 192.168.10.10 http-post-form "/testsite/administrator/index.php:username=^USER^&passwd=^PASS^&lang=&option=com_login&task=login&return=aW5kZXgucGhw&9567f9b6921e51f0d45edb26177b2612:Username and password do not match or you do not have an account yet." -W 10 -V
Any ideas?
The key is getting the "failed" message correct in the command
"Username and password do not match or you do not have an account yet." is the failed message that pops up, though.
From my tutorial;
"Getting the failure message is key to getting THC-Hydra to work on web forms. In this case, it is a text-based message, but it won't always be. At times it may be a cookie, but the critical part is finding out how the application communicates a failed login. In this way, we can tell THC-Hydra to keep trying different passwords; only when that message does not appear, have we succeeded."
So you're saying even if a text-based message pops up, it may not be the way a failed attempted is communicated? How would we indicate on the CLI if it's cookie based then?
Burnct:
You are getting ahead of yourself. First, find out how the application communicates a failed attempt.
Here's more information from the Burp's two interceptions during login. I'm not entirely sure how to find out in which way it "communicates" the failed attempt. This seems pretty straight forward that it posts a message in plain text:
POST /testsite/administrator/index.php HTTP/1.1
Host: 192.168.10.101
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.4.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.10.101/testsite/administrator/
Cookie: PHPSESSID=59ivhamr6svumtpp18442evuk3; af5dc374e4af2e4345969e6b50136729=ucp00rfi9vpr11r436dr3idn36
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 114
GET /testsite/administrator/index.php HTTP/1.1
Host: 192.168.10.101
User-Agent: Mozilla/5.0 (X11; Linux i686; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.4.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://192.168.10.101/testsite/administrator/
Cookie: PHPSESSID=59ivhamr6svumtpp18442evuk3; af5dc374e4af2e4345969e6b50136729=ucp00rfi9vpr11r436dr3idn36
LOL, I give up!
Have you figured this out? Did you try "Use a valid username and password to gain access to the administrator backend"?
I'm sort of struggling with this too. Did you try using "Use a valid username and password to gain access to the administrator backend"?
Where else other that the POST response or text would we find this? I struggled here also
I read somewhere about using the cookie data to flag a failed response but not sure how to implement that.
You can get it using tamper data. It's an addon. Go to addons and search for tamper data and install it. Then navigate to the login page and fill out the user name and password. Before clicking submit, open the tamper data tool and click 'start tamper'. Hit submit button on the website. A pop up will ask you whether you'd like to tamper, discard, or submit. Hit submit. Then look through the entries in tamper data and click on it. It will give you the request along with the post data. This works best if no other website is open; just the one you're trying to log into. Otherwise you're going to get a lot of pop ups asking you whether you'd like to tamper, in which case you could just discard, but it's harder to find request you're looking for. Hope this helps. I saw OTW did an article about how to crack passwords using tamper data and hydra. It's the same concept as when using burp essentially. I'm sure it provides a better instruction
I've been using the tamper data addon for years. It was the first thing I tried. I'm able to get this to work on most routers. However, the problem on my router is that I cannot figure out the format of adding the username and passwd to the url bar. Thats all tamper data / burp suite shows. I've tried adding it after the /check.php and nada.
Hello World! hehe, im so funny. Jokes aside, I do have a question. I have been following your tutorial and have installed DVWA locally on kali linux (Dual booted) and when I setup the proxy on Iceweasel, I cannot load any pages, not allowing Burp Suite to access any of the needed information. It loads for a bit, than quits. I took a picture of my proxy settings but it was to big so I put a link to it below. Also, sorry if this is the most obvious thing, im tired and have been at this for a while. Sorry for LQ, couldnt take a screenshot for a reason and used my phone.
Solved
Hey OTW, really well explained tutorial, I have a question though : should I use proxy with hydra if I want to crack password for ONE account let's say my friend's Facebook account? Will I get an ip ban or something like that ? And BTW , I really want to know if you could make a tutorial on how in Mr.robot episode 1, Elliot hacked his psy's password by simply adding custom word to a dictionary and instant cracking. I know you can do it with crunch but it is only creating wordlist.
Thanks.
Hey OTW ! Your tutorials are vey well explained and I'm learning a lot. Could you please tell me if I should use a proxy list in order to crack an online account with crunch and hydra ? And can you teach us how did Elliot cracked his target's password in episode 1 of Mr. Robot ? They way he adds password to a password list and instantly run the brute force . I'm waiting for your answers , thank you .
He used cupp.
sorry for double post and thanks for the reply, now that i managed to use CUPP this magical password creator, any clue on which type of password he cracked ? Most online passwords has a tries/ip or tries/account limitaion, he treid a 90k password list :o
or do you have any tip on how to auto change ip addres in kali linux ?
