Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.
With reports of Russian disinformation campaigns in the news, many are curious how these attacks are even possible. As with most effective attacks, it all starts with good recon. Scanning a global conversation on social media isn't the same as scanning a network, but thanks to machines in Maltego designed for monitoring Twitter, we can use some of the same tools we use to examine networks to visualize social media conversations.
- Don't Miss: How to Use Maltego to Do Network Reconnaissance
Disinformation Campaigns
Disinformation campaigns were made famous by the tactics discovered to be in use during the 2016 election tampering operations used by Russian-linked hackers. These attacks used the anonymous nature of Twitter and other social platforms to attempt to deepen political and social rifts in US society by spreading false and misleading information designed to be polarizing.
To enable these campaigns, online conversations were carefully studied to craft information that would have the maximum impact. Once sensitive topics were gathered, the fake news was aggressively injected into the public discussion by strategically placed bots targeting real users determined likely to share the content as legitimate. Often, these talks would appear to be from a valid or known source, or at the very least, a member of an existing fringe group.
The careful study of online conversations used by activists or other politically involved users was a vital part of these campaigns. Several tactics contributed to the success of these efforts, such as feeding fake content to real users for distribution by monitoring who shared news stories, and what they tended to share.
Amplifying a Polarized Discussion
Social media companies have been developing the ability to automatically sort tweets and social media messages by sentiment, using machine learning to identify patterns associated with positive or negative tweets. By using sentiment analysis, an attacker can amplify a polarizing discussion by triggering an army of bots to retweet and share legitimate tweets about specific topics or people depending on if they are saying negative or positive things.
The advantage of this attack is that you can emulate a reactive jammer, which waits for a specific type of communication to happen before performing the jamming action. In this case, an attacker can use sentiment analysis to sort polarizing tweets to amplify, and quickly overwhelm, a discussion by amplifying fringe opinions. This prevents a fair and open debate, allowing the attacker to overcome dissenting views with tweets written by real users.
Jamming Tactics
Generally, the techniques used to jam other communications apply equally to interactions on social media. In particular, we'll discuss how continuous jamming, deceptive jamming, and scan-jamming can be used to dominate an online conversation.
Continuous jamming effectively aims to overload the communications targeted with random noise in order to make it unsuitable for use. It does not attempt to blend in with the conversation, instead, looking more like spam. Bots are used to flood a particular hashtag being used to communicate with unrelated tweets, diluting the discussion so that finding legitimate tweets becomes impossible. This tactic has the added benefit of Twitter automatically censoring the tweet because it's detected as being used to spread spam.
Deceptive jamming aims to disguise the attack by making the jamming appear to be part of the conversation. In this attack, a targeted hashtag is flooding with legitimate looking tweets spreading confusing of misleading information. Through rendering the information on the channel useless by introducing doubt, anyone using the hashtag to communicate or understand what's happening will quickly find themselves buried under tweets offering important-sounding false information. This attack can also be used in a targeted way by spreading negative information about critical individuals more quickly.
Using Maltego to Monitor Unfolding Events in Real Time
To launch any of these attacks, it's essential to be able to "scan" an ongoing Twitter conversation the same way you would run Nmap on a network. Without knowing an attack surface, you cannot design a practical plan to attack it, so the challenge becomes mapping a very organic conversation like on Twitter using hacking tools usually more suited to scanning routers and hosts.
As it turns out, Maltego is a perfect platform for watching social media conversations unfold. With the added advantage of importing targets directly into Maltego for followup research or targeting, a hacker using Maltego to track social media can find all the key hashtags and users involved in the spread of information around an event, topic, or person.
While most hackers think of Maltego as useful for finding static information like network fingerprinting, several Maltego machines are specifically designed to do things like track users and topics of interest on social media.
These tactics are used by authorities to track the social media accounts of known activists in real time, allowing police to stay on top of what's happening at protests in real time without a warrant. The same tactics can be used to decide on how best to use an army of Twitter bots to disrupt a society from half a world away.
Sign into Maltego
To install Maltego, you'll need to have Java installed on your machine. Maltego comes installed by default in Kali Linux, so if you're running Kali, you should be able to get started by just selecting it from the main menu.
If you're using macOS or Windows, you can download Maltego Community Edition from the Paterva website.
Once you open up Maltego in Kali or install it on another system, you will need to create a free account with Paterva to use the community version. Register the account, receive the confirmation email, and then enter the code to confirm your account so you can log in.
When this is done, log into the Maltego Community Edition, and you'll be ready to start a new graph.
Begin Watching the Conversation
In our example, we'll be searching for conversations around sensitive current events that could be used in a disinformation campaign. To start, we'll be using a machine that monitors Twitter for activity around certain phrases. These phrases, like "space force" or "collusion," are likely to bring up a heated debate on a sensitive topic. By zeroing in on the global conversation around these issues, we can start to determine who the major players are and what the discussion looks like.
To start, click on the "Machines" tab in Maltego, and you'll be taken to a menu where you can select the "Run Machine" icon.
