Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.
Why Privacy & Security Matters
While you may not have anything to hide, there are still many things in your digital and personal life you should want to protect. Your phone number, your computer, your smartphone, your online accounts, your bank accounts, your email address, your home security system, even your home — these are all items you'd probably want to secure with passwords, biometrics, and other tools made available to you.
In 2018, there were a number of significant data breaches. Collectively, they affected hundreds of millions of people worldwide, and you may have been one of them. Listed below are some of the biggest hacks of 2018, which includes compromised phone companies, e-commerce websites, and social media giants — all of which may have had access to your personal data.
- T-Mobile: Hackers stole personal data belonging to T-Mobile customers. 2 million users affected.
- Cathay Pacific Airways: A data breach containing passport information, credit card numbers, and email addresses. 9.4 million users affected.
- Ticketfly: A hacker exploited a vulnerability in the website which led to a leak containing names, home addresses, email addresses, and phone numbers. 27 million users affected.
- Facebook: Attackers gained access to millions of highly sensitive data. 29 million users affected.
- Google+: A bug in Google's software exposed customer data to the internet. Fortunately, there were no reports of hackers discovering this vulnerability. 52.5 million users affected.
- Quora. A data breach that led to leaks containing names, email addresses, encrypted passwords, and data from user accounts. 100 million users affected.
Website databases aren't the only way hackers may try to compromise your digital privacy and security. It may not always appear as if your digital identity holds much value, but hackers and criminals may find ways of targeting your friends and family via your online profiles. They could also find other ways of abusing information you've shared online in recent years.
- Cyberstalking: This type of harassment is a real possibility for anyone with an online presence. In more extreme cases, hackers may find themselves in a position to blackmail the victim, upload their information to prostitution websites, or even locate them at their place of work and home. Worse still, children are often targetted by cyberstalkers.
- Doxxing: Another form of internet harassment, where hackers will publicly disclose personally identifiable information belonging to a victim on public websites. Data found in doxes usually include full names, social security numbers, spouse and children personal information, home addresses, phone numbers, email address, passwords, and much more. This information is shared with the intent of other hackers abusing the data and further harassing the victims.
- Identity theft: The recent Equifax hack put millions of people at risk of identity theft. And that's just one example of a massive data breach. Every single day, hackers target individuals in an effort to steal identities. Becoming the victim of such a hack can cause catastrophic or permanent damage to a person's life.
- Internet service providers: ISPs have become increasingly aggressive about abusing customer data. It's not uncommon for ISPs to sell customer data, embed supercookies into web traffic, inject code into websites without consent, as well as use spyware and crypto miners.
- Government agencies: Governments around the world have worked independently and cooperatively to create spying programs designed to harvest and analyze data on a global scale such as ECHELON, XKeyscore, FASCIA, and PRISM. Disclosed by Edward Snowden over five years ago, PRISM is still in full effect. Journalist Glenn Greenwald highlights some of the risks of government spying and combats the "I've got nothing to hide" argument in a TedTalk.
'Private Browser' Mode Isn't Protecting You
In a recent study held by DuckDuckGo, the company asked 87 volunteers in the US to make identical Google Search terms while in private browser mode and logged out of their Google accounts. Now, according to Google claims, without the help of browser cookies, all (if not most) of the volunteers should've produced the same search results. However, DuckDuckGo researchers found that:
- Most volunteers received results unique to them.
- Entire websites were omitted from search results for certain volunteers.
- Results within the news, video, answers, shopping, snippets, and knowledge graph infoboxes also varied significantly.
The findings of this research are significant because it shows that Google utilizes more than browser cookies to target its users and create filter bubbles. The Google Search algorithm also takes into consideration our IP address, web browser type, operating system, and more. No one should feel protected or anonymous while in private browser mode or when using Google Search.
Getting Started with Privacy & Anonymity
You can easily terminate all of your personal accounts and use the internet as little as possible. That would create a small (if not non-existent) digital fingerprint — but that's not the intention of this article. Instead, you should be able to enjoy the internet without completely sacrificing your digital freedom or forfeiting your digital identity to profit-driven companies like Google and Facebook.
Simply switching to a Linux distribution isn't the solution either. Even open-source and privacy-respecting organizations find themselves on the front page of the news. In times like this, it's important to proactively protect yourself from hackers, cyberstalkers, advertisers, and data-hungry organizations alike.
When talking about security, adding defensive measures almost always creates an inconvenience for the attacker but also the user. It's for that reason, these security and anonymity measures have been separated into four different categories varying in difficulty: Easy, Moderate, Hard, and Extreme.
Easy: Best Security Practices
The security recommendations in this category can and should be implemented by everyone. These tips will not inconvenience most of you but will likely thwart basic hackers.
In later Hard and Extreme categories, readers will learn to utilize free and open-source software, as well as anonymity tools and techniques. Those sections are geared toward those of you who don't mind being inconvenienced to dramatically improve your privacy, security, and anonymity.
1. Use Two-Factor Authentication
Two-factor authentication (2FA) adds an additional layer of security to online accounts. It allows you to generate a one-time-use security code for account logins. The security codes are generated locally on your phone, which means a hacker who has successfully acquired your login credentials will also need physical access to the 2FA app or SMS texts on your phone before they can do any damage.
Two-factor authentication should be enabled on as many websites and apps as possible. TwoFactorAuth.org has a comprehensive list of sites currently supporting 2FA, including Apple, Binance, IFTTT, Instagram, and Snapchat are just a few. However, don't use SMS-based 2FA codes. It's an unsafe practice. Both Gmail and Bitcoin accounts have been compromised even when secured by SMS-based 2FA.
2. Don't Give Away Your Info on Social Media
Hackers can easily gather bits of personal information about you collected across all of your social media accounts. While posting your date of birth on one website and your phone number on another may seem harmless, hackers can gather and use that information to social engineer their way into other accounts you own.
- Phone numbers: A hacker with your phone number(s) can social engineer your cell phone provider into forwarding text messages to an anonymous number they own. This would allow them to bypass SMS-based two-factor authentication protections.
- Addresses: Your home, work, family, and friends addresses should never be shared online. Likewise, diners, parks, and public places you frequent should never be advertised or linked to a photo. Address sharing is often marketed as a convenience tool — and it is. It allows your friends and family to easily find you during a meetup, but it also allows hackers to easily locate your geographic location with terrifying accuracy.
- Names: In 2019, it's bad security practice to use your real name when signing up for websites. Hackers may use this information for social engineering attacks, identify theft, and other illegal activities.
- Photos: Catfishing is a serious problem on the internet. A hacker may decide to use your selfies in a catfishing scheme which can result in legal issues or public embarrassment for you and your family.
Generally speaking, submit as little personal data to social media websites as possible. If a particular website doesn't absolutely require your real information to sign up, don't include it. A general rule of thumb here, ask yourself: "Does this website absolutely need my real name and real information?" If it's not vital to how the website operates (e.g., bank accounts), then don't submit personal information.
- Don't Miss: How to Make an Anonymous Facebook Profile
Avoid strangers online. Try to avoid communicating or sharing any kind of information about yourself — regardless of how harmless the information may seem. A conversation with someone about your grade school teacher's name might be all a hacker needs to bypass a login security question. Patient hackers and cyberstalkers will gradually be able to collect small pieces of personal information about you to compromise accounts or discover your home address. Remember, people can be easily social engineered and tricked into divulging their passwords and security question answers.
3. Get Rid of Unnecessary 'Friends' on Social Media
Some people keep too many "friends" on Facebook. We're talking about friends of friends and people we've never met in real life that serendipitously happened into a public Facebook conversation you were a part of and later friended you. These interactions could easily be engineered by a hacker attempting to infiltrate your private accounts.
Cyberstalkers on social media may follow you to track your whereabouts and activities. However, you may not always be the primary target. Hackers may use you to pivot to one of your children, friends, or relatives. Similarly, catfishers may follow you on online to steal your photos for fraudulent activities which could result in criminal charges again you.
As a best practice, take an afternoon to go through all of your social media accounts. Unfollow people you don't actually know in real life and minimize the number of photos you upload to websites.
4. Use These Smartphone Best Practices
Smartphone security is a complex topic. For now, we'll have a look at general best practices that may make it more difficult for hackers to compromise your mobile devices.
- Uninstall apps. Less is more. If you don't absolutely need an application, uninstall it. Uninstall unused and shady applications immediately. It's not uncommon for hackers to embed backdoors into Android apps and upload them to the Google Play Store. And it's not uncommon for developers to have innocent apps that are later updated with malicious intentions.
- Turn off Bluetooth. If you absolutely need Bluetooth enabled, then, of course, use it. However, there are quite a few Bluetooth exploits in recent years. Bluetooth security is far from bulletproof. A number of critical Bluetooth vulnerabilities have been disclosed in recent weeks.
- Turn off location services. If an app doesn't absolutely require your location to operate, turn off its access to your device's geolocation. Or at least, turn it off as soon as you're done performing the operation.
- Use stronger PINs and passwords. For physical security, don't use short and easy-to-guess PINs or passcodes. Studies have shown the PIN "1234" is used by 1 in 10 people. This is a dangerous practice. Passcodes greater than 6-digits or passphrases containing letters and digits are strongly recommended.
- Use a VPN. They are available for both Android and iOS and encrypt all data traffic in a secure tunnel. It can be slower, but it's well worth the extra security. It also masks your IP address so you don't have to worry about companies or hackers gaining access to it. There are some downsides too, which will learn about in a couple sections.
- Use 2FA. Already discussed above.
- Use a password manager. See the next section.
Another great practice is to purge overly permissive smartphone apps. That game app doesn't need your GPS coordinates. That video streaming app doesn't need access to your call history. If an app is extraneously attempting to access sensitive parts of your device, you'll have several courses of actions:
- Install the app anyway. This is extremely unsafe. Many apps should not require access to call logs, contacts, text messages, or the ability to modified your phones settings. It's a major red flag if apps are requesting these permissions.
- Not use the app at all. As inconvenient as it may be, this is the safest option. The app in question may be a social media application your friends, family, and/or coworkers use regularly. To abstain from using the app would mean isolating yourself (digitally) from people you know and care about — which is terribly inconvenient and an unfortunate consequence some (more extreme) readers deal with every day.
- Use a virtual Android OS. This is less inconvenient and a safer solution that installing a shady app directly to your device. It's quite easy to create a virtual Android OS. These VMs can be easily cloned and deleted if the app turns out to be malicious, as well as used anonymously when coupled with Whonix. Isolating an app to a virtual machine will help isolate and minimize the damage inflicted. For example, the malicious app won't have access to photos, call logs, SMS, and personal files outside the VM.
5. Use Password Managers for Strong Passwords Everywhere
In a recent survey by LastPass, it was disclosed that at least "53% of the respondents confessed to not changing their passwords in the past 12 months ... despite news of a data breach involving password compromise."
This is an unfortunate fact that needs to change. The use of a complex password is vital to the security of your online accounts. If a website has its user database leaked to the internet, a strong password may prevent brute-force attacks against encrypted hashes. This kind of data breach can lead to the compromising of other online profiles you own and is often thwarted by complicated passwords and two-factor authentication.
If a website requires your mothers maiden name or first pets name as a security question, use a randomly generated string as the answer and store it in the password manager. Never use real security question answers. Password managers are great for this.
KeePassX is an open-source password manager for macOS, Windows, and Linux that allows anyone to easily secure their passwords and personal data locally. An attacker would need to first hack the target's computer to compromise the KeePassX database.

