Information is power and today, it can mean money, a lot of money. Hence, the collection of data, is permanently rearranged through new techniques for theft of information.
As we know, data capture assumes various forms of hacking, either through a sniffer , or through remote access, or stealing socially engineered or phishing credentials , or directly by malware infection, to mention an example .
Today we are going to comment on a technique to capture information, known in the decade of '60, in its little divulged moment, and that at the moment they are gaining popularity: the TEMPEST attacks
There is some consensus among researchers of the subject that a TEMPEST attack is one that tries to obtain information from electromagnetic radiation, radiofrequency vibrations, emanations, etc. unintentional or unintentional that an electronic device (mobile, computer, tablet, etc.) emits, the purpose of which is to obtain data that once decoded would give access to information from the sender.
More technically: "Tempest: the scanning of electrons by the computer screens emanates signals that can be captured even several kilometers away. The tempest technology is able to reconstruct, from the captured signals, the image shown on the screen that caused them. "
But beware, TEMPEST attacks, have a history of espionage with a little widespread spread. It seems that during the Cold War, that stage is worth everything and where to find out what the "enemy" is doing together with their own survival as a more powerful nation, the US NSA implemented a project based on this technique to obtain information of his Soviet enemies.
Under the security umbrella they got into the neighbors' house, and TEMPEST was the covert name of this espionage system which -value to the radio-electric system emissions- intercepted the EM waves of radiation from them.
Also, the TEMPEST FOR ELISA test by means of a program written by Erik Thiele, demonstrated that it is possible to capture the AM frequency emissions using a CRT monitor (we speak of the 60-70 decade); circumstances that no longer surprise us today because more recent studies have shown that it is possible to detect the radiation corresponding to the press of a key on a keyboard, not only for wireless but for traditional keyboards and even for laptops .
We also know that any electronic device continuously emits electromagnetic waves that propagate either through the air or from conductors such as the wiring to which it is connected, and whose variations produce the almost exact reflection of the processed data, so that with resources or appropriate equipment can be captured, and subsequently, reproduced the transmissions that have been issued.
The hardware of our computer concentrates its most notable emissions on the monitor, the CPU and the printer, whose wiring acts as "antennas" that increase the distance of the emissions of our PC, and of these takes advantage of the TEMPEST attack .
The researchers of the subject indicate that inside the PC, the "buses" are channels of digital data that connect their different components, like this: "The connections between computers separated from each other act, without pretending, like antennas since they generate signals that can be intercepted easily, unless special precautions are taken. The fact that the emissions of a device continue to occur even though it is turned off is because they have an internal battery that continues to feed certain functions. "
As for the meaning in itself of the term TEMPEST , there is no peaceful agreement and different versions are read . We have already seen that there are those who say that it was a key name in a US military operation in the middle of the Cold War.
Others say that the term is an acronym:Transient Electromagnetic Pulse Surveillance Technology , which in Spanish would be something like Technology for the Transmission of Involuntary Electromagnetic Pulse.
But the meanings do not end in the preceding lines, there are those who say that is the acronym of Telecommunications Electronics Material Protected from Emanating Spurious Transmissions or Transient Electromagnetic Pulse Emanation Standard . As you can see, there are interpretations for every taste.
It should be noted that the US has indicated that it is not an acronym and that it has no particular meaning, to be known.
Another point to emphasize is that there are standards that already collect the precautions that must be taken to avoid an attack based on an interception of this type. Thus, the ISO-27002 standard states that "Equipment that processes sensitive information should be protected to minimize the risk of leakage of information due to emanation"; so also the expression TEMPEST , usually designates the standards of protection for emission safety (EMSEC), without any specific meaning.
In short, in order to get an idea - half of it - of what is a TEMPEST attack, imagine that you are in front of the PC, chatting quietly by IRC or SKYPE and someone close to our house, is receiving the waves that our screen generates, which decrypted correctly, would let you know what we are writing!
But the TEMPEST of the spies is modernized, thus it is spoken of attacks of interference Van Eck, that is nothing more than to spy the image emitted by an LCD or CRT, based on the capture of the emissions of the monitor and its cables.
It was discovered by a Dutchman whose name gave the name to the technique and was publicly demonstrated in 1985, with equipment that cost 225 dollars and allowed to obtain the image reproduced in a monitor from outside the building where it was. The following image shows the equipment used.
