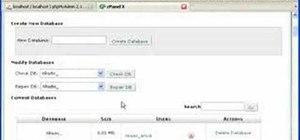
OnTime is such a flexible tool and it can be used in a variety of ways, with completely different methodologies. One of the methodologies that works well with OnTime is Scrum. This week we walk through a quick demonstration of setting up a new OnTime database for use with a Scrum methodology.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.










Be the First to Comment
Share Your Thoughts