If most of your web browsing is done on mobile devices, you can try a password manager like LastPass. With LastPass, your data is stored in the cloud, which can be dangerous. It's still better than nothing.
6. Make Use of Virtual Private Networks
VPNs will not make you anonymous on the internet. VPNs are far from a bulletproof solution but are recommended as a basic line of defense in this Easy category. In later categories where we can't afford to trust their "no logs" policies, VPNs are not recommended. Below are some pros and cons readers should consider.
VPN Benefits
- Enhance security on local networks by preventing man-in-the-middle attacks.
- Access websites without revealing true IP addresses to websites administrators.
- Hide website activity from ISPs (e.g., torrent downloads).
- Bypassing ISP blocks, filters, and caps (in some cases).
VPN Disadvantages
- Provider knows who and where you are.
- Provider can log web traffic without your knowledge or consent.
- Does not make you untraceable or totally anonymous on the internet.
- Slower speeds (usually).
- Can be difficult to install and setup.
- Forced to place blind trust in the VPN provider.
VPNs can be beneficial in some cases. Most notably, they prevent ISPs and attackers on your network from manipulating and collecting your web traffic. The unfortunate side effect of VPNs is we're forced to trust third parties (the VPN providers) over popular ISPs like Verizon. The upside to this is: we know for a fact corporations like Verizon don't have the best intentions with customer data. With VPN providers, there's a chance the provider we choose won't share Verizon's practices.
Free VPN solutions should be avoided as they may inject ads and crypto miners into customer web traffic. Gadget Hacks recommends Windscribe for iOS and Opera for Android.
- Don't Miss: Fully Anonymize Kali with Tor, Whonix & PIA VPN
7. Use These Router Security Best Practices
Securing Wi-Fi routers can be difficult as they're all designed with varying features and unique graphical interfaces. Instead of showing how to secure a single type of router, we'll outline a non-exhaustive number of security recommendations everyone should adhere to.
- Update the firmware. Router companies often issue bug and exploit patches. It's important to keep the router firmware up to date and have it check for updates automatically if possible.
- Disable remote administration. Some routers allow for remote access by default. Without knowing it, hackers may find your router on the internet and seize control of it.
- Change default passwords. Never use the default passwords. This goes for the Wi-Fi password other devices use to connect to the router, but also the admin portal which allows you to change sensitive router settings. There are many websites dedicated to sharing default admin passwords.
- WPA2 encryption. Only use WPA2 encryption. Weaker encryption options like WEP will leave your router extremely vulnerable to attackers.
- Disable WPS. WPS is a feature designed into most routers that are supposed to make secure access to your router without a password more convenient. Unfortunately, this feature is usually enabled by default and can be easily exploited by hackers.
- Be persistent. Change your Wi-Fi password every few months. It's a pain to reset the Wi-Fi password on all your devices, but this tactic will keep hackers guessing ... literally. If a hacker has captured a WPA2 handshake and spends several weeks trying to crack it, changing your password will render the captured handshake useless.
Moderate: Take Back Your Privacy
Welcome to the Moderate category. This section is intended for readers who wish to maintain private communications and scrub their unwanted digital profiles off the face of the internet. Increasing your overall privacy online while operating in secure environments is the goal of this particular category.
1. Make Sure Text Communications Are Private
Text messaging was not designed for secure or private communications. All types of data can be seen by cell phone providers when we send text messages, including location data, timestamps, and user IDs, but more importantly the messages themselves, which can include passwords and 2FA codes, package tracking information, appointment reminders, and other sensitive information.
Facebook Messanger is equally bad, if not worse. Facebook collects a list of running apps and email accounts linked to your smartphone, it can access your contacts and calendars, and it can even send emails to your contacts without your knowledge. It is for these reasons uninstalling Facebook Messanger is highly recommended.
There are several encrypted messanger alternatives:
- Wire. Wire offers secure texting, calling, video chat, and file-sharing without requiring a phone number to signup. It is currently the top recommendation as it has undergone several security audits over the last few years. Wire is cross-platform and fully-featured.
- Signal. Much-like Wire, Signal offers secure texting and calling. Signal's source code has also been audited but has suffered more than one embarrassment in recent months.
- iMessage. Apple's iMessage is the least favorite solution for those looking to improve their text message privacy. Readers should use iMessage with caution as it has its caveats. It's not open-source software so it wouldn't be possible to know what code is actually running in the background. We understand some contacts (friends and family) may not be willing to switch to Wire or Signal. If they're iPhone users as well, iMessage is probably a better option than standard SMS.
2. Make Sure Email Communications Are Private
Standard email methods are possibly one of the least private forms of communication today. To make matters worse, switching email providers can be an incredibly difficult task.
This is especially true if we're talking about transitioning from a five or even ten-year relationship with a particular email address. While completely ditching Gmail is not required in this Moderate category, it's a good idea to start transitioning your most valued accounts to a secure email provider. It's also good to have a secure email alternative on hand for times when we need to share account credentials or personal documents with friends and family.
There are a handful of privacy-respecting email providers but ProtonMail stands out above them all. It's an encrypted email provider that utilizes open source cryptography. Its email encryption makes it difficult for anyone other than you to read the messages in your mailbox. In a blog post, ProtonMail outlines the many reasons their service is more secure than Gmail.

