Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.
As of this article's writing, Nmap is over 21 years old. Some of you reading this article right now might not be as old as Nmap. This is a testament to Nmap's usefulness over the last two decades. While there are several worthy port scanner alternatives, Nmap is still as useful a security tool as it was in 1997.
One lesser-known part of Nmap is NSE, the Nmap Scripting Engine, one of Nmap's most powerful and flexible features. It allows users to write (and share) simple scripts to automate a wide variety of networking tasks. Nmap has a comprehensive collection of NSE scripts built in, which users can easily utilize, but users can also create custom scripts to meet their individual needs with NSE.
Using NSE Scripts to Find More Vulnerabilities Faster
Here, I'll be demonstrating two similar premade NSE scripts at once, nmap-vulners and vulscan. Both scripts were designed to enhance Nmap's version detection by producing relevant CVE information for a particular service such as SSH, RDP, SMB, and more. CVE, or Common Vulnerabilities and Exposures, is a method used by security researchers and exploit databases to catalog and reference individual vulnerabilities.
For example, the Exploit Database is a popular database of publicly disclosed exploits. Exploit-DB uses CVEs to catalog individual exploits and vulnerabilities which are associated with a particular version of a service like "SSH v7.2." Below is a screenshot of a possible exploit on the Exploit-DB website ... notice the CVE number assigned to this particular SSH vulnerability.
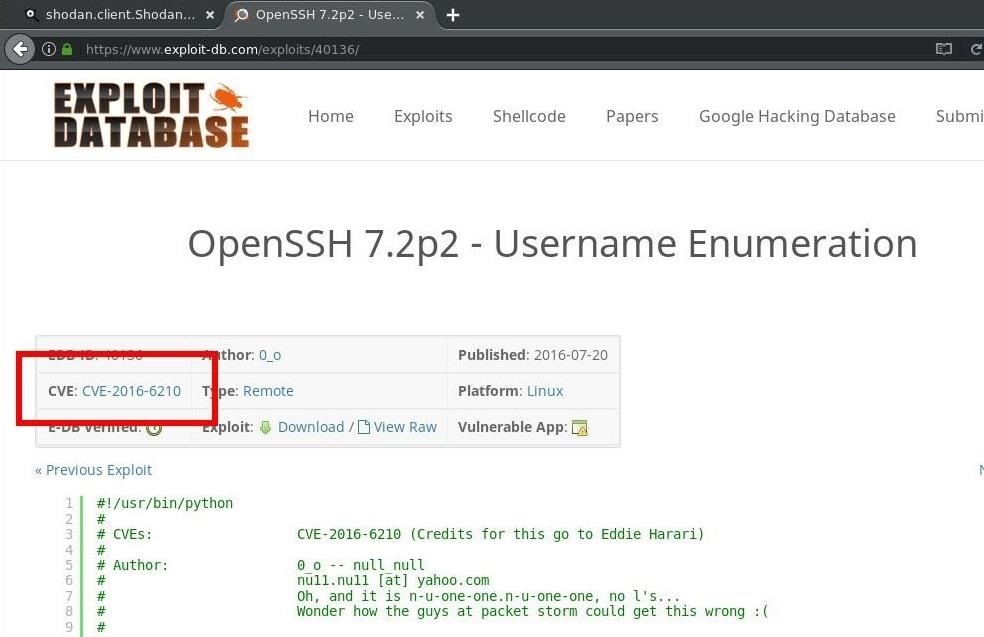
Both nmap-vulners and vulscan use CVE records to enhance Nmap's version detection. Nmap will identify the version information of a scanned service. The NSE scripts will take that information and produce known CVEs that can be used to exploit the service, which makes finding vulnerabilities much simpler.
Below is an example of Nmap version detection without the use of NSE scripts. Nmap discovered one SSH service on port 22 using version "OpenSSH 4.3."
nmap -sV -p22 1##.##.###.#21
Starting Nmap 7.60 ( https://nmap.org )
Nmap scan report for 1##.##.###.#21
Host is up (0.58s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)And here's an example of that very same server using the NSE scripts. We can see there's a much more informative output now.