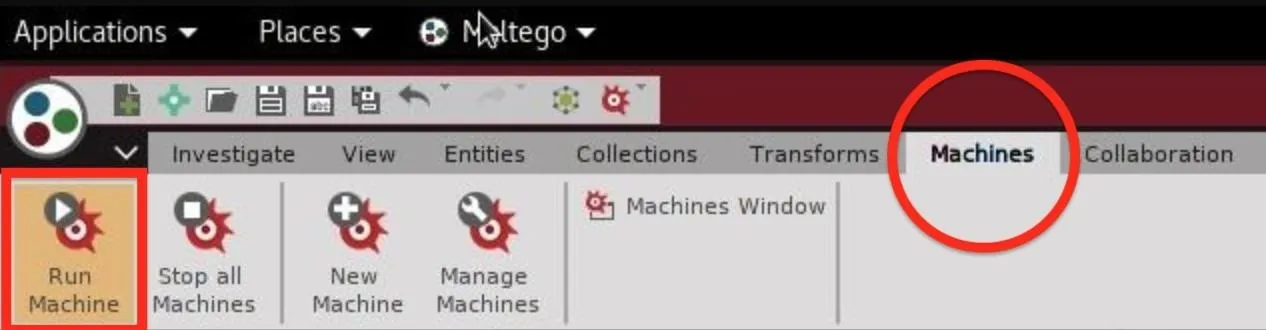
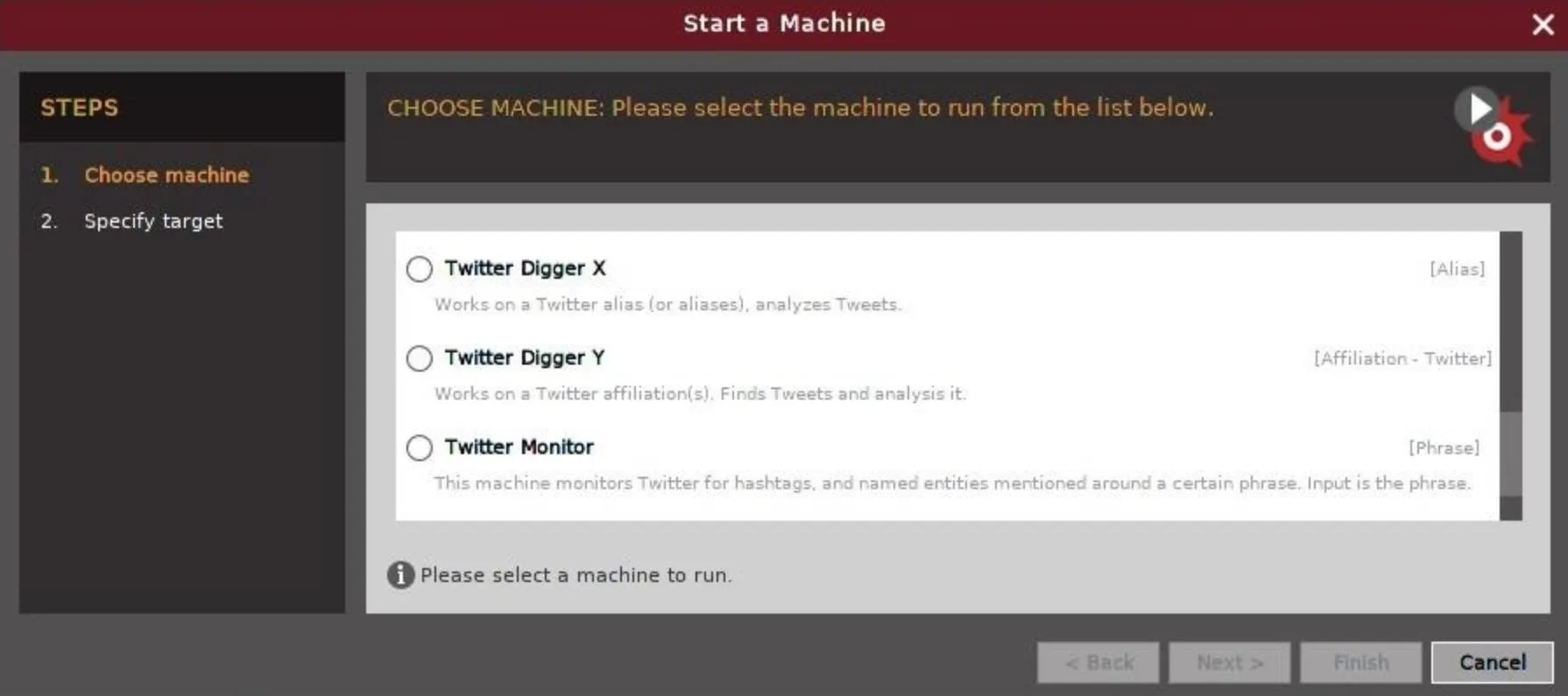
Within the machine's menu, there are three relevant ones to explore. Of those three, you'll see a "Twitter Digger X," a "Twitter Digger Y," and a "Twitter Monitor."
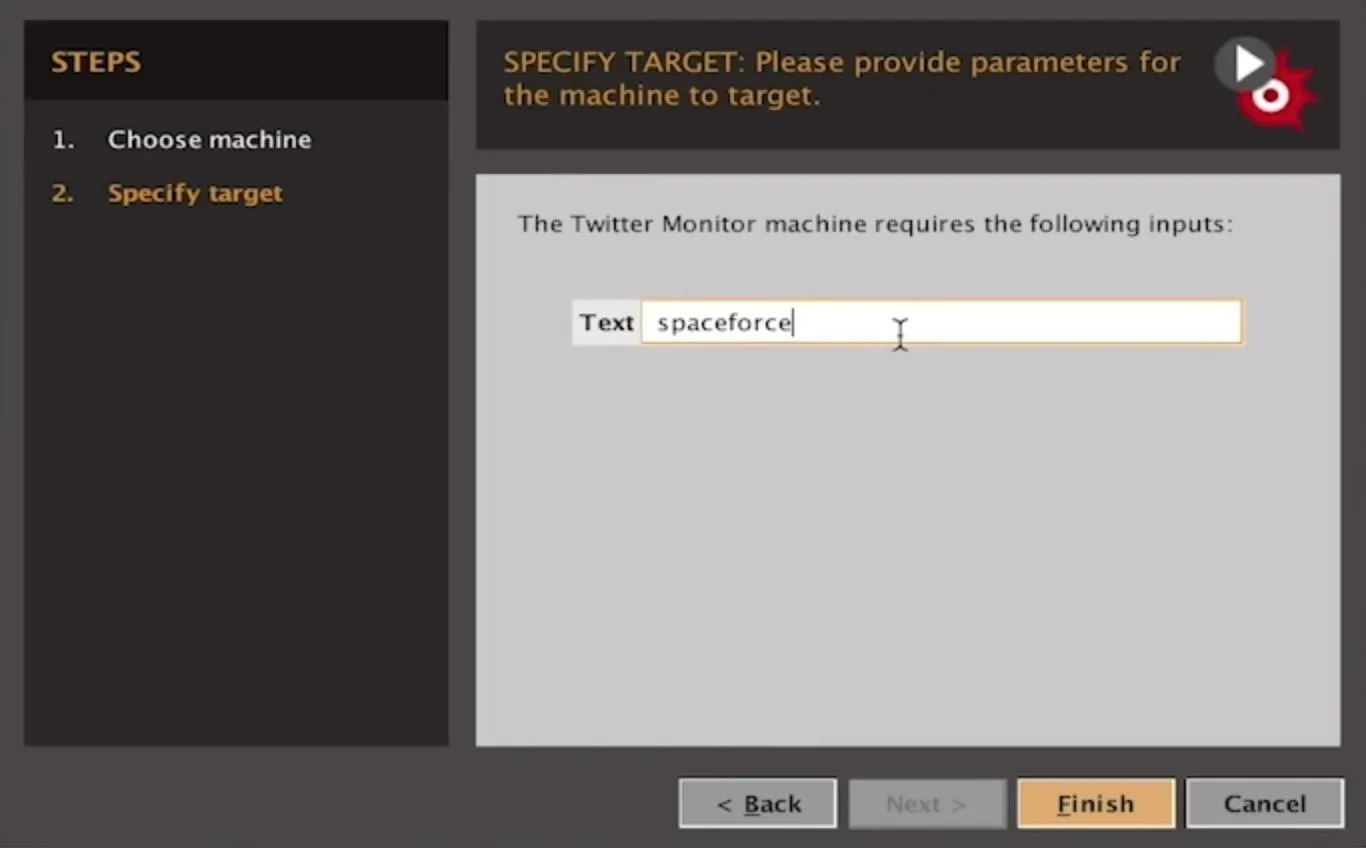
We'll be using a phrase to find tweets, so we'll select "Twitter Monitor." The input here will be a phrase that we expect the conversation to be around. It's important we pick something that will bring up a controversial debate, so for our examples, we picked "Papa John," "Space Force," and "Collusion" in separate searches.
