Welcome back, my tenderfoot hackers!
As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.
Of course, the Internet is mapped by IP addresses, so this translation from domain name to IP address is essential for easy navigating. Can you imagine if we had to remember the IP address of WonderHowTo and all our other favorite sites to navigate the web? I can't, and I have a pretty good memory. This means that DNS servers contain vast amounts of data that we might use as a hacker to gain information about our potential victims.
This essential and ubiquitous service can be abused for our purposes as hackers. It can reveal hidden servers that may contain confidential or key information that we might find valuable.
Step 1: Dig for DNS Info
The domain information groper, or dig, is a command that is built into every distribution of Linux and UNIX. It is designed to be able to grab and display for the user key DNS info. Let's open a terminal and start digging!
With a terminal open, we can type dig from any directory as this ubiquitous command is located in the /bin directory in every version of Linux and UNIX. Let's do some digging on our friends at SANS, one of the leading information security training and consulting firms in the world.
kali > dig sans.org
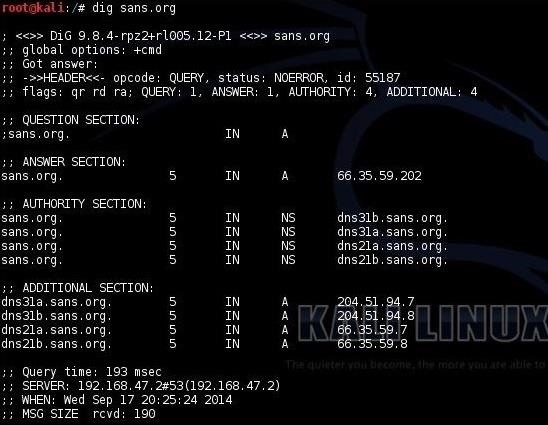
Dig goes out to the Internet and grabs the records from your DNS server as seen above. You can see that it grabs the IP address (66.35.59.202) of the domain sans.org. The next section contains the name servers for this domain:
- dns31b.sans.org
- dns31a.sans.org
- dns21a.sans.org
- dns21b.sans.org
If we want to find their email servers, we simply add an mx to the end of the command like this:
kali > dig sans.org mx
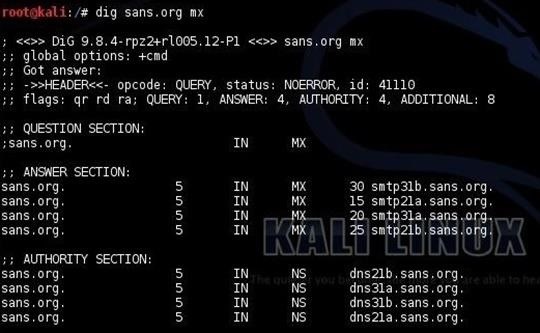
As you can see, this simple query reveals for us the four email servers that SANS utilizes. Hmmmm....very interesting. Anyone want to send anonymous, spoofed, or bulk email?
Step 2: Open Dnsenum
Kali and BackTrack both have a nice little tool that can do everything dig does and more. It's called dnsenum. We can find it by going to Applications -> Information Gathering -> DNS Analysis -> dnsenum.
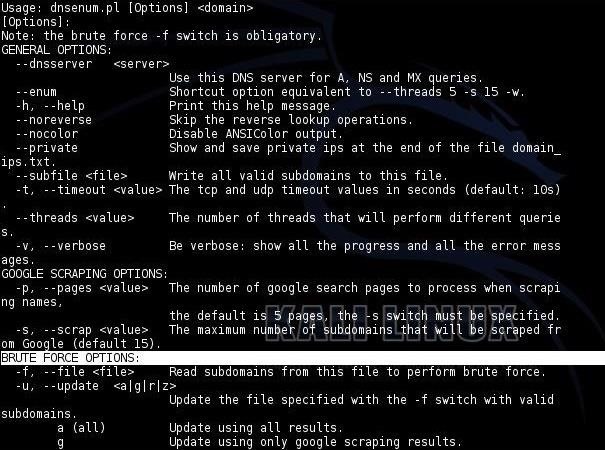
When you do, it will open a dnsenum help screen like that below. Among the things that dnsenum can do for us is find subdomains that are not obvious or are hidden from the public. I have highlighted the section in the screenshot that addresses brute-forcing these subdomains.
Step 3: Run Dnsenum
Let's try running this simple, but effective tool against our friends at SANS and see if we can find additional information about their servers and subdomains from querying DNS. It's probably worthwhile to note here that all of this reconnaissance is "passive." There is no way for the victim to know we are "casing" their systems because we are not "touching" their systems, just the DNS servers so it looks like normal traffic.
kali > dnsenum sans.org -f /usr/share/dirbuster/wordlists/directories.jbrofuzz
You can use any wordlist you have available to you that you believe may contain the name of subdomains of the organization, so choose you wordlist carefully, my tenderfoot hackers. You can find all the wordlists built into Kali by typing;
kali > locate wordlist
In this case, I chose the /usr/share/dirbuster/wordlists/directories.jbrofuzz wordlist, as it has many directory names which also are often used in the names of subdomains.