So I was tryin to brute force a yahoo email , so I tested it first with my real email and made a .txt word list with 5 passwords and one of them was the right one and the other 4 weren't.
I got and I type-
Hydra -l (my email) -P (my wordlist) -s 465 -S -v -V -t 1 smtp.mail.yahoo.com smtp
hydra checks all of the 5 words and says that all were invalid and no password was recovered even though the 3rd was my password, what my be happening?
You are missing probably the most important part of the Hydra command, the last section. That section defines how the server communicates that the password was wrong. You didn't include it.
so what should I add to the end of the script? can you give me an example?
Hydra -l (my email) -P (my wordlist) -s 465 -S -v -V -t 1 smtp.mail.yahoo.com smtp - than whats the next part?
thanks for responding so quick :D
Please go back and re-read this article. There are several errors in your command.
Ok thanks :D
I know that this is really late, but I still hope you respond. I followed your tutorial and did everything, but I still have one problem. I looked at the real time code for the website and attempted a fake login and it told me that the error message was "error: "Incorrect Password" ". When I put that into hydra it just came up with the screen you get when you open hydra. The command I'm using is
hydra -l (the email) -P Desktop/wordlist.txt 54.215.131.188 http-post-form "/api/auth/login:data%5Busername%5D=^USER^&data%5Bpassword%5D=^USER^:error: "Incorrect username."" -V
Any help would be very much appreciated!
Great tutorial. I managed to get something similar to work on a test VPS I use to attack.
The issue however is that the auth.log file shows my IP when simply using hydra.
Therefore I tried using:
"hydra -s 22 -v -V -l root -P /usr/share/wordlists/testlist.txt -t 4 -w 60 SERVERIP ssh HYDRA_PROXY=socks5://121.40.102.199:1080"
and also tried using
"proxychains hydra -s 22 -v -V -l root -P /usr/share/wordlists/testlist.txt -t 4 -w 60 SERVERIP ssh"
Howerver in both cases it said in the auth.log file:
"reverse mapping checking getaddrinfo for MYHOMEIP failed - POSSIBLE BREAK-IN ATTEMPT!"
Can you explain why it has my home IP some how via "reverse mapping? My proxychains list has about 15 proxies in it using dynamic_chain. Im very confused.
A great tutorial from OTW but this one has a more detailed explanation for those still having trouble:
While setting up Burpsuite and Iceweasel I did everything you stated and after that every page will result into unlimited loading........ and Burpsuite seems to only get the GET request or parts of it. Of course when I put the proxy off in Iceweasel everything works perfectly fine.
EDIT:
Fixed it by going to options and enabling all the 'Intercept Client Request'.
I tried the following commands which none of them worked....... :(:
Triphat, can you give me an example of what you mean? So far I have this:
hydra -l admin -p '/root/Desktop/Passwords/rockyou.txt' IP http-post-form "/login.cgi:UserName=^USER^&password=^PASS^=1234&hiddenPassword=1234&submitValue=1:The username or password is not correct." -V
Hey, great tutorial. I follow those steps, but something is still wrong (I get 16 valid password, from which mine is none) and I don't really know what it is.
My command is:
hydra -l (my username) -P /usr/share/wordlists/rockyou.txt.gz 69.162.92.205 http-post-form "/login.php:action=login&login=^USER^&autologin=1&password=^PASS^:Authentication failed." -V
Also my console shows me those "signs" instead of letters. I never encountered that before.
Thanks for incoming help :)
The DHS uses Login.aspx......