nmap --script nmap-vulners,vulscan --script-args vulscandb=scipvuldb.csv -sV -p22 1##.##.###.#21
Starting Nmap 7.60 ( https://nmap.org )
Nmap scan report for 1##.##.###.#21
Host is up (0.54s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:4.3:
| CVE-2006-5051 9.3 https://vulners.com/cve/CVE-2006-5051
| CVE-2006-4924 7.8 https://vulners.com/cve/CVE-2006-4924
| CVE-2007-4752 7.5 https://vulners.com/cve/CVE-2007-4752
| CVE-2010-4478 7.5 https://vulners.com/cve/CVE-2010-4478
| CVE-2014-1692 7.5 https://vulners.com/cve/CVE-2014-1692
| CVE-2009-2904 6.9 https://vulners.com/cve/CVE-2009-2904
| CVE-2008-4109 5.0 https://vulners.com/cve/CVE-2008-4109
| CVE-2007-2243 5.0 https://vulners.com/cve/CVE-2007-2243
| CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906
| CVE-2006-5052 5.0 https://vulners.com/cve/CVE-2006-5052
| CVE-2010-5107 5.0 https://vulners.com/cve/CVE-2010-5107
| CVE-2010-4755 4.0 https://vulners.com/cve/CVE-2010-4755
| CVE-2012-0814 3.5 https://vulners.com/cve/CVE-2012-0814
| CVE-2011-5000 3.5 https://vulners.com/cve/CVE-2011-5000
| CVE-2011-4327 2.1 https://vulners.com/cve/CVE-2011-4327
|_ CVE-2008-3259 1.2 https://vulners.com/cve/CVE-2008-3259
| vulscan: scipvuldb.csv:
| [44077] OpenBSD OpenSSH up to 4.3 Signal denial of service
| [39331] OpenBSD 4.3p2 Audit Log linux_audit_record_event unknown vulnerability
| [32512] OpenBSD OpenSSH up to 4.3 unknown vulnerability
| [43307] OpenBSD 4.0 unknown vulnerability
| [41835] OpenBSD up to 4.8 unknown vulnerability
| [38743] OpenBSD up to 4.6 unknown vulnerability
| [36382] OpenBSD OpenSSH up to 4.6 information disclosure
| [32699] OpenBSD OpenSSH 4.1 denial of service
| [2667] OpenBSD OpenSSH 4.4 Separation Monitor Designfehler
| [2578] OpenBSD OpenSSH up to 4.4 Singal race condition
| [32532] OpenBSD OpenSSH 4.5 packet.c denial of service
| [1999] OpenBSD OpenSSH up to 4.2pl scp system() Designfehler
| [1724] OpenBSD OpenSSH 4.0 GSSAPIDelegateCredentials Designfehler
| [1723] OpenBSD OpenSSH 4.0 Dynamic Port Forwarding Designfehler
| [26219] OpenBSD OpenSSH up to 4.1 pl information disclosure
| [16020] OpenBSD OpenSSH 4.5 Format StringThe nmap-vulners NSE script reported over a dozen CVEs disclosed in the last few years. The nmap-vulners CVEs are organized by severity, with "9.3" being the most severe, placed at the top of the list and therefore worth investigating. The vulscan NSE script (after all the CVEs) also reported over a dozen interesting vulnerabilities related to OpenSSH v4.3.
Both of these NSE scripts do an excellent job of displaying useful information related to vulnerable services. Nmap-vulners queries the Vulners exploit database every time we use the NSE script. Vulscan, on the other hand, queries a local database on our computer which is preconfigured when we download vulscan for the first time.
Now, there's a lot going on in the above screenshot, so let's first learn how to install these NSE scripts before we get into using them. The video below is useful if you learn better that way, otherwise, skip to my full guide beneath it.
Step 1: Install Nmap-Vulners
To install the nmap-vulners script, we'll first use cd to change into the Nmap scripts directory.
cd /usr/share/nmap/scripts/Then, clone the nmap-vulners GitHub repository by typing the below command into a terminal. That's it for installing nmap-vulners. There's absolutely no configuration required after installing it.
git clone https://github.com/vulnersCom/nmap-vulners.git
Cloning into 'nmap-vulners'...
remote: Counting objects: 28, done.
remote: Compressing objects: 100% (23/23), done.
remote: Total 28 (delta 9), reused 19 (delta 4), pack-reused 0
Unpacking objects: 100% (28/28), done.Step 2: Install Vulscan
To install vulscan, we'll also need to clone the GitHub repository into the Nmap scripts directory. Type the below command to do so.
git clone https://github.com/scipag/vulscan.git
Cloning into 'vulscan'...
remote: Counting objects: 227, done.
remote: Compressing objects: 100% (23/23), done.
remote: Total 227 (delta 19), reused 22 (delta 9), pack-reused 194
Receiving objects: 100% (227/227), 15.87 MiB | 408.00 KiB/s, done.