Find Key Players & Trending Information
Once we start our machine, we'll have to let the information fill the graph. This may take a few minutes of Maltego running new iterations to pull in more data, especially if you're using the free version of Maltego. The information you see in the graph may be overwhelming, so it's good to "Set layout mode to Organic" from the Layout section in the toolbar on the left of the graph.
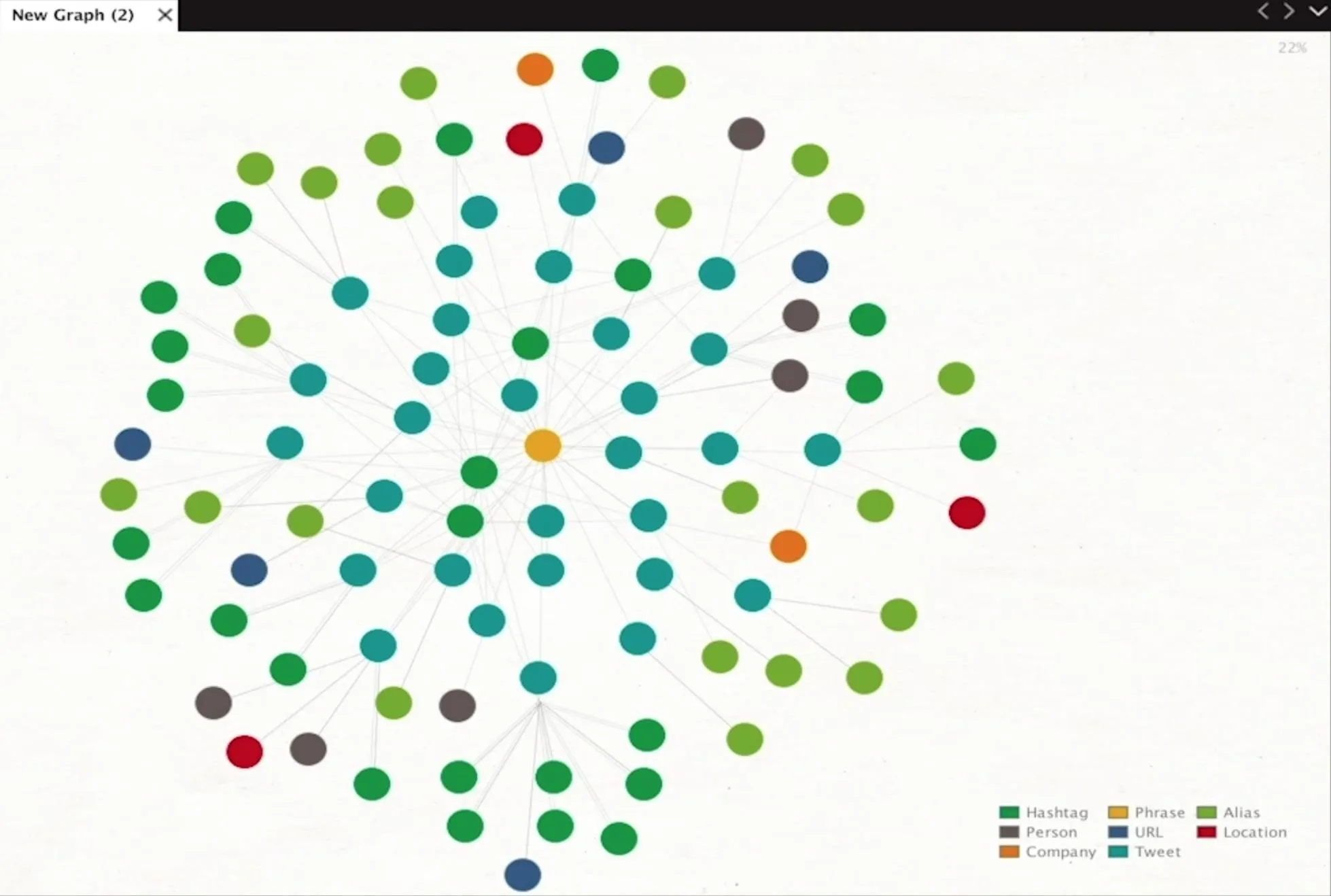
Also, by setting the view to "Ball Size by Diverse Decent" from the "Manage View" options found in the "View" tab, we can look for larger ball icons which show bigger discussions; This will make the relationships more clear by emphasizing things many people are talking about with larger icons.
