Welcome back, my budding hackers.
So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.
Wireless Hacking Requirements
When it comes to Wi-Fi, the question I probably get asked most often is, "Which wireless adapter is best for hacking?" Well, let's find out.
#1. Good Wi-Fi Hacking Software
Before we address the hardware necessary to hack wireless networks, let me once again recommend the Aircrack-ng suite of hacking tools. Nothing else in our open-source world quite compares to the power and versatility of Aircrack-ng.
#2. Fast & Powerful CPU
A fast multi-core or multi-processor CPU is certainly helpful. When cracking WEP passwords, which is a statistical crack, you need to crunch a lot of numbers, and the faster the CPU the better. The WPA2 crack basically involves crunching millions of password hashes, which is also very CPU-intensive. So, the faster the CPU, the faster you can crack wireless passwords.
One caveat, though. The difference in speed is not huge. You can only expect a 20 to 50% improvement in hacking speed between the slowest modern CPUs and the fastest. More cores, on the other hand, will improve performance significantly.
#3. The Right Wireless Adapter
Beyond the two primary tools listed above, the next most important requirement is good wireless adapter. To really be effective at wireless hacking, your wireless adapter should have two primary features.
- The ability to enter monitor (promiscuous) mode.
- The ability to inject packets and capture packets simultaneously.
A wireless adapter that can't do these two critical features doesn't mean that you won't be able to crack wireless, but it will mean that it will be so slow that it renders it effectively impossible. Wireless hacking in a world of WPA2 encryption can be a relatively slow process with the best equipment.
If you are hamstrung without a proper wireless adapter, you might as well quit before you begin.

Monitor Mode
Network adapters, whether wired or wireless, are designed to only capture and process packets that are sent to them. When you want to sniff a wired connection and pick up all packets going over the wire, you put your wired network card in "promiscuous" mode.
In the wireless world, the equivalent is monitor mode. This enables us to see and manipulate all wireless traffic passing through the air around us. Without this ability, you are limited to using your wireless adapter to only connect to wireless APs that accept you and authenticate you. That is not what we are willing to settle for.
In the Aircrack-ng suite, we need to be able to use Airodump-ng to collect packets.
Packet Injection
Most wireless attacks require that you be able to inject packets into the AP while, at the same time, capturing packets going over the air. VERY few wireless cards are capable of doing this.
As you can imagine, wireless adapter manufacturers are NOT looking to add features to their standard wireless adapters to suit OUR needs. Most wireless adapters built into your laptop are designed so that mom and dad can connect to AOL and send their email. We need something much more powerful and versatile than that.
If we can't inject packets into the AP (in Aircrack-ng, this is the function of Aireplay-ng), then it really limits what we do.
For instance, in our WEP attack, we will be forced to passively wait for packets to traverse to air in order to capture the ever valuable and vulnerable IVs. Since we need to capture around 500,000 to crack WEP, we could be waiting for days and weeks on a little used AP. With packet injection capabilities, we can reduce that to a few minutes by injecting the AP with ARPs.
Linux vs. Aircrack-Ng Compatibilty
The first issue we need to address in choosing a wireless adapter is making certain that it has drivers for Linux. In 2017, most wireless adapters now have Linux drivers, but that wasn't always the case.
It's important to note, though, that Linux compatibility is far from being an optimal wireless hacking adapter. It is only a minimal requirement.
Probably the most important feature we need is compatibility with our software of choice, Aircrack-ng. The developers of Aircrack-ng maintain a compatibility list on their website that includes all of the adapters they have tested and their level of compatibility.