Resolving deltas: 100% (137/137), done.As mentioned previously, vulscan utilizes preconfigured databases that are stored locally on our computer. We can view these databases in the root of the vulscan directory. Run the below ls command to list the available databases.
ls vulscan/*.csv
vulscan/cve.csv
vulscan/exploitdb.csv
vulscan/openvas.csv
vulscan/osvdb.csv
vulscan/scipvuldb.csv
vulscan/securityfocus.csv
vulscan/securitytracker.csv
vulscan/xforce.csvVulscan supports a numbered of excellent exploit databases:
- scipvuldb.csv
- cve.csv
- osvdb.csv
- securityfocus.csv
- securitytracker.csv
- xforce.csv
- expliotdb.csv
- openvas.csv
To ensure that the databases are fully up to date, we can use the updateFiles.sh script found in the vulscan/utilities/updater/ directory. Change into the updater directory by typing the below command into a terminal.
cd vulscan/utilities/updater/Then, make sure the file has the proper permissions to execute on your computer with the below chmod command.
chmod +x updateFiles.shWe can then execute and run the script by entering the below command into our terminal.
./updateFiles.sh
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/cve.csv...
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/exploitdb.csv...
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/openvas.csv...
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/osvdb.csv...
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/scipvuldb.csv...
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/securityfocus.csv...
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/securitytracker.csv...
Downloading https://raw.githubusercontent.com/scipag/vulscan/master/xforce.csv...
Returning 0, as no files have been updated, but script ran successfullyWith that done, we're now ready to start using the NSE scripts.
Step 3: Scan Using Nmap-Vulners
Using NSE scripts is simple. All we have to do is add the --script argument to our Nmap command and tell Nmap which NSE script to use. To use the nmap-vulners script, we would use the below command. Of course, change the # after -p to the port your scanning, and the following #s to the IP address you're using.
nmap --script nmap-vulners -sV -p# ###.###.###.###The -sV is absolutely necessary. With -sV, we're telling Nmap to probe the target address for version information. If Nmap doesn't produce version information, nmap-vulners won't have any data to query the Vulners database. Always use -sV when using these NSE scripts.
nmap --script nmap-vulners -sV -p80 1##.##.###.#24
Starting Nmap 7.60 ( https://nmap.org )
Nmap scan report for 1##.##.###.#24
Host is up (0.89s latency).
PORT STATE SERVICE VERSION
22/tcp open http nginx 1.0.15
|_http-server-header: nginx/1.0.15
| vulners:
| cpe:/a:igor_sysoev:nginx:1.0.15:
| CVE-2013-4547 7.5 https://vulners.com/cve/CVE-2013-4547
|_ CVE-2013-0337 7.5 https://vulners.com/cve/CVE-2013-0337Step 4: Scan Using Vulscan
We can use the vulscan NSE script in the same exact way as nmap-vulners:
nmap --script vulscan -sV -p# ###.###.###.###By default, vulscan will query all of the previously mentioned databases at once! As we can see in the below code box, it's an overwhelming amount of information to digest. It's really more information than we need.
nmap --script vulscan -sV -p22 1##.##.###.#77
Starting Nmap 7.60 ( https://nmap.org )
Nmap scan report for 1##.##.###.#77
Host is up (0.67s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| vulscan: scip VulDB - http://www.scip.ch/en/?vuldb:
| [44077] OpenBSD OpenSSH up to 4.3 Signal denial of service
| [39331] OpenBSD 4.3p2 Audit Log linux_audit_record_event unknown vulnerability
| [32512] OpenBSD OpenSSH up to 4.3 unknown vulnerability
| [43307] OpenBSD 4.0 unknown vulnerability
| [41835] OpenBSD up to 4.8 unknown vulnerability
| [38743] OpenBSD up to 4.6 unknown vulnerability
| [36382] OpenBSD OpenSSH up to 4.6 information disclosure
| [32699] OpenBSD OpenSSH 4.1 denial of service
| [2667] OpenBSD OpenSSH 4.4 Separation Monitor Designfehler
| [2578] OpenBSD OpenSSH up to 4.4 Singal race condition
| [32532] OpenBSD OpenSSH 4.5 packet.c denial of service
| [1999] OpenBSD OpenSSH up to 4.2pl scp system() Designfehler
| [1724] OpenBSD OpenSSH 4.0 GSSAPIDelegateCredentials Designfehler
| [1723] OpenBSD OpenSSH 4.0 Dynamic Port Forwarding Designfehler
| [26219] OpenBSD OpenSSH up to 4.1 pl information disclosure
| [16020] OpenBSD OpenSSH 4.5 Format String
|
| MITRE CVE - http://cve.mitre.org:
| [CVE-2009-2904] A certain Red Hat modification to the ChrootDirectory feature in OpenSSH 4.8, as used in sshd in OpenSSH 4.3 in Red Hat Enterprise Linux (RHEL) 5.4 and Fedora 11, allows local users to gain privileges via hard links to setuid programs that use configuration files within the chroot directory, related to requirements for directory ownership.