Readers who want to transition from Gmail entirely can start by going through primary online accounts and updating them to use their new ProtonMail email address.
Then, start forwarding Gmail messages to the new ProtonMail email address. This will allow for a gradual transition of old accounts to the new ProtonMail address. Forwarded emails will act as a reminder of which online accounts are associated with the Gmail address. Simply update the online accounts over time. After a few months of this, it will be possible to delete the old Gmail account without getting locked out of online accounts associated with it.
Dislaimer: No email or secure communications provider is 100% immune to compromise. While ProtonMail does what they can to protect customers and their data, we still have to put absolute trust in these service providers not to serve users malicious JavaScript.
3. Be Wary of the App Store You're Using
Those of you with Android phones should stop using Google Play immediately. There havebeenmanyarticlespublished in the last two years related to Google Play Store malware. F-Droid is an open-source, community-maintained software repository for Android OS. Similar to the Play Store, F-Droid allows you to easily install and update applications.




While F-Droid applications could as well silently install malware, the developers utilize LibScout machine learning to detect known tracking libraries and some automated scanning. Moreover, only open-source applications are allowed in the F-Droid repository, which makes it difficult for attackers to sneak in malicious code. F-Droid's security model, inclusion process, and reproducible builds make it the recommended choice.
Additionally, the F-Droid app recently underwent its second security audit. Such audits are important as it makes the F-Droid Android app and their servers much more resilient to outside attacks.
If you're using an iPhone, the iOS App Store is the best option. There aren't any other app markets for iPhone that aren't riddled with software that's pirated, modded, or malicious. If you're jailbroken, there's Cydia and Sileo, but tweaks in those repositories aren't strenuously reviewed. While the iOS App Store has had a few failures in security, it's still the way to go.
4. Keep Google from Tracking You on Smartphones
All Android devices that have access to the Google Play Store (all but a few phones in the US) have to come preloaded with a set of Google apps that include Google Maps, Chrome, and Gmail. However, it's been shown that Google apps can record your location as many as 340 times a day, so these apps aren't ideal for privacy.
Apple apps record your location at a rate roughly one-tenth of Google's (PDF warning). When you combine that with the fact that most Android phones have Google apps preinstalled, while iPhones don't, it's safe to say iPhones are a better option for privacy in most cases.
I say "in most cases" because Android phones can actually be more private than iPhones — in fact, Gadget Hacks recently found that the top two best phones for privacy and security both ran Android. Short of purpose-built privacy phones, however, most Android phones aren't quite as privacy-friendly as iPhones.
For those who dislike Apple or iPhones and wish to remain in the Android ecosystem, you can replace the stock operating system with a custom ROM like LineageOS, which is basically a Google-free version of Android. You can take things a step further by replacing Google services with an open-source alternative like MicroG. So yes, Android phones can be more secure than iPhones, but if you want the best off-the-shelf experience in this area, Apple is probably your best bet.