When we run this command, we get the following results. First, we see the name servers and the mail servers (mx) just as we did by using dig. These records also include the IP addresses of these servers. It's interesting to note that SANS is using Google mail servers. I would have thought they would use their own email servers, considering their level of IT expertise.
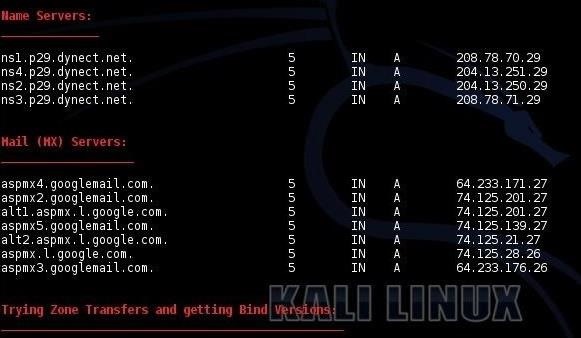
Next, dnsenum will attempt to do a zone transfer. In this case, it failed against the DNS server.
Finally, it will try to find subdomains within sans.org. Many times, companies have subdomains such as training.sans.org and admin.sans.org—dnsenum can help us find these by attempting to brute-force these potential subdomains using a wordlist. Of course, as I mentioned, the wordlist you choose will be critical to your success, but generally, these subdomain names are simple dictionary words like training, test, sales, admin, etc.
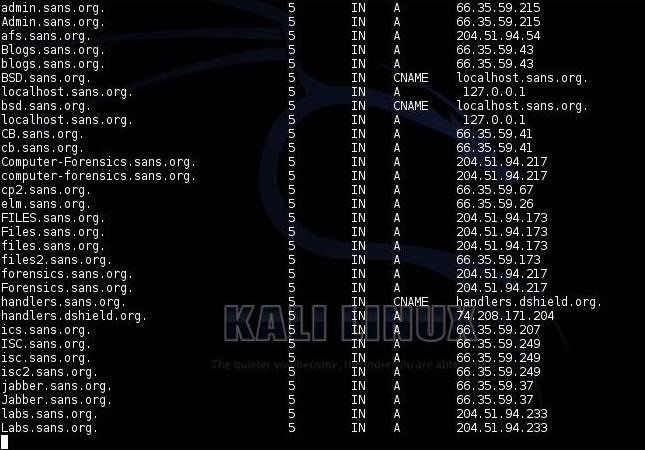
Like any brute-force attempt, this can be tedious and time consuming, so be patient. If you choose a good wordlist and are patient, you are likely to find many hidden servers that the company doesn't necessarily want you to know about, but might be juicy targets. Dnsenum will not only find these servers, but will also provide you the IP address which can VERY helpful when we get around to attacking that system.
I ran dnsenum for a few hours and retrieved the subdomains listed above. As you can see, it was about 50% done, having only gone through the letter "L."
Dnsenum is just one more tool in our hacker toolbox that can be useful for doing reconnaissance on potential targets. The beauty of this tool is its ability to find those hidden servers by simply abusing DNS, and the potential victim is totally unaware of any untoward activity.
I'll keep showing more and more tools and techniques for hacking, so keep coming back, my tenderfoot hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























13 Comments
you are calling dns domain name service but i read that it is (domain name system) servers, which is correct?
also i don't fully understand what a name server is and what it does.
please explain, and thanks for a great lesson.
Chris:
Domain name service vs. System? Does it really matter?
OTW
yeah i know, but i like to make sure im saying this correctly so i dont sound like an idiot.
could you explain to me what a name server is used for?
The nameserver responds to the query translating the domain name to IP address.
thanks for the post, very useful......
just adding, you can also use dnsmap to bruteforce sub domain :)
I might have missed it, but did you say why you would want to do this?
Reconnaissance is getting information about your target before you attack. This is the most important step in the hacking process and, most of the time, the longest step. Abusing the DNS will show you the IPs of servers that could be potentially vulnerable to attack, or show servers with some confidential information!
Thank you. Yes, I definitely understand the importance of recon. For some reason I just wasn't correlating DNS with servers...I know, sounds ridiculous.
Why I failed to find hidden servers?it shows:AXFR record query failed: connection failed
master OTW after finding mail servers,how can i use themt to send spoofed emails... ?
Also, you can use the command "dig", many dns servers are poorly configured, so we can try to make a transfer zone:
$ dig @dns21a.sans.org sans.org axfr
Sometimes it works, and lists all the hosts inside the domain in seconds.
what is zone transfer? and it's use?
Share Your Thoughts