Welcome back, my greenhorn hackers!
Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.
Although we would love to get Metasploit's Meterpreter on the target and use all its capabilities on the owned system, that is not always possible. Some exploits will only allow us to get a CMD shell on the target Windows system.
In these cases, you will need to understand how to control the system strictly through the command prompt, without ever having the convenience and familiarity of the Windows GUI.
What I want to do in this tutorial is demonstrate some Windows commands on a Windows 7 system (Windows 7 is still over 50% of the installed base of Windows systems), but these commands change very little from Windows version to Windows version. I will be running the Windows commands from a remote Kali system on the target.
Connect to a Remote Windows System from Kali
Windows makes a distinction between commands that can be run while physically on the system and those that can be run remotely. We can't assume that a command we can run while on the system will run remotely.
Here, we are only interested in those that can be run remotely. In my case, I will be connecting to the target system with a Netcat connection, but a Metasploit-spawned command shell or other will work just as well.
Basic Commands
In many ways, Windows CMD commands are similar to Linux/Unix commands (Unix preceded these commands by over a decade, and Microsoft borrowed heavily from it). At its most basic, we need to change directories within the file system. Like Linux, Windows uses the cd (change directory) command. To travel to the root of the directory system, we can just type:
cd \
In addition, we can move up one level in the directory structure by typing:
cd ..
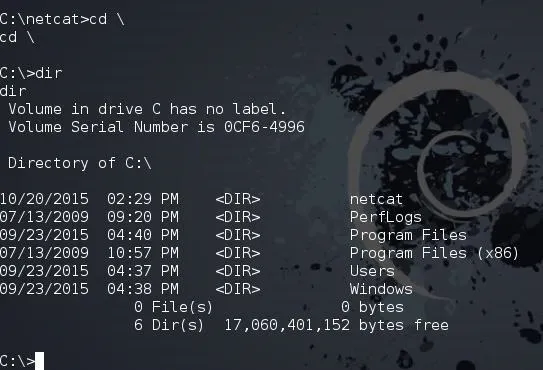
If we want to see the contents of a directory, we type dir as seen above. Some other key and basic commands include:
del
This will delete the file, similar to the Linux rm.
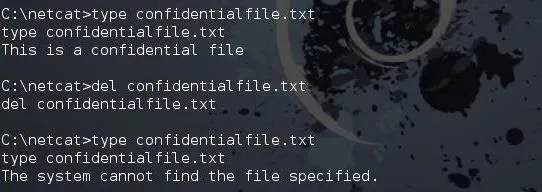
type
This will display the contents of the file, similar to the Linux cat.
As you can see below, I used type to display the contents of the confidentialfile.txt. I then del (delete) the confidentialfile.txt, and when I return to display the contents of it again, I get the message that "The system cannot find the specified file."
To create a new directory, we use the md (make directory) command (in Linux, it's mkdir). To create a directory named "newdirectory," we type:
md newdirectory
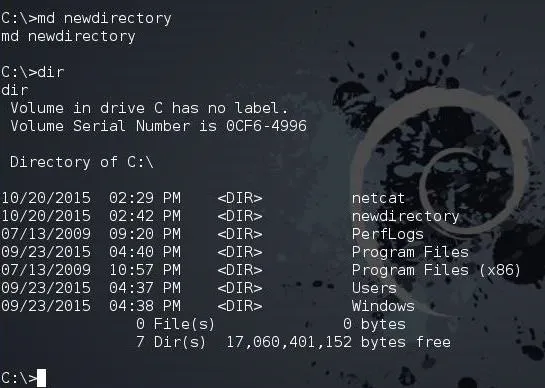
After making newdirectory, we can now run dir and see the new directory that we created.
Network Commands
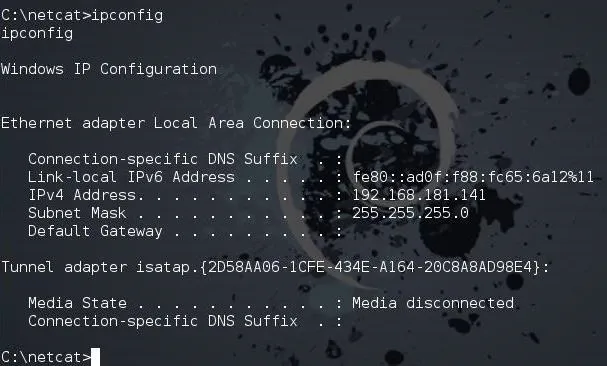
When we are on the remote system, we may need networking information. To do so, we have two basic commands, ipconfig and netstat. Ipconfig is very similar to the Linux ifconfig, as seen below.
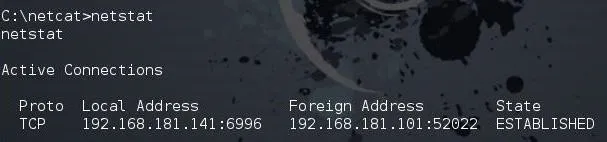
To view the network connections of the system, we can type netstat, just like in Linux.
