With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.
Often, an anon will delete files from his computer, but that is only half the story, as those files are still really there. And if the careless anon doesn't take steps to fix that, when his door gets kicked in and the FBI takes his hard drive, they will be able to see everything. Don't be that anon.
What Is Computer Forensics? The People on 'CSI'?
Computer forensics is the collection, preservation, analysis and presentation of computer-related evidence. In summary, it helps determine the who, what, where, and when related to a computer-based crime or violation. When the feds are finished arresting you and boxing up your belongings into evidence crates, they will ship them off to the FBI data lab in Washington, D.C.
In addition, an examiner will work to uncover all files on the subject's system. This includes existing active, invisible, deleted, hidden, password-protected, and encrypted files. In many cases, information is gathered during a computer forensics investigation that is not typically available or viewable by the average computer user, such as fragments of data that can be found in the space allocated for existing files (known as "slack space"). Special skills and tools are needed to obtain this type of information or evidence.

An expert can recover pretty much all of your deleted files, along with other data that has not yet been overwritten. As a computer is used, the operating system is constantly writing data to the hard drive. From time to time, the OS will save new data on a hard drive by overwriting data that exists on the drive, but is no longer needed by the operating system, i.e. a deleted file. So, the ongoing use of a computer system may destroy data that could have been extracted before being overwritten.
How to Protect Yourself
While erasing files simply marks file space as available for reuse, data-wiping overwrites all data space on a storage device, replacing useful data with garbage data. Depending upon the method used, the overwrite data could be zeros (also known as "zero-fill") or could be various random patterns. This is why simply deleting information is never enough. You must take proactive steps to ensure your removal is complete.
We are going to use a great boot disk called DBAN to perform this operation.
Step 1 Obtain and Burn DBAN
You can download the 2.2.6 Beta release from Sourceforge. Once you have the .ISO, all that's left to do is burn it to a blank CD/DVD. Place the media into your drive and restart the computer. Most computers are set to try and boot from the CD drive before the hard disk. If this is not the case, and your computer does not boot the CD drive, you will need to enter your BIOS setup and change the boot priority order.
Step 2 Boot and Run!
After the CD starts, you will be greeted with this screen:
We want to simply press enter here to start DBAN in interactive mode. The main menu shown below should display your hard drive to be wiped.
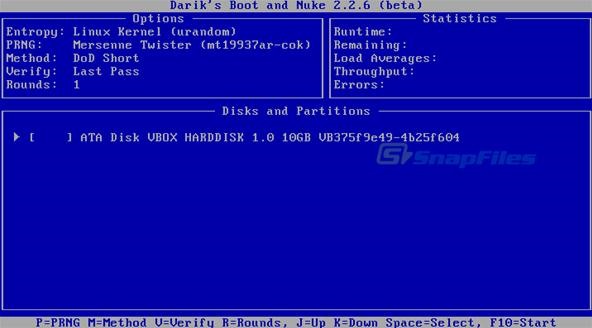
The next screen shows us DBAN is ready to get down to work, the default method is a DoD Short wipe, and it will work fine for us.
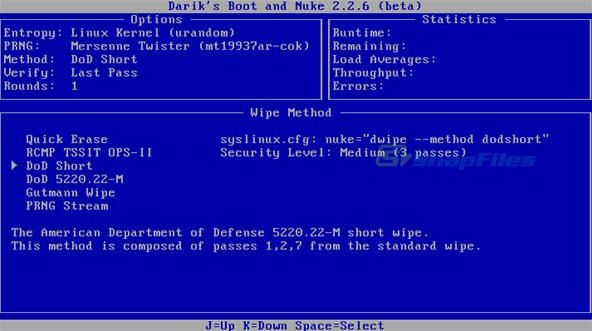
Hit the space bar to select and it will start. Be warned though, the DoD wipe takes a bit of time, especially on larger hard drives. But not as long as a prison sentence would be.
In Closing
DBAM is a great tool to clean a hard drive. I carry a copy of it in my laptop bag when I travel and you should do the same. It is quick and easy and works better then most other tools I have used. Be careful as (obviously) it is impossible to recover if you zap the wrong hard drive!
Questions? Comments? Shoot me a line here, in our forums, or on our IRC2P channel (#nullbyte).
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.
