5. Opt-Out of Shady Telecom Provider Programs
In 2014, it was disclosed that Verizon and AT&T were injecting "perma-cookies" into mobile customers web traffic. This allows phone companies to better track individuals for advertising purposes. AT&T has since stopped the practice after much uproar, but Verizon has not, though, you can opt-out.
There are privacy issues with pretty much every wireless carrier out there, so there's not much to say here besides to be knowledgable of the types of antics they use to invade your privacy. See if your carrier has unique identifier headers to track you for advertising purposes and opt-out if so.
While we could encourage everyone to stop using wireless carriers, something that'd fit more in the Extreme section below, but we know that's pretty impossible in this day and age. So just being aware of everything your carrier is doing and then stopping what you can is the best route to take.
6. Use These Web Browser Best Practices
When talking about web browser privacy and security, there are extreme degrees that can be achieved. In this Moderate category, we'll focus on mitigating cross-site tracking and browser privacy issues.
Google's Chrome and Chromium browsers have come under fire in recent years for enabling user laptop microphones and using other privacy-compromising "features" without warning or consent. It is for these reasons, andmanymore, that Firefox is the recommended web browser for all you privacy-conscious users.
Firefox is a free and open-source web browser with a reputation for respecting user privacy. It's available on all operating systems, including smartphones.

To make hardening Firefox easier on desktops, there are tools like Firefox Profilemaker. Simply click the "Start" button, and it will begin walking you through the different settings available in Firefox while explaining how each function affects the browser. When it's done, download and import the profile into Firefox for the hardened settings to take effect.
As for cross-site tracking, this is a bit more challenging to defeat and therefore an optional step. Cross-site tracking refers to advertisers and companies like Facebook collecting data about you across multiple websites. They usually accomplish this data aggregation through social share buttonsfound on many websites.
These buttons, in addition to first-party browser cookies, make it convenient for website administrations to personalize their visitors' experiences. The unfortunate side effect is they also empower giants like Google, Facebook, and Amazon to track us across multiple domains while sharing information with data brokers and advertising networks.
To mitigate cross-site tracking, Firefox's profile manager can be used to isolate browser activities. For example, using different browsers to separate work accounts, personal profiles, and private browser sessions. The profile manager can be invoked by entering about:profiles into the URL bar.
Below is an example of how profiles can be managed and color coordinated to prevent confusion. Each profile can utilize a different Firefox Profilemaker profile and have varying degrees of hardening applied. For instance, the neutral web browser (black) can harden some privacy and tracking functions, while the private browser (red) hardens them all.

- Green — Work accounts, employee logins, and business bank accounts. The green color can act as a reminder (green like money) that this profile is designated for work-related tasks only.
- Black — This profile would allow cookies to persist in the browser, making it ideal for personal accounts that may be inconvenient to log into several times a day. The black color can act as a reminder that this browser window is somewhat neutral.
- Red — For everything else. This profile would use Private Browser Mode to ensure all browser cookies are purged when the browser window is closed. Ideal for general web searches and internet browsing. The red color can act as a warning that activity inside the browser will not be saved.
Browser extensions are dangerous. Only a few actually improve privacy and security in the browser withoutcompletelyputtingyouatrisk. In most cases, adding extensions and add-ons should be avoided. Many of the browser extension hacks affected Chrome in 2018, but Firefox add-ons are equally vulnerable. There are two add-ons that everyone should use:
- uBlock Origin — An open-source ad blocker designed to allocate very little CPU and memory while efficiently blocking ads. It has gained incredible notoriety over the years as being a superior alternative over popular solutions like Adblock Plus.
- HTTPS Everywhere — Many websites offer HTTPS in the browser but default to unencrypted HTTP. HTTPS Everywhere attempts to secure web traffic by rewriting URLs to use HTTPS every time.
Other noteworthy add-ons include NoScript, Privacy Badger, and Decentraleyes, but are not required. If they are not security-related, be wary of what they are doing.
When it comes to mobile browsers, Safari on iOS is actually pretty decent, since it has an option for disabling cross-site tracking, but Firefox Focus blocks a wide variety of online trackers. It's available for both iOS and Android.




7. Get Rid of Old & Inactive Accounts
The best way to minimize your digital footprint is to start deleting old and inactive accounts. Hackers can use data collection tools like SpiderFoot and Maltego to generate comprehensive activity and behavioral profiles about you.
JustDeleteMe
Many websites make it intentially difficult to find the "delete your account" button. The quickest way to delete online accounts is JustDeleteMe, a directory of direct links to "delete your account" pages for popular websites. It simplifies this process.

Pipl
One great tool for locating accounts you've forgotten about is Pipl, a free people search engine that's very easy to use. Simply enter your common usernames and email addresses into the search bar, and Pipl will generate a list of associated profiles based on public information.
Below I'm using @snubs, a well-known Hak5 personality and influencer in the infosec community, as an example. We see she's on LinkedIn, Flickr, Twitter, FourSquare, and more.

PeekYou
Alternatively, PeekYou can be used as well. In the example below, we can see the accounts associated with the @hak5darren username.

More alternatives include BeenVerified, CheckPeople, and Spokeo. Simply enter your name, usernames, or email addresses into the search engines, and they'll likely produce information you didn't realize was publicly accessible.
Email Searches
Another method for identifying online accounts is to search your email inbox for terms like "sign up," "signup", "verify," "account created," and "verify your email."

Have I Been Pwned
Yet another method for discovering accounts that need to be deleted is Have I Been Pwned. Enter your email addresses into the search bar, and HIBP will tell you which addresses were affected by recent data breaches.

