Welcome back, my hacker novitiates!
If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.
In the previous tutorials in this series, we installed and configured Snort on our Kali system. In this tutorial, we will be taking the next step in building a production-level, professional IDS—getting intrusion notifications we can easily analyze.
Snort has many capabilities and configurations, but we want an IDS that can be used in a secure, professional way to alert us of intrusions. To do so, we will need to send our alerts to a database where we can analyze them. We will be setting up a print spooler specifically designed for Snort called Barnyard2 and using it to send the data to a MySQL database.
In the previous guides, I used Kali as my base OS. Unfortunately, some of the libraries necessary to run Barnyard2 do not work well on Kali. As a result, subsequent tutorials in this series will be with Ubuntu. Everything you have done up to this point in setting up Snort works well in Ubuntu without modification. In reality, this makes much more sense as you would not likely be using an attack system like Kali as your server for Snort in a production environment.
Why Barnyard2?
Converting binary data to a human-readable form (usually binary-to-ASCII) is very CPU-intensive for any application. This is particularly true for Snort, and since we want to dedicate as much of our resources to packet capture and analysis as possible, we would like to lay off as much of these CPU-intensive tasks as we can. That's what Barnyard2 is designed for.
In a production environment, we want to send the event data from Snort to a database. Snort is capable of using any ODBC database such as Oracle, Microsoft's SQL Server, PostgreSQL, and MySQL. Here we will be using MySQL as this is the most common configuration for Snort. If we can send the alerts to a database, then we can query the database with another tool to be able to make sense of this information. For instance, we can query for what rules were alerted on, what IP addresses did the attacks come from, what severity level were the intrusions, etc.
Here, we will configure Snort to process its alerts in binary form—it's simplest and least CPU-intensive form—and then use Barnyard2 to read these events, convert to human-readable form, and place them into a MySQL database.
I want to note before we proceed that Snort will work without Barnyard2, but it will slow down its functioning—and potentially not process and analyze some packets in a busy environment—which may be dangerous.
Step 1: Install Barnyard Prerequisites
Before we begin, we need to install some libraries and applications that are Barnyard2 prerequisites.
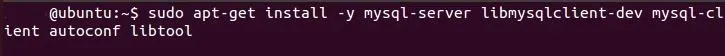
ubuntu > sudo apt-get install -y mysql-server libmysqlclient-dev mysql-client autoconf libtool
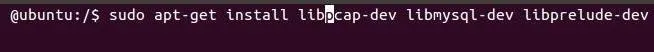
ubuntu > sudo apt-get install libpcap-dev libmysql-dev libprelude-dev
Step 2: Install Git
We will be downloading and installing the latest version of Barnyard2 from GitHub. If you don't already have git on your system, you will need to install it now.
ubuntu> sudo apt-get update
ubuntu> sudo apt-get install git
Step 3: Edit Snort's Configuration File
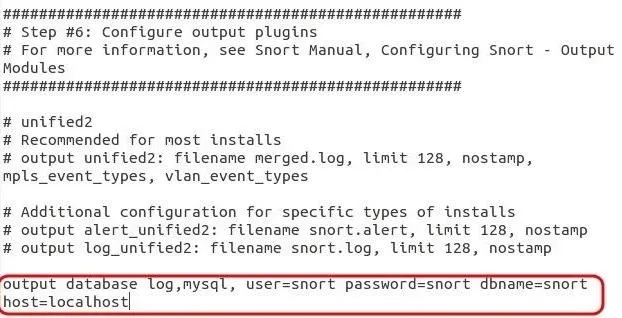
To direct our alerts to a database, we will need to edit the snort.conf file. Open it with any text editor and go to the output section (section #6). There, we will be telling Snort to use our MySQL database (that we will be creating later in this tutorial with the username and password of your choice).
In this example, I have used some simple selections for the database name, user, and password, all snort. Of course, replace those with your own selections (see Step 6 below).
Step 4: Download Barnyard2
Barnyard2 is a print spooler than reduces the overhead of the Snort daemon to write the alerts to a human-readable form. Instead, it allows Snort to write these alerts in the far more efficient binary form, then Barnyard2 takes those binary files and converts them to a human-readable form. Lastly, it places them in a MySQL database for later analysis.
Let's go ahead and get Barnyard2 from GitHub.
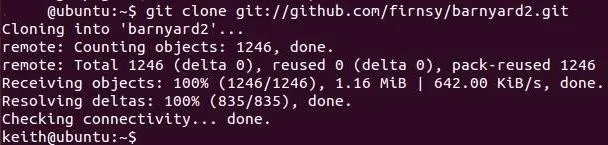
ubuntu > git clone git://github.com/firnsy/barnyard2.git
Now, let's check to see whether it was downloaded and installed by doing a long listing on this directory.
ubuntu > ls -l
As you can see, it has created a directory named barnyard2. Let's navigate to it and list its contents.
ubuntu > cd barnyard2
ubuntu > ls -l
Notice the very first file named autogen.sh. Let's execute that script.
ubuntu > ./autogen.sh
Next, type the following line.
ubuntu > CFLAGS = '-lpthread'
Then, run the appropriate configure command for your system.