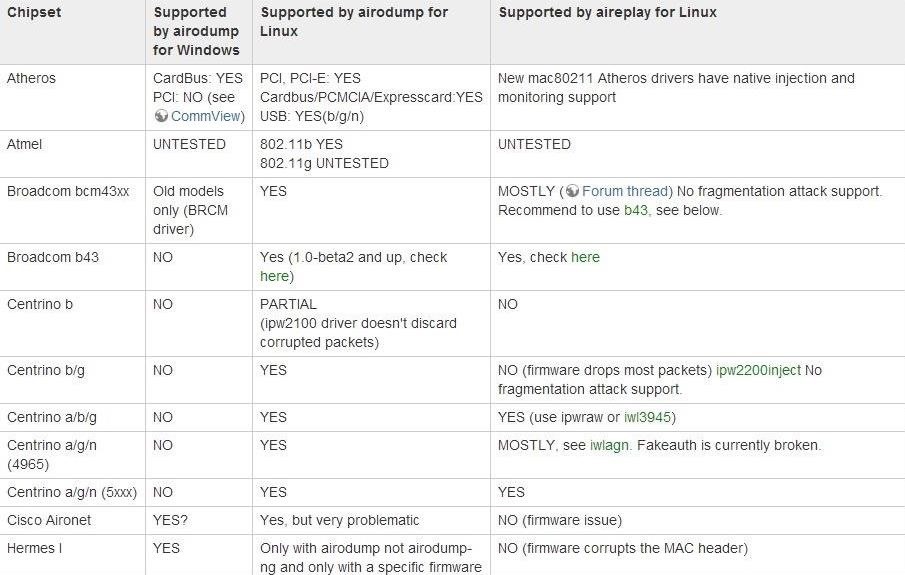
Note that you will need the chipset for your wireless card to find its compatibility on this chart. The first column indicates whether the chipset is supported in Windows for Airodump-ng (packet capture in monitor mode). The next column indicates whether that same capability is available in Linux for that chipset card. Finally, the last column indicates whether that chipset is supported for Aireplay-ng (packet injection) in Linux.
Internal vs. USB
If you choose to install Kali or BackTrack in a virtual machine (VMware or VirtualBox), you will need an external wireless adapter. This is because the virtual software hypervisor "pipes" your wireless access to a wired connection in your virtual machine. As a result, Kali does not have a wireless device to work with.
Since most built-in wireless adapters in your laptop are probably inadequate to crack wireless, you are better off purchasing a USB wireless adapter for wireless hacking. For long-range, our community recommends the Alfa AWUS036NHA Wireless B/G/N USB Adaptor. For a more discreet form factor, the Panda Wireless N USB Adapter is the most popular adapter among our newer hackers.

If you choose to install Kali as a dual boot system, you can use your built-in wireless adapter for wireless hacking, if its on the Aircrack-ng compatibility list. Although you can hack with wireless cards not on that list, you had better be very patient as this process make take you days or weeks without the proper adapter.
To effectively hack Wi-Fi passwords, you will need a proper wireless adapter. Make certain that you check the Aircrack-ng compatibility list to make certain that your wireless adapter has the necessary features to make your Wi-Fi hacking fast and effective.
If you're looking for a low-cost way to jump into Wi-Fi hacking, consider grabbing a $35 Raspberry Pi with your adapter to build a Kali-based hacking computer on a budget. You can check out our guide here on setting it up.

To learn more on this subject, stay tuned to my Wi-Fi Hacking series.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















98 Comments
Hi OTW,
would like to ask if we were to use Kali LIVE USB "persistence", can we still use the built in wireless adapter in the laptop, provided the wireless card can support monitor mode and can do packet injection ?
i am guessing yes right ? since it is boot from bios ? correct me if i am wrong. Thx
Will this be a good wifi network adapter?
yes
might sound very silly but iam new to this
will this wifi adapter work with kali linux running on vm workstation 10
i would really appreciate your help
many thanks for your time
Yes
many thanks for the help
yes it will work
he asked my question for me.
that's the same adapter i was going to buy.
it can do both monitor mode and packet injection?
perfect, thanks OCCUPYTHEWEB.
Are there any recommended websites you can upload captured WPA/WPA2 packets for decryption, save using your own resources & to improve speed and the likelihood of cracking the encryption.
David:
If I understand your question correctly, many people use the resources of AWS to speed up decryption. Also, using a multiple GPU's rather than a CPU or botnet also will speed up decryption.
OTW
will this work?
Is it on the aircrack list?