8. Get Delisted from People Search Engines Databases
The battle isn't over after deleting online accounts. Now, the information needs to be removed from the very same search engines used to discover them. Pipl and PeekYou have their own private databases. Deleting an old Twitter account won't necessarily remove the existence of it in Pipl's database. Unfortunately, the only way to completely rid an account from the internet is to contact each website directly and request they remove it.
For example, with PeekYou, it's required to first locate your listing on its website, send them the URL, and request it be removed. Remember to include your name and linked email address or they may not have a way to contact you or verify ownership the account(s) being requested for removal. Ironically, we have to send some personal information to have it removed from internet databases. This process is a real pain, but a necessary evil.
Hard: Don't Support For-Profit Companies
Congratulations on making it this far! If you've successfully managed to put most of the previously mentioned privacy and security tips into practice, you're in excellent shape for 2019.
Keep in mind, the Easy and Moderate categories were more geared toward privacy and basic security practices — not anonymity. This category will focus more on creating small digital footprints going into the future, actively evading aggressive tracking tactics, and only supporting open-source software. As we're about to see, putting these tips into practice will prove to be much more challenging.
1. Stop Using Windows 10 & macOS
There are many privacy concerns with Windows 10 — more than we could fit into this section. The privacy-compromising and telemetry tools Microsoft allows you to disable will not prevent them from abusing its control over the operating system. Below are a handful of reasons why Windows OS is a less-than-adequate choice for a private or secure solution.
- Windows 10 uses an opt-out keylogger.
- Disabling creepy "features" doesn't prevent Windows 10 from collecting data.
- Windows 10 steals your bandwidth.
- With hardened privacy settings, Windows 10 still sends telemetry data over 5,500 times a day.
Similarly, while Apple's macOS is based on open-source software, there are still many closed-source components. To make matters worse, Apple's operating systems, policies, and practices have been criticized in the past for containing backdoors, being involved in censorship, uploading files to iCloud without user consent, and surveilling macOS and iPhone users to several alarming degrees.
Start using a Unix-based operating system as your primary OS. There are so many great Linux operating systems designed for beginners. Elementary OS is one such example (shown below), which recently received a $1 million donation, which allowed them to hire more developers and really push the project to the next level.

Elementary OS has a macOS-like design with a minimalist interface that makes transitioning to a Linux system feel organic. Other recommended Linux distributions include Debian, Fedora, and Xubuntu. They all feature an easy installation process, massive support communities, and more control over the operating system than Windows 10 or macOS will ever allow.
Using an OS like Elementary won't make you completely immune to viruses and malware, however. No computer is. Joining a Linux community is more about supporting organizations that respect user privacy and security. These operating systems empower us to maintain full control over the system while having the ability to harden the OS to our heart's content.
2. Stop Using Gmail
It's time to stop using Google products. For some people, this is significantly more difficult than it sounds. Rest assured, more and more people are switching to privacy-respecting alternatives every single day.
At this point, there are too many privacy, anonymity, censorship, spying, data-mining, tracking, and overwhelmingethicalconcerns to support Google as a company or any of it "free" products. If that's not enough to get you to quit Google, below are several articles that might pique your interest.
- Google+ bug revealed the personal info of 52.5 million customers.
- Google isn't free, we've been paying for it with our freedom.
- Google's Allo service is more about surveillance than encryption.
- Google pays millions to sweep privacy concerns under the rug.
- Leaked documents show Google is making a censored search engine for China.
- Why you should quit Google, Amazon, Microsoft, Facebook, and Apple.
To delete your Google account, first, navigate to myaccount.google.com, and select the "Delete your account or services" button.

Select the "Delete Google Account and Data" button, then enter your password again.

Select the "download your data" button and store your Google data someplace securely in case you need to access an old email in the future. An encrypted container will work perfectly for storing such data.

Back on the deletion page, scroll down to the bottom of the page, check both acknowledgment boxes, and hit the "Delete Account" button.

And you're done! Congratulations on committing to quit Google! As stated previously, you should start using privacy-respecting email providers like ProtonMail instead.
3. Stop Using Google Search
Google's collection and aggregation of user data through the various tools enable it to determine a user's route through the internet by tracking IP addresses and cookies (cross-domain tracking). And remember: private browser mode (incognito) doesn't protect you entirely. Fortunately, there are several privacy-focused search engines available that allow you to search the internet without linking queries to your identity.
SearX, for example, is a highly customizable meta-search engine. It queries dozens of other search engines simultaneously to produce the best possible results. There are over one hundred search engines available to Searx including DuckDuckGo, Bing, and StartPage. Best of all, SearX supports operators (aka "Google Dorks") for advanced search queries, all without compromising your privacy or serving ads.
- Don't Miss: Create Your Own Search Engine for More Privacy

Now, keep in mind, Google has expertly embedded itself into so much of our digital lives. It's near impossible not to unknowingly send data to its servers in one way or another. Even if you're not an avid Gmail, Google Search, and Google Maps user, simply visiting an ordinary non-Google website might result in your computer silently contacting Google-owned servers. We're talking about Google Fonts, Google Analytics, Google AdSense, and other Google products. In later sections, we'll show how to actively avoid these lesser-known analytical and privacy-invading services.
4. Stop Using Social Media (Sorta)
This is likely another big hurdle for most readers. Disconnecting from popular social media websites can be a real challenge. For some, Facebook is their primary method of communication with family members who are in different parts of the world. To make matters worse, social media websites make their services intentionally addictive to keep people from quitting while forcing them to consume ads.
Social media giants are susceptible to massive data breaches just like any other website and are known to sell customer data to third-parties. Furthermore, cyberstalkers and hackers can abuse the information you put online to compromise your digital and personal life, as well as the lives of your friends and family.
The good news is: we don't have to quit social media entirely. While the below websites can also be hacked, they at least allow people to sign up and access the website without forcing them to submit a phone number or real name. Now is the time to help your family and friends switch to privacy-friendly social media solutions. Don't wait for another data breach that results in their private data being shared by hackers around the world. There are some open-source, decentralized, and privacy-respecting alternatives that allow everyone to socialize securely while maintaining control over their data.
Disroot
Disroot providers a collection of services based on principles of freedom, privacy, and decentralization. It takes pride in its no tracking, no ads, and no data mining policies. Its services include email, chat client, pastebin, search engine, and more.

Mastodon
Mastodon is a free, open-source, Twitter-like platform. Like Disroot, Mastodon has no advertising, monetizing, or major corporations behind the project.

Diaspora*
Diaspora* is a non-profit, distributed social network that consists of independently owned "pods." The pods work together to form the social network.