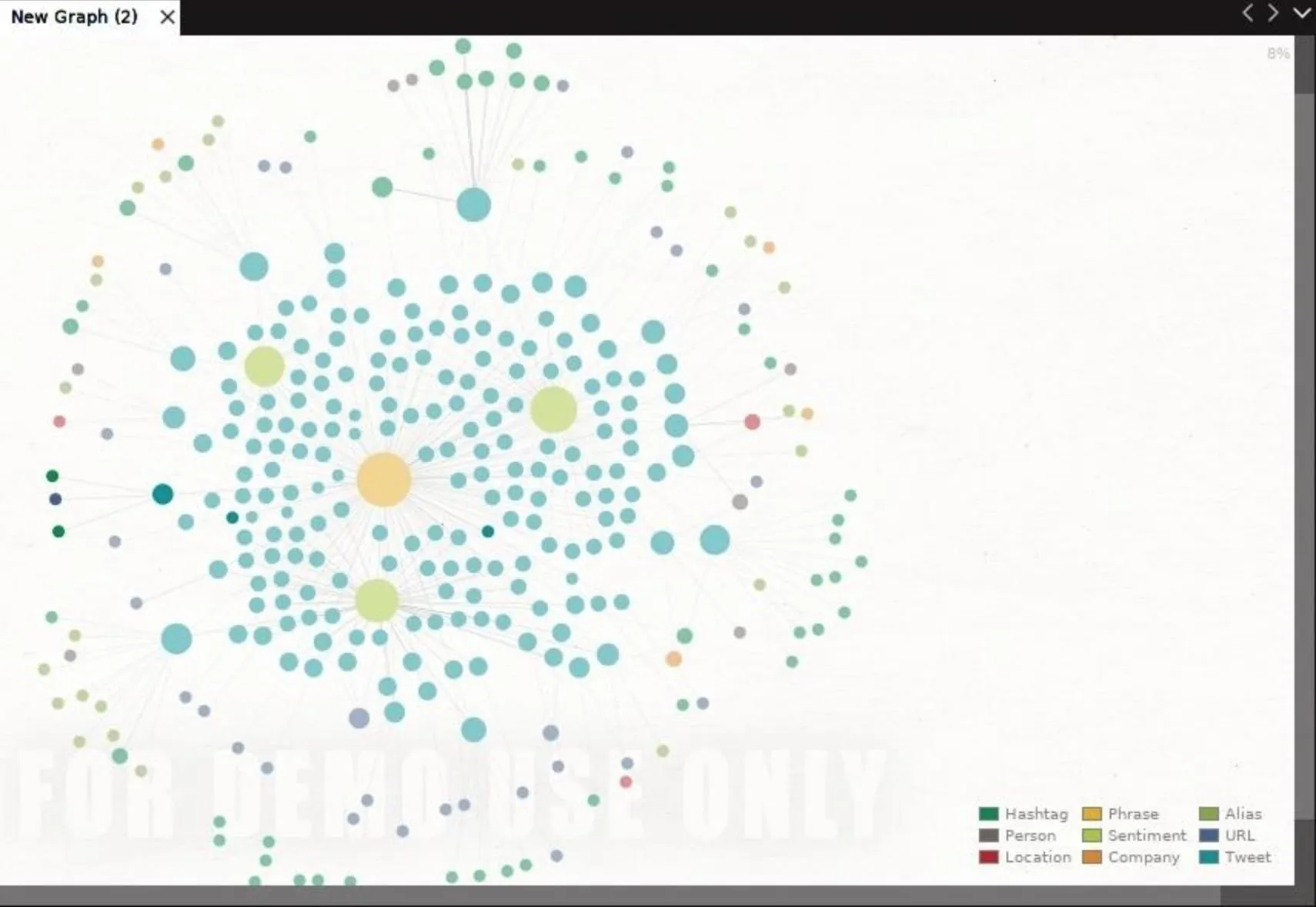
This machine will pull in updates automatically, and you can see the timer to do so on the top right of the Machines pane. As the information fills the graph, you can start to organize it by selecting all entities with Ctrl-A.
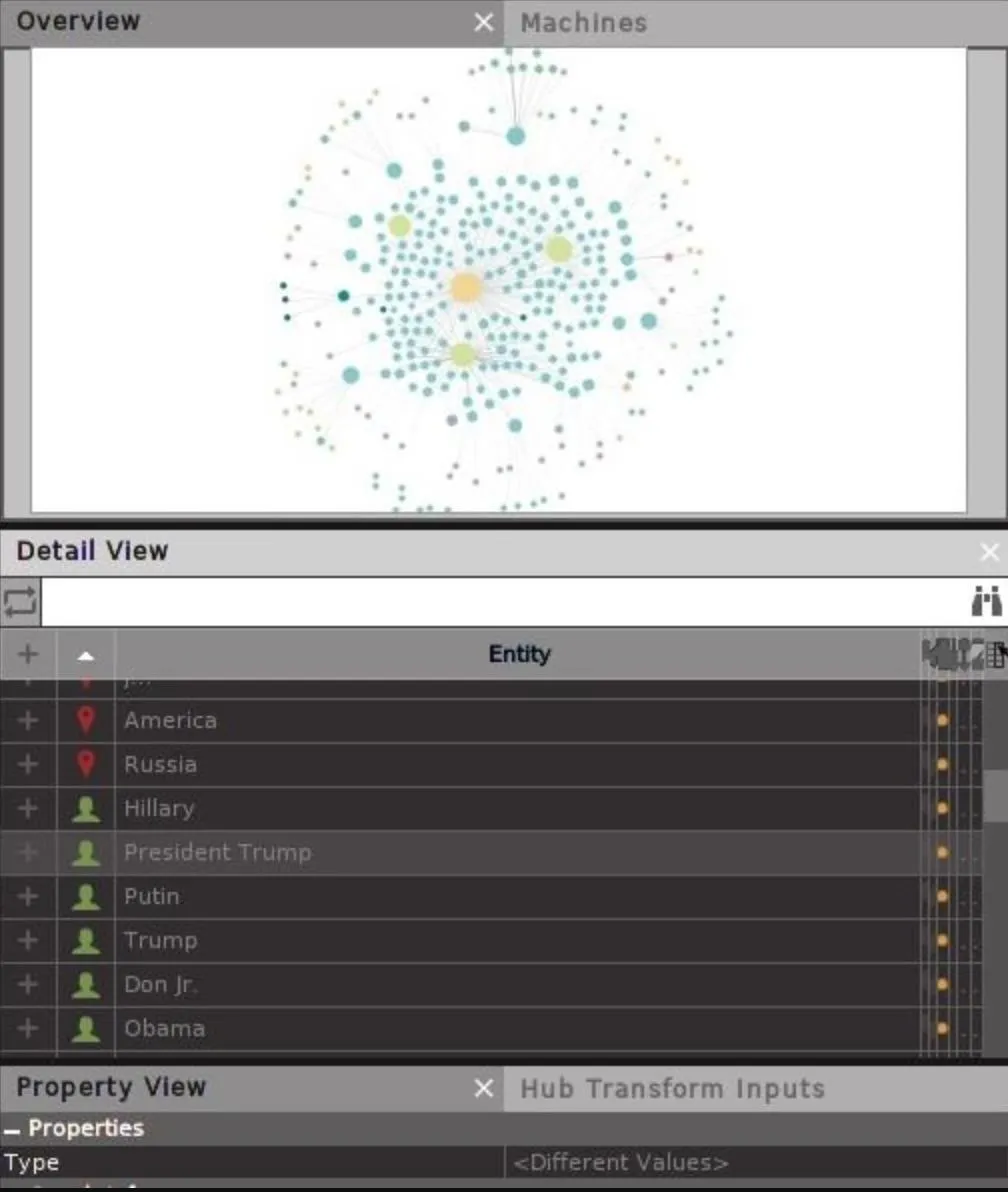
In the Detail View pane on the bottom right, you can click the box next to the plus symbol to organize entities by type. Within these groupings, you can see Maltego has resolved certain entities as people who are being frequently mentioned or discussed.