Please help me
I'm getting this:
DATA attacking service http-post-form on port 80
ATTEMPT target mysite - login "test" - pass "0" - 1 of 957 child 0
ATTEMPT target mysite - login "test" - pass "00" - 2 of 957 child 1
ATTEMPT target mysite - login "test" - pass "01" - 3 of 957 child 2
ATTEMPT target mysite - login "test" - pass "02" - 4 of 957 child 3
ATTEMPT target mysite - login "test" - pass "03" - 5 of 957 child 4
ATTEMPT target mysite - login "test" - pass "1" - 6 of 957 child 5
ATTEMPT target mysite - login "test" - pass "10" - 7 of 957 child 6
ATTEMPT target mysite - login "test" - pass "100" - 8 of 957 child 7
ATTEMPT target mysite - login "test" - pass "1000" - 9 of 957 child 8
ATTEMPT target mysite - login "test" - pass "123" - 10 of 957 child 9
ATTEMPT target mysite - login "test" - pass "2" - 11 of 957 child 10
ATTEMPT target mysite - login "test" - pass "20" - 12 of 957 child 11
ATTEMPT target mysite - login "test" - pass "200" - 13 of 957 child 12
ATTEMPT target mysite - login "test" - pass "2000" - 14 of 957 child 13
ATTEMPT target mysite - login "test" - pass "2001" - 15 of 957 child 14
ATTEMPT target mysite - login "test" - pass "2002" - 16 of 957 child 15
80www-form host: 185.27.134.143 login: test password: 03
80www-form host: 185.27.134.143 login: test password: 00
80www-form host: 185.27.134.143 login: test password: 2001
80www-form host: 185.27.134.143 login: test password: 0
80www-form host: 185.27.134.143 login: test password: 01
80www-form host: 185.27.134.143 login: test password: 2000
80www-form host: 185.27.134.143 login: test password: 02
80www-form host: 185.27.134.143 login: test password: 20
80www-form host: 185.27.134.143 login: test password: 123
80www-form host: 185.27.134.143 login: test password: 1000
80www-form host: 185.27.134.143 login: test password: 100
80www-form host: 185.27.134.143 login: test password: 1
80www-form host: 185.27.134.143 login: test password: 2
80www-form host: 185.27.134.143 login: test password: 10
80www-form host: 185.27.134.143 login: test password: 2002
80www-form host: 185.27.134.143 login: test password: 200
1 of 1 target successfully completed, 16 valid passwords found
My command was:
hydra -l test -P /usr/share/dirb/wordlists/small.txt mysite http-post-form "/index.php:userlogin=^USER^&passlogin=^PASS^&log=Login:Please enter valid Username and Password." -V
Please reply soon
I get the same exact thing anyone know why and how to fix it?
Thanks for a awesome post.
I'm started hacking my web login of Wi-Fi router but there is a catch every time I entered a wrong password it refresh the page and doesn't show any wrong message. What should I do?. Please help. The web file if you need: https://57cb3da913017b33230a33ee90f78e7b977fd794-www.googledrive.com/host/0BzJkbqA_bKIEfllJR0RseVhTMF9VTktSUExPa3ZmSHRJN1NmRDRUc0wzVVFyMHc3UFF6NGc/GPON%20Home%20Gateway.rar
THC-Hydra is the wrong tool. Try using aircrack-ng for hacking the passwords on your WiFi router.
no i'm hacking the web login of my router not the wifi password. Thanks for the reply!
OTW, I tried to crack my own password and everything was going ok, but THC-Hydra didn't stop when the correct password was attempted.
What might be the problem?
Hey, after a long time trying I succeed in my tests! But...
80http-post-form host: **** login: ****
STATUS attack finished for **** (valid pair found)
1 of 1 target successfully completed, 1 valid password found
The password was found, but Hydra do not show it!
Any ideas?
P.S.: Sorry for my bad english.
Nobody? =(
Notice where the username and password appears in this tutorial. What does it say there when you run THC-Hydra?
My output is like yours, except this last screen:
In my case the "password : password" is not there.
Thanks for your time.
It says right there that it found the password "password" for the admin user.
Yes, but this is your screen, I just copied from your output trying to show whats is missing. I 'll try again and post my screenshot this time, just give me 2 min =)
How can I help you when you have obscured all the key information?
I see green color.
Did I? Sorry. I did because the target is a website and the login is my own account.
I thought the target have nothing to do with it...
Just tell all information you need and I will be pleased to give to you =)
Thank you man, this is awesome! :)
I just have two questions: What about if I know that the username's password is written in another language, with maybe 2 numbers. Should I use kali linux wordlists? Or should I create my own wordlists with crunch?
And how do I find the wordlists and passwordlists using the terminal?
I hope you can help me out :(
If you know username and password then find wordlist with terminal use this command "locate wordlist" or "locate rockyou" (Kali Linux) then open with text editor and find if there or not .. you can add in list if not found.
I have problem like @BURNCT when scan my website with Hydra I get 208 valid passwords (lol)
Content-Type: application/x-www-form-urlencoded
Use: http-post-form
inputUsername, inputPassword, inputLogin - form (method="post")
Try everything (http-get-form, http-post-form, use Cookie,...) but not works.
How can I use Hydra... "and hack like pro"?
Hi
Thanks for the useful guide. However i dont manage to succeed. Some help would be appreciated. Below a print of Burp results and the command line in Hydra. Hydra tells me after 'enter' the syntax rules but does not start the job.
Also : i use Hydra with Cygwin on Windows 7. Does it matter from WHERE i start the hydra command, i mean should i do it while being in the hydra dir, or should it be the cygwin dir or just the root dir C ?