5. Use Free & Open Source Software
Free and open-source software (FOSS), in contrast to Apple's and Microsoft's proprietary software, is software that anyone can review and audit. It is also freely available (actually free) to copy and use. In this Hard category, it's important to avoid proprietary software that can't be reviewed by third-parties and independent developers.
The use of open-source software is vital to your privacy, security, and anonymity. A good example of this is when the Kodi community discovered malicious code in a streaming app that turned everyone's Kodi device into a DDoS botnet. If Kodi and its extensions weren't open-source, it might've been weeks, if not months, before someone discovered the DDoS activity originating from Kodi devices.
To help you transition from popular third-party software to open-source solutions, below are several great alternatives to popular closed-source software.
- Discord: Wire, a cross-platform and fully-featured alternative with secure texting, calling, video chat, and file-sharing.
- Dropbox: Syncthing, a lightweight file-syncing solution. No data is ever stored anywhere else other than on your computers.
- Evernote: EtherCalc, a web-based spreadsheet, designed for teams working in collaboration. Changes to a document are reflected in real-time across everyone's screen.
- Facebook: Diaspora*, a distributed social network that consists of independently owned "pods." The pods work together to form the social network.
- Facebook Messanger: Wire, a cross-platform and fully-featured alternative with secure texting, calling, video chat, and file-sharing.
- Gmail: ProtonMail, an encrypted email provider that utilizes open-source cryptography.
- Google Chrome: Firefox, an open-source web browser with a reputation for respecting user privacy.
- Google Drive: SpiderOak, an online backup and file hosting service that allows you to synchronize and share data using an encrypted cloud-based server solution which doesn't allow SpiderOak or (or anyone) access to data stored in the cloud.
- Google Maps: OpenStreetMap, a community-based Google Maps alternative that respects user privacy.
- Google Search: SearX, a privacy-focused meta-search engine that queries dozens of popular search engines simultaneously to produce the best possible results.
- LastPass: KeePassX, a password manager for that allows anyone to easily secure their passwords and personal data.
- Twitter: Mastodon, a Twitter-like platform with no advertising, monetizing, or major corporations behind the project.
For more alternatives, check out PRISM-Break.org
6. Utilize Disposable Emails
Disposable email addresses are a fantastic way to evade spam while minimizing exposure to website data breaches. For example, when a websites gets hacked, user email addresses are usually among the first thing hackers start passing around. In some cases, spammers will even buy email databases from hackers for email bombing schemes and other nefarious purposes.

Guerrilla Mail is the disposable email provider of choice. At the time of this writing, Guerrilla Mail allows up to eleven different domains (e.g., @guerrillamail.com, @grr.la, @spam4.me), access via onion service (for anonymous access, which will be convenient in later steps), and the ability to scramble the email address.
Scrambling the Guerrilla Mail address is very important to the usage of disposable addresses. In the event hackers acquire a leaked database containing your Guerrilla Mail address, the scrambled address will prevent them from simply logging in as you and resetting account passwords associated with the disposable email address. Always scramble the Guerrilla Mail address before signing up for websites.
When storing disposable email addresses in your password manager, be sure to save the unscrambled address as well. This will allow for access to the email address again in the future, in case you need to reset the password or verify the account for some reason.
It's not recommended to use disposable email addresses with sensitive accounts like banking and Bitcoin wallets, however. Sensitive accounts should be linked to your primary ProtonMail email address. While your Instagram and Reddit accounts, for example, can use Guerrilla Mail without damaging your security and simultaneously minimizing your exposure to data breaches.
7. Use a Privacy-Focused Smartphone ROM
At the time of this writing, Plasma Mobile is the only viable non-Android smartphone OS far along enough into development worth recommending.
Plasma Mobile is a completely open-source, Linux-based mobile operating system. And best of all, it's not based on Google's Android OS. It is currently under active development so the end-user experience may not be as flawless if you're used to Android. To get started, reference the official site for different ways of joining the community and contacting the developers.

As an alternative, postmarketOS is another Linux-based mobile OS but it still in the very early stages of development and therefore isn't stable enough to confidently recommend. In the future, readers can look forward to the Librem 5 and the Necuno. Both devices are 100% open-source Android OS alternatives.
8. Only Use PrePaid Debit Cards Online
Credit card numbers are dumped on the internet and shared privately on websites every single day. The below screenshot was taken from a website that publicizes new credit card information several times a day.

The website is currently online and seemingly publishes hacked credit card information for no reason at all. How this data is acquired is unclear but anyone can easily become a victim of such compromises. Fortunately, using disposable debit cards will drastically help mitigate this kind of exposure.
When making online purchases, it much safer to use disposable debit cards with a limited dollar value attached to the card. For example, losing a disposable card with only $200 USD on it will be far less devastating than hackers sharing your credit card info and accumulating $10,000 in credit. In the latter scenario, your funds will likely remain depleted for weeks while the credit card company attempts to verify your claims of being a victim of fraud.
Additionally, when registering and activating the card, false information can sometimes be used to further minimize your attack surface from data breaches suffered by the companies distributing the disposable cards.
The use of prepaid debit cards will help prevent fraud, as well as allow for some degree of anonymity when making purchases online.
9. Use the Tor Browser Bundle
Start using the Tor Browser as often as possible. It offers a simple solution for those of you who want to browse the internet anonymously, as we begin to dive deeper into anonymity technologies and concepts.
The Tor network is a collection of thousands of volunteer-operated servers that allow anyone to improve his or her privacy and anonymity on the internet. The Tor browser allows us to securely access the Tor network and prevent tracking techniques deployed across the internet, like Google Analytics. For those of you who are unfamiliar, Tor provides a brief two-minute video that explains what Tor is and how it works.