"TP-LINK TL-WN722N v1
FCC approval date: 18 November 2009
(Est.) release date: 10 November 2009
UPC: 845973050467 (UPC DB, On eBay)
EAN: 6935364050467 (UPC DB, On eBay)
Amazon image
ASIN
B002WBX9C6 (Flag of the United States.svg, On Amazon, On CCC)
Interface: USB
USB 2.0
Connector: Male A
Form factor tags: dongle
ID: 0cf3:9271 (6 addl. devices)
Windows: USB\VID0CF3&PID9271
FCC ID: TE7WN722N
Chipset: Atheros AR9002U
WI1 chip1: Atheros AR9271
Probable Linux driver
ath9khtc (in backports, open firmware)
USB ID first seen in kernel v2.6.35 (2010-08-01)
(see also passys)
Windows driver
try this, if it doesn't work let me know
Antenna connector: RP-SMA
bgn, 1x2:1
OUI: D8:5D:4C (3 E, 6 W, 2010):"
I'm looking for Aircrack-ng compatible WIFI USB that's affordable maybe something that i can possibly hack to attach a high gain antenna
Check out the Alfa USB adapters.
TL-WN7200ND this has a higher power transmit which helps in evil twin creation, but will this support monitor mode and packet injection?
on alpha which one i want to buy for both pentesting and monitor mode am using kalilinux 2017.3 32 bit in a virtual machine and my corrent OS is windows 10 64bit
okay thanks
Hey OTW,
I really need your help. I bought the AWUSO36NH usb wireless adapter, but it doesn't seem to work with kali in my virtualbox. I downloaded the driver (the RT2870 for windows) and the virtualbox extension pack, and i updated and upgraded everything with apt-get.
On my Kali Linux settings i use network bridge adapter, and i added my network adapter to the usb section.
I hope you can help me with this information, but since im new to this all, please reply and tell me to send more information if you need. Otherwise, please tell me why it's not working. Please help me.
A different name but the answers the same..
ALFA Network AWUS036NH
Manuf/OEM/ODM AWB WUS620-H-JET
FCC approval date: 19 July 2010
EAN: 4718050300235 (UPC DB, On eBay)
Country of manuf.: Taiwan
Amazon image
ASIN
B0035APGP6 (Flag of the United States.svg, On Amazon, On CCC)
Interface: USB
USB 2.0
Connector: Female Mini-B
Form factor tags: corded (modular) adapter
ID: 148f:3070 (18 addl. devices)
Windows: USB\VID148F&PID3070
FCC ID: UQ2036NH
WI1 chip1: Ralink RT3070
Additional chips
2.4GHz Power Amplifier IC;Skyworks;SE2576L;;1;
Probable Linux driver
rt2800usb (in backports) or rt2870sta
USB ID first seen in kernel v2.6.31 (2009-09-09)
(see also passys)
Windows driver
see MediaTek's website
Antenna connector: RP-SMA
bgn, 1x1:1
Flags: high power, schematics
OUI: 00:C0:CA (5 E, 22 W, 2010)
Thanks for your quick responce! Does this mean i have to download rt2870sta as a linux driver and it will work? Do i download this driver while in my virtualbox or just on my host os? Thanks man
I would surmise that you need to compile a driver on that Vbox. It will need to be compiled locally to make sure it grab it's deps. Either the sta ble or the back port if the sta is not functioning correctly.
if you google that chipset it has many posts on the issue and remedy.
As far as getting it to load in VM, CIUFFY has made many posts on connecting USB WiFi to VM successfully .
Me. I would of just got the regular alfa because you paid extra bucks for nothing but it saying n band when the cheaper one will connect to mixed n bands already and 100% plug and play. They both have exact same specs otherwise.
CHH,
I succesfully installed the Powerwifi USB RT3070 v2.3.0.0 driver. (i installed the RT2870USB(RT2870/ RT2770) v2.4.0.1 first, but got the same error) I followed several tutorials but everytime i reached the "make" command, i got this error 2:
I have no idea what to do about this. Any ideas?
OTW I really need your help!
So I got the AWUSO36NH and installed everything on kali (apt-get for update and linux headers). I had some problems with 'make' but finally fixed that too. So I updated everything and installed the rt2870sta drivers in linux, so it should be working, right? But it doesn't. I added my USB in the settings at virtualbox, but when I start up kali linux from virtualbox and connect the usb adapter to my computer, it won't connect on 'iwconfig'... "lsusb" only shows this:
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Bus 002 Device 002: ID 80ee:0021 VirtualBox USB Tablet
Bus 002 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
I blacklisted the rt2800usb, I followed alot of tutorials and honestly I'm kind of desperate at this point. I know you have the same wifi adapter as I have, so can you please help me out here?