| [CVE-2008-4109] A certain Debian patch for OpenSSH before 4.3p2-9etch3 on etch
| [CVE-2008-1483] OpenSSH 4.3p2, and probably other versions, allows local users to hijack forwarded X connections by causing ssh to set DISPLAY to :10, even when another process is listening on the associated port, as demonstrated by opening TCP port 6010 (IPv4) and sniffing a cookie sent by Emacs.
| [CVE-2007-3102] Unspecified vulnerability in the linux_audit_record_event function in OpenSSH 4.3p2, as used on Fedora Core 6 and possibly other systems, allows remote attackers to write arbitrary characters to an audit log via a crafted username. NOTE: some of these details are obtained from third party information.
| [CVE-2010-4755] The (1) remote_glob function in sftp-glob.c and the (2) process_put function in sftp.c in OpenSSH 5.8 and earlier, as used in FreeBSD 7.3 and 8.1, NetBSD 5.0.2, OpenBSD 4.7, and other products, allow remote authenticated users to cause a denial of service (CPU and memory consumption) via crafted glob expressions that do not match any pathnames, as demonstrated by glob expressions in SSH_FXP_STAT requests to an sftp daemon, a different vulnerability than CVE-2010-2632.
| [CVE-2008-3844] Certain Red Hat Enterprise Linux (RHEL) 4 and 5 packages for OpenSSH, as signed in August 2008 using a legitimate Red Hat GPG key, contain an externally introduced modification (Trojan Horse) that allows the package authors to have an unknown impact. NOTE: since the malicious packages were not distributed from any official Red Hat sources, the scope of this issue is restricted to users who may have obtained these packages through unofficial distribution points. As of 20080827, no unofficial distributions of this software are known.I highly recommend querying just one database at a time. We can achieve this by adding the vulscandb argument to our Nmap command and specifying a database as shown in the below examples.
nmap --script vulscan --script-args vulscandb=database_name -sV -p# ###.###.###.###
nmap --script vulscan --script-args vulscandb=scipvuldb.csv -sV -p# ###.###.###.###
nmap --script vulscan --script-args vulscandb=exploitdb.csv -sV -p# ###.###.###.###
nmap --script vulscan --script-args vulscandb=securitytracker.csv -sV -p# ###.###.###.###Here's an example of one of those in use:
nmap --script vulscan --script-args vulscandb=exploitdb.csv -sV -p22 1##.##.###.#43
Starting Nmap 7.60 ( https://nmap.org )
Nmap scan report for 1##.##.###.#43
Host is up (0.52s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| vulscan: exploitdb.csv:
| [2444] OpenSSH <= 4.3 pl (Duplicated Block) Remote Denital of Service Exploit
| [21402] OpenSSH s.x/3.x Kerberos 4 TGT/AFS Token Buffer Overflow Vulnerability
| [3303] Portable OpenSSH <= 3.6.1p-PAM / 4.1-SUSE Timing Attack Exploit
|
|_As lead architect of VulDB, the vulscan developer usually finds time to update the scipvuldb.csv database file. Querying that database will probably produce the best results when using the vulscan NSE script.
