Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.
When we have a file that we need to audit against a checksum provided by the file's author, we can use open-source cryptographic software to calculate a checksum. Reviewing the checksum is used for situations where maybe you are at a sketchy website or you don't know if your favorite site is being spoofed.
How a Hash Works
Data from a file to be checked is divided into 512-bit blocks. Each block is passed through the SHA-256 algorithm and added to a sum until there is no more data to be added to that number. The final sum of this calculation is our checksum, also known as a hash. You can learn more about how hashing works in the video below.
In essence, when we calculate a hash, it is a one-way cryptographic function, meaning a change to a single bit will generate a new, seemingly random number that is very hard to arrive at again. If you can cause two different files to generate the same checksum, this creates an extremely rare condition called a collision. This kind of attack is a weakness in SHA-1 and other cryptographic functions but takes significant time and resources to attempt to exploit.
In this article, I will demonstrate how to compare the SHA-256 hash of a file downloaded with the one provided by the file's author first on a Windows system, and then on Kali Linux.
Method 1: Using 7-Zip on Windows
The first thing we are going to do is download a program for Windows called 7-Zip. This tool isn't only for comparing the checksum, but also for compressing and decompressing files and folders. You can download that from the official 7-Zip download page. Make sure to download and install the most recent and stable version. It is a very simple to install; just follow the on-screen prompts.
Next, let's compare a downloaded hash by going to a website that displays the checksum for a download. For this test, we will be using the download page of VLC media player for Windows. On their site, they helpfully display their checksum in an SHA-256 hash format by clicking the "Display Checksum" button. Stay on this webpage, as we'll need to compare the hash against that number shortly.
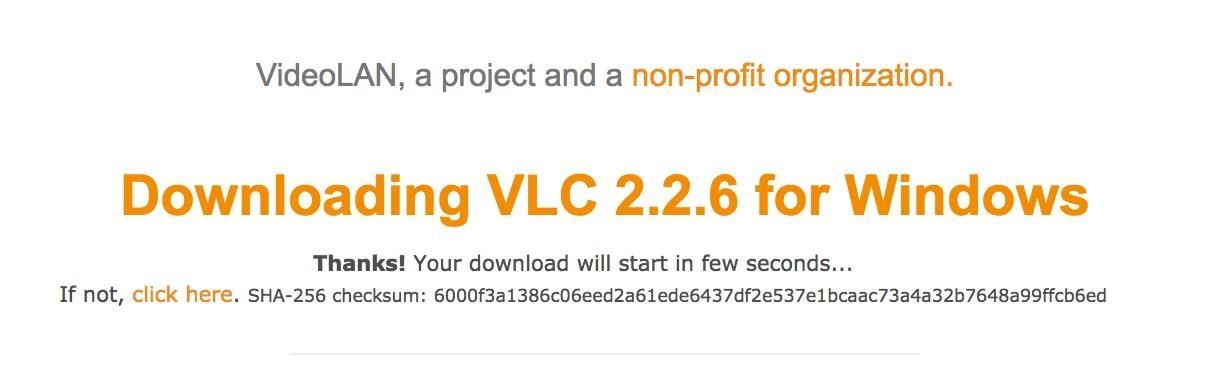
Go to the folder where you downloaded the VLC installation file. After locating it, just right-click on the file and scroll down to the part where it says "CRC SHA." We will need to choose the correct SHA algorithm, which VLC has provided on their website. In this case, we will select the SHA-256 option by clicking on it in the submenu. Notice you don't have to open 7-Zip up directly to do this.
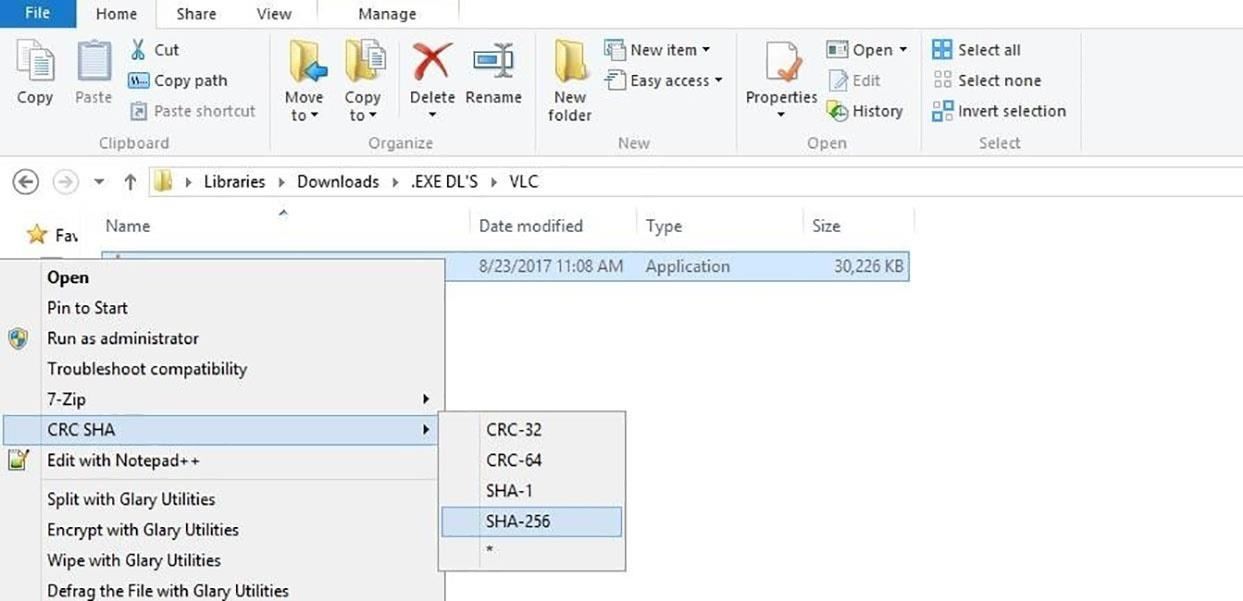
Finally, 7-Zip will show the outcome of the checksum. Now, we'll need to compare this value with the one we were provided by the website. Check back with the VLC website and locate the checksum to compare the values.