Can i use this 150Mbps Wireless N Nano USB Adapter
TL-WN725N
Pavel:
You can check on the www.aircrack-ng.org website.
OTW
Version 1 or 2?
Side note: Looking at it being a nano if the chip set is supported your attack area is very small due to antenna size.
When you are able you should upgrade to a more powerful antenna if you think you will be using packet injection more than a little bit.
TP-LINK TL-WN725N v1
EAN: 6935364050719 (UPC DB, On eBay)
Country of manuf.: China
Interface: USB
USB 2.0
Connector: Male A
Form factor tags: nano dongle
ID: 0bda:8176 (17 addl. devices)
Windows: USB\VID0BDA&PID8176
FCC ID: TE7WN725N
Industry Canada ID: 8853A-WN725N
WI1 chip1: Realtek RTL8188CUS
Probable Linux driver
rtl8192cu (in backports) or Realtek's vendor driver
USB ID first seen in kernel v2.6.39 (2011-05-19)
(see also passys)
Windows driver
see Realtek's website
Antenna connector: none
bgn, 1x1:1
OUI: none specified
----------------------------------------------------
TP-LINK TL-WN725N v2
FCC approval date: 02 April 2013
Country of manuf.: China
Interface: USB
USB 2.0
Connector: Male A
Form factor tags: nano dongle
ID: 0bda:8179 (2 addl. devices)
Windows: USB\VID0BDA&PID8179
FCC ID: TE7WN725N
Industry Canada ID: 8853A-WN725N
WI1 chip1: Realtek RTL8188EUS
Probable Linux driver
8188eu (vendor driver)
precompiled binary driver for the RPi (Raspbian)
USB ID not yet observed in any mainline kernel / this list
(see also passys)
Windows driver
see Realtek's website
Antenna connector: none
bgn, 1x1:1
OUI: 0C:82:68
OTW i have a question. i read that with a gps reciever connected to my laptop i can get the location of the access point. so i could use this to find out which house the AP is in? If so could you write a tutorial on it or just explain to me what tool i can use that will show me Geo-location?
Chris:
With a GPS receiver you can get the location of YOUR AP. It will not give you other people's AP.
You could simply walk around your neighborhood with airodump-ng running and map the location of the AP by the strength of signal.
Google maps the location of every AP by gathering the GPS info from the phones that connect to the wifi AP.
OTW
Airodump-NG CSV Visualizer v0.1
Fore advanced stuff you can perform using Airodump-ng output files.
This is fantastic web based tool to Visualizer Airodump-ng output files.
The Airodump-NG Scan Visualizer takes the XML/CSV output given by Airodump-NG and will allow the following:
Allow search / sort / filtering on different properties like Channel, BSSID, ESSID etc. in a table visualization
Automatically create graph and charts for quick understanding of the network around
Create custom reports
The tool will be deployed in the beginning as a Hosted Service available to everyone and transition to a downloadable bundle at a later stage once its stable enough to be released.
http://wifiscanvisualizer.appspot.com/
Sample:- http://wifiscanvisualizer.appspot.com/visualize/f288f030c0ee11e4966c59911fae7d95
More Information:-http://community.pentesteracademy.com/t/airodump-ng-scan-visualizer-tool/1214
Hi, I am having some problems with a wireless adapter. I bought the ALFA AWUS036NH but found out that it does not have a driver for OS X 10.10 (Yosemite). Now I am struggling to find an adapter both on the aircrack's list of compatible adapters and with drivers for OS X 10.10.
Can anyone help me out a bit? Thanks.
Are you running Kali or aircrack-ng in OS X?
Kali on VMware
Kali on VMware Fusion.
Then, you don't need OS X drivers. You attach the wireless card directly into the VM, bypassing the host operating system. The Alfa should work for you.
I am also struggling to find sufficiently latest linux drivers. The latest one available is kernel 2.3.37. Is that good enough?
