Welcome back, my rookie hackers!
"How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.
There are a multitude of reasons for wanting privacy for communications on the Internet. I think it goes without saying that every human being has an inherent right to privacy. In our current technological state of surveillance, this right to privacy has been severely compromised. Google, the NSA, and GCHQ are all spying on our private communications.
Furthermore, I believe that we have a right to free communication and uncensored communication. Many nations and companies limit what sites its citizens and employees can visit and view. In some cases, if they do go to certain sites, they are immediately suspected of criminal or anti-government activities (often those two are conflated). In these cases, browsing the Internet anonymously can be a matter of life and death.
Take back your right to privacy on the web by using some or all the technological fixes listed below. Most of these technologies will provide you with some level of privacy on the Internet, and one option in particular can get you almost total privacy (nothing is absolute, but this solution is the best available).
Remember, encryption is your friend.
Option #1: Tor
The Onion Router (Tor) is a specially designed Internet routing system that routes traffic while encrypting the IP address of where it came from. To enable routing, only the last and next IP addresses are available at each hop. The original and all other hops along the way are encrypted and can only be decrypted by a Tor router.
Tor can evade detection from nearly everyone except the most powerful state-owned surveillance machines. Even then, the NSA has some challenges in breaking Tor, but they have and still can. In general, Tor is safe for most traffic, but if someone or some agency wants to spend the time and resources to watch you, they can and will.
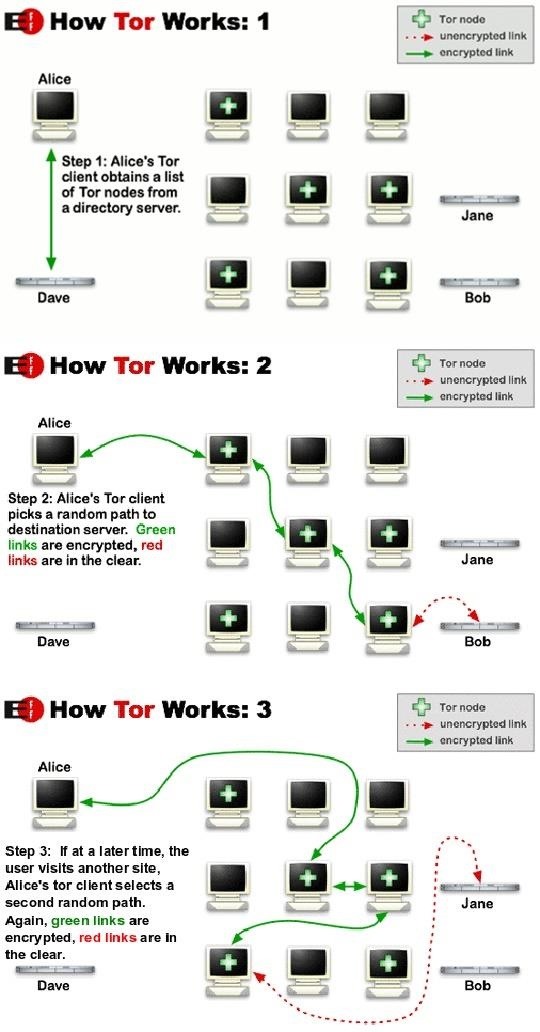
You can access the Tor network by using the Tor browser, which is simply a plug-in to the open-source browser Firefox. You can download it here.
Option #2: Proxies
Using proxies is a tried and true method of obscuring your identity on the Internet. Although your traffic is not encrypted and can be sniffed, the traffic cannot be attributed to any person as the proxies use their IP addresses rather than yours. Of course, this does not prohibit your traffic being tracked by your cookies.
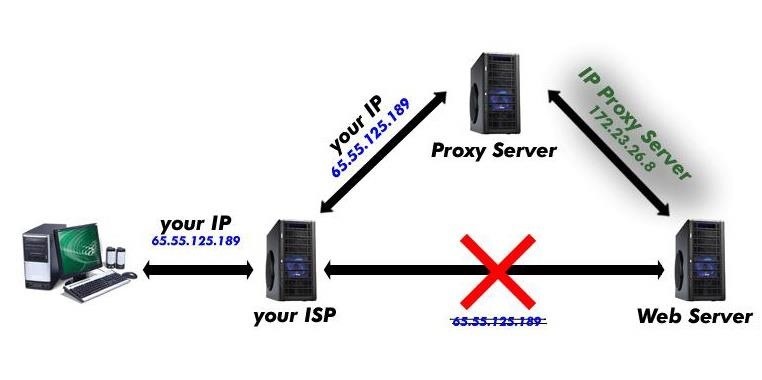
To set up proxies for your Internet traffic in Kali, please take a look at my tutorial on using ProxyChains.