When using the Tor Browser, resist the urge to install any of browser add-ons. This is contradictory to what's stated in the Moderate category where we recommend installing uBlock Origin and HTTPS Everywhere. Part of how the Tor Browser is able to protect anonymity is by making all of your web traffic appear indistinguishable.
For example, if ten people are using the Tor Browser to visit the same website and one of them has a User-Agent spoofing add-on installed, the Tor exit operator (possibly fingerprinting web traffic) and the website administrator(s) will be able to easily single out that user's web behavior from the other nine Tor Browser users. Additionally, Firefox add-ons are not audited or inspected by Mozilla or Tor developers, and they may even find ways of circumventing the browsers proxy settings — which could lead to de-anonymization. It's difficult, but in this Hard category, it's time to ditch your favorite browser add-ons entirely. They're unsafe and damage your anonymity.
There are a few caveats to using the Tor browser you should be aware of. The NoScript add-on (installed by default) can sometimes break websites or prevent certain JavaScript elements from displaying web content. This can be frustrating and is an unfortunate side effect of hardening web browsers. Other times, CloudFlare, a web application firewall service, will block your exit IP address, and you'll have to deal with a lot of CAPTCHAs.
A starter guide to Tor Browser best practices can be found on the Whonix website. For a more technical understanding of how Tor works, check out the official documentation. For help setting things up, visit the Tor StackExchange website or check out Null Byte's article by Black Slash.
Extreme: Anonymity Best Practices
The recommendations in this Extreme category introduce some advanced concepts intended for those of you who wish to maximize your operational security while remaining as anonymous as possible.
Be advised, practicing the below steps without first adhering to the privacy and security practices in the Moderate and Hard categories will dramatically reduce the reliability of these Extreme recommendations. For example, using Whonix on a Windows 10 or macOS host is greatly discouraged for the reasons outlined earlier in the article. Or creating fake identities using a Gmail account will allow Google to collect data about you, the identity, and other accounts that may be linked to the Gmail address.
Implementing any number of the below recommendations (correctly) will significantly improve your privacy and anonymity in 2019. Congratulations on making it this far.
1. Use Cryptocurrencies for Online Purchases
Cryptocurrencies like Bitcoin, Ethereum, and Monero allow people to make purchases online with some degree of anonymity. As with prepaid debit cards, cryptocurrencies can help minimize exposure to credit card fraud while providing some degree of anonymity to online transactions.
The benefits and disadvantages of cryptocurrencies have been covered in greater detail in Hoid's article on buying bitcoin anonymously" Null Byte article. Be sure to check that out for more information.
2. Use OnionShare for Anonymous File-Sharing
OnionShare (via onion service) is an open-source tool that allows you to securely and anonymously share files using the Tor network. It's lightweight and easy to set up. When sharing files, OnionShare will automatically generate a new onion address that can be shared (shown below).
Similarly, OnionShare has a function to receive files. It will automatically generate an onion address where your contact can upload files from their computer. This means your contact doesn't need to install OnionShare on their computer at all.
3. Use Fake Identities & Disinformation
The use of fake identities online is a great way to minimize your exposure in the event a website you're associated with becomes compromised.
Obviously, it would be easier to simply load the account with gibberish information, but don't underestimate the value of disinformation and blending in with the crowd (i.e., the leaked database). Using false yet believable information will make it difficult for cyberstalkers and advertisers to single you out as a privacy-conscious user.
Of course, we're not recommending you go and start catfishing people online. Rather, this section should be used to help pollute website databases with false information. For example, when account registrations unnecessarily require a date of birth, profile picture, or home address. In the event said websites are breached, the personal information associated with your account will only contain false data, partially shielding you from compromises.
Fake Person Generator is an excellent tool to help generate fake identities for online accounts. It provides a name, address, date of birth, phone number, and generic profile picture that can be used when registering to websites.

The person in the above photo is not "Stephen Ortiz" at all. In fact, the photo was taken from websites that allow content redistribution. Alternatively, for unique profile pictures, thispersondoesnotexist.com can be used, which creates a new artificially-generated human face every time the webpage is refreshed.
As a best practice, while assuming a fake identity, minimize communications with people online. This will be a challenge for all you social butterflies, but it's important to anonymity as we unwittingly divulge too much information about ourselves in the ways we write, form sentences, and choose words. Various darkweb forum users have been de-anonymized by their stylometry and patterns of writing. Be mindful of this when socializing online.
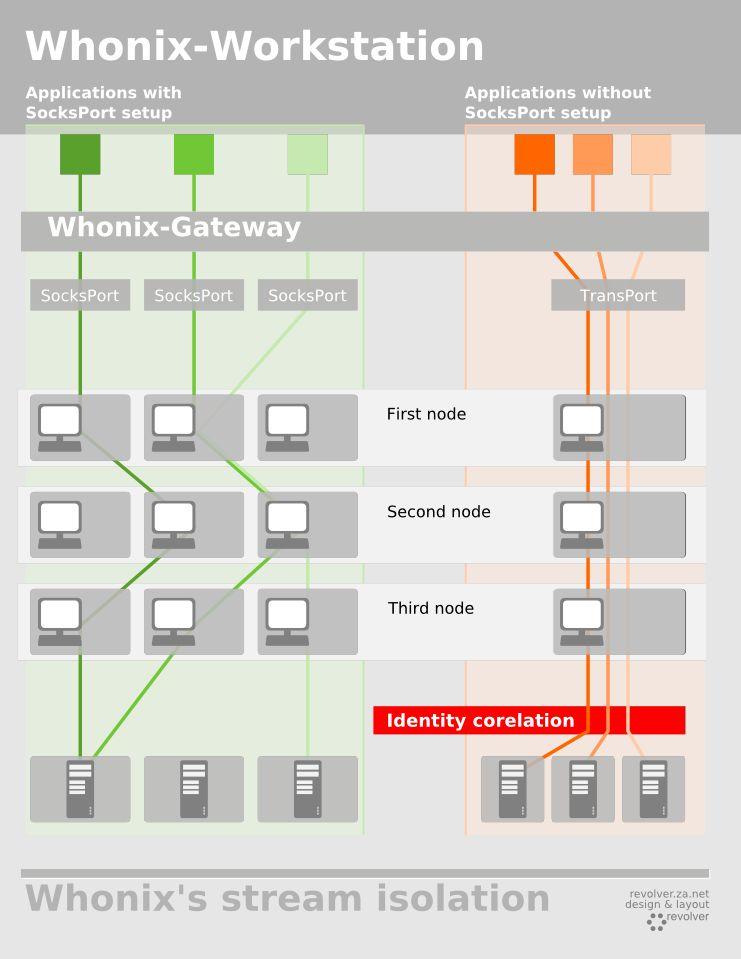
4. Use the Whonix OS for Stream Isolation
Whonix is an open-source, security-focused desktop operating system (OS) designed to be used in virtual machines. It consists of two VMs; The Whonix-Gateway runs the Tor process and acts as the secure gateway to the internet, while the Whonix-Workstation is where you install and use applications, completely isolated from the Whonix-Gateway.
Isolating the two instances greatly increases operational security. If an application running inside the Whonix-Workstation becomes compromised, it would be difficult for the attacker to then compromise the Whonix-Gateway (or VirtualBox itself) in an effect to de-anonymize you.

