Hello folks,
I'm a new member of the Null Byte community that subscribes just recently.
I read and learnt a lot from the various tutorial and decided to share my little experience.
In this post I'll teach how to write Daemonic Reverse Backdoor using Python3.
Note: I'm not a native English speaker, so I want first to apologize for any mistakes I would make in this article.
Credits and Disclamer
Relatively new on Python network programming I based my work on several other articles that I need to mention in first place.
If you're up for the challenge you can just skip my tutorial and try to do it only based on these links.
Sources:
Build a simple network packet sniffer with python:
http://www.binarytides.com/python-packet-sniffer-code-linux/
Build a shell with python:
https://null-byte.wonderhowto.com/how-to/build-evasive-shell-python-part-1-introduction-concepts-0168634/
Create a daemon with python:
http://www.datamation.com/netsys/article.php/3786866/Creating-a-Daemon-with-Python.htm
Important: real Hacking is illegal.
Breaking into a information system or installing any tool that may provide you any kind of access on the system without the concent of its owner is severally punished by the law... You're warned.
Requirements
You'll need 2 machines:
- Kali Linux with python3 and scapy installed as our attacker, obviously
- A relatively Linux distribution (I used ubuntu 16.04) with Python3 installed as our victim
You can use VMs if you don't have the physical devices.
Note: The script you'll obtain at the end the tutorial would work only on Unix based system.
Theorical Concepts
In this tutorial I will use 3 important concepts: daemon, backdoor and reverse shell.
Daemons
A daemon is basically a long lasting process that run in background. So it's a process that run without any interaction from the user. For an unaware user it's completly invisible and may not even suspect its existence. Daemons are really commons and you can easily find them if you know where to look : a lot of services on your computer are daemons.
Backdoors:
A backdoor is a hidden feature in a software that grant a certain level of access to the software to whoever aware of this feature . For example: hardcoded credentials in a soft for debugging can be considered as backdoors.
In the computer hacking field it refers to a more or less hidden malicious "hole" in your system that grant unauthorized access. You can find many malicious backdoors on Metasploitable OS if you want some examples.
Reverse Shell:
While attacking, hackers often try to get a remote access on your system.
An common technique they use in order to gain control is the shell-binding : first the attacker comprises your system by exploiting a vulnerable service and send his payload. This payload is in fact a remote shell that open a port on the victim system, wait the attacker to connect and execute the attacker commands.
However what happens if the victim is protected by a firewall that dismiss any remote incoming connection?

The attacker can't connect to its shell. Oh my, the victim is safe... well not really because it's possible to "deceive" the firewall : usually the firewall block the incoming connections but not the outgoing ones because you know... people needs to go on Internet.
So instead of trying to connect to the shell he placed on the victim, the attacker will just build its shell so that it will initialize the connection. All he has to do is to patiently wait his victim to connect back to him.
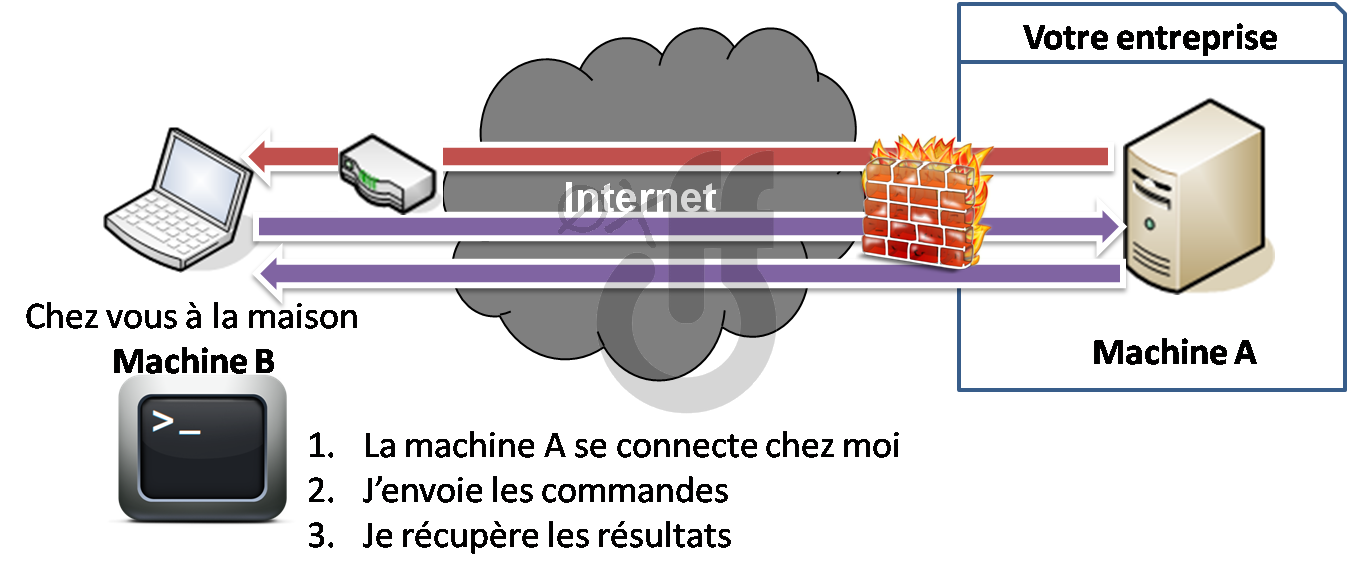
This technique is called reverse-shell.
Now we see what the interest of all these concepts if we mix them together: We'll obtain a invisible backdoor shell that will bypass most firewalls.
To Be Continued
In the next part : I'll show you how to write the backdoor, so victim side program.
See you soon.
WhichHat?




Comments
No Comments Exist
Be the first, drop a comment!