Option #3: VPN
As the name implies, a virtual private network, or VPN, is a private way (encrypted) to connect over a public network (Internet) to a private network. It requires an authentication mechanism and then encrypts all the traffic between the client-to-server or peer-to-peer communication. It can encrypt all communication including the control channels, making it very hard to crack or identify the user.
You can access private VPN services where you will connect to their VPN server through an encrypted tunnel and then browse the Internet with their IP address. All of your traffic appears to be from their IP address and your communication to the service is encrypted so the traffic can not be traced back to you.
By default, VPN capabilities are NOT included in Kali, but I will be doing a tutorial on installing and stetting up VPN services on Kali in the near future.
Option #4: Encrypted P2P Chat or Encrypted VoIP
Often, people want to chat or use voice communications over the Internet. Both can be intercepted and read. There are at least two technologies available to encrypt these types of communications that makes it very difficult to intercept and read.
Chat
For Internet chats, CSpace is among the best. Like so many of these technologies, CSpace relies upon encryption. CSpace uses a 2048-bit RSA key for authentication and each user has a unique public key to identify themselves. Users are only identified by a hash of their public key on a central server. All communication is encrypted with TLS (Transport Layer Security). You can find more information about CSpace here, though, it is no longer in active development.
If the members of Anonymous had been using this service, many of those now serving time in prison (Jeremy Hammond received a 10 year sentence for hacking Stratfor and releasing the information to WikiLeaks) would still be free.

VoIP
For VoIP, consider ZRTP for private voice communication. ZTRP is an open-source (thank the heavens for open-source developers) technology for VoIP communication that authenticates both ends of the communication with Diffie-Hellman and then encrypts the communication with a pre-shared key and salting.
For those of you not familiar with cryptography and password-cracking, salting makes it more difficult for a third-party to break the encryption. This technology (ZRTP) was developed by Philip Zimmerman, the same guy who developed PGP and a longtime advocate for privacy rights (Zimmerman fought the U.S. government all the way to U.S. Supreme Court when the NSA demanded a backdoor to his PGP). As a result, I have a lot of trust in ZRTP.
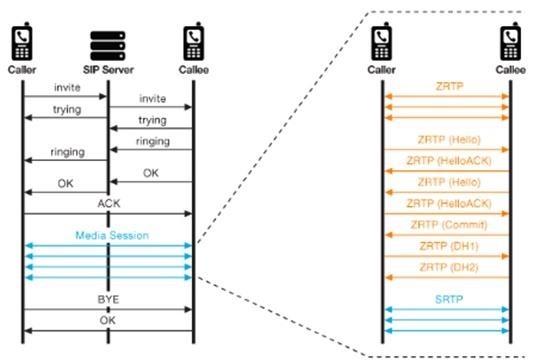
ZORG is an implementation of ZRTP and is available on the Android, BlackBerry, iOS, Linux, Mac OS X, Symbian, and Windows platforms.
Option #5: Combine All of the Above for Ultimate Privacy
When Edward Snowden released confidential NSA documents in 2013, we got some insights into this super-secret snooping agency. In one of these documents, the kindly folks at the NSA rated their ability to snoop on communications when users were using any number of different anonymity technologies. On a scale from 1 to 4, 1 was the least difficult and 4 the most difficult.
According to the NSA, the combination of Tor, a VPN, and either CSpace or ZRTP basically blinds, so this combo received a 4 rating. In their own words, the "good" folks at NSA described these circumstances when trying to surveil users combining these technologies as "near-total loss/lack of insight to target communications, presence."
A Word of Caution
I am very reluctant to use any proprietary, commercial product for purposes of maintaining anonymity. The reason is that these companies easily bow to pressure from state authorities to enable snooping on their networks and products. Although not perfect, open-source products are more likely to give you a greater level of assurance for maintaining your anonymity and privacy.
Keep coming back, my rookie hackers, as we explore the arts and technologies of hacking!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















27 Comments
I'm cautious with Tor, but still use it. I would recommend VPNs, though. The best FREE one is FrootVPN, in case anyone wants to use it. Also, it's log-free... ;)
Thank you for sharing with us all about FrootVPN. Seems highly reliable. I shall start using it right now.
Forgot to ask, how does this VPN compare to paid versions?
Dad
Paid VPNs will almost always be more reliable than free ones, but FrootVPN is fast, 24/7, and no logs. It also was rated one of the highest VPNs on surveys.
I gotta try this. If I put a vpn on my host machine, will my virtual machines also be protected?