Thanks again
Thanks a lot.
Can Anyone tell me the speed of alfa NHA,NH of checking PINS in reaver,which is best for reaver
Hi there can someone give a hand please?
I have an Ralink RT3070L and I'm getting some issues using packet injection with aireplay-ng (for WEP) - I get something like "Read 12054 packets (got 25 ARP requests and 0 ACKs), sent 0 packets...";
I belive the chipset isnt able to inject but I'm not sure - google isn't beeing a pal in helping me out (or I'm doing the wrong questions).
I've tryed the Aircrack-ng page but I can't seem to find any info.
Thanks in advance
Jansen:
Did you check to see whether that chipset is compatible with aircrack-ng? I don't believe it is.
OTW
At the aircrack-ng site doesn't it or it isn't... I must have to assume it isn't some I saw some post (in other sites) that it was possible...
I'll try to test with other dongle.
Thanks anyway,
Cheers
What brand of adapter is it? 152 adapters with RT3000U (rt 3070) family chip set in it
By the way search on WHT found this... Thought that chip set sounded recent.. https://null-byte.wonderhowto.com/forum/problem-with-rt3070-chipset-kali-0159005/
Error Occurred
An unexpected AJAX Error occurred.
OK, I tried to post a comment but I kept getting the above message. The post was quite long. Is there a limit to the number of characters allowed in a post? Was that the cause of the error?
Been reading through the various lessons and categories of lessons on this brilliant site. Just one problem. After spending many hours each night reading and then re-reading those lessons I always come away confused and none the wiser.
I am a noob, for sure. This will become evident in my future posts, and there will be many future posts made by myself because I'm very interested / captivated by the whole area of hacking. I am determined to get to grips with using Kali and knowing how to hack wifi etc. I have to offer my thanks at this point to the authors of this site. You have sparked an interest in me which seems to have extremely quickly become a passion!
Things that cause me confusion? What is the difference between a wireless adaptor, a wireless card, an external wireless adaptor, a USB wireless adaptor? These various terms have been used in the above article and confused me. Do I need a wireless card or a wireless adaptor to be able to hack. Or, are all these the same thing, just being called by different names?
The above article states that most built in wireless adaptors are inadequate to adequately crack wireless and one is better off purchasing a wireless USB adaptor for wireless hacking. Yet further down the article it says that if you chose to install Kali as a duel boot system you can use your built in wireless adaptor for wireless cracking. I thought the article said that most built in wireless adaptors were inadequate to adequately crack wireless?
With reference to the 'Internal vs USB' wireless adaptor decision and the discussion around installing Kali or BT in a VM environment, I was totally confused. The article states that if Kali or BT is installed in Vm an external adaptor is required because the virtual software hypervisor 'pipes' the wireless access to a wired connection in the virtual machine. As a result Kali does not have a wireless device to work with.
Here is what confuses me about that. Even an external (also known as a USB?) adaptor (sometimes called a wireless card?) is wired connection since the wireless adaptor is connected to the vm by a USB cable connection?
Totally confused. Hoping someone can clear these things up for me to enable me to move forward with a clearer understanding.
I am dreading downloading and installing the Kali OS (or at least I understand it is an OS and not an application, although it does have a number of applications (?) within it such as aircrack etc). From what I have read so far it is likely going to be a nightmare to install.
Do I duel boot with my Windows 8 OS, do I install in a VM or do I live CD? I keep reading and re-reading about that area but can't quite get the gist of what is the best way to install Kali, i.e. the pros and cons of each installation choice.
Sorry for the long post but it's how my brain works.
Wow! That is long post.
First, you can use your internal wireless adapter on a dual boot system, but it will be so slow as to be rendered useless. Yes, it can be used, but not practically.
If you use an external USB wireless adapter, the VM see it as a USB wireless adapter.
As a beginner, I recommend using a VM.
I strongly suggest that you download Kali and begin, rather than just reading. Everything will make more sense once you start.
OTW
Thanks for the advice OTW. Should I use VirtualBox or VMware Player as the VM ?