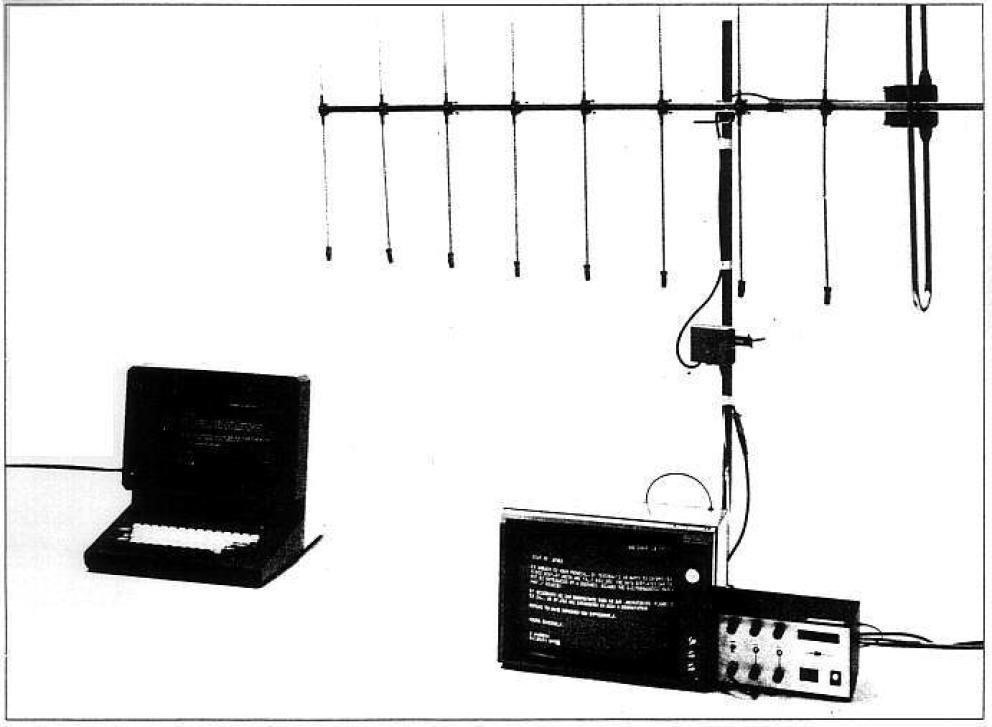
We are progressing, undoubtedly, and from the test assume that Elisa in the same room, and we go outside the building, which makes us think of neighbors and neighbors, in terms of spying ha5a .
Another type of TEMPEST attack is known as AirHopper (some of which are within the scope of PHREAKING), based on malware developed by Israeli researchers, which shows that an attacker can transmit sensitive information from isolated computers (not connected to the Internet) to mobile phones using radio signals and made ; in short, of the coveted data.
Malware called " AirHopper, "configured to capture data is installed on a mobile phone and uses the FM radio receiver of the device to pick up the signals from the electromagnetic emissions of the computer's graphics card and sent through the monitor cable that operates as an antenna when a key is pressed.After the data is sent to the telephone that interprets the signals, they can be transmitted to the attackers via the Internet or SMS messages.All
this we have been discussing would explain the reasons why Snowden the defendant to filter the spy program of the NSA, yes as you see this is from past and current spies D) to ask his lawyer to place his cell phone in the refrigerator in order to try to block any type of monitoring; that is, it was not to cool it, but through what is known as "Faraday Cage" , neutralize the electromagnetic signals emitted by the phone.
Removing the battery is no remedy because even without it, the devices have additional power sources inside (and still off), according to Seth Schoen , expert of Electronic Frontier Foundation.
As you can see the field is wide and profuse development, a type of espionage that leaves no trace, leaves no trace, silent and undetectable; and that to all this, we have put aside the attacks taking advantage of the light or acoustic signals, which may be the subject of other posts.
To close, I leave the TEMPEST SHOWROOM test link deleted
where you can download the ISO either to test it on a computer, burn a CD or use a virtual machine; following these steps that the site indicates:
- Using a radio, place it in front of the PC.
- Tune to the dial at 1500KHz (AM frequency)
- Press the <p> key to start the program
You will hear: "For Elisa" by Beethoven and the rest use the imagination.
But know, no longer be disconnected from the Internet or with the devices turned off prevents that with the appropriate equipment, we can be spied on. It will be necessary to go for covers, boxes, briefcases Dor enter a "Faraday cage", that is, a room / store specially equipped in complete electromagnetic isolation to avoid any radio emanation emerge and end up appropriating our information.
see u









































Be the First to Respond
Share Your Thoughts