If the contents of the file had been tampered with, the whole checksum would change, so I personally usually look at the last 4 characters. If the number has changed, then we know the download was tampered with or corrupted.
Method 2. Using UNXZ on Kali Linux
Now let's open our favorite Linux distro, Kali Linux, and open up the browser.
To run our test, go to the Kali ISO downloads page to locate our example file to download. For a shorter download, we will be selecting the smallest ISO, the "Kali armel" image, to download. You can choose to download it over HTTP or torrent.
Once the image has been downloaded, open up a terminal window and use cd to navigate to the folder where you downloaded the file to. There are many ways to unzip a file on Linux, but what worked for me was a command included by default in Kali called unxz. Run it followed by the path to the file to unzip the ISO image you downloaded.
Once that is extracted, we want to type the following into a terminal window. Make sure "2017.1" is replaced with the current version you downloaded.
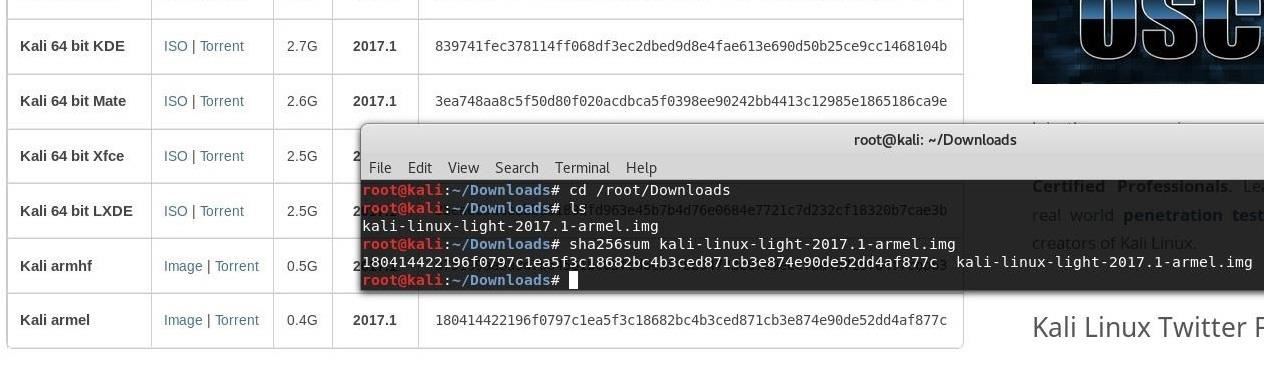
sha256sum kali-linux-light-2017.1-armel.img
Hit return and the checksum for the file will be displayed in the terminal window. Now, you can compare against the checksum provided by the website. They should match, as shown in the image below.
Threats Against Hashing
There are still attacks about using the checksum method, most recently SHA-1 was demonstrated to be vulnerable to a collision attack, so most users have switched to a new standard protocol with a longer, more secure cryptographic algorithm called SHA-256. There could be people, at this moment, working on a generating a collision attack on SHA-256.
These techniques can be subverted by tactics like a man-in-the-middle attack. An attacker could simply comprise the web host for that file, replace the real hash with the checksum of their own malicious file, or create a new hash with the attacker's manipulated file's checksum value and swap the file for the original on the site. This is exactly what happened to users who downloaded a compromised version of Linux Mint 17.3 Cinnamon edition hosted on a compromised Bulgarian FTP server, so be careful out there!
SHA-256 — Your Second Set of Eyes
So that's it, you can now confirm that the download is in its true form, and was not manipulated in any way. This is just one of many methods for staying safe on the internet while downloading files. In reality, this is a way of being more aware of your surroundings, similar to protecting your PIN number at an ATM. Aside from defending against malicious hackers embedding malware into downloads, it also can be used to detect corrupted files.
Thanks for reading. Stay connected and check out our social accounts!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
Screenshots by Nitrous/Null Byte























1 Comment
You don´t need to install 7-zip .
You can open cmd with
and then navigate to your file with "cd"
and type: certutil -hashfile YOURFILENAME.mp4 hash algorithm
For Example:
Share Your Thoughts