This will begin to show you the people behind the conversations on this topic. Here, we can see the key people mentioned in conversations about "collusion" after the machine runs a few times.
We can also use this method to identify links that are being shared about a topic.
In a disinformation campaign, we could search articles being shared for the most slanted and divisive content, and tag the users sharing those kinds of links. After creating fake and inflammatory information, we can pass the phony news to those real users who are most likely to share it.
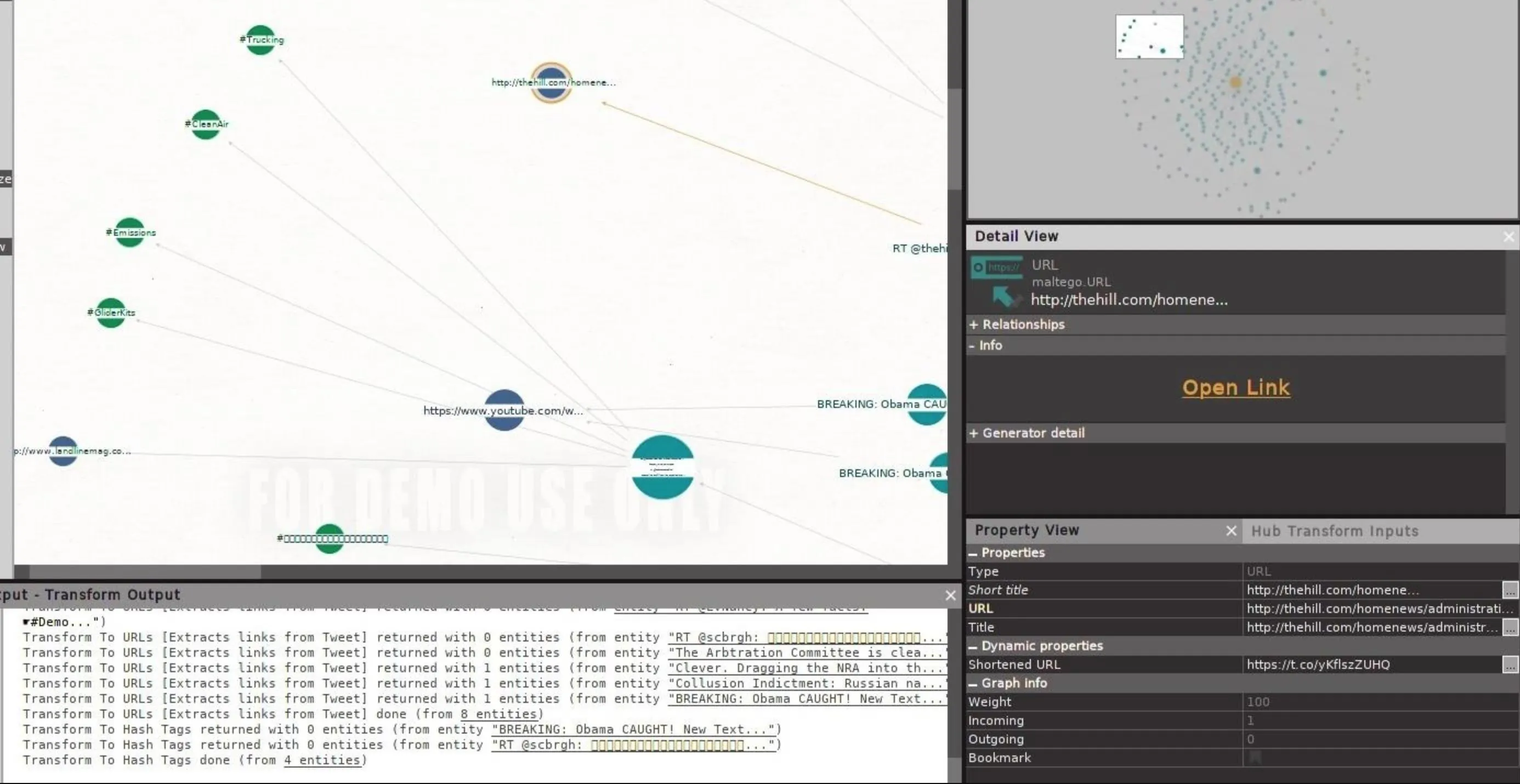
Click on image to enlarge.
Identify Social Media Channels for Jamming
In the event an attacker wants to jam a conversation on a topic, this Maltego machine provides a convenient list of hashtags being used to communicate around a particular topic. With this information, an army of bots could flood the channel with noise, rendering the conversation impossible.
You should be able to view hashtags from discovered tweets automatically, but if you're only seeing tweets in your graph, you can select all by clicking on the graph, choose Ctrl-A, right-click to bring up the transform menu, then type "hashtag" into the search bar that appears. This should show the "To Hash Tags" transform, which you can click to extract hashtags from tweets.
