Welcome back, my tenderfoot hackers!
WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!
WordPress websites are also among the most vulnerable websites. Generally, WordPress hosts small- to medium-sized businesses that are not the most vigilant at installing patches and updates. This makes for some broad and fertile ground for web app hacking!
In this tutorial, before we advance to vulnerability assessment and exploitation, I want to show how to identify these potentially vulnerable WordPress websites.
WordPress Vulnerabilities
WordPress is among the Internet's most widely used content management systems (CMS). In addition, it is among the most vulnerable. A quick glance at SecurityFocus's website reveals 16 pages of known vulnerabilities to WordPress sites, with the most recent group coming just last month.
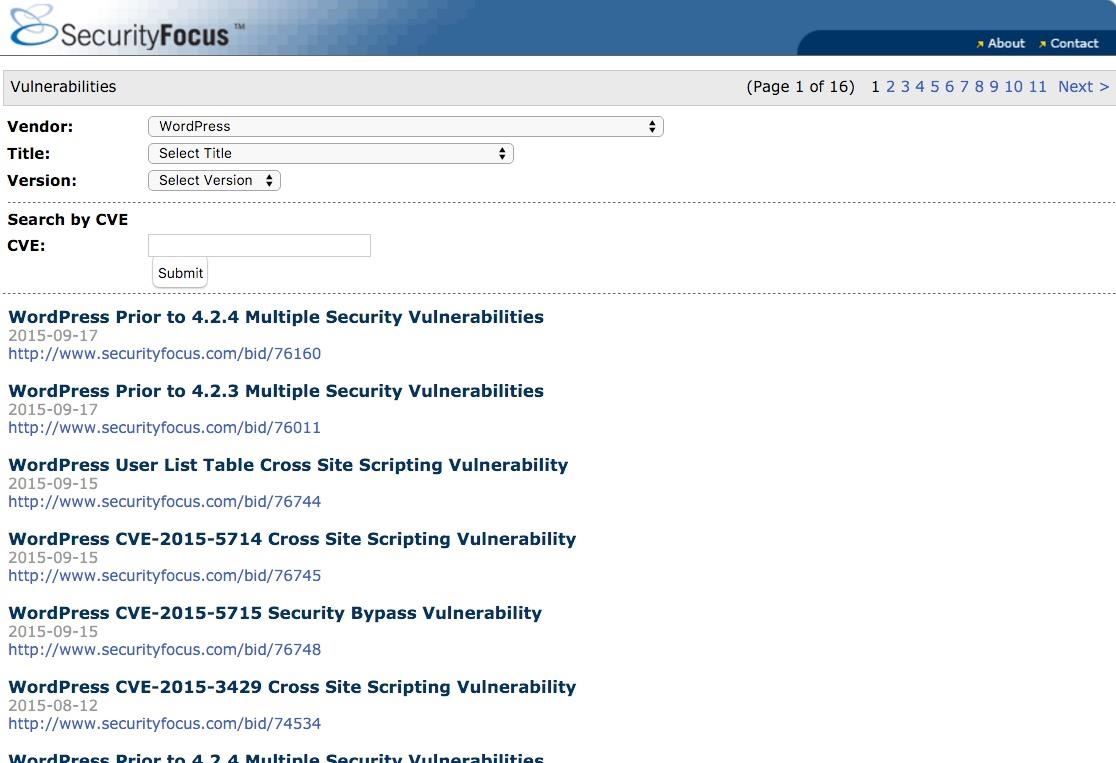
A similar analysis of exploits particular to WordPress on Exploit Database reveals 784 exploits. The most recent of these are just this month, October 2015.