I found a site (http://www.drchaos.com/the-ultimate-installation-guide-for-kali-linux/) that seems to offer precise instructions for downloading and installing a Kali Linux VMware ISO. I haven't been able to find the same degree of precise instruction for installing Kali on VirtualBox.
I only mention these two particular VMs because they are free. If there is a paid VM that you would recommend as being a better alternative I am open to suggestion.
Regards
Worm
VMWare is the best, but it is NOT free
One question:
For WPA, wich is better, CPU or GPU cracking?
I've been reading that GPU (AMD) is the best way
GPU is much faster.
Thanks for the reply and one last question if I may:
If i try to "find" a hex password with 10 to 12 chars lowercase, wich will be best: using a rainbow dictionary or a brute force techinic (using rules)? Or is the same?
Thanks
I knew this hacking stuff would be hard to get to grips with. The best stuff always is hard to understand though. If it were easy everyone would be doing it and that would make it boring, right! ;)
But, I am struggling at the very first steps. Not a good omen. I received my wifi adaptor (AWUS036H) this weekend (ordered off EBay) and I downloaded Oracle's VirtualBox (latest version 4.3.28 r100309).
I then downloaded Kali 64bit from Kali.org and proceeded to create a new operating system environment in VB. The dropdown list on VM only offered 32bit for the Linux OS. In fact it only offered 32bit for all the OS options.
Yet, when I looked on the Web I found a few sites (that described how to install Kali on VB) that showed VB offering Linux OS 64bit options.
So, now I must dump the 64bit version of Kali and download the 32bit version because the seemingly latest version of VB I have does not support 64bit Kali.
I will let you guys know how I get on as soon as I download the 32bit Kali (Torrent) version and attempt to create a new OS environment in VB. This last step looks totally daunting judging by the 'help' sites I have visited that offer assistance / guidance with installing Kali on VB.
Would it be easier just to download a Kali Linux VB image rather than the generic version? Kali.org are offering the Kali ISO image for VB as a download. Although when I navigate to the page all I can see is the VMware images and no VB images to download. Or is the VMware image compatible with VB?
Any help appreciated
Worm
Received my wifi adaptor (Alfa AWUS036H). Plugged it in to my laptop and could see straight away that the number of wifi signals I could receive had significantly dropped.
With my in-built (Atheros AR9485WB-EGI) wifi adaptor I could detect up to 5 different wifi networks. But with the AWUS036h I can detect only 2 networks, and one of those is my own router!
Any ideas what I might be doing wrong, i.e. why I am detecting fewer signals with the Alfa? I was under the impression the Alfa was a more powerful / sensitive wifi adaptor than a standard internal adaptor.
Yeah that's pretty odd results. I get on average 100-150 more AP's when I plug in the Alfa. Move it around a bit you may be getting RFI off something like a microwave, cell phone or something.
Thanks for the reply Cyberhit.
Turns out the aerial that came with the wifi adaptor was faulty.
I ordered the AWUS036H. It states on the label stuck on the back of the adaptor that the adaptor is an AWUS036H. Yet the driver CD that came with the adaptor when loaded states that it is for the newer AWUS036NH. That confused the hell out of me.
Have I been sent the correct driver software? When I try to install the driver for Windows 7 from the CD (I have Win 8 on my laptop but there is no Win 8 option to choose on the CD) I get the message, sorry, the computer system is not supported. So, I can't even load the diver for Win 7. So, I have had to load some driver that was on the CD that at least gets the adaptor working on my laptop but I am not sure what version of Windows the driver I installed is meant for.
I am not even sure if it is the correct driver or if my adaptor is functioning at full capacity or just ticking over on an incorrect driver? How can I tell? Can anyone recommend a Win 8 driver for the AWUS036H?
Thanks in advance for any help offered.
Worm
You sound like they gave you the wrong drivers. Go to their website and get correct drivers or better get slim drivers (app) and update all your drivers for free and fast.
Okay, so I am slightly confused in this topic as well, but the biggest reason for my confusion is to the reason why nobody as popped the question to you (OTW) as to what network adapter you use as an elite hacker (professional?). So, the question is as follows. OTW, what network adapter(s) do you use? Also, Internal? External? Both? (Not trying to pry, haha, I just would like to know what an elite uses)
The Alfa AWUS036H is an excellent, inexpensive and plug and play external wireless adapter that is aircrack-ng compatible. I recommend it.