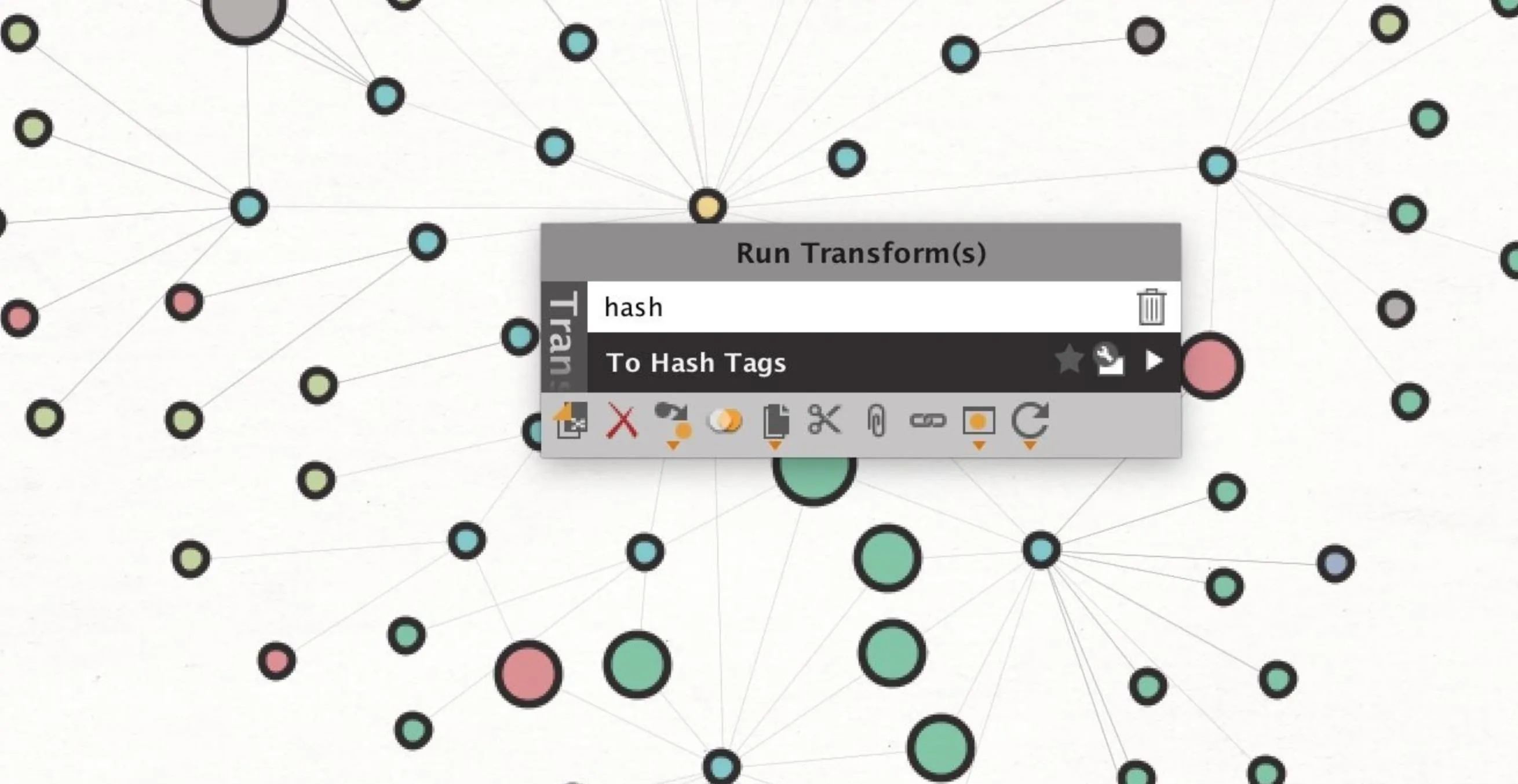
Now you can select the hashtags involved and sort them by how many times they appear with the other options in the Detail View pane. In a social media jamming attack, any hashtag over a certain popularity could be automatically fed to Twitter bots to disrupt, acting like a "scan jammer" constantly looking for the activity to jam.
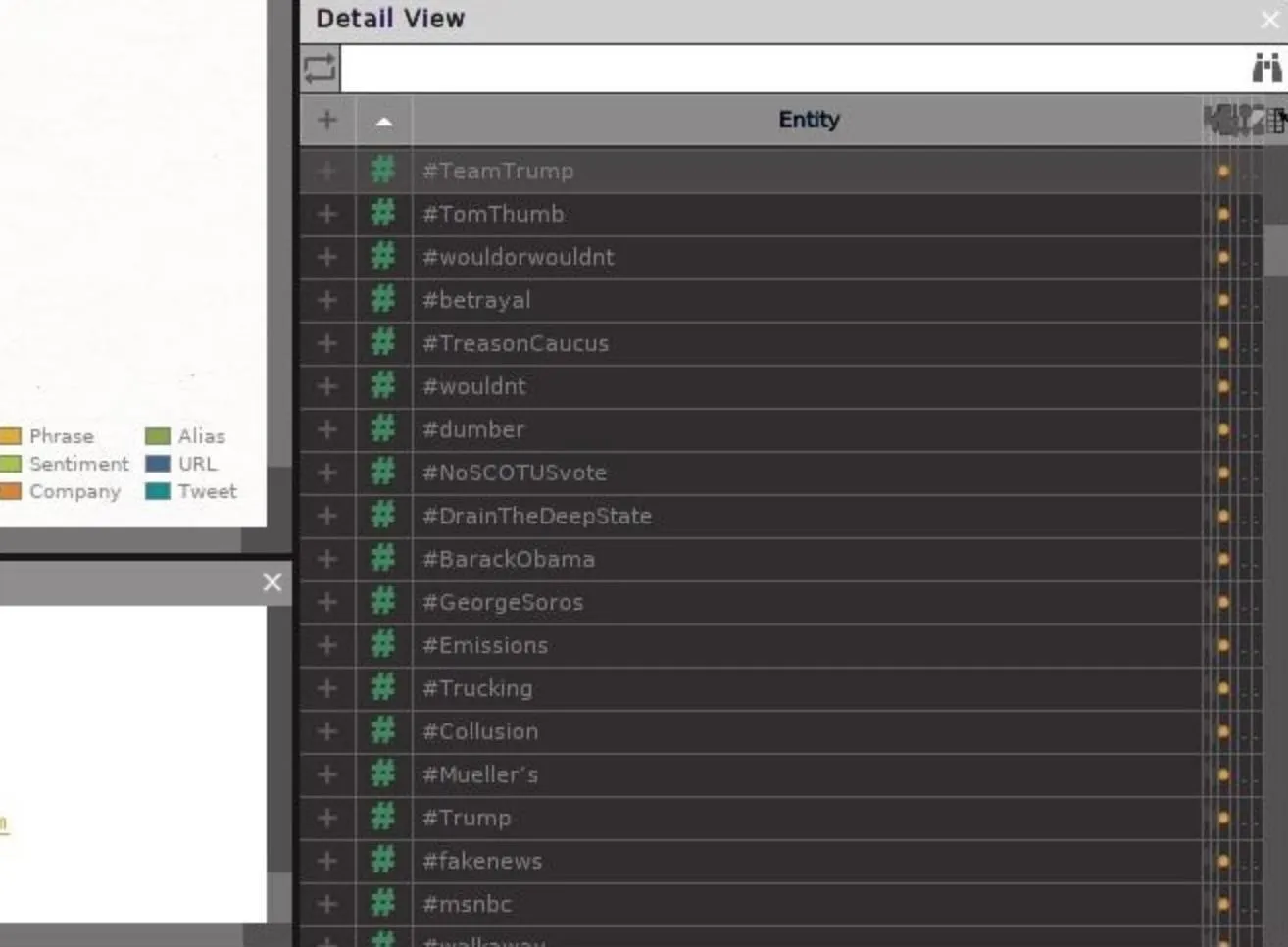
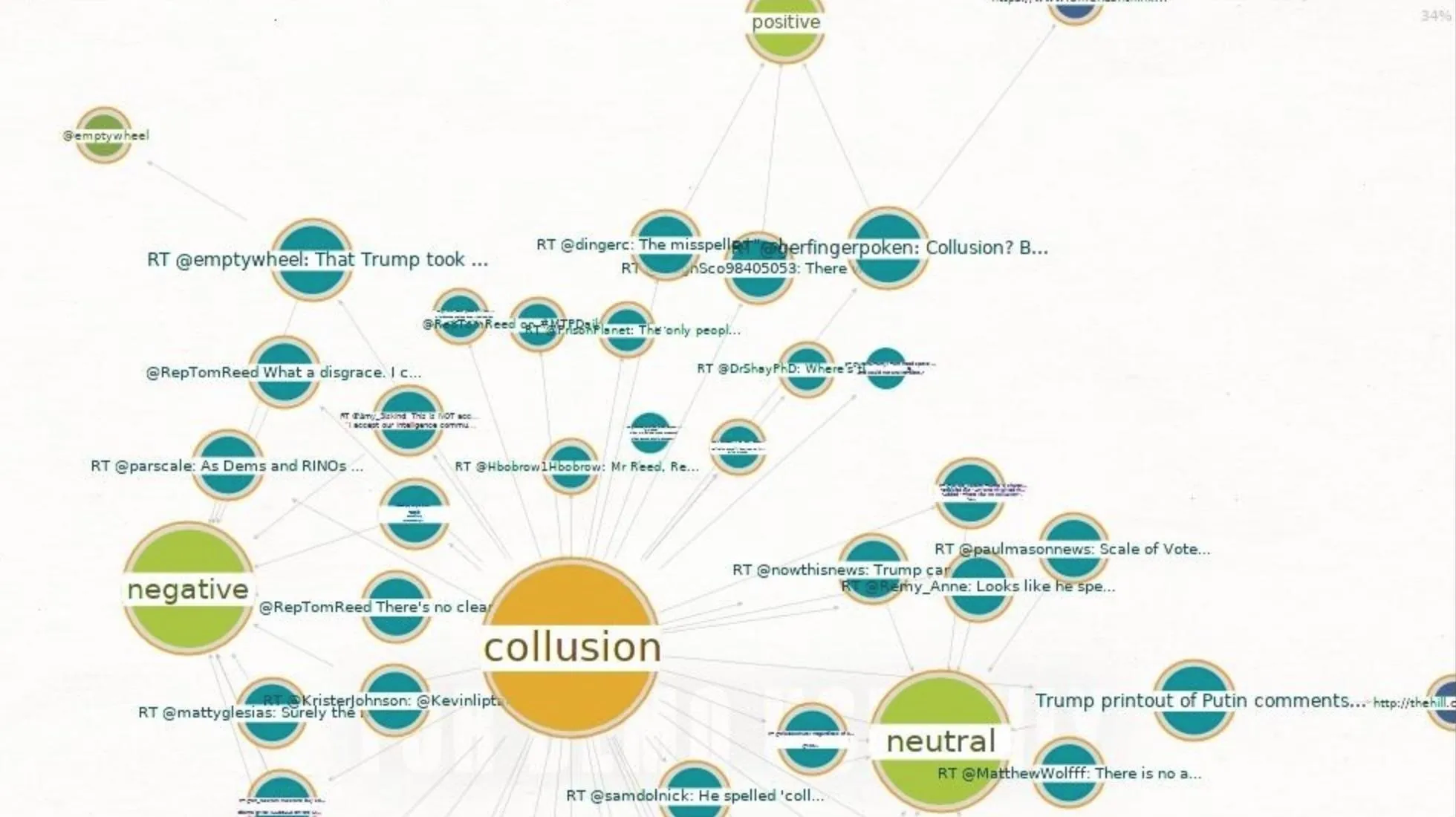
Amplify Divisive Opinions with Sentiment Analysis
Once you've gained a pool of tweets around a certain topic, you can start to automatically organize them by a few rules. One of the most interesting is sentiment analysis, which allows you to separate out negative or positive tweets about the topic you're monitoring. These tools have been available to social media manager for years, but Maltego allows hackers to have the same advantage.
To sort discovered tweets by sentiment, select all with Ctrl-A, then right-click to show the transform menu. Type "sentiment" to show the "To Sentiment [IBM Watson]" transform. Click on this to run it on all discovered tweets. If you have a lot of tweets in the Community Edition, which has a 50 entity per run limit, grab the tweets 50 at a time in the Detail View and run them through the transform quickly to squeeze all the data out quickly.