No, because the VM is a different client.
Is there any way to get a vpn on my kali linux?
As I said in the article, I will be doing a tutorial on setting up a VPN on Kali.
Alright, great!
Yes, there are many ways. Refer to this video for help:
What I do, when I want to use a VPN in Kali is install OpenVPN on Windows (host), connect to a VPN from vpngate.net and then start my virtual machine with Kali using the NAT network options, so my Kali is in another network that uses my host to go out to the internet through the VPN.
I don't know if this configuration entirely protect my Kali VM for being traced, but when I see the IP address that go out to the internet in my Kali is the same as the VPN. So I think that I'm at least a little bit secure.
I think it depends on how the NIC of the VM is configured. if you put it in : Internal NAT or Host-only then yes your VMs will connect over the vpn tunnel. and if you use Bridged connection (so the VM is in parallel with your host) then NO you VM is not protected
An exemplar of an extremely insightful and useful article.
A few questions for you Guru.
What do you recommend for hard drive encryption? Is it even necassary if all other anonymity methods are followed?
TrueCrypt seemed like a good option, however, it has now been discontinued and is no longer being updated. Do you know of any secure alternatives to TrueCrypt that is actually being updated?
Dad
I found this tutorial very helpful. Thank you.
Very useful for straight forward explanations.
You must have the super power of efficient synthesis.
I'm using TunnelBear as VPN. Also, thank you for sharing CrackerH.
Is TunnelBear free?
Yep. You need to register.
I actually can't tell you more details, pro and cons as I've used it only a few times for testing purposes only.
Hey OTW,
This one's just out of curiosity -
Your own profile states you as an IT Security professional and forensic investigator...then why would you suggest all these tricks which make your own life difficult ?
PS - No offences meant
First of all, Welcome to Null Byte, Bravo.
Second, to learn how to expertly secure your network, devices, etc, you should know how to do an exploit first or at least you know how an exploit works.
Third, OTW know all of these that's why he became an IT Security Professional and as long as he knows how to hack and how things work, he can manage to secure his networks and devices.
Fourth, to answer your question, OTW already knew what he teaches us. There are two reasons why he tells us these stuffs:
You should know how to create a virus first or at least know how it is created before making an antivirus. Same goes with securing one's computer.
Correct me OTW
If I may pose a hypothetical question on anonymity for OTW or the other contributors more knowledgeable than myself; I purchase a laptop for cash and do nothing with it for several months until the CCTV of the shop from which I purchased it is more than likely overwritten. Using public wifi I download Kali and use a live USB to run it on my laptop. I use cash to purchase an antenna capable of packet-injection and follow the excellent tutorials on Null-Byte to crack the passwords for a few APs that are nowhere near my home address, but that I can spend time on without being obvious to the public or picked up on CCTV. I use proxychains to further obscure my initial point of access to the internet. On the assumption that I'm not foolish enough to log on to my Facebook account using this machine is there any way that whatever I do online could be tracked back to me?
Hi, we need help getting started with notepad++ thanks geniuses!
How about you post that to the forum?
I am currently using a VPN, but I'm wondering, would I be more protected if I used another one?
Dad:
Full disk encryption is necessary. It is your defense of last resort.
Grab a copy of truecrypt v7.1a before they're gone, it is still available lots of places, and it is secure.
Other good option, if your use linux, is to use LVM and LUKS encryption. One good feature of LUKS is the ability to backup the keystore (so it can be restored later) and nuke the on-computer keys. I store my backup heavily encrypted in the cloud and always nuke my laptop keys when traveling. When I get to destination (or more correctly, when I and my laptop get to destination) I boot my laptop with a LiveCD, download, decrypt the keys and restore the LUKS keystore. Hard drive is completely useless to anyone until the keys are restored. LUKS Nuking is clearly described on the Internet.
If you use Windows a dual boot solution (with windows and a really minimal linux) might allow you to use LUKS with Windows. I will have to give that one some thought.
Hahahaha yes nuking is very good. Reminds me of a time in the past when I was even more of an idiot than I am now. Forgot to backup the header after I nuked my drive XD.
Tor,VPN,Proxy all these slow down speed of connection.
Well, of course they do.
can you make just one tutorial mixing between below or adding any others to increase security and anonymity? would be great to show how to connect everything together... i'ts easy to configure everything separately but some challenge for me to make them work together
| VPN | TOR | IPTABLES | PSAD | FWSNORT | CLAMAV | HAVP | DNSMASQ | DNSCRYPT-PROXY | PRIVOXY | POLIPO | AUTO MACCHANGER | PROXYCHAIN |
Share Your Thoughts