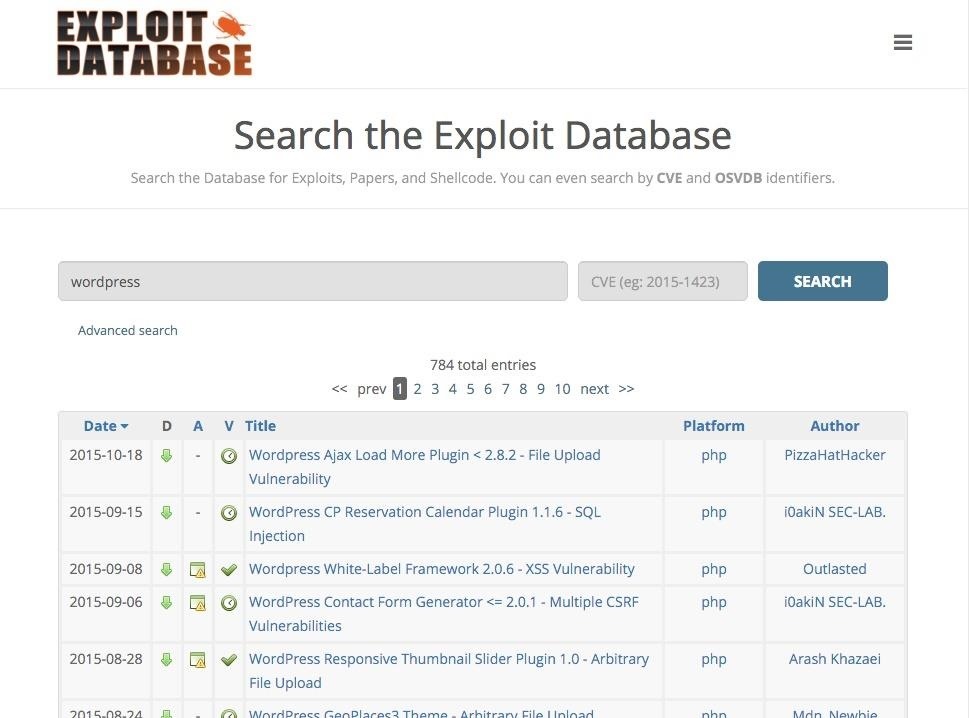
These two bits of information make it clear that WordPress provides fertile ground for web app hacking.
Step 1: Finding Sites Built on WordPress
The first step here is to identify whether the website is running WordPress. If we are examining a particular website and we want to know whether it runs WordPress, there is a website called BuiltWith where we can enter the domain name and it will return information on the technologies that the site was built with.
In this case, let's take a look at the Toronto Standard, a venerable newspaper of Canada's largest city. When we enter its URL into the BuiltWith website, it returns that following information.
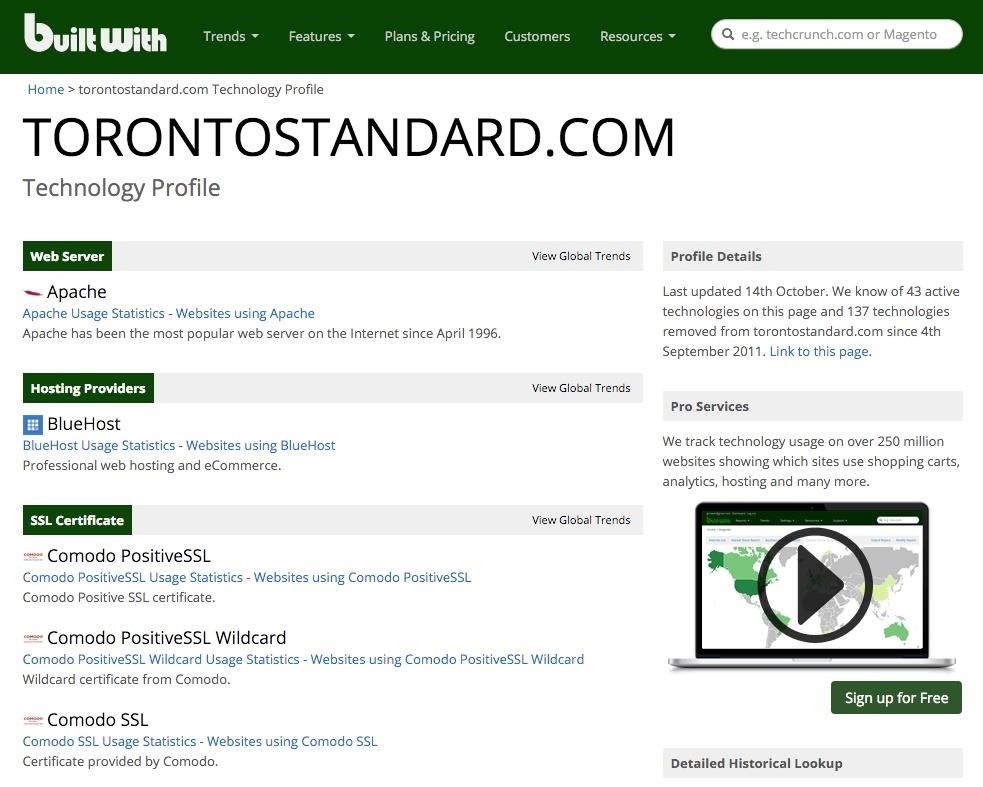
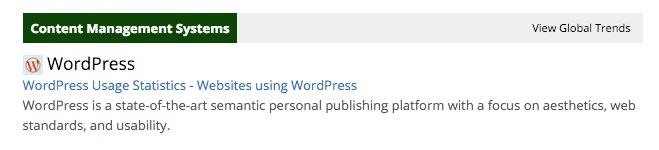
As you can see, it reveals to us that the Toronto Standard runs on Apache and is hosted by BlueHost. If we scroll down a bit, we can see that BuiltWith tells us that the newspaper uses WordPress as its CMS.