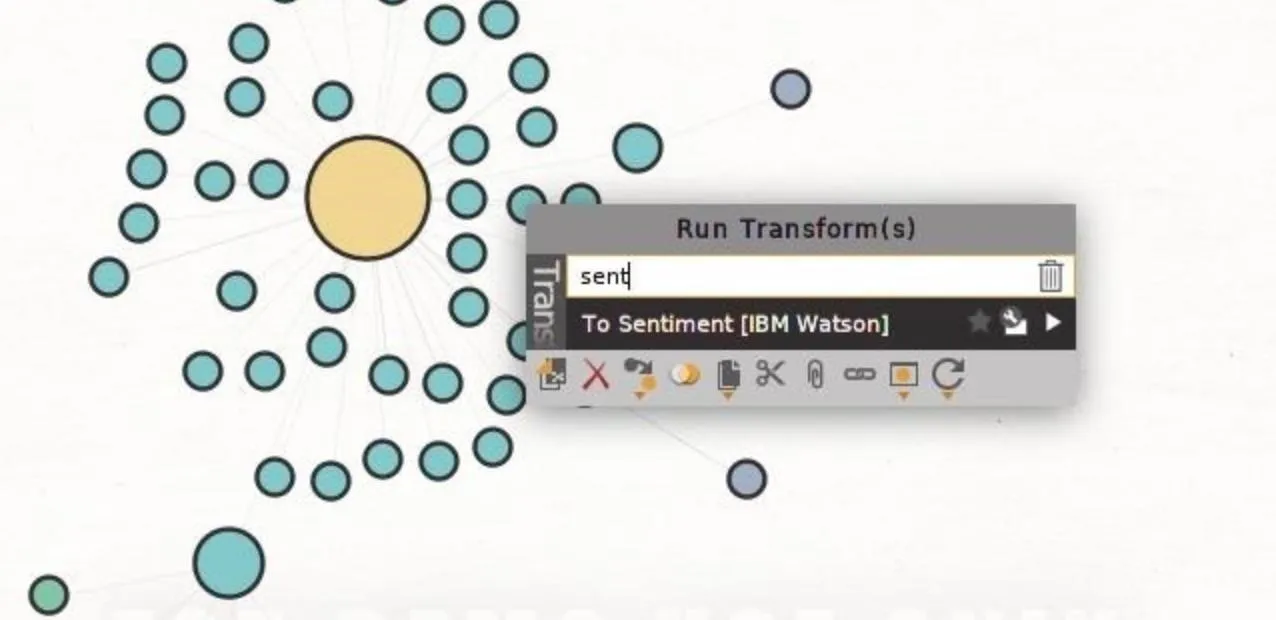
The output will do a serviceable job of trying to organize the tweets by the meaning behind them. This does have its limitations, as sarcasm still can fool this system pretty badly.
You can see all the negative tweets by selecting the "Negative" ball, then selecting the "Investigate" tab at the top left. Next, click "Add Parents" to add every tweet that has been sorted as "Negative." You can do the same with the "Positive" and "Neutral" balls, too.
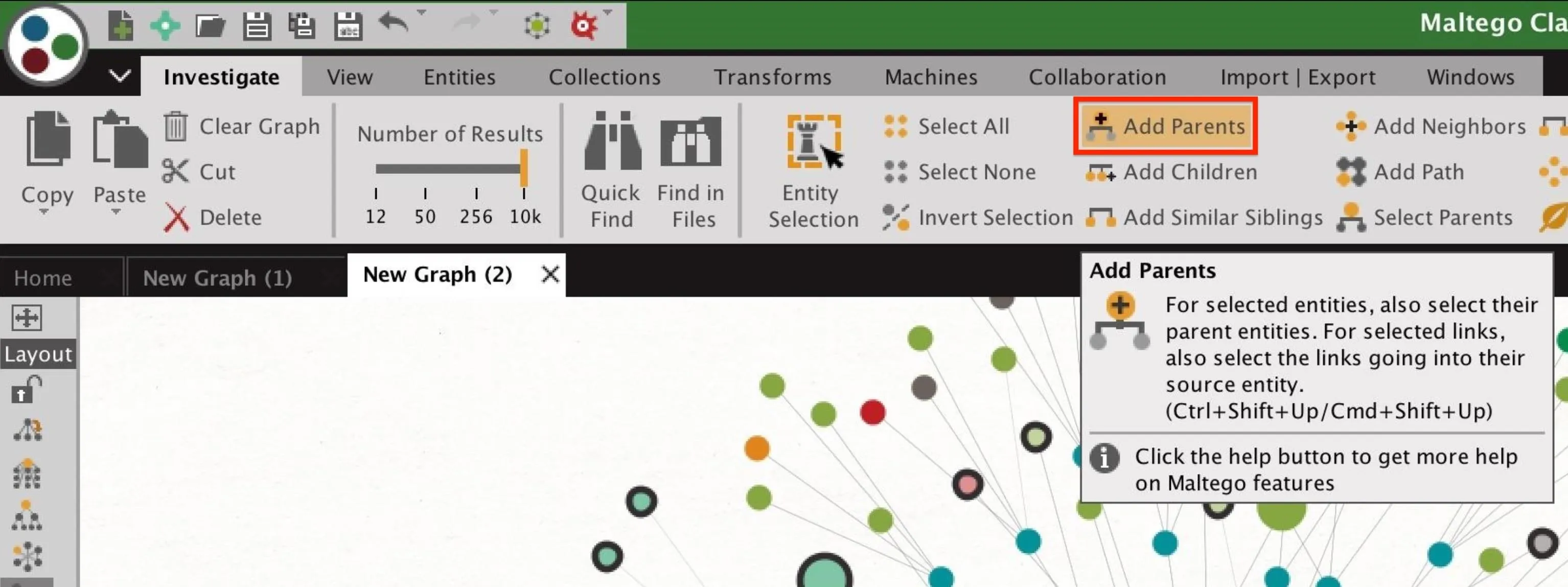
You can use this approach to sort incoming tweets, and in an attack, a series of bots could simply amplify one side of the conversation to overwhelm the legitimate discourse. The tactic of sorting legitimate tweets by what the user is expressing and promoting one side over the other becomes much easier and more effective with tools that automate the process.
Freedom of Speech on Social Media Isn't Guaranteed
Thanks to the promise of open communication in real time in a scalable fashion, Twitter has been used by journalists, activists, and others reporting critical information or coordinating events. This use has made the service a prime target for monitoring, interfering with, and suppressing online conversations by those with the resources to do so.
Advanced persistent threats like nation-state backed hackers will continue to exploit these weaknesses in platforms like Twitter that are used for online discussions to satisfy political, propaganda, and censorship ambitions.
Because these attacks borrow from traditional jamming, some of the same defenses can be applied. First, finding out whether jamming is taking place in the first place must be established. If a conversation is suddenly flooded with messages from accounts which have little to no legitimate posts, or which appear to have been hijacked and are suddenly acting out of character, this is a sign a conversation is being targeted autonomously. Using the same tactics in Maltego, you can explore talks of interests and determine the likelihood they are being influenced or jammed.
I hope you enjoyed this guide to using Maltego to monitor events on Twitter in real time! If you have any questions about this tutorial or Maltego machines, feel free to leave a comment or reach me on Twitter @KodyKinzie.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo and screenshots by Kody/Null Byte




Comments
No Comments Exist
Be the first, drop a comment!