In this video, you will learn how to draw the Lewis Dot structure for CH3CH2OH, or drinking alcohol. To draw the first type of alcohol, draw H, C, C, O, and H horizontally. Now draw, an H above and below both C. Draw the dot structures in between each letter. Hydrogen has one valance electrons, Carbon has four, and Oxygen has six. Now, connect the Lewis Dot Structures. If you are given C2H6O, write down C, O, and C horizontally. Draw a line between the O and the C's. The Carbons will have three unpaired valance electrons each. Thus, place the H's around the C's so that they will become paired. Draw a line between the Hydrogen and Carbons. Viewing this video will show you just how easy it is to create Lewis Dot Structures.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.



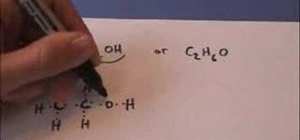

















Be the First to Comment
Share Your Thoughts