As for which one I use, that is proprietary information.
Alrighty. And okay, understandable. Anonymity is key. Never let the world know you were there even after all is done.
Thank you for the recommendation on the wireless adapter sir. I'll pick one up ASAP.
can some one tell me do i need wireless adapter to hack wifi or can i hack with my own internal adapter please help me.
When you mean internal adapter, you are saying an PCI card or some embembed system on your motherboard?
You can test the macchange command or the monitor mode on both and check if they work. If they do, great, you can do it, if not, buy a USB dongle or so.
I'm in favour of using a USB dongle, because:
1 - If in a worry you can disconect fast as pulling a plug;
2 - Ease to change/switch
3 - Easer and faster to disposel
4 - You can use a longer USB cable to extend your wifi range without loosing serious signal power (that is what happen with an PCI card and you have to connect to a farther antenna)
5 - Antenna mods for wirelless dongles are cute and easy to make
Depends on the internal adapters chip set. One of my internals works just as good as my alfa just not the range. Easy fix just script a network shutdown shortcut.
As Jansen was saying tho the External opens up some different options with mounting and flexibility.
man i have to make new account because i forgot my password but thank you cyberhitchhiker and jansen smith,hey can you give me best suggestion plz guys i am buying a new laptop upto $700 laptop for pentesting and i don't know anything.thank you
Anon Pratik I belive is better to post your question in the forum, is more apropriated and you will get more viewers and some straigh anwsers.
Cheers.
ok bro thank you just curious..
http://www.amazon.com/Alfa-AWUS036NHA-Wireless-Adaptor-Compatible/dp/B004Y6MIXS/ref=sr_1_1?s=electronics&ie=UTF8&qid=1437832297&sr=1-1&keywords=Alfa+AWUS036NHA
Would you recommend this, or are there better and cheaper adapters than this?
That's good one, but for ease of use, get the AWUS036H.
Thank you.
Please tell me if this will work >>>
Please inform me about the flaws of each of them and will any one of those work ?
Go to www.aircrack-ng.org to see the compatibility list of wireless adapters.
I don't see any of the above there .... please tell me which one to use .. ?
Can't I use them if they're not listed ?
If they are not on the list, they won't likely work. Many are using the Alfa cards. They are inexpensive and effective.
i use a TP-LINK TL-WN722N works great for aircrack-ng and Ettercap haven't found anything it wont do as of yet, and it supports a WiFi antenna, i also use a alfa network 1 card and that works great too! this can be set to a higher TX power than the TP-LINK
I was actually looking for some AC version of the Alfa adapter, but since it's using a (currently) esoteric chipset (RTL8812AU) I guess it's not worth it. Also found hints claiming problems with kali/aircrack in the (kali forums.
Does anyone know of a great long range dual band adapter that works with linux/kali/aircrack-ng?
How about this adapter? The Alfa AWUS036EAC?
http://www.amazon.com/gp/product/B00WC4C3X4/ref=ox_sc_act_title_2?ie=UTF8&psc=1&smid=A2LM6ZPY06LT1N
Hi OTW,
I have installed kali 2.0 in virtualBox, when i am booting the OS it is not detecting the external usb Wireless adapter. but the adapter is shown in lsusb command, i am new to this so could you please tell me what i am doing wrong , or point me to right direction
When i am booting the kali form usb it is able to detect the wireless card and showing in iwconfig command.
Hallo Hallo,
It is the settings in your VM more than likely. About 73 posts on this site about people not being able to see the card in VM because they didn't add it in the settings as recent as 24 hours ago in another thread..
Search up there.
Hi. I'm looking for a good solid adapter for kali that can do all the things a expensive one can but for half the price. I know alfa adapters are good but they range from $30 - $40 . I'm looking for something priced about $15 (give or take). Any suggestions?
i got an acces point in client mode ( i see lots of networks) , so i got a wifi card and install it on my PC- but i see no network. Is there a way to make my Acces point to send signal with networks it gets to my wifi card so i can try to use aircrack ? ......
so what i mean is, i i want to see and connect with my card to what my acces p. see .
i have a intel Corporation Centrino Wireless-N 100 adapter build in
is this any good???