15 Comments
What is the method of action of these programs? I know people say it writes over the data, usually with 0's, but it can't be as easy as opening up file with a text editor and replacing everything in it with 0's prior to deletion.. How does it actually work?
This is a simplified explanation, but in short:
Hard disks store data by flipping tiny magnetic bits one way or another (with one direction representing a 1, and the other representing a 0).
In order to tell the OS where one file starts or ends, each partition keeps an index of each file, pointing to the start and end of each part of each file. In the same way it keeps track of which bits are unused, so that it can write to them the next time you need to store a file. The format of that index is dependent on what kind of partition it is (FAT, NTFS, HFS, etc).
Normally when you delete a file, for the sake of speed, your disk will simply update the index to tell it that the bits used for that file are now free. It won't actually flip any of the physical magnetic bits used to represent the data in those files. Because of this, it's fairly simple for a data forensics piece of software to scan over the actual bits of the hard drive and recover the data from files that have been deleted. Additionally, even if a bit has been flipped, because it is physical in nature, slight angles make it possible to guess if it used to be a 1 or a 0 even after it has been flipped (this is considdered very low level forensics).
All that is to say that in order to completely secure your data by truly deleting your files from beyond recovery, this software will flip each physical magnetic bit back and forth between a 1 and a 0 several times (and sometimes randomly) so as to remove any possible means of being able to tell what they used to be. Make sense?
Yes, great explanation! When you encrypt your harddrive with TrueCrypt you are given an option of overwriting any data that is not being encrypted to prevent data recovery. I did a 3 time sweep on mine, which I find sufficient, but you can certainly increase it (just takes more time).
Yes, that pretty much does it for me, I suppose I was wondering if by write-over they meant the soft-data or the actual state of the bits in your disk drive. So these programs actually operate on the hardware level.. Much better :)
Bryan covered that wonderfully!
I also keep this along with other DVDs in my laptop bag even if I didn't bring my laptop. I keep this Hieren's boot disk, a dvd copy of my current OS(s) and a backtrack disk
Depending on who you want to believe, during the cold war, technology was developed to recover data despite zeroing out the hard drive. Don't know how real this is, but SOP where I was at was not to zero the drive, but put it in a machine that reduced it to small parts, the largest being about dime sized.
Nothing is 100% guarantee, but as you increase the number of passes over your harddrive you approach a 0% probability of data recovery. Even the US Gov't uses this technique...usually having a standard for each type of information from confidential to top secret, from 1-15 passes. If a file was present and read often on a harddrive that increases the probability it will leave residual markers indicating appropriate 0's and 1's. I believe it is also possible to recover data from RAM, but shortly after the computer turns off all of the data begins to fade away. Look up "Magnetic force microscope", that is what is used for advanced data recovery. As that tool becomes more precise, it allows for data recovery. But 15 passes would definitely leave you clueless as to what the prior data was. In fact, I couldn't imagine much could be extracted with a 3 pass?
I watch a report on magnetic password recovery for siezed computers with encrypted drives. It seems that some programs keep the password in memory and during the show, the shut down the computer. Sprayed the memory with a compressed air can turned upside down and removed the memory and placed it in a different computer to extract the values from the memory and search for password keys. I don't know how feasible this is, but I do remember TSR viruses a decade or so ago.
Yes, that was what I was alluding to, that the password may be stored in RAM, thus you could extract it from there. However, I think RAM fades quite quickly, so you would have to freeze the RAM physically to maintain the state. I don't have any evidence to support this can be done as I am not a professional data recovery specialist or anything, but I think it would be possible?
what about ssd is there any good ways to completely erases data from that?
download link here is v.2.2.6 .there's v.2.3.0 available from dban.org (that'll also download from sourceforge...)
I know this article is kinda old, so I'm just saying for newbie who would be reading that in 2018
Seems like this would take a long time. Wouldnt keeping the drive encrypted and smashing it be faster? I mean the data is there yes but best of luck.
I am that newbie Kali, but we all have to start somewhere. Pain has brought me to the doors of this citadel. Awed by its writers knowledge of my woes this website has given me hope to soon be rid of a plauge that has followed me for 9 months now. I am eager to learn, as I was late to the table. So I thank you for even the scraps left behind.
Sorry my english is not good, if i wipe my phone once (with main data), and then i reboot the wiped device and shooting some photos for new data and wiping it again, is the phone with main data 100% wiped ?
Share Your Thoughts