In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.
On the surface, this may seem innocuous enough—especially considering Comcast's insistence that the two connections always remain separate. But, as we well know, very little of our data is truly secure, and any extra vulnerability like this will invariably open the door to potential exploits, though that may not necessarily be the case here.
Customers will be notified with a mailer before their router is remotely turned into a public hotspot, and when Comcast flips the switch, they'll send out an email to reiterate. But, for a company whose customer service is rated so poorly that it even has its own Wikipedia article, an opt-out service with these kind of reprocussions seems ill-advised.
Download the Xfinity WiFi app for your Android or iOS device to see if there are any hotspots near you, or if you're housing one of them!
Disabling This Feature on Your Router
XFINITY WiFi Home Hotspots, as it's being dubbed, requires an Arris Touchstone Telephony Wireless Gateway Modem for Comcast to activate the functionality.

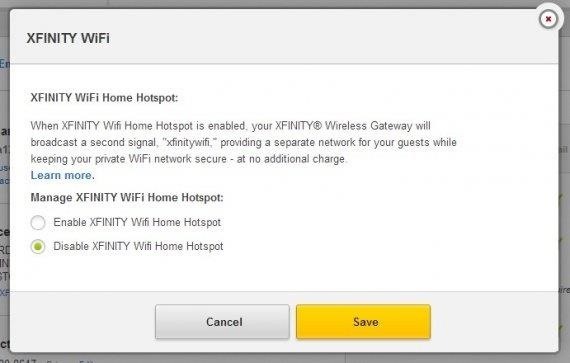
If this is the model of router that Comcast has provided you, and you wish to disable this functionality, Silverman has outlined a few simple steps:
- Log into your Comcast account page.
- Click on Users & Preferences.
- Look for a heading on the page for "Service Address." Below your address, click the link that reads "Manage Xfinity WiFi."
- Click the button for "Disable Xfinity Wifi Home Hotspot."
- Click Save.
After that, you shouldn't have to worry about other folks using your router or any associated risks that may go along with that. The service is currently rolling out through the city of Houston, with more markets to begin testing shortly thereafter.
Hopefully, Comcast has gone to great lengths to ensure that this service isn't susceptible to attacks, but only time will tell what kind of vulnerabilities this poses, if any.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.















3 Comments
Right saw one of these pop up around here the other day. Its up now. This is not a smart move for Comcast.
It has a gui that sends you too Comcast home page to log on to the hotspot.
It looks so safe"Xfinity Wifi Home Hotspot." Cool my house has a hotspot for us... No for everyone in range of the unencrypted signal, even worse it's on your network. Comcast gets -1 for this idea.
After looking into this a bit. It' is not safe and you can see the so called private data portion of the network and spoof macs from it.
Had the same issue since hooking up our new Comcasst modem (required when our phone stopped working). Only problem is, Comcast has gotten wise to your strategy: There's no longer a self-service option to disable the Xfinity Hot Spot on the account page as you described above. The only way I could disable it is to call Comcast customer service, which, as we all know, is a nightmare. 45 minutes later and it's fixed!!
Share Your Thoughts