I have TP-Link wn722n wireless adapter. I changed its mode to monitor through airmon-ng. I am using kali linux to hack wifi, I have tried all tools in kali linux for hacking wifi, but it is not capturing the WPA handshake... Help me please to solve this problem
Hello, I'm beginner to hacking. after a big search on the internet i found this. Is it fine ?
I am using Kali thorugh Virtual Box in a Mac. Anyone has a suggestion for a card which I can use?
Can anybody tell me if i can use this USB Long Distance Range WiFi Antenna Booster Wireless with kali linux and if it is any good to use to hack wifi my own of course, But just want to learn so if anybody can take a look at the link on ebay of the device or if anybody knows any i can get for long distance for around £15 to £20. Thanks all
http://www.ebay.co.uk/itm/USB-Long-Distance-Range-WiFi-Antenna-Booster-Wireless-Outdoor-Indoor-Mounting-/262924471428?hash=item3d37850c84:g:GvkAAOSwAANY5LrF
should I use this ? will it scan wifi networks in kali virtual machine.
Only if it's v1, not v2
I love your tutorials, and thanks for sharing your knowledge with me.
I am wanting to buy the The TP-LINK TL-WN722N 2.4 GHz, but don't how do I differentiate between the v1 and v2. How can I be sure I get the right one?
Thanks,
Thiv
Helo
I'm running kali in usb persistent.
why cant it access the internal network adapter even for a internet connection
do I have to install some drivers ore anything or is it not possible to access the internal wifi adapter in live usb mode please tell me sir
I just got the AWUS036ACH, I have searched the ends of google and YouTube to find an answer on a driver issue that I am having. I see that it is being used effective and efficiently. Long story short, I get dmesg "8812au unknown symbol vfsread (err 0)
I'm sure that's what is not allowing my card to show up in iwconfig, however dmesg sees the card when it's plugged in. Any help is greatly appreciated or just point me in the right direction( I love to learn)
Hmm, your short story is too short. Are you on arch linux?
I apologize if I come off sounding new as hell, but I am currently trying to learn Linux and the version I am on right now is the 2017.3 build of Kali. I'm not sure if that helps out at all. I want to learn as much as I possibly can about the other side of computing. I truly do thank whomever takes the time to teach me any facet of this "new" OS. We all start somewhere re. If you need anymore info please ask me. I really want to get this adapter up and running.
Did you try the advice on the Amazon page from the guy complaining that it sucks but that you can get it running and how? Best advice I saw so far, but we'll be testing and maybe doing a write up on this soon.
Hi , i just want to know some things maybe some stupid but i really want to know:
1.- it is really feasible to use a 16-26-32 dBi ubiquiti nano station to get a far away wifi signal, hack it and use it as your ip to launch an attack ?(just like Mr. Robot did with a pringles cantenna)
2.- can you actually use the same nano station to make a wifi hot spot for MitM attacks?
i don't really know if i´m being enough clear but i believe you get the point, any help/ideas will be welcome.
Thanks in advance you guys
Hey i have dual bootes my kali linux and windows 10 on my laptop do i need a wireless adpater to jam wifi networks and hack wifis
My question has to do with the extent of vulnerability to one's system while following the principles of ethical wireless PenTesting in a virtual environment.
Just like rule #1 of lock picking: don't pick locks you're not authorized to pick. Instead, buy practice locks and have a blast! Along those lines, I have a virtual lab with a VM running Kali (and other OS) on a MacBook Pro. Also, I have ethical PenTesting books for reference.
My question is: to what extent do I become vulnerable (or do I become more vulnerable) to malicious attack while taking part in Wi-Fi PenTesting in a virtual environment according to ethical principles? Also, does wireless PenTesting using the Alfa AP open my system up for others to easily walk through an "open door" into my system? Does virtualization offer an element of protection?
I realize the correct answer to these questions would be: "don't begin a test that you don't know exactly what the consequences will be." Yet, part of learning is asking these types of (dumb) questions. The books walk the user through the steps and I researched qualifications of the authors, but vulnerability was not specifically addressed.
Thanks.
Share Your Thoughts