Step 2: Google Dorks to Find WordPress Sites
There are numerous signatures of a WordPress website. These include unique directories, login pages, tags, text, etc. For those of you familiar with Google hacking, you can usually find those signatures in the URL.
A few useful Google dorks to identify WordPress websites include:
"index of" inurl:wp-content/
This dork returned 10,400,000 sites.
"inurl:"/wp-content/plugins/wp-shopping-cart/"
This dork returned 4,230 sites.
"inurl:wp-content/plugins/wp-dbmanager/"
This dork returned 290 sites.
I'm sure that you can come up with many more dorks that will return WordPress sites, but these should provide you with plenty of sites to practice on for awhile.
While doing Google hacking, you might get a webpage from Google with a CAPTCHA. Don't worry, Google is just trying to make certain you aren't running a script which violates the Google EULA.
Step 3: Tools for Identifying WordPress Sites
There are a number of tools that you can use to identify WordPress websites. Probably the two best are the browser extensions Chrome Sniffer for the Chrome web browser (it's also available on GitHub) and BuiltWith for the Mozilla web browsers (these include Firefox and Kali's IceWeasel).
With the Chrome Sniffer extension installed, when I navigate to torontostandard.com, a small WordPress logo appears in the the right side of the URL box indicating that this site runs WordPress.
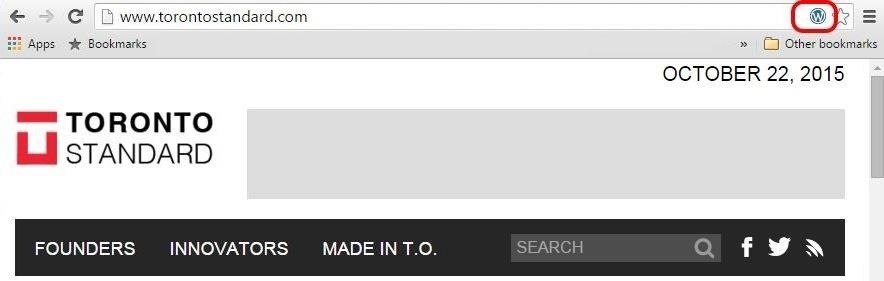
Now, whenever you navigate to a website, your browser will identify the technology the site is built with. This, obviously, can be useful for all types of web app hacking, not just WordPress.
Keep Coming Back for More Web App Hacking!
In my next tutorial in this series, we look at ways to find known vulnerabilities in these websites and, ultimately, the tools and techniques for exploiting them, so keep coming back!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















4 Comments
22 Kudos in 4 minutes!
Great job on the tutorial, OTW.
in kali linux you can use whatweb to identify wordpress-websites and others running on webserver and wpscan to scan wordpress-websites..just for those who does newbie around nullbyte
Mr_Nakup3nda
Another browser plugin I find useful is Wappalyzer. It shows not just CMS but also jQuery version, PHP version, host OS, and sometimes even common plug-ins used, for example it hits on Revolution Slider (which exposed a massive vulnerability not too long ago). Works with Chrome or Firefox.
Very interesting! I have a question,why I find some webs doesn't have CMS?
Share Your Thoughts