Step 5: Combine into One Command
NSE scripts significantly improve Nmap's versatility, range, and resourcefulness as a security scanner. To get the most out of Nmap's version scans, we can use both nmap-vulners and vulscan in one command. To go this, type the below command into your terminal.
nmap --script nmap-vulners,vulscan --script-args vulscandb=scipvuldb.csv -sV -p# ###.###.###.###As an example, let's revisit what we first started with in this article:
nmap --script nmap-vulners,vulscan --script-args vulscandb=scipvuldb.csv -sV -p22 1##.##.###.#21
Starting Nmap 7.60 ( https://nmap.org )
Nmap scan report for 1##.##.###.#21
Host is up (0.54s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:4.3:
| CVE-2006-5051 9.3 https://vulners.com/cve/CVE-2006-5051
| CVE-2006-4924 7.8 https://vulners.com/cve/CVE-2006-4924
| CVE-2007-4752 7.5 https://vulners.com/cve/CVE-2007-4752
| CVE-2010-4478 7.5 https://vulners.com/cve/CVE-2010-4478
| CVE-2014-1692 7.5 https://vulners.com/cve/CVE-2014-1692
| CVE-2009-2904 6.9 https://vulners.com/cve/CVE-2009-2904
| CVE-2008-4109 5.0 https://vulners.com/cve/CVE-2008-4109
| CVE-2007-2243 5.0 https://vulners.com/cve/CVE-2007-2243
| CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906
| CVE-2006-5052 5.0 https://vulners.com/cve/CVE-2006-5052
| CVE-2010-5107 5.0 https://vulners.com/cve/CVE-2010-5107
| CVE-2010-4755 4.0 https://vulners.com/cve/CVE-2010-4755
| CVE-2012-0814 3.5 https://vulners.com/cve/CVE-2012-0814
| CVE-2011-5000 3.5 https://vulners.com/cve/CVE-2011-5000
| CVE-2011-4327 2.1 https://vulners.com/cve/CVE-2011-4327
|_ CVE-2008-3259 1.2 https://vulners.com/cve/CVE-2008-3259
| vulscan: scipvuldb.csv:
| [44077] OpenBSD OpenSSH up to 4.3 Signal denial of service
| [39331] OpenBSD 4.3p2 Audit Log linux_audit_record_event unknown vulnerability
| [32512] OpenBSD OpenSSH up to 4.3 unknown vulnerability
| [43307] OpenBSD 4.0 unknown vulnerability
| [41835] OpenBSD up to 4.8 unknown vulnerability
| [38743] OpenBSD up to 4.6 unknown vulnerability
| [36382] OpenBSD OpenSSH up to 4.6 information disclosure
| [32699] OpenBSD OpenSSH 4.1 denial of service
| [2667] OpenBSD OpenSSH 4.4 Separation Monitor Designfehler
| [2578] OpenBSD OpenSSH up to 4.4 Singal race condition
| [32532] OpenBSD OpenSSH 4.5 packet.c denial of service
| [1999] OpenBSD OpenSSH up to 4.2pl scp system() Designfehler
| [1724] OpenBSD OpenSSH 4.0 GSSAPIDelegateCredentials Designfehler
| [1723] OpenBSD OpenSSH 4.0 Dynamic Port Forwarding Designfehler
| [26219] OpenBSD OpenSSH up to 4.1 pl information disclosure
| [16020] OpenBSD OpenSSH 4.5 Format StringThat's about it for version scanning with Nmap NSE scripts. Until next time, follow me on Twitter @tokyoneon_ and GitHub. And as always, leave a comment below or message me on Twitter if you have any questions.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























10 Comments
Great
you mind find this usefull;
offensive-security.com/metasploit-unleashed/
nmap-vulners doesn't seem to be working for me, vulscan works perfectly.
Wow! It's really cool! Thank you.
i have a windows and kali machine setup
my windows machine has the ms08-067 vulnerability but both scan dont show it
(cve2008-4250) the output i get is basicly the same as nmap -sV <ip>
i've managed to get the vulscan working doing the following;
nmap -sV --script=vulscan/vulscan.nse -script-args=eploitdb.csv -445 <ip>
but the vulners still wont do anything
nmap -sV --script=nmap-vulners/vulners.nse -p445 <ip>
i know moving the nse files to scripts will make me able to just ---script <nse file> however this is not mentioned in the guide.
at first i thought the problem was that it didnt got the rule statement of the script right so i put a + infront of it (--script +<nse file>) this didnt work aswell any sugestions?
in the vulners readme the dependency is json,http,string (.lua) and i cant seem to find the string one not even on the nmap github maybe that is the cause of vulners not working?
i just found out; nmap --script exploit -Pn <ip> gives a bit less but all you need
bro it is won't work.
QUITTING!
:|
Share Your Thoughts