Whonix has a number of benefits that make it a practical solution for anyone interested in increasing the overall security of their operating system. Most notably, Stream Isolation (shown below), which lets multiple applications running inside the same Whonix-Workstation to use different routes through the Tor network. So, using an IRC client to chat with your friends will allocate one Tor exit node, while your email client utilizes another. Identity correlation attacks are mitigated by isolating the traffic on a per-application basis.
You're encouraged to check out the Whonix documentation, user forums, tips on remaining anonymous, and onion address.
5. Use Qubes OS for Advanced Security
Qubes OS (available from its onion service) is a secure, free, and open-source operating system. It allows you to isolate different activities on your computer by securely separating them from each other in isolated "qubes." This is beneficial because if one qube becomes compromised, it won't affect the integrity of other qubes and applications on the computer.
For example, if you were to accidentally visit a mischievous website or open a Microsoft Word document containing an encrypted stager in one qube, it would not affect the security of another qube where banking transactions are taking place. The attacker would be isolated to one qube, which can be easily disposed of.

For more on how Qubes works, check out OnionShare developer Micah Lee's HOPE talk, Qubes' official documentation, and YouTube user mrwilsox's video review.
- Don't Miss: Using the Ultra-Secure Operating System OpenBSD
6. Force Onion Addresses with HTTPS Everywhere
The Firefox add-on HTTPS Everywhere has a great feature built-in that allows you to rewrite URLs. This makes it possible to force onion addresses for their respective .com or .org address. For example, typing "searx.me" in your web browser can automatically navigate to the SearX onion address (shown below).

After configuring HTTPS Everywhere, it will always use the onion address automatically, even when clicking on hyperlinks. To configure this in your browser, load the regular site's URL you wish to configure, click on the HTTP Everywhere toolbar item, then click the "Add a rule for this site" button. The below example is using the Security in a Box website.

Next, click the "Show Advanced" button in the Add New Rule section, and paste the onion address into the "Redirect to" field. Leave the HTTP domain in the "Matching regex" field, and hit "Add a new rule for this site" to finish. Then, add another rule for the HTTPS domain. (Note: You can view all of your custom rules via HTTPS Everywhere's preferences from your list of "Add-ons" in Firefox.)

That's all there is to it. From here on out, navigating to the website you set up, in my example, securityinabox.org, will automatically redirect to the onion address you specified.

Below is a non-exhaustive list of websites that currently support onion addresses that can be forced using HTTPS Everywhere. For more options, check out our guide on the top websites on Tor.
debian.org : sejnfjrq6szgca7v.onion
deepdotweb.com : deepdot35wvmeyd5.onion
duckduckgo.com : 3g2upl4pq6kufc4m.onion
facebook.com : www.facebookcorewwwi.onion
gnupg.org : ic6au7wa3f6naxjq.onion
guerrillamail.com : grrmailb3fxpjbwm.onion
mail.protonmail.com : protonirockerxow.onion
mail.riseup.net : zsolxunfmbfuq7wf.onion
nytimes.com : www.nytimes3xbfgragh.onion
onionshare.org : lldan5gahapx5k7iafb3s4ikijc4ni7gx5iywdflkba5y2ezyg6sjgyd.onion
privacyinternational.org : privacyintyqcroe.onion
propublica.org : www.propub3r6espa33w.onion
qubes-os.org : sik5nlgfc5qylnnsr57qrbm64zbdx6t4lreyhpon3ychmxmiem7tioad.onion
searx.me : ulrn6sryqaifefld.onion
securityinabox.org : bpo4ybbs2apk4sk4.onion
thepiratebay.org : uj3wazyk5u4hnvtk.onion
torproject.org : expyuzz4wqqyqhjn.onion
web.archive.org : web.archivecrfip2lpi.onion
whonix.org : dds6qkxpwdeubwucdiaord2xgbbeyds25rbsgr73tbfpqpt4a6vjwsyd.onion7. Avoid Exit Nodes with HTTPS & Onion Addresses
Onion addresses allow you to actively avoid Tor exit nodes that may be monitoring web traffic. There are a handful of websites that support Tor onion services including news outlets, email providers, blogs, and social websites.
Unfortunately, there are still many websites that don't support even basic encryption. Websites that don't support HTTPS leave Tor users especially vulnerable as Tor exit node operators will be able to see everything you're doing.
Now, this doesn't entirely negate the anonymity benefits that come from using the Tor browser. Tor exit node operators still don't know who or where you are — assuming there's no personally identifiable information in the HTTP traffic.
Regardless, using Tor with unencrypted HTTP is unsafe and should be avoided. As partial a workaround, Archive.org's Wayback Machine is a great tool for accessing static websites over a secure protocol. And best of all, the Wayback Machine is available as a Tor onion service.

Simply paste the domain (e.g., neverssl.com) into the Wayback Machine's search bar, and it will load the history of snapshots for the website you can choose from, immediately create a new one, or jump right to a recent one. Below, I'm viewing neverssl.com via the Wayback Machine's onion address. This allows for anonymous access to a normally insecure website.

Archive.org knows someone viewed NeverSSL anonymously but they don't know anything about you. Similarly, NeverSSL's website was pinged by one of Archive.org's servers which is likely in a different part of the world and can't be linked back to you. This, coupled with forcing the Archive.org onion address in your web browser, can make avoiding Tor exit nodes pretty convenient.

It's Up to You How Secure Your Data Is
Absolute anonymity on today's internet is impossible. Everything we do online leaves a digital trail that can be correlated back to us in some way. The tools and techniques demonstrated in this article only make it difficult for internet providers, cyberstalkers, and hackers to track us and break into our accounts — not impossible.
Still, it's worth trying to achieve some of the Hard and Extreme security and privacy measures. There's no telling which websites, companies, and databases will be targeted this year. You and your loved ones might end up the victims of a major data breach that ultimately lead to identity theft, fraud, and other compromises that might otherwise be mitigated by using two-factor authentication or deleting an old account you forgot existed.
Your data, no matter how little value you might believe it holds, has great worth. Don't give it hackers and money-hungry corporations for free.
- Follow Null Byte on Twitter, Flipboard, and YouTube
- Sign up for Null Byte's weekly newsletter
- Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover photo by 123RF; screenshots by distortion/Null Byte (unless otherwise noted)






Comments
No Comments Exist
Be the first, drop a comment!