If you are using a 64-bit architecture—and I hope you are—this is the appropriate configure command:
ubuntu> ./configure --with-mysql-libraries=/usr/lib/x86_64-linux-gnu --prefix=$HOME/barnyard2-install
If you are using a 32-bit architecture, then the configure command changes slightly to:
ubuntu > ./configure --with-mysql-libraries=/usr/lib/i386-linux-gnu --prefix=$HOME/barnyard2-install
There is one more library that Ubuntu needs for Barnyard2 called libdumbnet-dev. Let's get it from the repository.
sudo apt-get install libdumbnet-dev
Because the make script for Barnyard2 is expecting the dependency file named dnet.h, we need to create a symbolic link between dumbnet.h and dnet.h (the file names changed since the script was written).
ubuntu > ln -s /usr/include/dumbnet.h /usr/include/dnet.h
Then, update the libraries.
ubuntu> sudo ldconfig
Now, we can make Barnyard2.
ubuntu > make
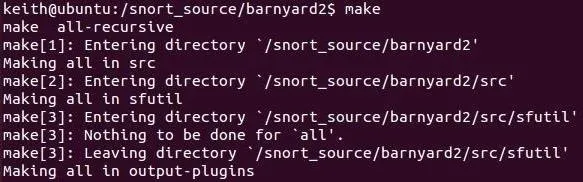
Finally, we need to make and install.
ubuntu > sudo make install
Step 5: Configure Barnyard2
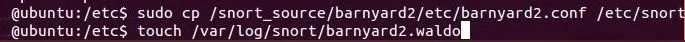
We need to do some basic configuration on Barnyard2 to make certain it runs properly. First, we need to copy Barnyard2's configuration file to the /etc/snort directory.
ubuntu > sudo cp /snort_source /etc/barnyard2.conf /etc/snort
Now we need to create a file that Barnyard2 needs in the var/log directory. This is the bookmark file.
ubuntu > touch /var/log/snort/barnyard2.waldo
Step 6: Set Up MySQL
Now that Barnyard2 is installed, compiled, and configured, we need to set up MySQL to receive the alerts. To do so, we need to:
- create a database
- create a database schema for the alerts
- create a user
- grant the user the appropriate privileges
Let's start by logging into the MySQL database system.
ubuntu > sudo mysql -u root -p
When prompted for a password, enter snort.
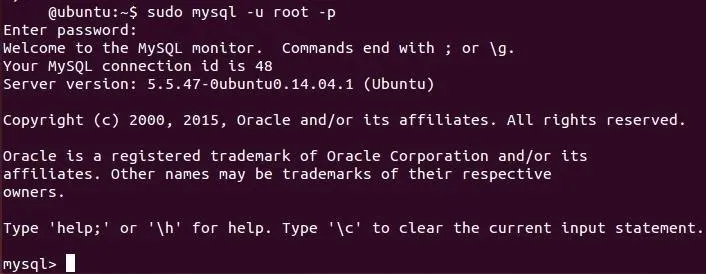
You are now in the MySQL system and should receive a MySQL prompt. Let's create a database for the Snort system to use.
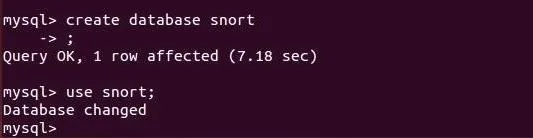
mysql > create database snort;
(Note that snort here is simply the name of the database we will be storing our alerts in. It could be named anything, but let's make it easy to remember.)
Then let's tell the system we want to use that database.
mysql > use snort;
Barnyard2 comes with a script to create the schema for the Snort database. It is at /snort_source/barnyard2/schemas/create_mysql. We can run the script by typing:
mysql > /snort_source/barnyard2/schemas/create_mysql
Next, we need to create a user for the snort database in MySQL.
mysql > CREATE USER 'snort'@'localhost' IDENTIFIED BY 'snort'
This command creates a user snort on the localhost server that uses the password snort. The name of the user and password can vary, but must be consistent with what you entered into the snort.conf file in Step 3 above.
Now to give that user the necessary permissions.
mysql > grant create, insert, select, delete, update on snort.* to 'snort'@'localhost';
This gives the user snort the rights to create objects, insert data, select data, delete data, and update data in the database snort at localhost.
That's it! Now we have set up Snort to send its alerts to a file where Barnyard2 will pick them up, convert them to human-readable form, and place them in our Snort database in MySQL.
In future tutorials in this series, we will begin sending the alerts to the database and analyzing those alerts, so keep coming back, my hacker novitiates!
Cover image via Shutterstock




Comments
No Comments Exist
Be the first, drop a comment!