netstat
View Processes
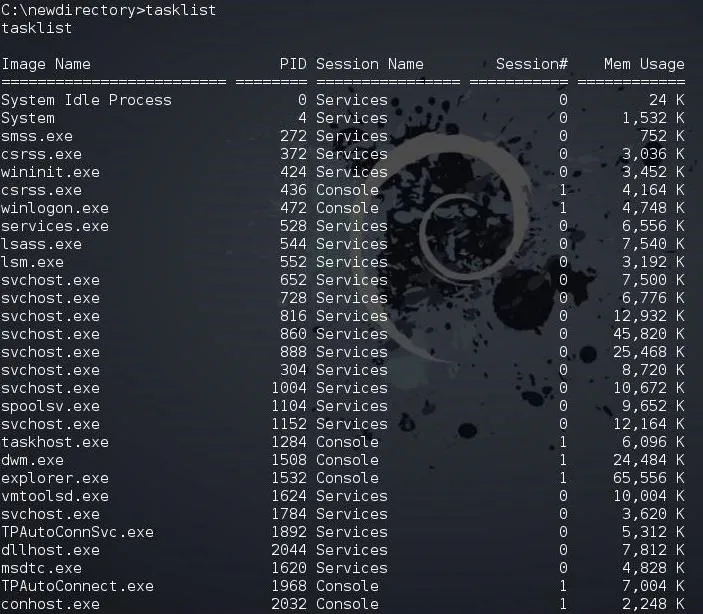
Often, when we are on a remote system, we will need to see a listing of the running processes. From the GUI, of course, we can use the Task Manager (Ctrl + Alt + Del), but from the command prompt, we use tasklist.
tasklist
If we want to find a single process, we could use the filter findstr (find string). This works similarly to grep in Linux. So, to find the process named "explorer," we could type:
tasklist | findstr explorer
Note, that we used the pipe (|), just like in Linux, to send the results from the tasklist command to the filtering command, findstr.
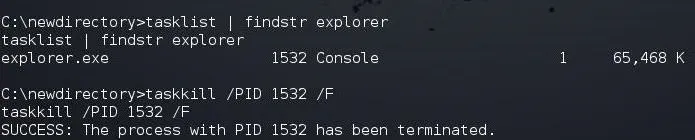
If I want to kill a process, I can use the taskkill command. It requires the PID of the process we want to kill. In this case, the explorer process has a PID of 1532, so to kill it, I can type:
taskkill /PID 1532 /F
Where the /F means to force the kill.
Find the User Accounts
If we want to see the users on the target system, we can type:
net users
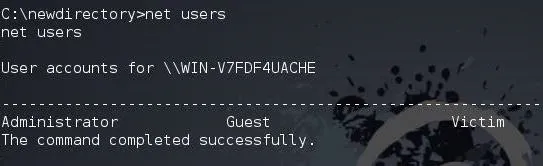
As you can see, this system has three users: guest, administrator, and the aptly named victim.
Run a Browser on the Target
While operating the system from the command prompt, we can execute some applications, such as the web browser. Internet Explorer is named iexplore on the command prompt, and we can find it either in the "Program Files" with the 64-bit version or "Program Files (x86)" with the 32-bit version. So, if I want to open Internet Explorer on the remote system from the command prompt and have it open wonderhowto.com, I would type:
iexplore www.wonderhowto.com
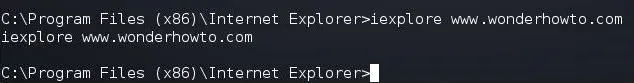
When we do, this opens Internet Explorer on the target system and goes to wonderhowto.com, as you can see below.
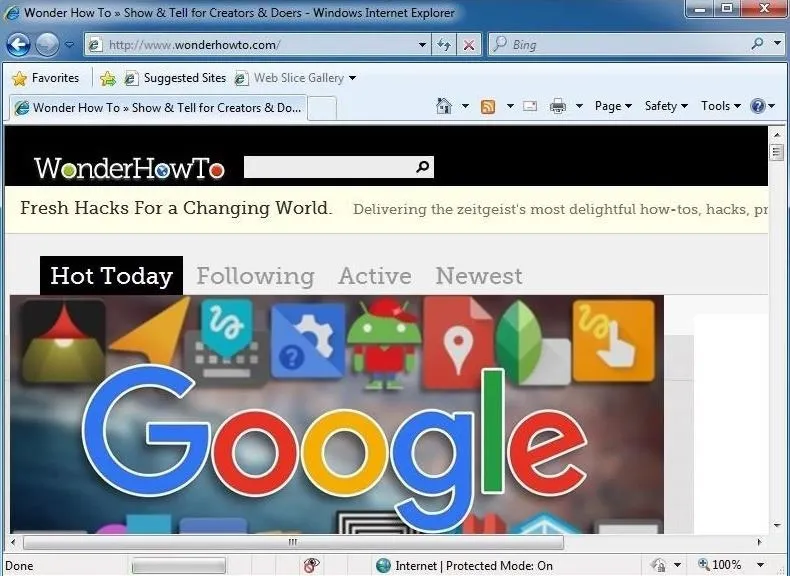
This might be really useful if you had a malicious XSS link set up and needed the target to go to a web server. Furthermore, we might just want the target system to go to our web server on Kali. We could start the Apache web server and then direct the target system to our web server where we may have some malicious software.
We can type:
iexplore
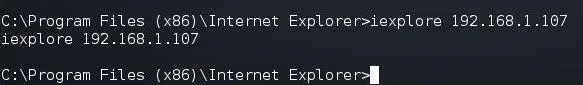
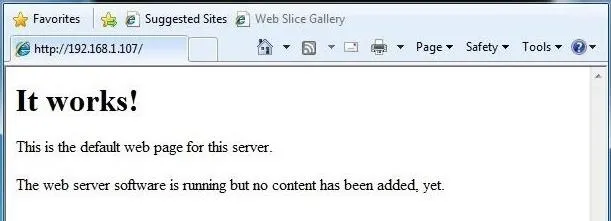
As you can see below, we have directed the target system to our web server on Kali.
Keep coming back, my greenhorn hackers, as we develop the most valuable skill set in the 21st century—hacking!
Cover image via Shutterstock




Comments
No Comments Exist
Be the first, drop a comment!