POST /login.php?action=in HTTP/1.1
Host: xxxxxx.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: nl,en-US;q=0.7,en;q=0.3
Accept-Encoding: gzip, deflate, br
Referer: https://xxxxxx.com/login.php
Cookie: visidincap526178=dBiizl5bQzKldS2WdMrM/ArT6VYAAAAAQUIPAAAAAAB6g3H+O0+VIC6UaHfrwDzi;
visidincap821436=nmDb/MkQTXm2VsdHkiWxuzYCN1cAAAAAQUIPAAAAAADrVUYTxunztOfbWaA78Xgm; _ga=GA1.2.242869812.1465591208
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 82
formsent=1&redirecturl=index.php&requsername=blop&reqpassword=blop&login=Login
Wrong username and/or password. This is the fail message of the site.
hydra -l yyyyy -P cygwin64/john.txt 123.456.789.000 https-post-form "/login.php:requsername=^USER^&reqpassword=^PASS^&login=Login:Wrong username and/or password." -V
Great tutorial. However, I do not think this technique will work with a particular router I have. The router's login page uses a Java applet. Any idea how I can approach cracking the password. Using hydra SSH gives me an error of password authentication not supported.
The IT department gave me a Motorola router (bought in 2010) to factory reset. The guy who set it up quit and did not document the password. There is no reset button, and when connected to the serrial port, pressing the ESC key while booting for factory firmware when loading does not work until it is too late. From what I understand, the IT guy who set this up was a real IT genious. Motorola will not help me with it without paying for support.
Hello
(At first I have to say that my English is not native then if I have any problem , Excuse me)
My Router is Linksys and it has different web page login panel and there is no part that related to Username and Password
Also my Router doesn't have any Username field
Please see these pictures to see burp suite log:
http://share.pho.to/AQnpb
Now how should I write hydra command(Web form)?
All that happens is firefox says connection is not secure and there is no way around this while the proxy is changed as seen in this tutorial. Cant connect so I cant use firefox thus I cant use burpsuite or crack logins.
Hey Perfect Storm,
I know this is a late reply but hopefully it helps either you or another person in your situation. So once the proxy is set up you have to type http://burp into the web address, then download the certificate. You can then install the certificate in Firefox by *: 3 bars top left corner, Options (or Preferences), Privacy and Security (or Advanced), find the Certificates section, View Certificates, navigate to Authorities, Import, find your certificate, double click. Done. Now you can carry on with your pentest
Hope this helps, Neox.
http://burp no longer works
Hi there!
Thanks for this tutorial!
I found myself stuck, please see the print screen:
And from there, it does not go on...
I would really appreciate if I could get some guidance.
Hey OTW and nice post as always :)
Since i began researching about brute-forcing and wordlist attacks i have been very wondering if "partial brute-force/wordlist attacks exist". A succesful brute-force attack against strong passwords may take hours, days and even weeks and it is undeniable that letting your computer operating for such long is not the best for the machine's health. And also if we take into consideration that most users do not change their passwords that often i think that diving your brute-force attempts could be a pretty good idea if you are not confident enough to let your machine operating 24/7. Isnt there a way to "pause" the brute-force attack either by saving the line of the wordlist that you have stopped or maybe saving the last combination of characters and its length so you dont need to begin brute forcing again from the start?
P.S. Sorry for my bad english :P
can't find "Edit" to go to preferences advanced network, help
However if there are more than 2 input fields other than USERNAME and PASSWORD Such as DATE OF BIRTH would burpsuite work - if I have all these wordlists ?????
i have configured icewasel and burpsuite as you have mentioned but my page just loads and finished when burpsuite has gotten nothing.
can someone give me the solution to it?
Would it be reasonable to use these brute Force methods on the admin cPanel of a website? If not, what other appropriate alternatives are there?
Great article what if the login failed message is cookies based. What to do then ? how to proceed further ?
Thank you
My DVWA is at 127.0.0.1. What should my Proxy be?
Hey i know this is an old post, need some help with the following. i,m trying to crack the login for the attached localhost form, can someone share what command i need to apply in thc hydra. i get passwords but they are incorrect & do not work. thanks,
Hydra : Wrong Password
I did the same as you , and I get wrong passwords...
Why ?
Help please !!!
Hello i'm have a site need to check on it with id's but my problem is i can't because it's different little, I need to check on it with open bullet or hydra tool but i can't creat a config on it, site is have a little sources complicated, if can any one help me Ther's the sourse of NETWORK Panel The Form Data:
and the View Source:
sorry 4 bad English
so while doing this my post is
/forum/login.php?do=login
the ? is blue and wont let it work. it makes it into
/forum/login.php
and that is not correct. with it only being that i states
ERROR Unknown Service
How do i work around this?
Share Your Thoughts